Top 5 IT Problems Small Businesses Face in 2025 — and How to Fix Them

Small businesses are more tech-enabled than ever — but that doesn’t mean the road is smooth. Between rising cyber threats, hybrid work headaches, and the pressure to adopt AI, SMBs are under serious digital strain.
Let’s unpack the top five IT problems small businesses face in 2025, why they matter, and what you can do to stay ahead.
1. Cybersecurity Threats: The Ever-Growing Risk
Why it’s a problem
Cybercriminals know that small businesses often lack the deep defenses of larger enterprises. According to a StrongDM study, 75 % of SMBs say they couldn’t continue operating if hit by ransomware. (strongdm.com)
Add to that the explosion of phishing and social-engineering campaigns targeting remote workers, and it’s a perfect storm.
What makes it worse
- Many SMBs lack dedicated budgets or in-house security expertise.
- Breaches now cost small firms an average of $1.3 million in downtime, recovery, and lost revenue. (verizon.com)
What to do about it
- Enable multi-factor authentication (MFA) on all critical systems.
- Conduct regular security awareness training.
- Keep endpoint protection and backups up-to-date.
- Partner with a managed security provider (MSSP).
- Draft and test an incident-response plan.
2. Hybrid & Remote Work Infrastructure Challenges
Why it’s a problem
The shift to hybrid and remote work forced small businesses to rebuild operations overnight. Many discovered that their infrastructure simply wasn’t ready.
- 46 % of IT leaders said their cybersecurity posture weakened due to hybrid and remote setups in 2025. (sqmagazine.co.uk)
- SMBs report struggling with connectivity, remote device management, and endpoint security. (teamwork.com)
What makes it worse
- Home networks lack corporate-grade firewalls.
- IT teams are stretched thin handling remote troubleshooting.
- Employees use personal devices or shadow-IT tools that bypass policy.
What to do about it
- Standardize devices or enforce minimum security baselines.
- Deploy mobile device management (MDM) and endpoint-monitoring tools.
- Use VPNs or adopt a zero-trust network model.
- Train remote employees on safe digital practices.
- Monitor remote endpoints continuously for unusual activity.
3. The Talent Shortage & Skills Gap
Why it’s a problem
The global IT skills gap is hitting small businesses hardest. Many can’t compete with enterprise salaries or recruitment budgets. A 2025 survey found talent retention and acquisition among the top 3 SMB IT challenges. (teamwork.com)
What makes it worse
- High turnover drains institutional knowledge.
- IT generalists are overextended.
- Lack of specialists means slower adoption of new tech and higher risk.
What to do about it
- Outsource key functions like cybersecurity or cloud management.
- Invest in ongoing training and certifications for existing staff.
- Build a retention culture — flexible work, recognition, and growth.
- Automate repetitive tasks to reduce workload.
- Document all processes to preserve knowledge continuity.
4. Legacy Technology & Integration Headaches
Why it’s a problem
Many small businesses still rely on outdated software or hardware, which creates performance and compatibility problems.
What makes it worse
- End-of-life systems stop receiving security updates.
- Old software doesn’t integrate with modern cloud tools.
- Employees waste hours on manual or redundant workflows.
What to do about it
- Conduct a full tech inventory — list every device, OS, and license.
- Prioritize upgrades for mission-critical systems.
- Use integration platforms (APIs, iPaaS) to bridge new and old.
- Plan phased cloud migrations.
- Maintain a 12-24 month modernization roadmap.
5. Keeping Up with Cloud, AI & Automation
Why it’s a problem
AI, automation, and advanced cloud services promise efficiency — but they also overwhelm small teams. Many SMBs say they want to use AI but lack the training and data readiness to implement it effectively. (techradar.com)
What makes it worse
- Rapid vendor changes confuse decision-makers.
- AI and automation rely on secure, structured data.
- Many small firms lack governance policies or pilot frameworks.
What to do about it
- Start small — pick one clear process to automate.
- Tie every tech initiative to a measurable business goal.
- Focus on data hygiene before deploying AI.
- Upskill your staff with AI-readiness workshops.
- Measure ROI quarterly — what saves time, reduces errors, or adds value?
2025 is the year small businesses either double-down on digital resilience — or risk getting left behind. The right mix of security, modernization, and smart partnerships will determine which side your business lands on.
Need help strengthening your IT defense? ExchangeDefender can help you protect data, empower remote teams, and modernize securely.
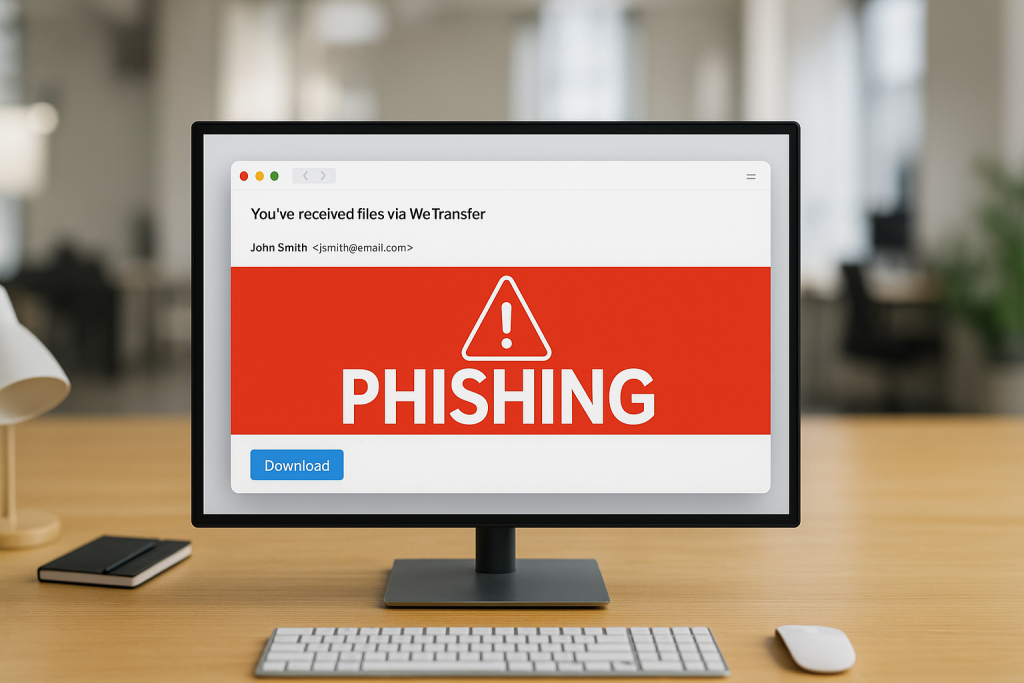
Hackers Use Fake WeTransfer Emails to Steal Your Information
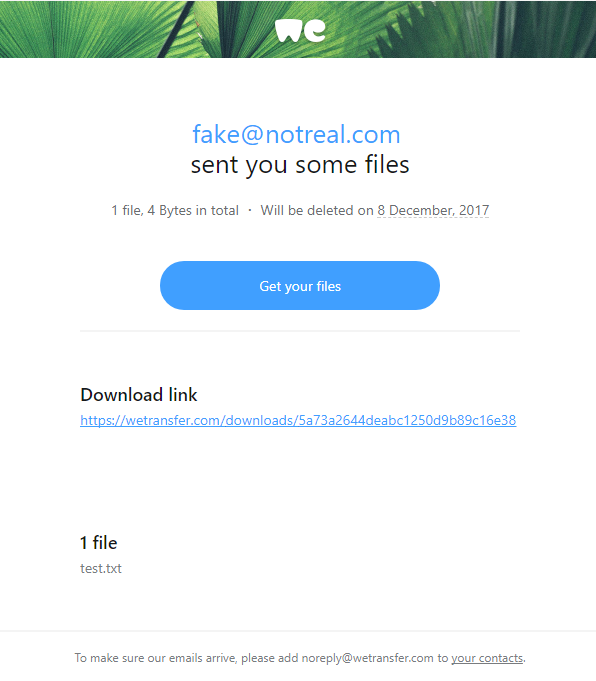
If you’ve ever shared a big file online, chances are you’ve used WeTransfer. It’s quick, it’s easy, and most importantly—it’s trusted. And that’s exactly why scammers love it.
Lately, there’s been a wave of phishing emails that look like they’re coming from WeTransfer. You get a message in your inbox saying something like:
- “You’ve received files”
- “Here’s your invoice via WeTransfer”
- “Download your contract now”
Sounds legit, right? The problem is, those links don’t actually take you to WeTransfer. Instead, they lead you to sketchy sites designed to steal your email login, personal info, or even infect your computer with malware.
Fordham Edu
https://medium.com/@resonance.security
So, how do you spot a fake?
Here are some quick red flags:
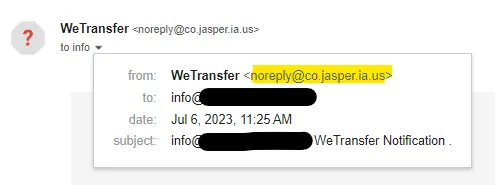
- Check the sender’s address. Real WeTransfer emails come from
@wetransfer.com. Anything else? 🚩 - Hover over the link. If the URL doesn’t point to
wetransfer.comorwe.tl, don’t click. - Unexpected transfers. If you weren’t expecting files, especially invoices or contracts, double-check with the sender.
- Scare tactics. If the message pressures you with “download immediately” or “expires in 1 hour,” take a breath. That urgency is a classic trick.
- Attachments. WeTransfer usually gives you a download link, not random attachments with .zip or .exe files.
What’s at risk if you fall for it?
A lot, unfortunately. Clicking on a fake transfer can mean:
- Your email or cloud account gets hacked.
- Sensitive data leaks into the wrong hands.
- Your device gets hit with malware (worst case: ransomware).
How to protect yourself
The good news? Staying safe is pretty simple:
- Verify before you click. If someone says they sent you files, confirm with them outside of email (call, text, Teams, Slack—whatever you use).
- Turn on MFA. Multi-factor authentication makes it way harder for scammers to break into your accounts.
- Keep your guard up. Train yourself (and your team, if you’re running a business) to spot phishing tactics.
- Update your devices. Security patches and antivirus tools help catch threats before they cause real damage.
How ExchangeDefender Helps
Here at ExchangeDefender, we take phishing attacks like these seriously. Our filters flag suspicious links, block spoofed domains, and keep bad emails out of your inbox before you even have to think about them. Plus, we love keeping you in the loop with updates like this—because knowledge is one of the best defenses.
Our Expert Tip:
WeTransfer is a great tool, but remember: scammers always follow trust. The more popular a platform is, the more likely it’s going to be abused. So next time you see that “You’ve received files” email—pause, hover, and think before you click.
Sources
What Happens After a Cyber-Attack? The Real Cost for Small Businesses

Let’s face it—most small businesses don’t wake up thinking today will be the day they get hacked. But when it happens, the impact can be swift, serious, and long-lasting.
A small business has suffered from a cyber-attack—what could be the resultant damage?
Spoiler: It’s a lot more than just a locked computer screen.
Let’s break it down in plain English.
Financial Fallout
Hackers love going after small businesses because defenses are often weaker—and payouts can still be big.
- Ransomware may demand thousands just to give back access to your files.
- Phishing or business email compromise could lead to fraudulent money transfers.
- Remediation costs (forensic investigation, legal help, software cleanup) stack up fast.
And while you’re fixing all that…
Time Is Money—And You’ll Lose Both
Most small teams rely on a few key systems to keep things moving. When those go down, so does your ability to do business. Orders get delayed. Calls go unanswered. Work comes to a screeching halt. And while the tech side gets untangled, your customers? They’re already wondering what’s going on.
You might be offline for hours. Maybe days. Either way, your clients won’t wait forever.
It Gets Personal Fast
A lot of cyberattacks aren’t just about locking up files—they’re about stealing data. That could mean employee records, customer information, payment details, contracts, or anything else sensitive. If that data ends up exposed, you may have to notify everyone affected. In some industries, that’s not just a courtesy—it’s the law.
And if clients lose trust? That can cost far more than any ransom demand.
The Recovery Isn’t Just Technical
Once the threat is handled (and your blood pressure returns to normal), you still have to deal with the cleanup. That might mean replacing devices, hiring an expert to audit your systems, redoing your cybersecurity setup, or retraining your team.
The worst part? This whole situation was probably preventable.
You Don’t Need an IT Department to Be Protected
Most small businesses don’t have a dedicated IT team—and that’s exactly why hackers love targeting them. They count on people being too busy, too stretched, or just unaware of the risks.
That’s where we come in.
ExchangeDefender is built for teams like yours—small, mighty, and ready to protect what matters. From secure file sharing to bulletproof email protection, we make cybersecurity simple, affordable, and human.
How to Spot and Avoid Geek Squad Email Scams
In recent years, scammers have increasingly impersonated Geek Squad, Best Buy’s tech support service, to deceive individuals into divulging personal information or making unnecessary payments. Understanding how these scams operate and how to recognize them is crucial for safeguarding your personal data and finances.
Understanding the Geek Squad Email Scam
The Geek Squad email scam is a phishing attempt where fraudsters pose as Geek Squad representatives to steal personal information or trick victims into paying for fake services. These emails often appear legitimate, making it challenging to distinguish them from authentic communications.
Common Types of Geek Squad Email Scams
- Auto-Renewal Scam: Scammers send emails stating that your Geek Squad subscription is about to auto-renew at a substantial cost. The email urges you to call a provided number or click a link to cancel the subscription, aiming to extract personal and financial details.
- Fake Antivirus Software Offer: You might receive emails warning of malware infections among Geek Squad customers, offering free antivirus software downloads. However, these downloads are malicious and designed to infect your device, steal data, or gain remote access.
- Password Reset Scam: Emails claim suspicious activity on your Best Buy account, prompting you to reset your password via a provided link. The link leads to a fake website designed to capture your login credentials, allowing scammers unauthorized access to your account.
Recognizing Scam Emails
Be vigilant for the following signs:
- Sense of Urgency: Scammers often pressure you to act quickly, creating a false sense of urgency.
- Suspicious Sender Addresses: Examine the sender’s email address for inconsistencies or misspellings. Official communications will come from a legitimate Best Buy domain.
- Generic Greetings: Emails that don’t address you by name, such as “Dear Customer,” may be fraudulent.
- Poor Grammar and Spelling: Legitimate companies maintain professional communication standards.
- Unsolicited Attachments or Links: Avoid clicking on links or downloading attachments from unknown senders.
Protective Measures
- Verify Communications: If you receive a suspicious email, contact Geek Squad or Best Buy directly using official contact information from their website.
- Avoid Unsolicited Links and Downloads: Refrain from clicking on links or downloading attachments from unknown sources.
- Use Security Software: Ensure your devices are equipped with reputable antivirus and anti-malware programs.
- Stay Informed: Educate yourself about common phishing tactics to recognize and avoid potential scams.
Reporting Scams: If you encounter a Geek Squad scam, report it to Best Buy. Additionally, file a complaint with the Federal Trade Commission (FTC) through their Complaint Assistant.
Avoid Netflix Payment Scams: Recognize Phishing Emails
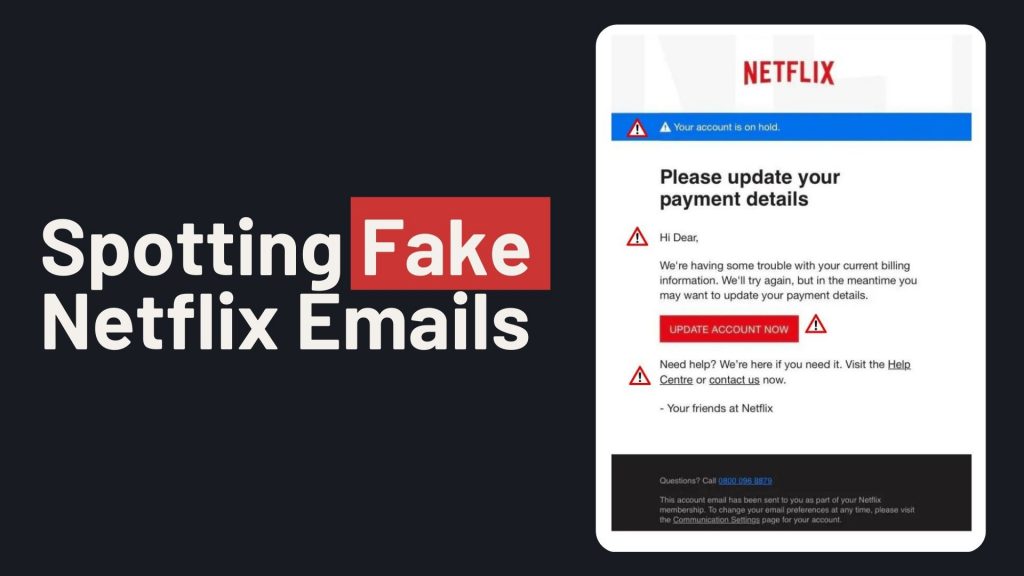
In recent months, a sophisticated email scam targeting Netflix users has emerged, aiming to steal personal and financial information. These phishing emails closely mimic legitimate Netflix communications, making them particularly deceptive. If you don’t have ExchangeDefender PRO Phishing protection, then here’s what you need to know:
How the Scam Operates
Victims receive emails claiming issues with their Netflix account, such as payment problems or account suspensions. The email urges recipients to update their payment details via a provided link, which leads to a fake Netflix login page. Entering information on this page allows scammers to harvest login credentials and credit card details.
Identifying the Scam
- Sender’s Email Address: Scam emails may originate from unofficial domains, such as an iCloud domain, rather than Netflix’s official domain.
- Urgent Language: The message may claim your account is on hold and prompt immediate action to update payment information.
- Suspicious Links: Hovering over links may reveal URLs that don’t direct to Netflix’s official website.
Protective Measures
- Avoid Clicking Links: Do not click on links or open attachments from unsolicited emails.
- Verify Authenticity: Log in directly through the official Netflix website to check your account status.
- Report Suspicious Emails: Forward any dubious emails to phishing@netflix.com.
- Monitor Financial Statements: Regularly check your bank and credit card statements for unauthorized transactions.
Netflix’s Official Stance
Netflix states it will never ask for personal information, such as credit card numbers or passwords, via email or text messages. By staying vigilant and recognizing the signs of phishing attempts, you can protect your personal and financial information from these scams.
Texas Strengthens Cybersecurity with New State-Level Command Center

In February 2025, Texas Governor Greg Abbott announced the creation of the Texas Cyber Command, a state-level initiative headquartered in San Antonio.
This command center aims to enhance the state’s ability to anticipate, detect, and prevent cyberattacks, leveraging local expertise from institutions like The University of Texas at San Antonio. The Texas Cyber Command will collaborate with state universities, Regional Security Operation Centers, and various local and state agencies to create a unified defense against cyber threats.
Key objectives include promoting cybersecurity awareness, conducting simulation exercises, and providing forensic analysis for post-attack investigations. This development underscores the growing importance of state-level initiatives in safeguarding digital assets and infrastructure.
For a visual overview of the Texas Cyber Command, you can watch the following video:
ExchangeDefender Web Services Update

ExchangeDefender Web Services Update has concluded and the new infrastructure is handling 100% of the ExchangeDefender traffic. So far the new platform is performing exactly as expected and we have already closed several minor bugs. Overall, we are extremely happy at ExchangeDefender today!
We want to take a moment to high-five ourselves and highlight three main areas where our clients and partners are going to benefit from this investment:
1. Enhanced Security
With the changes in the development backend, our platform now utilizes the latest security patches and modern language features, significantly reducing vulnerabilities and providing a more robust threat defense.
Our old platform was also rock-solid in terms of performance and security, but that secure-by-design methodology forced us to reverse-engineer as well as design and manage everything from input validation to report routing. Modern web services take care of these routine things allowing us to spend more time on policy development.
2. Improved Performance
The new infrastructure supports faster processing and is optimized for global operations allowing us to deliver a more responsive and reliable service.
You’ve already seen a hint of this in the ExchangeDefender LiveArchive relaunch as a standalone data vault for cloud operations. By breaking up our infrastructure into microservices we’re able to deliver edge operations closer to where our clients are, we can keep data more securely in your local data geography, and we can delegate away control as required.
3. Features Shipped Faster
By moving away from legacy code and internal systems/plugins for policy and protocol enforcement, we can dedicate more of our development cycles to policies and training that will keep your organization more secure. You will be able to benefit from the latest improvements and security innovations while we deliver more.
Thank you for filling out our survey, if you haven’t done so please take a moment to tell us where we can help. We have intentionally dedicated a large window to bringing the new web service infrastructure online so we do have spare cycles to help alleviate some pain points our clients are experiencing. Please take a moment to fill out our survey
We are hard at work on the new User Interface, we’re nearly ready for the public launch of our Phishing platform, all sorts of goodies are heading your way so once again – thank you for your business and your faith in us to deliver safe and secure email to your organization.
Sincerely, Vlad Mazek CEO ExchangeDefender
Pretexting Scams Explained: How to Protect Your Personal Information

Pretexting is a type of fraud where scammers create a false scenario or identity to trick you into revealing personal information. This information can then be used for identity theft, financial fraud, or other malicious purposes.

How Does Pretexting Work?
Scammers often employ a variety of tactics to gain your trust. Here are some common examples of pretexting:
- Impersonation: Scammers may pretend to be government officials, law enforcement officers, bank employees, or even family members to gain your confidence.
- Phishing: This involves sending fraudulent emails or text messages that appear to be from legitimate companies, urging you to click on links or provide personal information.
- Social engineering: Scammers use psychological manipulation techniques to exploit your emotions or curiosity.

Common Pretexting Scams
- Government Imposter Scams: Scammers posing as IRS or Social Security Administration agents may threaten legal action if you don’t provide personal information or make immediate payments.
- Tech Support Scams: Fraudsters claim to be from tech companies and offer to fix non-existent computer problems for a fee.
- Grandparent Scams: Scammers pretend to be grandchildren in distress, requesting money urgently.
- Romance Scams: These involve building fake online relationships to gain trust and then requesting financial assistance.

Protecting Yourself from Pretexting Scams
- Be Wary of Unsolicited Contact: Avoid sharing personal information with anyone who contacts you unexpectedly.
- Verify Information: If you receive a suspicious call or email, independently verify the sender’s identity before providing any information.
- Protect Your Personal Information: Be cautious about sharing sensitive details online or over the phone.
- Use Strong Passwords: Create complex passwords for your online accounts and consider using a password manager.
- Monitor Your Financial Accounts: Regularly review your bank and credit card statements for unauthorized activity.
Remember, legitimate businesses and government agencies will never ask for personal information through unsolicited calls, emails, or texts. If you suspect a scam, hang up or delete the message, and report it to the appropriate authorities. By staying informed and vigilant, you can protect yourself from becoming a victim of pretexting.
Preparing for LiveArchive Retirement

As mentioned on our recent webinars and blog posts, LiveArchive has worked very hard for us for decades and it’s time for it to go to Florida and retire.
The new kid on the block – ExchangeDefender Inbox – has been running our client’s business continuity for over a year and it’s proven to be more efficient and popular than LiveArchive. Just log in to your account (https://admin.exchangedefender.com) or use passwordless login and click on Inbox. You’ll have the last two weeks of email waiting for you there and you can send/receive while your email server/mailbox/or whatever is down or under maintenance.
Longer Term Archiving
While Inbox will take care of our clients’ email needs when their email is having issues, many of you need long-term archiving. If LiveArchive was ever power-used it would be in the realm of data recovery after a disaster, cryptolocker, or other threat destroyed the client’s email infrastructure. For those of you who are aware of the risk, there will be a need for archiving to go way beyond two weeks – even years. This is what the new LiveArchive will start doing for you on January 1st, 2024!
First, let’s get ready for the retirement of the current LiveArchive – the service will shut off on December 31st, 2023 at which point all data including backups and configurations will be removed from our network. This means that if you wish to keep current LiveArchive contents the migration request must be put in as a ticket at our support site at https://support.exchangedefender.com. Simply open a ticket with the subject “LiveArchive Migration” and provide the domain names you wish to migrate and the S3/RDS login credentials by December 1st, 2023. As promised on the webinar, we are offering this migration free of charge to our clients and partners but you need to get in the line by December 1st and have your AWS S3/RDS or self-hosted setup completed.
Second, if you need any help with AWS S3/RDS or if you’d like assistance with deploying this solution in your home office or data center, we got you too. If you need help and get in touch with us by December 1st, we’ll take care of it for you. It’s super simple, takes about 5 minutes total, and is extensively documented – but we love our clients and if you want an extra pair of hands we can help you. After December 1st (and depending on availability) we will take care of the setup for a one-time fee of $499 for AWS or $999 for self-hosted.
Future of LiveArchive
We look forward to this middle tier that every organization that relies on email to run their business needs. For business continuity, Inbox will give you access to email anywhere, anytime. For backups and long-term retention across various clouds and storage options, LiveArchive will take care of archiving your data. For additional assurance and best-in-class storage that meets complex compliance and insurance requirements, ComplianceArchive is your eDiscovery and compliance archiving solution. Simply put no matter how critical email is to your organization we’ve got a solution that fits your problems and your budget.
The new LiveArchive will start doing for you on January 1st, 2024!
Looking for beta testers: “Project Inbox”
We would like to invite our clients, partners, and enterprise users to a closed beta of Project: Inbox – an affordable email solution that can be used as a standalone solution or in hybrid mode with M365 and G Suite.
If you are interested, please email client.services@exchangedefender.com along with a domain name you will be using for the beta test.
Our CEO recently held a webinar explaining the strategy behind this new service and it has been evolving ever since based on market feedback. Simply put, there is a huge market for affordable mailboxes that still meet the high end security and business requirements like top of the line email security, SSO, IMAP/Outlook/Mobile access, and still use the same domain name as the more expensive Exchange or Gmail office suites.
For an overwhelming majority of users within larger organizations, email is an absolute necessity but the average cost of $150/year/employee is putting a strain on IT budgets. Furthermore, the projected slowdown in the economy will make our clients more cautious about their IT spending. Our models show a trend of more users being mobile-first (with remote work being mobile-only) and a growth of service-related mailboxes is creating an opportunity to help us improve our clients security while reducing their service bill.
If this sounds like a winning opportunity for your business or your clients we hope you’ll join us in building something new and awesome. Those that help us out will enjoy the service for free for a while but we have a limited number of spots depending on industry and seat count so if you’re even remotely interested please email us as soon as possible.