Why Email Security Isn’t Optional Anymore (Even for Small Businesses)

Once upon a time, email security was something only big corporations worried about—firewalls, encryption, threat detection… it all sounded like enterprise stuff.
But those days? Long gone.
If your business has an email address (and let’s be honest, who doesn’t?), you’re already a target. And the bad guys? They’re counting on you thinking security is “someone else’s problem.”
Let’s break down why email security is no longer optional—especially for small businesses.
1. Small Businesses Are Easy Targets
Cybercriminals know that smaller companies don’t always have the time, money, or resources to invest in advanced security tools. That’s exactly why they get hit more often.
Think of it this way: would a burglar go after Fort Knox… or the house with the front door wide open?
2. Phishing Scams Are Smarter (and Meaner)
Today’s phishing emails don’t look like Nigerian prince spam. They’re clean. Branded. Personalized.
They might come from what looks like your vendor, your CEO, or even your bank.
They want you to click the link, download the invoice, or reset your password.
And they’re sneaky good at it.
That’s why real-time threat detection and phishing filters are essential—not just “nice to have.”
3. Email Holds the Keys to Your Business
Think about it: your inbox is a treasure chest of…
- Client communications
- Invoices and payment links
- Internal documents
- Credentials and logins
- Contracts, quotes, and private notes
If someone gains access to your email, they don’t just read your messages—they own your business operations. And the recovery costs (both financially and reputation-wise) are brutal.

4. The Cost of NOT Securing Email Is Way Higher
Sure, tools like ExchangeDefender cost money. But do you know what costs more?
- Downtime
- Breach cleanup
- Legal fees
- Lost client trust
Email security is no longer a cost center—it’s a business continuity solution.
5. The Right Tools Make Security Simple
You don’t need to hire a team of security experts. ExchangeDefender helps small businesses stay protected with:
✅ Spam + phishing filters
✅ Email encryption
✅ Real-time malware scanning
✅ Quarantine reports + trusted sender controls
✅ Simulated phishing training
✅ 24/7 monitoring + support
It’s not just about defense—it’s about peace of mind.
Your email is your front door. Lock it.
Small business or not, today’s threats are real—and relentless. But with the right protection in place, you can focus on growing your business instead of chasing down security fires.
🔐 Want to see how ExchangeDefender can keep your email secure? Let’s talk.
Watch Out: New Norton LifeLock Phishing Scam Targets Inboxes Nationwide

Email scams are getting bolder, and the latest one impersonating Norton LifeLock is making waves across inboxes everywhere. If you or your clients have received a suspicious email about a Norton subscription renewal or refund, here’s what you need to know—and why it matters.
🚨 What the Scam Looks Like
This phishing campaign is cleverly designed to mimic official Norton communications. The email usually warns of a pending charge or a renewal for Norton LifeLock services you never signed up for. Some versions say the charge is already complete, encouraging panic.
It may include:
- Official-looking logos and invoice PDFs
- Toll-free numbers to “cancel” the subscription
- Links that direct you to phishing pages
🤔 Why It Works
Scammers know how to create urgency. These emails often claim you’re being billed hundreds of dollars, prompting victims to call the provided number or click a cancellation link. Once on the phone, scammers may:
- Request remote access to your computer
- Ask for banking credentials to “process a refund”
- Install malware or steal sensitive data
🛡️ How to Protect Your Organization
ExchangeDefender recommends taking the following actions to stay safe:
- Never call phone numbers listed in suspicious emails
- Avoid clicking links or downloading attachments
- Report emails that look off – even if they seem to come from a known brand
- Enable 2FA wherever possible
If you’re using ExchangeDefender’s advanced phishing protection, our system is already working behind the scenes to stop these attacks before they hit your inbox.
MSPs, Take Note
This scam isn’t just a one-off – it’s part of a growing trend targeting businesses through brand impersonation. If you’re an MSP, we recommend sharing this post with clients and ensuring email continuity is part of your disaster recovery planning.
With ExchangeDefender’s LiveArchive, even if a phishing email triggers an outage or breach, business communication can continue seamlessly.
🔎 Learn More
Stay informed, stay secure. Read Norton’s official scam alert page here or contact ExchangeDefender support if you need help tightening your phishing defenses.
Have questions or want to beef up your email security stack? Try ExchangeDefender PRO! Contact us today.
Stay safe out there!
ExchangeDefender — Email Security, Backup & Continuity Built for Business.
Top 5 Email Threats You Didn’t Know Were Hiding in Your Inbox

Let’s face it—email is the lifeblood of modern business. But behind every “urgent” subject line or familiar sender name, there could be something much more sinister lurking. At ExchangeDefender, we spend our days defending inboxes against threats most people don’t even know exist. So today, we’re spilling the secrets. Here are 5 sneaky email threats that could be hiding in plain sight:
1. Lookalike Domains (a.k.a. Evil Twins)

These emails come from addresses that look legit—maybe a single letter off from your CEO’s real email, or a domain that’s cleverly misspelled.
Why it’s dangerous: They’re made to trick you into clicking links or wiring money.
How we stop it: ExchangeDefender uses advanced domain and sender verification to block imposters fast.
2. Zero-Day Attachments
These are brand-new threats that haven’t even made it to antivirus databases yet. They come disguised as invoices, resumes, or project files.
Why it’s dangerous: Traditional filters might miss them.
How we stop it: Real-time scanning and sandboxing help catch unknown threats before you open them.
3. Credential Harvesting Links
Not all phishing scams are loud and obvious. Some hide in the form of password reset requests or shared documents.
Why it’s dangerous: One click can expose your login—and open the door to your entire system.
How we stop it: Link analysis and real-time URL scanning keep you protected, even from shortened or masked links.
4. Conversation Hijacking
Hackers insert themselves into real email threads and respond like they’re part of your team. Creepy, right?
Why it’s dangerous: You’re more likely to trust something that feels familiar.
How we stop it: Behavioral monitoring flags unusual responses—even when they happen mid-thread.
5. Impersonation of Internal Staff
Ever get a weird request from “Accounting” or “HR”? Sometimes, attackers mimic your internal teams to request sensitive info or payments.
Why it’s dangerous: These attacks rely on trust and internal knowledge.
How we stop it: ExchangeDefender uses AI and policy enforcement to detect when internal communication doesn’t add up.
So, What Can You Do?
Well, you already did the first step: you’re here. 🧠👏
The next step? Put a solution like ExchangeDefender Email Security between your team and the bad guys. We’re built to detect, block, and neutralize all of these threats—before they hit your inbox.
Because email should be for collaboration, not chaos.
👉 Learn more about how ExchangeDefender protects your business: https://exchangedefender.com/email-security
How the eBay Phishing Scam Works

The eBay phishing scam is a common cyberattack where scammers impersonate eBay to steal user credentials, financial details, or personal information. These scams often take the form of fake emails, text messages, or websites designed to trick users into providing sensitive information.
In eBay phishing scams, attackers send counterfeit emails or messages that appear to originate from eBay. These communications often contain urgent prompts, such as warnings about account issues or unauthorized transactions, compelling recipients to click on malicious links. These links lead to fake websites resembling eBay’s login page, where users are tricked into entering their credentials. Once obtained, cybercriminals can exploit this information for fraudulent activities, including unauthorized purchases or identity theft.

Red Flags to Watch Out For:
🚨 Generic Greetings – Legitimate eBay emails usually address you by name. Look for fake logos!
🚨 Suspicious Links – Hover over links before clicking—real eBay links should start with “ebay.com.”
🚨 Poor Grammar & Spelling – Many phishing emails have obvious errors. Look for fake phone numbers!
🚨 Requests for Personal Info – eBay never asks for passwords, payment info, or security details via email.
How to Protect Yourself:
✅ Enable Two-Factor Authentication (2FA) for extra security.
✅ Go Directly to eBay – Instead of clicking links, log in at eBay.com.
✅ Report Suspicious Emails to eBay at spoof@ebay.com.
✅ Use Strong, Unique Passwords – Avoid reusing your eBay password on other sites.
Mitigating Phishing Risks with ExchangeDefender PRO
To safeguard against such evolving threats, businesses require robust cybersecurity solutions. ExchangeDefender PRO offers comprehensive email security designed to protect organizations from advanced email-borne attacks. Key features include:
Anti-Phishing Protection: Identifies and blocks phishing attempts, preventing unauthorized access to sensitive information.
Anti-Spam and Malware Defense: Filters out spam and detects malicious attachments, reducing the risk of malware infections.
Ransomware Protection: Guards against ransomware attacks that can encrypt critical business data.
Domain Fraud Prevention: Prevents spoofing and unauthorized use of your domain, protecting your brand’s integrity.
On-Demand Encryption: Ensures sensitive communications are securely encrypted, maintaining confidentiality.
Adding ExchangeDefender PRO to your cybersecurity setup can help protect your organization from phishing scams and other email threats. It’s a smart way to stay safe online and keep your business and relationships secure.
Upgrade Notice: Login Service Enhancements and Monitoring Improvements

Over the weekend, we designed, tested, and implemented new architectural solutions to address recent issues with the central login service for ExchangeDefender products. Additionally, we identified and began resolving a critical alerting issue that had prevented our NOC from receiving timely notifications about service outages.
To expedite improvements, we deployed a web cluster originally planned for a later release. This new cluster introduces advanced high-availability features, including self-healing capabilities and integration with modern, distributed monitoring solutions to ensure consistent global accessibility.
Given the scope of this upgrade, we opted for a phased rollout using A/B testing to ensure service reliability. Over the past three days, we’ve gradually increased traffic to the new cluster, starting at 12%, while monitoring server and load balancer performance metrics. Currently, 20% of traffic is routed through the new cluster, with the remaining 80% handled by the legacy system. In the event of a failure in either cluster, the load balancer will dynamically shift all traffic to the active system, even if a customer was initially pinned to the affected cluster.
Performance Improvements
The initial results have been highly encouraging, with noticeable performance gains. We’ve observed a 5x improvement in P95 latency and a 3x improvement in P99 latency compared to the previous setup.
Next Steps
Next weekend, we plan to implement the final phase of this upgrade, introducing automated transitions between data centers to address any performance or reliability issues proactively.
Addressing Notification System Failures
During our investigation, we identified a failure point in our notification system. Alerts were being throttled or discarded by our SMS gateway, particularly during cascading outages triggered by login server downtime. We’ve since refreshed our monitoring solution with modern analytics tools and implemented multiple alerting pipelines to prevent future disruptions. While we continue to work with our SMS gateway provider to resolve filtering issues, these changes significantly improve our ability to detect and respond to service issues.
Thank You for Your Patience
We sincerely appreciate your understanding as we worked to diagnose and resolve these challenges. We recognize how frustrating the repeated service interruptions have been and want to assure you that we’ve been actively addressing these issues with a focus on long-term reliability and minimal disruption.
Thank you for your continued trust in ExchangeDefender.
What is Ransomware? The Price of Clickbait


What is Ransomware?
Ransomware is a type of Malware. It is a nasty computer virus that locks up your important files. Think of your files as your favorite photos, important documents, or work projects. When ransomware strikes, it scrambles these files, making them useless until you pay the hackers. It’s like a digital thief who kidnaps your data and demands a ransom to give it back.

The Allure of Malicious Links and Attachments
Let’s be real, we’re constantly bombarded with information. From social media to email, we’re exposed to a constant stream of links and attachments. While many of these are harmless, some can be incredibly dangerous.

Why do people click on malicious links and attachments?
- Curiosity: A well-crafted subject line or intriguing message can pique our interest, leading us to click without thinking.
- Sense of urgency: Cybercriminals often use tactics like “urgent action required” or “limited-time offer” to create a sense of urgency, prompting us to click impulsively.
- Trust in the sender: If the email appears to be from a trusted source, such as a friend, family member, or colleague, we may be more likely to let our guard down.

The Devastating Consequences
The consequences of clicking on a malicious link or attachment can be severe. Ransomware attacks can cripple businesses, government agencies, and individuals, leading to significant financial losses, data breaches, and reputational damage.
How to Protect Yourself
To protect yourself from ransomware attacks, it’s essential to practice good cyber hygiene. Here are some tips:
- Be cautious of unsolicited emails: Avoid opening emails from unknown senders or those with suspicious subject lines.
- Verify the sender: Double-check the sender’s email address and look for any typos or grammatical errors.
- Hover over links before clicking: This can help you identify malicious links that may redirect you to harmful websites.
- Use strong, unique passwords: A strong password can make it more difficult for cybercriminals to access your accounts.
- Keep your software up-to-date: Regularly update your operating system and software applications to patch vulnerabilities.
- Back up your data: Regularly back up your important files to an external hard drive or cloud storage service.
By following these simple tips, you can significantly reduce your risk of falling victim to a ransomware attack.
Remember, a single click can have devastating consequences.
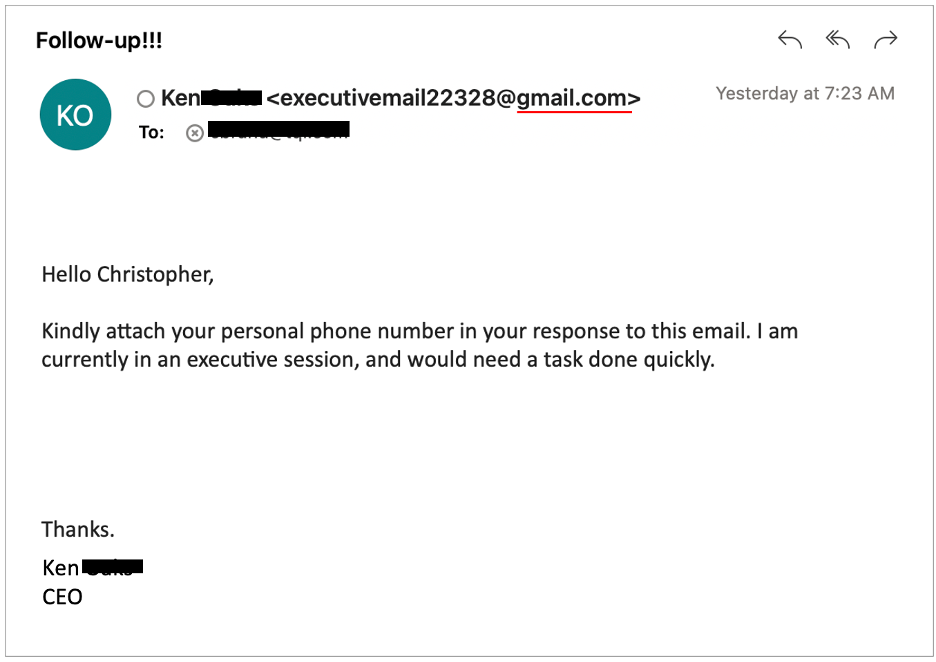
Whaling: A Sophisticated Cyber Threat Targeting High-Profile Individuals

Whaling, a type of phishing attack, targets high-profile individuals within an organization, such as CEOs, CFOs, and other executives. These individuals are often referred to as “whales” due to their high-value status and the potential for significant financial gain or data breaches if compromised.
How does whaling differ from traditional phishing attacks?
While traditional phishing attacks cast a wide net, sending out generic emails to a large number of recipients, whaling attacks are highly targeted and meticulously crafted. Cybercriminals conduct extensive research on their victims, gathering information about their personal and professional lives to create highly convincing and personalized messages.
Key Characteristics of Whaling Attacks:
- Highly Personalized: Whaling emails are tailored to the specific recipient, often referencing their role, recent projects, or personal information.
- Urgent Tone: Whaling attacks often create a sense of urgency, urging the victim to take immediate action, such as transferring funds or sharing sensitive information.
- Spoofed Identities: Cybercriminals may spoof the email addresses of trusted individuals or organizations to increase credibility.
- Sophisticated Social Engineering Techniques: Whaling attacks employ sophisticated social engineering tactics to manipulate victims into compromising their security.
Example of a Whaling Attack
A cybercriminal might impersonate a company’s CEO and send an urgent email to the CFO, requesting an immediate wire transfer. The email could be crafted to appear legitimate, using the CEO’s email address and signature. If the CFO falls for the deception, they could unknowingly transfer a large sum of money to the attacker’s account.
Protecting Yourself and Your Organization
To protect against whaling attacks, organizations should implement robust security measures, including employee awareness training, strong password policies, multi-factor authentication, and email filtering solutions. Additionally, executives should be particularly cautious when receiving unexpected requests, especially those that involve financial transactions or sensitive information.
Protect your Microsoft 365 environment with ExchangeDefender security solutions. Try ExchangeDefender PRO for free today!
Phishing 101: The Most Common Scams

Have you ever been hooked by a phishing email? It’s like those annoying telemarketers calling your landline, but way more dangerous. Instead of trying to sell you a vacation package, scammers are trying to steal your identity, your money, or both.
Let’s reel in some of the most common phishing scams
- Spear Phishing: Scammers use personal information to make their emails seem legit. They might know your name, job, or even your favorite vacation spot.
- Whaling: This is the big game of phishing. Think of it as hunting down CEOs and other high-profile targets. Scammers use sophisticated techniques to trick these folks into giving up sensitive information
- Smishing: This is like getting a text message from a friend asking for a favor. But instead of needing a ride, they want your bank account details.
- Vishing: This is the phone call version of phishing. Scammers will call you pretending to be from a bank or government agency, trying to trick you into giving up your personal information.
- Clone Phishing: This is like a scammer impersonating your friend or coworker. They’ll send you an email that looks almost identical to one you’ve received before, hoping you’ll fall for the trick.

But don’t worry, you’re not a helpless target. Here are some tips to avoid falling victim to phishing scams:
- Be cautious of unfamiliar emails. If you receive an email from someone you don’t know or a suspicious subject line, be extra careful.
- Verify the sender’s address. Look for typos or suspicious email addresses.
- Avoid clicking on suspicious links. If you’re unsure about a link, hover over it to see the actual URL
. - Never share personal information. Scammers will try to trick you into divulging your passwords, credit card numbers, or other sensitive data.
- Keep your software updated. Ensure your operating system and antivirus software are always up-to-date.
Remember, staying safe online requires vigilance, knowledge, and a bit of caution. So the next time you receive a suspicious email, don’t let scammers trick you!
Tired of dealing with phishing scams? ExchangeDefender’s advanced phishing protection can help keep your inbox clean and your data safe. Ask us for a free trial!
Spoofing vs. Phishing: Understanding the Differences

In today’s digital world, online security is more important than ever. Two common threats that can compromise your personal information and security are spoofing and phishing. While these terms may sound similar, they represent distinct types of cyberattacks. In this blog post, we’ll explore the differences between spoofing and phishing, how they work, and how you can protect yourself from falling victim to these scams.

Spoofing: It’s Not Who You Say You Are
Spoofing is like someone pretending to be someone else online. For example, a scammer might send you an email that looks like it’s from your bank, but it’s actually from them. They’re trying to trick you into thinking they’re someone you trust.

Phishing: A Fishing Expedition for Your Information
Phishing is a bit like a fishing expedition, but instead of catching fish, scammers are trying to catch your personal information. They might send you an email or text message that looks like it’s from a legitimate company, asking you to click on a link or download an attachment. If you do, you might end up giving away your personal information, like your passwords or credit card numbers.
The Key Differences
- While both spoofing and phishing involve deception, there are some key differences between them:
- Intent: Spoofing is often used to gain unauthorized access or launch other attacks, while phishing is primarily used to steal personal information.
- Techniques: Spoofing involves technical methods to disguise the sender’s identity, while phishing often relies on social engineering techniques to manipulate victims.
- Impact: Spoofing can have a variety of consequences, while phishing attacks are primarily used to steal personal information.

How to Protect Yourself
- Be skeptical. If you get an unexpected email, text, or phone call, be suspicious. Don’t click on links or open attachments unless you’re sure they’re from who they say they’re from.
- Check for typos and grammar mistakes. Scammers often make mistakes in their emails or texts.
- Never give out personal information. Don’t share your passwords, credit card numbers, or other sensitive information with anyone unless you’re absolutely sure they’re who they say they are.
By being aware of the difference between spoofing and phishing, and by following these tips, you can help protect yourself from becoming a victim of these scams.
Looking for Spoofing AND Phishing protection that’s affordable? Go for ExchangeDefender PRO!
Insider Threats: A Growing Cybersecurity Challenge

Insider threats pose a significant risk to organizations of all sizes. These threats come from individuals within an organization who have authorized access to systems and data. They can range from unintentional mistakes to deliberate acts of sabotage.

Types of Insider Threats
- Malicious Acts: Deliberately stealing data, sabotaging systems, or causing damage.
- Negligence: Accidentally compromising security due to carelessness or lack of awareness.
- Espionage: Sharing sensitive information with unauthorized parties.
- Fraud: Using their position to gain financial advantage.

Why Insider Threats Are Dangerous
- Access to Sensitive Data: Insiders have legitimate access to critical systems and data, making them a significant threat.
- Difficult to Detect: Insider threats can often go undetected for extended periods, as they may mimic normal user behavior.
- Damage Potential: Insider threats can cause significant damage, including financial loss, reputational harm, and operational disruption.

How to Mitigate Insider Threats
- Strong Access Controls: Implement robust access controls to limit user privileges and prevent unauthorized access.
- Regular Security Awareness Training: Educate employees about the risks of insider threats and provide them with the tools to identify and report suspicious activity.
- Behavioral Analytics: Monitor user behavior for anomalies that may indicate malicious activity.
- Data Loss Prevention (DLP): Implement DLP solutions to prevent unauthorized data exfiltration.
- Incident Response Plan: Develop a comprehensive incident response plan to address security breaches effectively.
By understanding the risks posed by insider threats and implementing appropriate measures, organizations can significantly reduce their vulnerability to these attacks.