Documentation
Analyzing SMTP Mail Headers
Analyzing SMTP Mail Headers
ExchangeDefender uses SMTP headers to help troubleshoot mail delivery problems and delays. Every email message consists of email headers and the email body. Email body includes all the message text, encoded attachments, etc and is generally what you see when you open an email. Email headers are typically hidden and contain a lot of transit information that mail servers print in the header of the message as it passes through them. This article will show you how to locate SMTP headers and how to interpret and analyze them.
Getting SMTP Headers
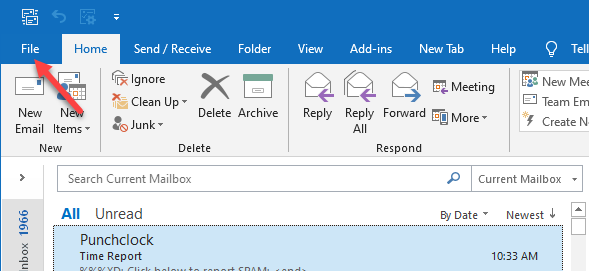
Outlook 2010 - current
Double click to open a message in it's own window:
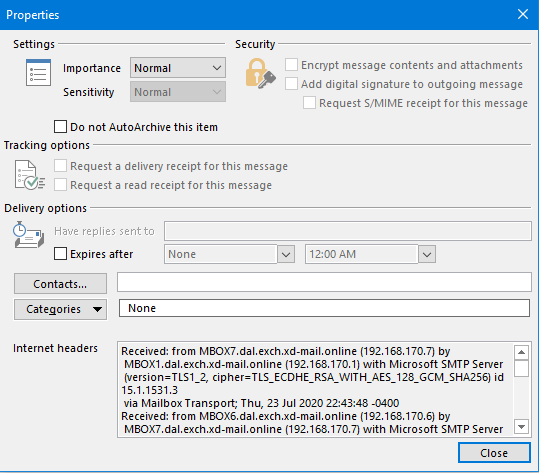
File > Info > Properties > Internet Headers
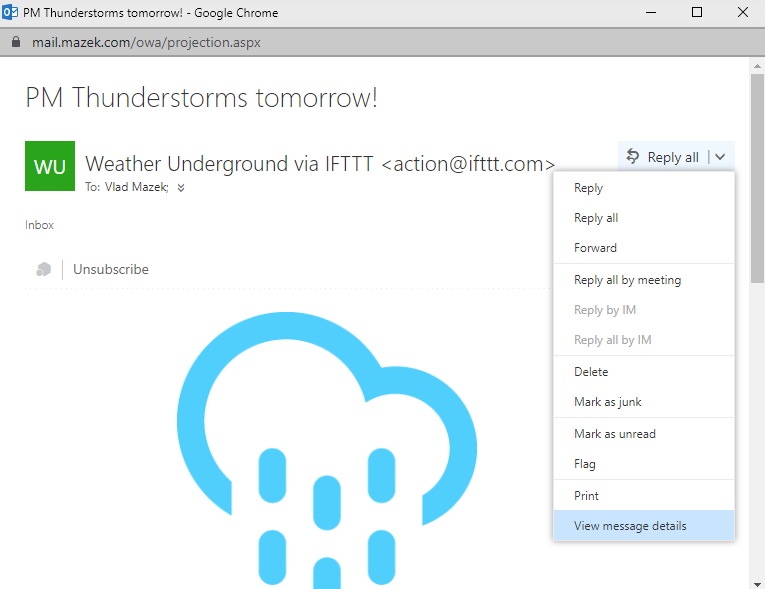
Outlook Web App (OWA)
Open the message in it's own window:
Down arrow next to Repy all > View message details
Apple Mail
View > Message > Raw Source
Outlook 2018 for Mac
From the message listing:
Control + Click >> View Source
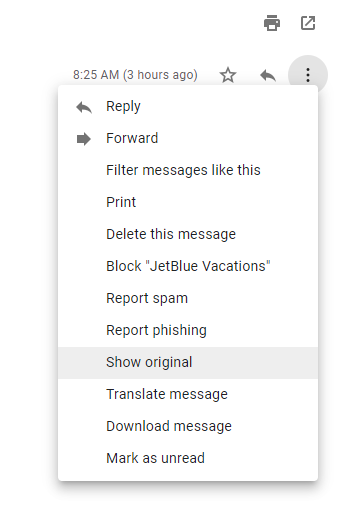
Gmail
Open the message:
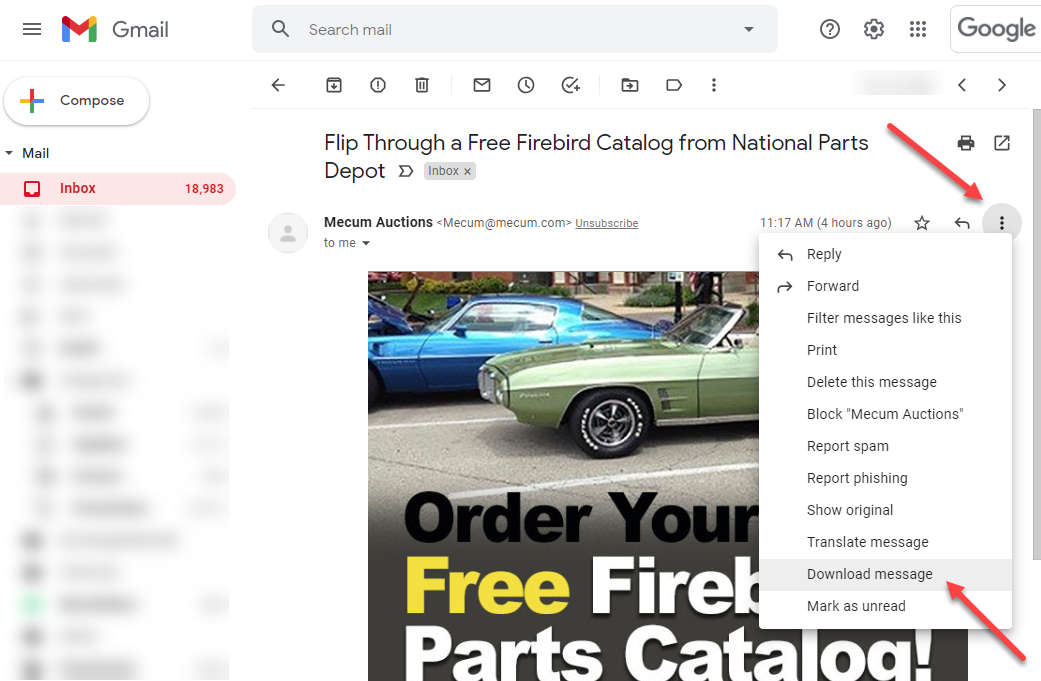
Down arrow next to Reply > Show Original
Most of the time SMTP headers are too long to display in a small box (note scroll bars on the side) so make sure you select and copy all the text in them before opening a support request. ExchangeDefender prefers having the entire message submitted, so if you can save the entire message in an .msg file we’ll dig for the SMTP headers for you.
Analyzing SMTP Headers
When you compose a new message, your email client (MUA, Mail User Agent) submits the message along with any attachments to a mail sever with the basic SMTP headers indicating From, To, Subject, and so on. After that, every mail server that processes the message will put it’s own routing diagnostics at the top of the SMTP headers.
There are many SMTP header analyzers available for free on the Internet where you can paste your headers and get a pretty and intuitive graphical breakdown of the message, contents, and delays. In general, your SMTP headers may look something like this:
Received: from MBOX7.dal.exch.xd-mail.online (192.168.170.7) by
MBOX1.dal.exch.xd-mail.online (192.168.170.1) with Microsoft SMTP Server
(version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256) id 15.1.1531.3
via Mailbox Transport; Thu, 23 Jul 2020 22:43:48 -0400
Received: from MBOX6.dal.exch.xd-mail.online (192.168.170.6) by
MBOX7.dal.exch.xd-mail.online (192.168.170.7) with Microsoft SMTP Server
(version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256) id
15.1.1531.3; Thu, 23 Jul 2020 22:43:48 -0400
Received: from XDON-DAL-EDGE1.dal.exch.xd-mail.online (192.168.190.10) by
MBOX6.dal.exch.xd-mail.online (192.168.170.6) with Microsoft SMTP Server
(version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256) id 15.1.1531.3
via Frontend Transport; Thu, 23 Jul 2020 22:43:48 -0400
Received: from duckburg.exchangedefender.com (65.99.255.23) by
XDON-DAL-EDGE1.dal.exch.xd-mail.online (192.168.190.10) with Microsoft SMTP
Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id
15.1.1531.3; Thu, 23 Jul 2020 22:42:19 -0400
Received: from mx1.slc.paypal.com (mx0.slc.paypal.com [173.0.84.225])
by duckburg.exchangedefender.com (8.14.7/8.14.7) with ESMTP id 06O2h1LX025300
(version=TLSv1/SSLv3 cipher=DHE-RSA-AES256-GCM-SHA384 bits=256 verify=NO)
for ; Thu, 23 Jul 2020 22:43:02 -0400
DKIM-Signature: v=1; a=rsa-sha256; d=paypal.com; s=pp-dkim1; c=relaxed/relaxed;
q=dns/txt; i=@paypal.com; t=1595558581;
h=From:From:Subject:Date:To:MIME-Version:Content-Type;
bh=0UdynO8yHqgNmi+Y07Cg5PgD0UkUheWWZH5GPvOwZ5I=;
b=0MLRhP/3yQSRmAL6QYs6Gun7EK12BU43deNCiLXjKLWXhqyVhCqGmYsU5Oapgmbf
mEGN1dqoydjG8xwWFZkHw7FnA8dL4rVhKrQZ9tG5lhp6Km/pGQUMpvlH7DuDg77D
eLXq5NzFRPRDo1bXlw/BRPpgZE1aSne/fWaGskdzSrgtm6sbubTFanGDQj+p/If/
KTCCNilH3F+XDQpUKzKxzsyKzd2gTQlA9nEqXYrX7ruMRvG6ZSFRZPR1hP/p9Qkr
M4NRAHW9Hnbx9sh7ipBzjwmBmPWLzKSVgSDRLW7FBL1dpbYO2Q4fnAppLXurjPGG
+c3+u5i7dqj+dsV78y7nSA==;
Received: (qmail 3685648 invoked by uid 993); 24 Jul 2020 02:43:01 -0000
Date: Thu, 23 Jul 2020 19:43:01 -0700
Message-ID: <1595558581.3685648@paypal.com>
X-PP-Priority: 0-none-false
AMQ-Delivery-Message-Id: EMAILDELIVERY-Notification_EmailDeliveryEvent-5-1595558574658-288606171
X-PP-REQUESTED-TIME: 1595558571935
X-PP-Email-transmission-Id: 5fed7b4e-cd57-11ea-a9f7-b875c0bfd1b3
PP-Correlation-Id: 52ddcd53e2d25
Subject: Receipt for Your Payment to Microsoft Corporation
X-MaxCode-Template: PPX001066
To: Vladimir Mazek
From: "service@paypal.com"
X-Email-Type-Id: PPX001066
Content-Transfer-Encoding: base64
Content-Type: text/html; charset=UTF-8
MIME-Version: 1.0
X-ExchangeDefender-Info: ExchangeDefender Mail Security
X-ExchangeDefender-VirusScan: Found to be clean
X-ExchangeDefender-SpamScan: not spam, SpamAssassin (score=4.002, required 5,
autolearn=disabled, DCC_CHECK 5.50, DCC_REPUT_70_89 4.00,
DIGEST_MULTIPLE 0.00, DKIMWL_WL_HIGH -0.00, DKIM_SIGNED 0.10,
DKIM_VALID -0.10, DKIM_VALID_AU -0.10, HTML_FONT_LOW_CONTRAST 0.00,
HTML_MESSAGE 0.00, MIME_HTML_ONLY 0.10, PYZOR_CHECK 1.98,
RCVD_IN_DNSWL_BLOCKED 0.00, RCVD_IN_MSPIKE_H3 0.00,
RCVD_IN_MSPIKE_WL 0.00, SPF_HELO_NONE 0.00,
T_KAM_HTML_FONT_INVALID 0.01, URIBL_BLOCKED 0.00,
USER_IN_DEF_DKIM_WL -7.50)
X-ExchangeDefender-SpamScore: 4
X-ExchangeDefender-From: service@paypal.com
Return-Path: service@paypal.com
X-MS-Exchange-Organization-Network-Message-Id: 98c38cec-bf35-463b-339b-08d82f7b2f41
X-MS-Exchange-Organization-AuthSource: XDON-DAL-EDGE1.dal.exch.xd-mail.online
X-MS-Exchange-Organization-AuthAs: Anonymous
X-MS-Exchange-Transport-EndToEndLatency: 00:01:29.3013741
X-MS-Exchange-Processed-By-BccFoldering: 15.01.1531.003
Each line in the SMTP headers contains vital information that the server processing the message wanted to note. Many of these lines are used to determine processing delays, mail delivery issues, evaluate routing, why a message went to SPAM, where it was sent from, and so on. Because every mail server can add lines as the message passes through them, these lines are also subject to spoofing and other malicious behavior so while useful in troubleshooting not every line is trustworthy. Here is a summary of the SMTP headers you’ll often see:
The received lines are best read from bottom to top. That is, the first "Received:" line is your own system or mail server. The last "Received:" line is where the mail originated. Each mail system has their own style of "Received:" line. A "Received:" line typically identifies the machine that received the mail and the machine from which the mail was received. Dkim-Signature & Domainkey-SignatureDomainKey Signature string. You can learn more about these by visiting: http://en.wikipedia.org/wiki/DomainKeys. Message-idA unique string assigned by the mail system when the message is first created. These can easily be forged. Mime-VersionMultipurpose Internet Mail Extensions (MIME) is an Internet standard that extends the format of email. Please see http://en.wikipedia.org/wiki/MIME for more details.Content-TypeGenerally, this will tell you the format of the message, such as html or plaintext. Message BodyThis is the actual content of the email itself, written by the sender. X-ExchangeDefender-VirusScanExchangeDefender virus report, either found to be clean or infected. X-ExchangeDefender-SpamScan ExchangeDefender SPAM signatures and definitions. This important block identifies all the SPAM definitions this email contained X-MS-ExchangeMicrosoft Exchange-specific headers and routing information.
ExchangeDefender often uses SMTP headers to help troubleshoot email delivery delays. You can always paste your SMTP headers into a Header Analyzer such as https://mxtoolbox.com/EmailHeaders.aspx which will produce a visual breakdown of which servers processed the message, if they are on any blacklists, etc.
Exporting Messages
ExchangeDefender automatically enforces policies and categorizes messages based on the content of the message and message headers (Yes, seriously. It’s all automated. No human being, under any circumstances, looks at your message as it goes through ExchangeDefender).
Sometimes you do need professional help (to find out why a message was blocked or allowed, which policies were enforced or should be enforced) and our support team at https://support.exchangedefender.com will request a copy of the SMTP headers and the message in .eml/.msg format.
This guide will walk you through how to save the message.
Exporting Messages from Outlook
There are two ways of exporting messages from Microsoft Outlook.
The simplest way is to simply drag the message from the message listing to your Desktop. Outlook will automatically save the message in a .msg format with the same file name as the subject.
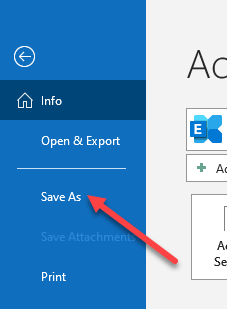
The more flexible way to export a message is to select it from the message listing and click on File.
On the left navigational panel, click on Save As.
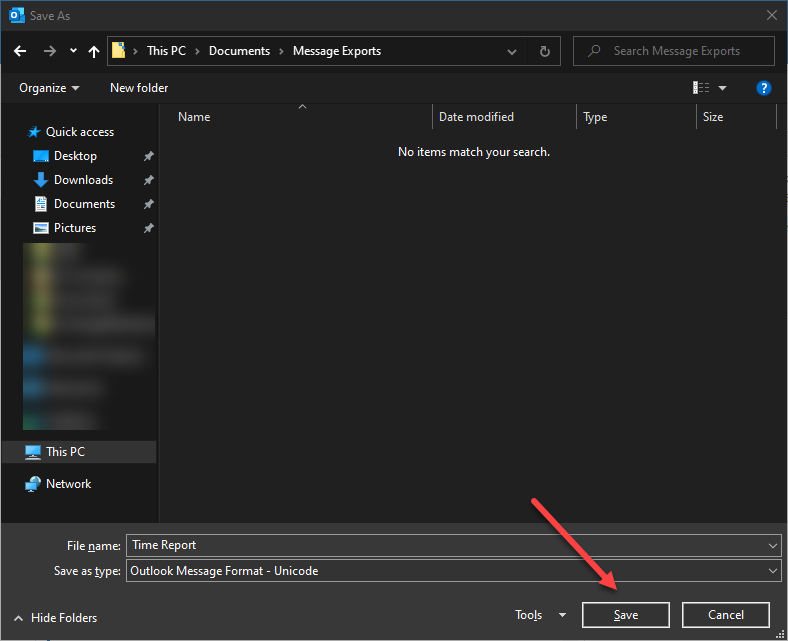
Microsoft Outlook will prompt you where to save the file, make sure you select “Outlook Message Format – Unicode (default)” as the format and click Save.
Exporting Messages from Outlook Web Access
To export messages from Outlook Web Access (Outlook Web App / Outlook on the web) first login to the OWA account.
Click on New > Email message.
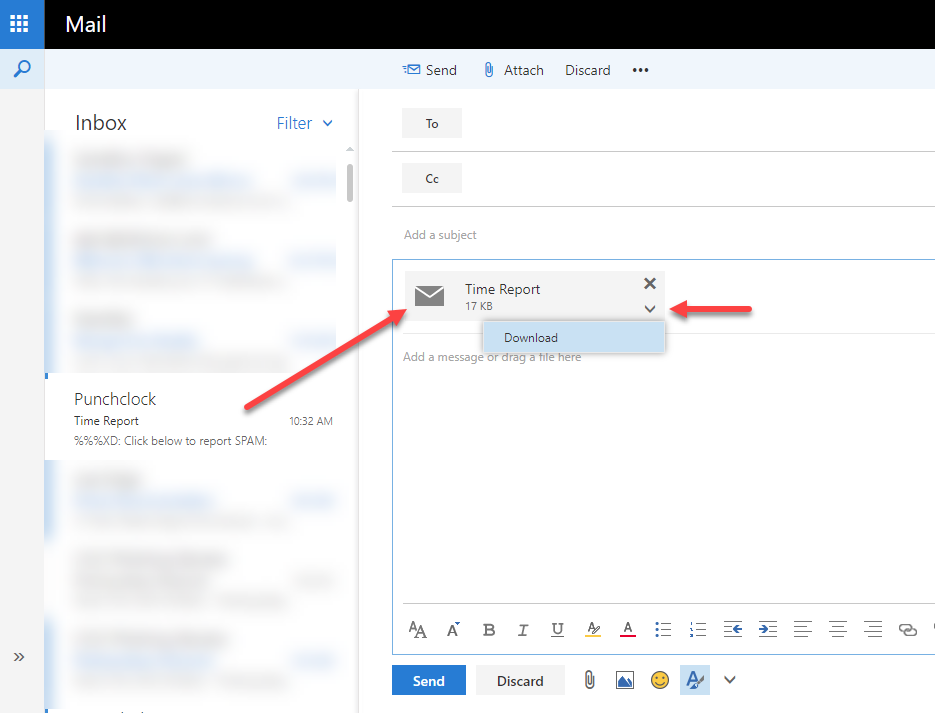
Drag and drop your message onto the body of the new message. You will see the message as an attachment.
In the lower right hand corner of the attachment you will also see a menu arrow. Click on it and select Download. Message will be saved as a .eml file on your computer.