ExchangeDefender Address Book Lockdowns
Effective March 1st, ExchangeDefender will only allow delivery to email addresses that exist in our Service Manager or ExchangeDefender Admin Portal. This is a non-event for 99.999% of our clients (it’s only being mentioned because it’s a refresh of the AUP/TOS policy) and it is intended as a security precaution against threats we’re seeing in the wild and on our honeypot networks.
The Problem
ExchangeDefender as an SMTP proxy will scan and deliver any email targeted at a protected domain. Even though we sanitize each message and do not permit dangerous content through, if the email address does not exist on the clients server, the message will bounce to the sender. Now, imagine that sender doesn’t have an SPF/DMARC, and imagine that the address itself is spoofed – now send that message a few thousand times and an attacker can destroy a mailbox simply by overloading with non-delivery receipts and bounce messages.
Why this happened in the first place
Bad automation. It happens, and when it happens on a scale of ExchangeDefender, it creates an issue. So to minimize complaints, we just stopped actively enforcing address book validation. To those of you protecting servers on networks outside of ExchangeDefender’s control (think Google, Office 365, etc) the management and addition of new addresses will become automatic. Here is a peak at our new support portal. It should make a lot of you very happy.
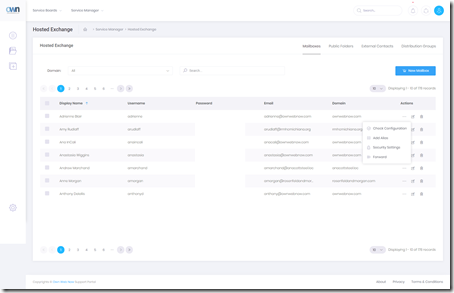
Figure 1: Service Manager. Instead of having a ton of accounts in the listing, everything is now logically grouped by a Company. This way whenever you go to manage one client you only see the users belonging to that client and any addition or modification will pull pricing, configuration and meta data from that organization’s settings. This should virtually eliminate mistakes, billing issues and configuration problems.
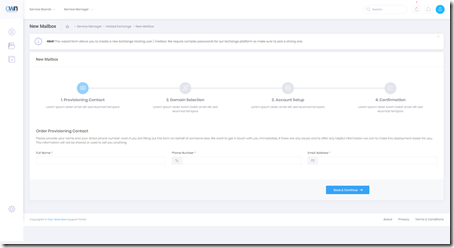
Figure 2: Adding a new mailbox. The process is streamlined, clean and remarkably simple. The reality is that IT departments are no longer in charge of this anyhow, neither are our MSP partners. Businesses want the ability to control memberships, configurations, distribution lists, permissions and everything in between.
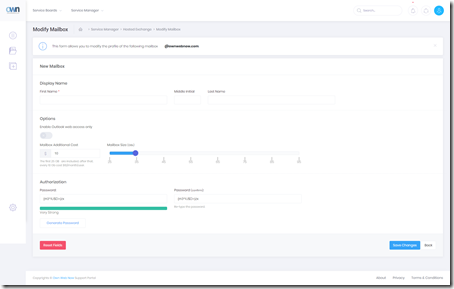
Figure 3: Mailbox permissions, settings, etc. There are several screens for this but needless to say we’re looking to expose a lot of the features that can be managed granularly in a way that businesses expect them to. Let’s face it, your average office manager dealing with the new hire isn’t about to fire up remote PowerShell; Strong passwords, additional features, granular control, public folder and distribution group membership templates, etc are all coming soon.
Other really cool stuff is coming very soon as well, we’re pretty excited with what we’re building and delivering… but the focus for us always remains on the security and safe communication – and everything that supports it goes hand in hand.
ExchangeDefender Account Lockouts
We live in interesting times. With over 1.4 billion compromised accounts and users relying on the same password for every site, it’s nearly impossible to secure users that don’t want to set strong passwords. Nevertheless, that’s what you pay us for and we’re doing our best.
Until the new Service Manager is in and automatic service policies with full compliance are added in, we’ve been forced to institute lockouts on accounts that are being compromised or have suspicious activity. Unfortunately, when an attack on a mailbox is launched it doesn’t come from one IP address, it comes from hundreds, and blocking them is impossible.
But locking the account and making the client change the password to something that isn’t on the dark web.. that’s simpler. This is something that absolutely has to get done, if the account is used for spamming purposes it can blacklist that address, domain or worse.
If your account gets locked out due to a security compromise, you can now unlock them and restore service automatically.
Just go to the Service Manager, find the user, reset the password and you should be all set.
P.S. In the event that you aren’t regularly changing your clients passwords, or you have ridiculously simple ones, we need to talk. Part of the issue is that your clients, regardless of size location or industry, are just SPAM zombies waiting to happen if you don’t set long and complex passwords that aren’t used anywhere else. If you don’t want to do that, we need to talk about two factor authentication. ExchangeDefender network has never been compromised – but individual accounts get popped all the time and it’s generally with a password that is well known and available in a simple Google search.