We’ve Upgraded Exchange Essentials
Let’s face it, not all businesses need mission critical, data center redundant, year-long business continuity backing their operations. They just need an effective system to communicate and collaborate. Say hello to ExchangeDefender Exchange Essentials 2013. Here is the executive overview:
Microsoft Exchange 2013 Mailbox (10GB)
ExchangeDefender Essentials Security
5 days of business continuity (Emergency)
Private Branding + White Label
24/7 Support via portal, phone and chat
Just
$7.99$6.99 / month
This highly redundant offering is a perfect starter email solution for a company migrating from SBS or in-house server solution. True, it doesn’t have long term business continuity of LiveArchive, compliance, encryption, migration assistance or data center redundancy but if you need to manage your budget this is a great way to do it.
One more thing: For the next month we will be offering a discount of $1 that will be locked in for at least one year, so it’s yours for just $6.99 per user per month. Of course you can rebrand it and adjust the pricing to compensate you for provisioning and rollout.
But what if it goes down?
Exchange in the cloud is the same as Exchange in your office, there is no magical version and from time to time it will have issues. We have a redundant and clustered deployment so when we have to do maintenance or when there is an unexpected issue, we can shut down servers without interrupting service. But let’s say something significantly bad is going on and everything goes lights out – what now? Well, we have ExchangeDefender Emergency backing you up and giving you access to 5 days worth of email archive that you can search, view and reply/compose from. You continue to work until your Exchange mailbox is ready.
This in fact is the biggest and easiest upsell in our cloud portfolio: Once you show your users how easy it is to be able to send and receive email when there is an outage, just tell them you have another solution that also gives them access to all their contacts and appointments – along with a year worth of items available for them. Oh, and it works on your mobile device as well so you don’t have to be stuck in front of a PC with a web browser. For just $2 a month more you can have ultimate peace of mind knowing that you’ll never have to worry about your mail.
But Vlad says this is not for business? Is it?
As an expert (not meaning smart, meaning I’ve been through enough email outages to know better) I cannot in good conscience recommend a solution that I know has a potential to cause downtime. ExchangeDefender Essentials was built as a way to compromise on data center and business continuity systems in order to create a budget friendly service.
My personal opinion of the potential pitfalls is not the corporate representation of the product or everyone that works here: We support the product around the clock, we spare no expense when it comes to creating a high end product, we have built what we believe is the most effective and most powerful email solution on Exchange 2013. But if something has a potential to go down, when the rock solid one costs just $2 more, I just cannot hide my contempt for it, that’s all. Take it with a grain of salt as you do all opinions. This is just one of the differences with ExchangeDefender, we are here for our partners and our clients – not investors. We want to give you every benefit we can possibly come up with so you can win in the market and make your clients happy.
To sum it up
Enjoy. If you have any users on SBS this is a great opportunity to get them on a solid platform for $6.99 with the discount through the end of January 2014.
Sincerely,
Vlad Mazek, MCSE
CEO, ExchangeDefender
vlad@ownwebnow.com
ExchangeDefender Q4 Call Summary
 Last week we held our latest partner call for the year and announced a number of solutions that you have been asking for. We have two new products that our partners have been very successful with and we’re now opening them to our entire partner base. I encourage you to download and listen to the webinar because we go over quite a bit, as we will on the blog in the coming days:
Last week we held our latest partner call for the year and announced a number of solutions that you have been asking for. We have two new products that our partners have been very successful with and we’re now opening them to our entire partner base. I encourage you to download and listen to the webinar because we go over quite a bit, as we will on the blog in the coming days:
ExchangeDefender Q4 Partner Briefing
http://www.ExchangeDefender.com/media/ExchangeDefenderQ4.wmv
11:13 Exchange Essentials 2013
16:54 Exchange for Business
24:52 Exchange Defender Android & iOS
30:10 2014 For Us
34:01 2014 For You: Threats
37:37 2014 For You: Opportunities
That said, here is a brief summary:
Exchange Essentials 2013 – We are launching an affordable Exchange 2013 offering to help you compete with inferior Exchange hosting solutions. There is no pretty way to put this – some people don’t think they need data center redundancy, full ExchangeDefender, SharePoint/Lync, compliance or business continuity. We have been offering Exchange 2010 Essentials for years and now we’re adding 2013 to that portfolio at $7.99/mbox: easy, redundant clustered infrastructure, ExchangeDefender Essentials and our 24/7 support.
Exchange for Business – The exact opposite of Exchange Essentials, this is the full suite with our best failover, business continuity, business tools like Compliance Archiving & Encryption. But there is more: this is a concierge deployed service – we will migrate your clients data and their configuration if you’d like but we’ll definitely take care of setting up all the services for you and confirm everything is setup as it should be. We find it that some of the larger accounts don’t quite cross their t’s and dot their i’s so we will make sure we have someone here to manage this rollout end to end and make sure it’s deployed right. Since it’s going to save us some support costs and time we’re knocking off $1/month off what it would cost you to put these products together separately. Keep in mind that competitive solutions for archiving start at $10 by themselves so charging less than $25-35/month for this $16.99 offering would be considered a pretty big Christmas present on your part.
ExchangeDefender Mobile for Android and iPhone – And now on to something free: ExchangeDefender is coming to mobile in a big way and our iPhone and Android apps will be on your devices in time for the holiday break (depending on the Apple store approval). We are bringing quarantine access, SPAM management and previews, LiveArchive and other stuff to the app to give your clients a better handle on email. We are looking for ideas and suggestions but we already have plans to integrate LocalCloud, Compliance Archiving search and more right in the app so all of your information is always at hand. There are no plans for Blackberry or Windows Phone versions at this time due to each platform making up less than 1% of our current mobile user base.
Brief note on availability: We will be open during the last week of the year but we will be working on a skeleton crew while everyone will be in training December 30th – January 3rd. During this time most of the sales staff will only be available for an hour or two on the phone and executives might only be available after hours. It is important for us to get 2014 started right so these days of training and planning will take precedence over regular operations.
Sincerely,
Vlad Mazek, MCSE
CEO, ExchangeDefender
vlad@ownwebnow.com
ExchangeDefender Client Software
We are proud to present the first release of the new Client Software infrastructure that is starting to include all of our ExchangeDefender solutions under one look and experience. As I’ve explained before, we are bringing the same ExchangeDefender web experience to your Desktop/Outlook as well as the mobile world of iOS and Android. Lot’s of new stuff so let’s get started.
Branding: The most demanded feature for the Outlook and Desktop addin. You don’t have to customize things either, all the product names, logos and colors will be pulled down from ExchangeDefender based on the user login.
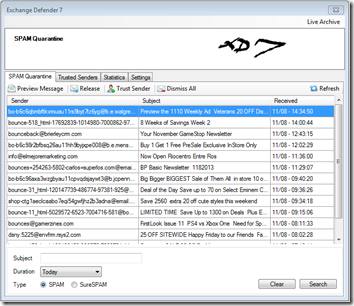
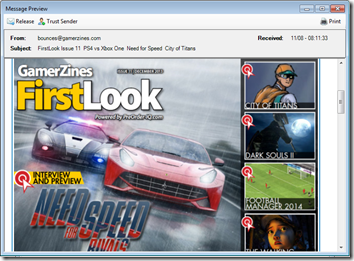
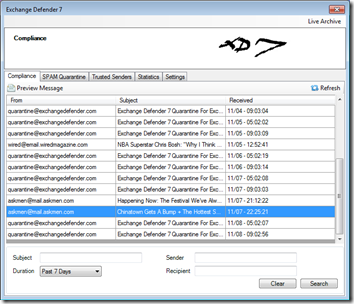
We are adding search as well as message previews to ExchangeDefender quarantines. This gives our clients true, live access to the SPAM quarantine and makes the system respond in realtime along with the ability to instantly print, whitelist or deliver the message.
Previews are great for clients that need immediate access and don’t want to waste tons of time waiting for emails to be released and delivered to their Inbox – they can access them right away!
Speaking of the need for realtime alerts, some of our clients really liked old email reports because they would get that daily reminder of all their SPAM. We’ve introduced a new feature with the ExchangeDefeder Outlook addins (desktop has had it for years) that will pop up a reminder that there is new SPAM waiting for you every 30 or 60 minutes.
LiveArchive & Compliance Archive
Just one more.. well, two more things. We are adding access to LiveArchive and ComplianceArchive so it’s never more than one click away.
LiveArchive will give you a one click access to the full web experience of a fully functional webmail client now with contacts, appointments and a year of your email.
Compliance Archiving is being embedded right into the product – you will be able to quickly locate, open and even filter down messages by subject, sender, recipient and date. This will allow people with very large mailboxes to quickly get to the messages that may have been received years ago with a quick search.
One of the biggest improvements in the actual infrastructure of the Desktop and Outlook 2010 & 2013 addins is that the addin will automatically update itself whenever a new version is released. Unfortunately, you will have to uninstall the existing addin and install the new one from here, but this will be the last time!
As always, all our software is available for download here.
Hank Newman
VP, Development
Exchange Migration Conversations
 Many of our partners have been asking about the migration collateral as well as the experience our partners and their clients have on these calls. What is being discussed? How are you being introduced? Do you try to sell? What sort of information do you provide? What kind of guarantees do you provide? Relax. It’s a process and a very flexible one at that with two goals in mind: Reassure the client and identify any problems up front.
Many of our partners have been asking about the migration collateral as well as the experience our partners and their clients have on these calls. What is being discussed? How are you being introduced? Do you try to sell? What sort of information do you provide? What kind of guarantees do you provide? Relax. It’s a process and a very flexible one at that with two goals in mind: Reassure the client and identify any problems up front.
Pre-call (Partner)
Prior to the call with the client, ExchangeDefender and our Partner get together and go over the new opportunity. We discuss all the obvious stuff – domain names, current technology, current problems, any special personnel or solutions in place, timelines, etc. We determine how ExchangeDefender will be introduced (sometimes as ExchangeDefender, sometimes as “migration team” and other times just by the name) and which solutions we are to discuss during the call.
We do not sell to the client on the call. It is partners responsibility to evaluate the needs and requirements the client may have for more complex things like corporate encryption, long term archiving, Outlook addins and so on. However, sometimes we can explain the technical and business implementation matters better because of our experience with them and we make sure we get our partners permission to talk about those items. Sometimes partners have a third party encryption or compliance product they prefer over ExchangeDefender so we try to make sure we follow the plan the partner has laid out for their client and assist in what they want to do.
Initial Client Call (Partner & ExchangeDefender & Client)
Partners typically arrange a phone call between the client, themselves and us and we get on the line with our questionnaire and go through the typical barrage of questions that lead us in the direction the client deems to be most important. This is critical: Always let the client guide you through their problems so you can address them. Based on their prior experience, company management may have different concerns than their IT team or previous IT Solution Provider; they may not be the right ones to answer the questions you may be asking; they may provide more detail of where the company is going and give both the partner and ExchangeDefender an avenue to help mitigate some risks and problems that will show up down the road.
During the initial talk we identify their primary problems and concerns; identify the contact points and vendors they rely on; timelines or dates around which no service interruption should take place; regulatory compliance requirements and activities, etc.
The purpose of the first call is to introduce our process, make adjustments and determine the correct plan of action.
Followup Partner Call (Partner & ExchangeDefender)
There are always surprises and opportunities the more we talk with our clients. The purpose of the followup call is to divide up the work and discovery process and begin the assessment. While some partners will allow us full control of the process and trust us to do the work end-to-end, others may prefer to do parts of the migration process themselves (installing their own RMM, making backups, etc) and we plan our course of action during this call.
Without getting extremely granular on every detail, the technical process of a migration is not complex. The complexity comes from problems, issues and limitations that come up during the mailbox move. So one of the first steps after we deploy the ExchangeDefender Business Monitoring tool (or our partners RMM choice) is to deploy bandwidth monitoring tool and verify the speed of the Internet connection around the clock. We go through the mailbox infrastructure and identify large mailboxes that are appropriate for Compliance Archiving, run tests and so on. The goal of the followup is to get an understanding of what can and cannot be done, what timelines we may be looking at given the limitations and restrictions and to match up calendars and migration schedules.
Followup Client Call (Partner & ExchangeDefender & Client)
Followup calls are optional and frequently handled by the partner but ExchangeDefender does offer to be a part of the whole process of explaining our discovery and our recommendations about compliance, encryption, DNS control, migration, LiveArchive business continuity, upgrading of various desktops and systems, viability of the Outlook addins or third party vendors or remote office migration plans.
The initial process is all about gathering ideas, suggestions, problems and solutions and running them by your client. It’s never going to be foolproof and we’ve heard this one often:
“You are very reassuring and seem to have a good grasp on how all this works. I’m happy about that. My concern is with things that you don’t know about and things that we don’t bring up that will break the system after the migration. We don’t want to be in a situation where you just tell us that you didn’t know about it because we didn’t tell you”
The above problem is inevitable, it is commercially impossible to both provide an economical move and a fool proof one. So we focus on the process at hand, we do only what we write into the contract and then we deal with anything that may be outside of that contract through other means. It doesn’t make all the clients happy – which is unfortunate – but it gives them something they can count on and a process they can understand.
As we go through the migration, every step is clearly communicated to the partner. They are armed with tons of branded collateral and every message we send out also has their logo on it. We can send the notification directly to the partner or to the partner and the client contact. Whenever a mailbox moves, whenever a DNS record changes, whenever a login is about to be made or profile reconfigured – we send out notices.
For more details on the collateral and the process notifications and the actual migration and technical stuff, stay tuned. There is new stuff being added every single day and a lot of it is customized with each given scenario. The key to migrations is planning and constant communication. So we’ll obviously have more and more of it here.
-Vlad
Sincerely,
Vlad Mazek, MCSE
CEO, ExchangeDefender
ExchangeDefender Outlook 2013 Integration
We’re happy to announce Outlook 2013 addin for ExchangeDefender. You can download it here and you won’t have to use anything but Outlook to access your most frequently used ExchangeDefender functions such as management of SPAM quarantines, whitelists, stats and so on. The plugin will refresh the data every 30-60 minutes (or in realtime if you prompt it to do so) and it’s just that simple.
What I would like to discuss now is the future of the platform. As you may have seen on this blog, there has been a significant amount of mobile development on our Shockey Monkey platform. All of that is coming to ExchangeDefender as well this quarter.
It gets even better: Now that we have ExchangeDefender Outlook addins for Outlook 2007, Outlook 2010 and Outlook 2013 (in addition to our Desktop addin, our web portal) we are looking to extend these addins to incorporate additional ExchangeDefender features to the everyday Outlook experience: LiveArchive Business Continuity, Encryption, File Sharing, Compliance Archiving Search and Recovery, LocalCloud, Chat and more. By further integrating these services with your mobile and desktop (or Outlook) experience we are able to provide a more cohesive and collaborative office experience no matter where you are or which device you are using. This is a significant challenge but one that we are working on every day.
Hank Newman
VP of Development, ExchangeDefender
hank@ownwebnow.com
Answering With The Cloud
 Every new wave of technological advancement brings nuances that make it difficult to make the exact comparison to the problems old technology solved. The easiest way to promote the new stuff is to talk about all the new great things it does, but what do you say when you are questioned about things that are no longer a problem in the 21st century?
Every new wave of technological advancement brings nuances that make it difficult to make the exact comparison to the problems old technology solved. The easiest way to promote the new stuff is to talk about all the new great things it does, but what do you say when you are questioned about things that are no longer a problem in the 21st century?
One of the questions we are usually asked is if a company has enough bandwidth to rely on Hosted Exchange.
Fair question. When the small company first started it’s Exchange deployment in late 90’s early 00’s it had all it’s employees in one site and every desktop was on the LAN. Fast forward to 2013 where most employees have mobile phones that are in constant sync with the Exchange deployment over the WAN. Remote offices, road warriors, executive laptops at home – now each user has several devices connecting to the Exchange server at the office and there would be actual net savings in bandwidth if the Exchange server went to the cloud!
To be fair, these “infrastructure concerns” are typically coming from the IT employee who is trying to protect his job with inferior solutions: Your sales process should focus on actual business operations concerns around business continuity, security and compliance. Here are some ways to differentiate the cloud model with the DIY model.
Just how reliable is the cloud version? What happens when it goes down?
Well it uses the same software that you would run in your office so it is comparable to your existing experience. The difference with the cloud is that the systems are much larger and far more redundant so they can conduct more maintenance without affecting operations because it’s not a single server. Maintenance keeps small problems from becoming big problems and when there are issues they are posted here so you know exactly what is going on.
Cloud Exchange is also redundant across two data centers so if there is a networking issue that impacts one you will still be in business.
In the event of a catastrophic outage, where your cloud Exchange is actually down, you can rely on ExchangeDefender LiveArchive which gives you last year worth of email including all your contacts, calendars and appointments with full realtime access to send and receive even over a mobile device.
What about backups? What if they go out of business? How can I be sure I have my data?
You’re protected in several ways, the most immediate one being Outlook 2013 cached mode. Because Outlook 2013 is included for free we will upgrade all your workstations to store all your email locally on your workstations or laptops so it will be protected by the local backups first.
We also provide business level backups of your entire organization and we can do it on a monthly, quarterly or annual basis so you can snapshot your mail and keep it here or off site in a safe deposit box on a portable USB hard drive. We can even automate the process by keeping this information on BDR systems in our data center.
There is also an option for Compliance Archiving – we can store up to 10 years of email and have it available for immediate search without additional devices or appliances. It’s just another service available to protect your data.
To be honest, the concept of backups worked in the old days where organizations had small servers or single instance storage with a single RAID – cloud deployments are scalable, using multiple servers with DAG that keeps copies of the data in multiple locations. Because these systems are built for scale they offer more flexibility and more data copies – but we can certainly help you sleep easier at night by providing these additional services that make sense if you’re not so sure about the cloud.
What about security? I hear the cloud is hacked a lot! I have compliance to worry about as well.
The threat of having your security compromised is real regardless of where your Exchange is. One thing you can be sure of is that providing the level of monitoring and security layers available in the cloud would make an office server solution very expensive. ExchangeDefender provides stated Security Procedures document, Data Destruction Document, is SSAE 16 certified and undergoes multiple security audits every year – how about your IT employee?
We already mentioned Compliance Archiving, the system that gives you realtime access to 10 years of your email, where you can quickly locate any inbound, outbound and even interoffice email that matches search criteria. If you have HIPAA concerns, ExchangeDefender will sign a Business Associate Agreement (BAA) so you’re covered and have full access to your mail without worrying if it has been tampered with by the IT staff.
Security is really a matter of monitoring, technology and user awareness. ExchangeDefender has a lot more resources and higher end firewalls and DDoS protection service to address security problems when they pop up, patch the systems quickly because it can offline redundant servers, filter suspicious traffic and more that we cannot do affordably for you in the office. But what we can do is implement requirements for password rotation, we can deploy RSA SecurID for one-time passwords, we can monitor usage patterns and more.
Summary
Sometimes it’s hard for people stuck in the old model of IT to quickly accept how change has provided for better solutions to old IT problems. The key to a successful client relationship and a sale is not to argue some preconceived notions about IT but to explain the advances in technology and all the better stuff they will get from the cloud.
While everything about technology can be debated endlessly by the tech world, technical implementation to suit business has been taken out of the clutches of IT departments and placed into control of executives who have a more practical view of technology. Try asking two IT people: “What’s the best way to backup data” and see how many answers you get. Asking an executive will get you a different, more practical answer: We need to be able to continue work as usual within X hours but we need to have access to Y years of data in case of an audit.
ExchangeDefender and our partners are constantly evolving the best technology and the best local people around the world to solve these IT problems. Sometimes starting the conversation and framing it in a way to explain the advancement we’ve had in the past two decades when it comes to email is more difficult than just providing the solution. We hope this helps and if you need more info please do not hesitate to contact us.
Sincerely,
Vlad Mazek
CEO, ExchangeDefender
ExchangeDefender Reputation Scoring
When you send an email through ExchangeDefender it is checked for the presence of viruses, malware, SPAM and other dangerous content. It is our responsibility to make sure that the mail crossing the network, both in and out, is safe and that we are notcontributing to the flood of junk across the Internet. This is the story of our outbound network and it’s working great.
We also have another network, outbound-jr (affectionately nicknamed junk relay) where the rules are a little more relaxed. Some organizations have business case scenarios thatrequire them to send out null sender messages (maintenance, bounces, oof replies), some like to send bounces, some have massive email notification systems (RMM, transactions, etc) and they are on the line of legitimate andjunk mail as a choice. Since junk classification is handled by computers, (not humans), sometimes-legitimate mail is not being accepted for delivery.
A change that we are considering implementing, is a stricter set of monitoring and access restriction controls on outbound-jr. The first of these is a restriction on open SMTP ports, which often contributes to open relay mass mailings. This can be accomplished by rolling out a service that will deny access to outbound-jr if a client’s port 25 is accessible from the Internet (outside of the ExchangeDefender network). Traditionally this has been managed by IT departments and partners, but with a constant barrage of overly aggressive SPAM methods, the ability for most to manage this without security threats or incidents is an overwhelming issue.
To counter these threats and provide the most effective and best solution possible for our partners, we are soliciting feedback and beginning the alerting process to clients that have port 25 open without IP restrictions to the ExchangeDefender network. If there are no major objections to enforcing IP restrictions to port 25 (after all, if you have external client that requires SMTP relay access they can always use the SSL port) then we are considering adding this as a service requirement.
Thoughts? Opinions? Let us know via phone, chat, support tickets or just email me at vlad@ownwebnow.com
Sincerely,
Vlad Mazek, MCSE
CEO, Own Web Now Corp
ExchangeDefender Service Check
Although I can’t talk about our major initiative until the webinar next week, we have a ton of new stuff we’re developing on the backend to make your life easier. First of many that I have the pleasure of announcing is the ExchangeDefender Validation Wizard:
ExchangeDefender Validation Wizard gives you the ability to eliminate/isolate problems on the ExchangeDefender network through the same process our team uses and through the same systems our engineers rely on. The beta is available at: http://www.exchangedefender.com/check.php
Simply plug in the mailbox email and password and our wizard will troubleshoot things end to end and line up with our best practices:
Validation Wizard
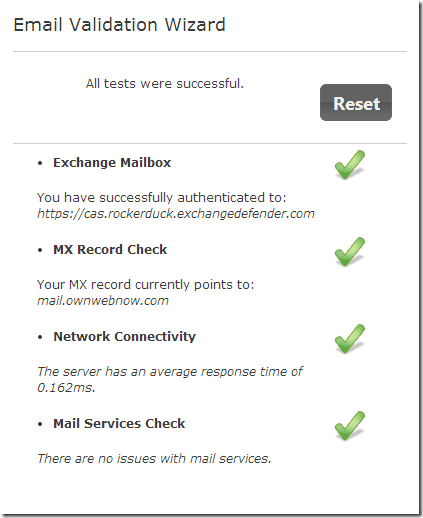 What the wizard actually does is even more important to understand: this is not some simple database field validation tool. It actually opens connections to the live backend servers, tests connections, looks up DNS records and does everything that technicians typically do by hand.
What the wizard actually does is even more important to understand: this is not some simple database field validation tool. It actually opens connections to the live backend servers, tests connections, looks up DNS records and does everything that technicians typically do by hand.
Exchange Mailbox: Wizard will first check the password and authentication credentials against the live CAS server. If this check fails it means you have the wrong email/password combo. Please note that this check validates the actual connection, not what is in the control panel. If your user went around you and reset their password via OWA then just remember the best practice to reset it right back to something you can support.
MX Record Check: After the mailbox is verified as live and online, system will check the DNS for the correct MX and Autodiscover records. This is particularly useful in the mail troubleshooting process when email delays and missing emails are a problem. Clients tend to have incorrect, missing or external MX records in their delivery list and more often than not this is the culprit to missing and delayed email. Every now and then we also find that the domain record registration had expired (and as it’s the last thing we ever check it’s among the most frustrating)
Network Connectivity: As the test implies, we check the connectivity to clients CAS, HUB and Mbox server to check on the backend and identify any potential bottlenecks that could be affecting connectivity.
Mail Services Check: The extension of the network test, in which we go through all the web, SMTP, IMAP, POP3, CAS and MAPI services to make sure the clients mailbox is setup correctly, mail flows as it should and there aren’t any “weird” issues on the backend such as a mailbox that is locked out, over quota, possessed by email gremlins and so on.
Piece of a Proactive Puzzle
As you can tell, we are putting more and more pieces together that allow us to deliver a truly managed service throughout the cloud. Typical cloud service checks verify that the servers are online and functioning but the truth is that there are typically dozens of servers and multiple data centers involved in service delivery and the transparency to the backend can at times make it impossible for a third party to effectively troubleshoot the service.
By extending the access of our backend into your hands we feel we can deliver powerful functionality in a very easy to use and manage tool set. Even though PowerShell access is available, we find it that few have the capability to rely on it and every time you have to do something manually through PowerShell you will waste more time than you expected. Not to mention that the testing has to be layered in order to make sense.
Our business model calls for us to further simplify and eliminate the hassle of email issues. By transferring these complex, procedural and often poorly documented best practice and troubleshooting sets to a simple, easy to use and cleanly presented service we can eliminate a huge cost and open up our portfolio to delivering managed mail services that are not conditional on the infrastructure problems.
I certainly look forward to sharing everything we’re up to here but I think you can agree that it helps when we’re on the same page ![]()
Sincerely,
Vlad Mazek, MCSE
CEO, Own Web Now Corp
vlad@ownwebnow.com
(407) 536-VLAD
Shockey Monkey launches native app for Android phones & tablets
We are proud to announce that Shockey Monkey is now available for download on your Android device. This app does require Android version 4.0 and higher in order to install and take advantage of its great features. Now you can take your service desk with you on the road and never again be stranded without knowing exactly what support issues await your arrival.
Google Play Link – Shockey Monkey
We’ve taken the feedback from our previously release BETA that was published to the iPad to enhance this experience. The Shockey Monkey app now supports background synchronization, so you are no longer stuck sitting and watching a loading screen for long periods of time. You also now have complete control over your companies & contacts, with the ability to dial them from the application.
We’ve implemented an advanced synchronization module that will feed information efficiently and provide you with more accurate and up to date information. You have access to all of your open tickets within your portal and can easily navigate, update and retrieve critical information from these tickets. This become critical when you are on the road and forget your job details or new jobs come in within a moment’s notice!
We also have more good news!
We are so pleased with the outcome of this new app, that we are pushing the changes onto the Apple iOS version as well. We have already finished the iPhone port and are making the updates to the iPad app currently. We hope that by the end of the month both of these new mobile apps will be available via the iTunes and you can take Shockey Monkey anywhere your job takes you!
Hank Newman
The Truth About Cloud Services
If you attended our last webinar (will be posted for download in our portal next week) you already know what I’m going to say: Winning in the cloud has nothing to do with technology and everything to do with good customer service. The technology of implementation, scalability, redundancy, system capacity and long term legacy use are terms both distant and hard to differentiate for most clients from SMB to enterprise: If you meet their compliance requirements the question of whether you will make money in the cloud or not depends solely on your ability to set the correct expectations and deliver the non-IT part of the service effectively.
Good news is that we are here to help!
But is it smug to believe that you actually need help? When we talked to our partners about cloud adoption the answer surprised even us: not at all and to be honest we’d rather have our weekends back. Truth behind cloud deployments is that the up front investment in time and planning is expensive, messy and clients do not like downtime – forcing IT Solution Providers to execute complex migrations over weekends, holidays and provide ongoing support for unpredictable surprises that always come up.
Truth about the cloud is that the deployment of a cloud solution is 1% technology, 99% proper project management and customer communication. It’s the 99% of the prep work and followup that is keeping most solution providers from seriously taking advantage of the cloud solutions because without help the ability to scale to the cloud is the same as the ability to scale to another inhouse solution.
Over the next two weeks ExchangeDefender is dedicating significant resources to help you navigate what we’re internally calling Napalm Cloud – rapid fire cloud service deployments for Exchange, SharePoint, Lync, ExchangeDefender, LocalCloud, LiveArchive and all the project management, communication and service that goes along with it.
We will be posting several articles, blogs, webinars and guides that we use at ExchangeDefender to deliver our Managed Messaging service in hopes of giving you an idea of how these projects happen consistently, successfully and with a great deal of client satisfaction.
I hope you join us as we discuss these topics because they are of a great importance to your success and profits in the cloud. Money in the cloud will not be made on subscription revenues, the “free” model has effectively assured that, so the greatest opportunity for solution providers is in providing a peace of mind and predictability when it comes to technology – today, tomorrow and years from now.
Can you say that you deliver that? Hopefully over the next two weeks we’ll help you get closer to yes.
Sincerely,
Vlad Mazek, MCSE
CEO, Own Web Now Corp
(877) 546-0316 x500