Passwordless Login – Lower support, better profits
ExchangeDefender Passwordless Login is a new feature that lets users get into their ExchangeDefender account easier and faster. Instead of logging in and tracking passwords, the user just enters their email address and the OTP code we send there – and they get access to all their ExchangeDefender services.
The Passwordless Login feature will drive down the support costs because that was the major issue our clients found in supporting login and authentication problems. We even joked that you may have answered your last login problem email. We now have more data and feedback indicating that this feature is a hit:
In practical terms, wider adoption of this feature means less support work for login and authentication. The fact that it’s more popular than password reset on launch means the users have already seen this feature elsewhere and trust it as a secure way to get into their account.
We’ve also heard from our technical and compliance audience: “It allowed us to finally take you up on an automated password expiration knowing that it will keep our passwords secure and users wouldn’t notice.“
The value we provide to our clients is in the ability to securely email, send secure encrypted messages, and continue emailing when there are IT issues. By making it easier for our users to get to these features everyone benefits.
Thank you for your business and for trusting us to protect your email.
Unlock Your Admin Portal with Ease: Introducing Passwordless Login
On Thursday, May 18th, the login experience at ExchangeDefender will change. Everything still works the same way as before and the new features will not affect user login: you’ll still go to https://admin.exchangedefender.com and type in your email & password to log in.
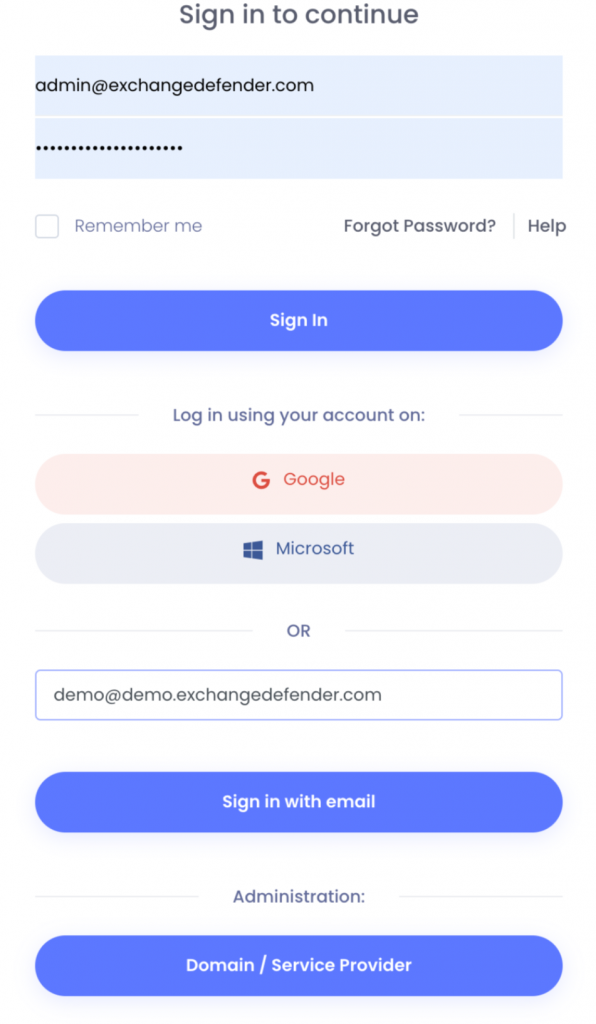
Below the main login block, you will see the new Advanced Login block featuring Passwordless and Administrator login features.

Passwordless – Tap this if you forgot your password and don’t want to set a new one. We’ll email you a code (for account verification) and when you type it in you’re good for the next 30 days.
Administrator – Tap this to log in to the management console for ExchangeDefender – Domain Admin and Service Provider. It’s safer & smarter to use user->domain, and service provider escalation and this is a more convenient way for smaller organizations.
Social and app authenticator login buttons are on the bottom and we now support all the TOTP app authenticators and encourage you to lock your accounts down.
Protect Your Privacy with Disposable Tracking Emails
Do you ever wonder who is selling your email address to marketing companies? Or do you ever sign up for services and sites while checking things out but don’t want to end up on every email they send until the end of time? Gave your email address for a 10% off discount? Used it with a sketchy parking lot?
We’ve all been there.
Wouldn’t it be nice to be able to come up with an address on a whim? I’m at Subway and they want my email:
“Yeah, that’s subway+vlad@exchangedefender.com“
ExchangeDefender now let’s you do this on a whim there is nothing to set up. Just add any tag+ to the front of your email address and that’s it. Yep, any text you can imagine. Tie it to a specific search like pi+orders+vlad@exchangedefender.com so you can create an Inbox filter rule and potentially automation based on the address alone.
Message is still subject to your security policies so if it’s safe it will come right to your inbox.
Yeah but how do I unsubscribe?
You can do the traditional click & pray that the unsubscribe site is 1) up and 2) works.
The cool thing about tracking emails is that they are integrated in admin.exchangedefender.com and you can see a report similar to the daily quarantine report. Here you can see who is sending messages to which disposable address.
ExchangeDefender shows you where the sender got your email address from and where your data may have been compromised or sold.
You have even more flexibility with the address. If you’re starting to get a lot of abuse at the address, just click on the <b>Stop</b> button and we’ll bounce any email sent to that address tag+ address.
Changed your mind? Hit play and the address will be reactivated as usual.

ExchangeDefender Passwordless Logins

ExchangeDefender is pleased to announce the addition of passwordless logins. This convenient authentication method has become an industry standard and we’re implementing it at the request of many of our clients.
The problem: “I don’t know what it is, I don’t know what my password is!” OK. Reset password. Wait for the email. Pick a new password. A more complex password. One that you’ll forget as soon as you log in. We’ve all been there.
In our May update, you will see another login option under the default sign-in, allowing you to sign in with email. It’s as simple as it sounds, type in your email address and we’ll email you a magic link (with an OTP code) that you can use to log in to your account without your password. It’s that simple.
The session will stay logged in for a month so as long as you’re on the same computer/mobile you won’t have to worry about tracking passwords with ExchangeDefender.
PS. This means anyone with access to your mailbox will have access to ExchangeDefender as well – so for those of you that value security over convenience we’ve also added a domain-level policy that can disable this feature.
We should talk…
ExchangeDefender is aggressively adding features and growing the security footprint and we understand that IT staff is already spread thin enough – so if you’re tight on time or security expertise we are able to help by reviewing, applying, and configuring your mail flow so users get fewer interruptions while getting the latest and best-tuned security service for email.
Service Provider Dude, where is my SPAM?

ExchangeDefender is the ultimate cybersecurity wrapper for an organization and we already discussed how Users and Domain Admins can locate messages ExchangeDefender was configured to keep out of the mailbox.
ExchangeDefender users have a beautiful and powerful way to access their quarantined mail and work around email problems, domain admins have flexible settings, policies and access to the logs to keep the organization protected. So what do ExchangeDefender Service Providers have that others don’t?
ExchangeDefender Service Provider access enables you to do deep troubleshooting and emergency “incident response” activities. Service Provider login is the highest level of control in ExchangeDefender so you have access to all the data that ExchangeDefender has.
Accessing Logs
ExchangeDefender Service Provider access gives you access to the centralized log facility where you can locate any message ExchangeDefender has processed from a central pane of glass.
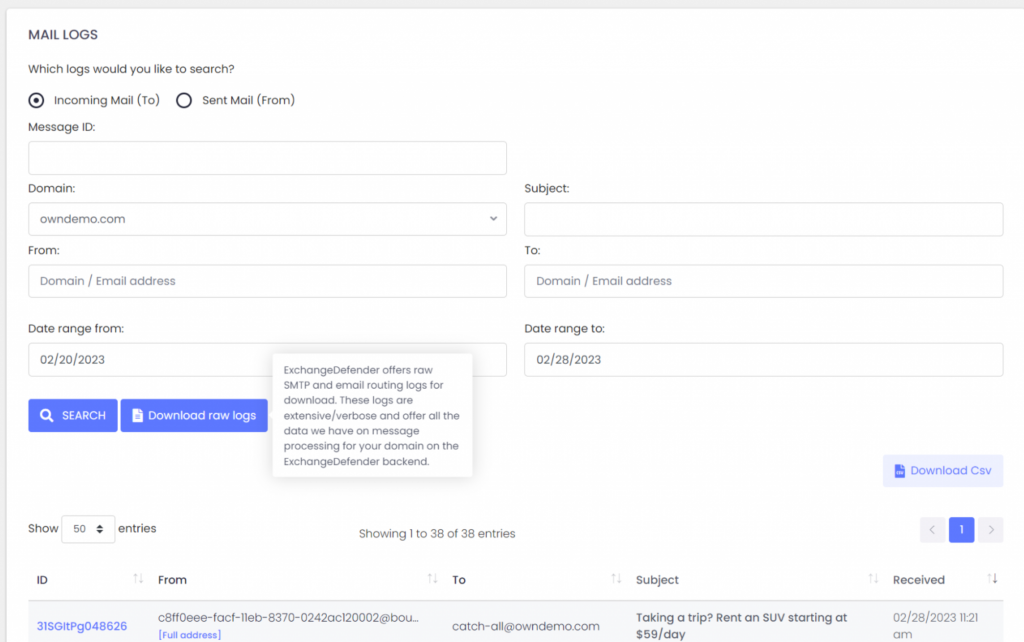
You can download any search results as a CSV file that can be better visualized and analyzed in a spreadsheet and reporting tool of your choice. This is particularly useful when you don’t know the sender or are searching for an automated sender with a fake tracing email address.
Our partners frequently rely on this facility to troubleshoot for missing messages.
Downloading Raw Logs
ExchangeDefender Service Providers also have access to raw SMTP Mail Logs which give our partners direct access to low level SMTP transactions and error logs. It’s located in the same location as log search.
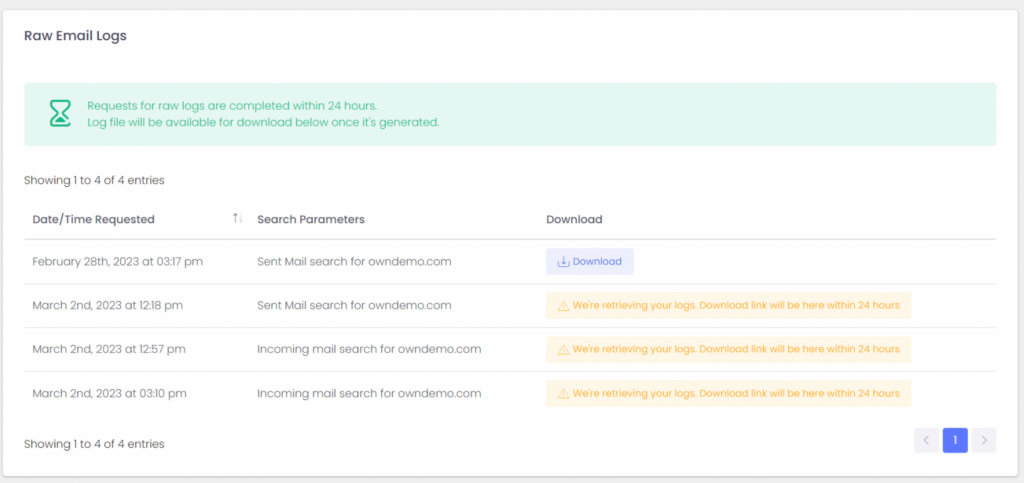
Service Providers rely on these logs as the ultimate source of truth regarding the traffic for the ExchangeDefender protected domain. This is a fantastic tool if you’re looking for intermittent delivery errors or policy violations or just have a very specific email or server you’re looking for.
Logs will get pulled from all our services and will be available for download within 24 hours. Don’t let the boilerplate distract you, almost all of our clients will get their logs within the hour. From there you can load the logs into your favorite analytics tool and dig for the errors and problems in the mail flow.
To sum it up
ExchangeDefender can help you account for every message going in and out of your organization. While users have a powerful and beautiful way to access their quarantined mail or continue where they left off during an outage or email problem, domain admins and service providers have far more access to the logs so they can troubleshoot around different settings and policies.
Domain Admin Dude, where is my SPAM?

In our previous post we discussed how users can get to their own SPAM quarantines but did you know that you as the domain administrator have access to EVERYONE’s junk mail?
ExchangeDefender Admin Portal features a SPAM Admin section where you can release ANY message caught by ExchangeDefender to ANY user in your organization.
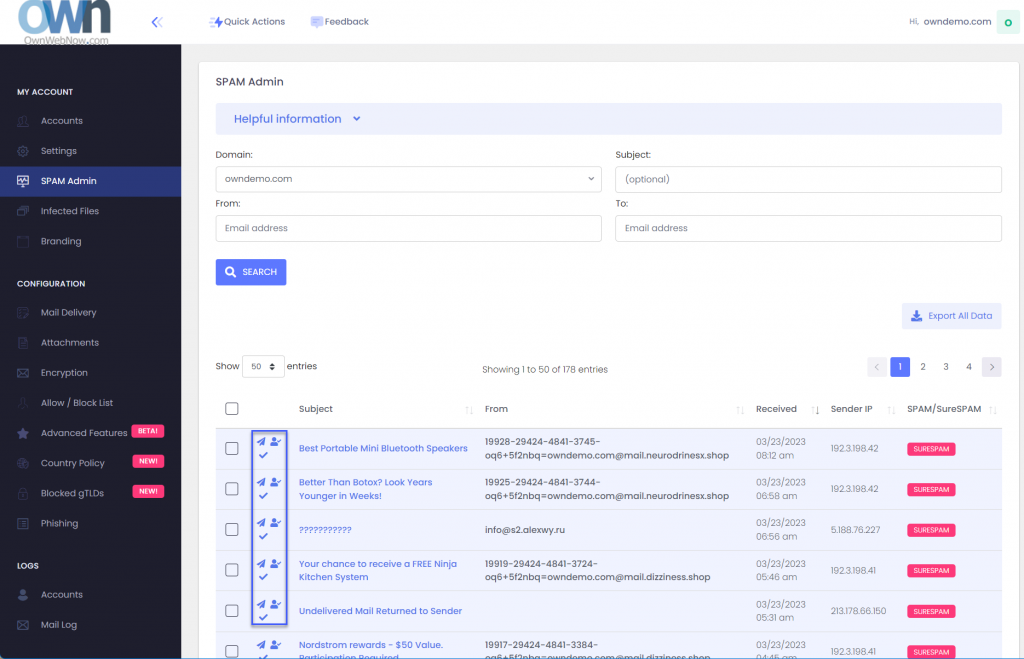
The three icons next to the message are Release Message, Allow Sender, and Mark as reviewed. Releasing a message will get it to the end users mailbox while allow sender will create an Allow policy for that email address so it skips SPAM checks in the future.
Many organizations designate a SPAM Admin that is in charge of fishing out important messages, attachments, and other content that was blocked by an IT or corporate policy. If you have a lot of users that are not tech-savvy this feature will save you a ton of time.
I already have an Allow Policy and my mail from this sender is always ending up in Junk Mail!
ExchangeDefender Advanced Features can help you here as this problem is so common we’ve built an entire feature to help solve it. The issue is, most of the messages coming are from automated systems (password reminders, newsletters, appointment confirmations, etc) that are sent by a computer instead of someone’s Outlook or phone. They all rely on mass/bulk mail systems like Amazon SES, Sendgrid, etc and those networks use a fake email address to send a message every time (so they can track bounces). You can’t create an allow policy (whitelist) for those addresses as they change every time, so take a look at the Bulk Mailer Policy section:
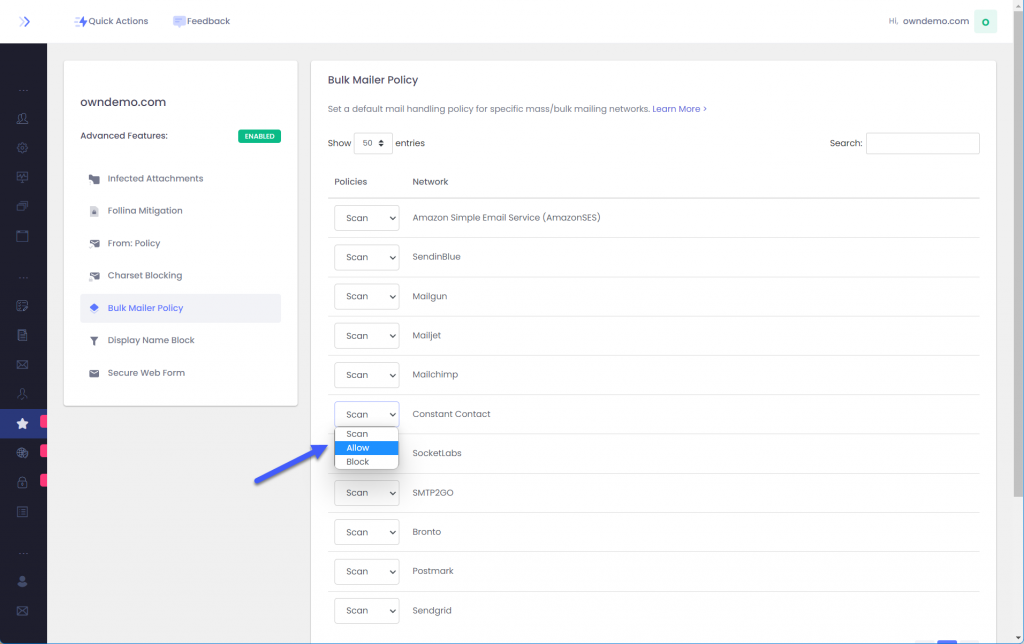
Here you can tweak the policy applied to each bulk mailer network to accommodate your users. By default we scan each message from these networks for SPAM contents but depending on the problem you are trying to solve with SPAM you can change it to Block or Allow messages from that network.
I already did all that, seriously, where is my email?
Most of policy enforcement problems stem from not knowing which message the user is looking. As mentioned earlier, automated systems forge the email address they send mail from so the address you see in Outlook is not the actual email address. It’s tough to make policies or find the message when you don’t know the senders email address: ExchangeDefender Mail Log to the rescue:
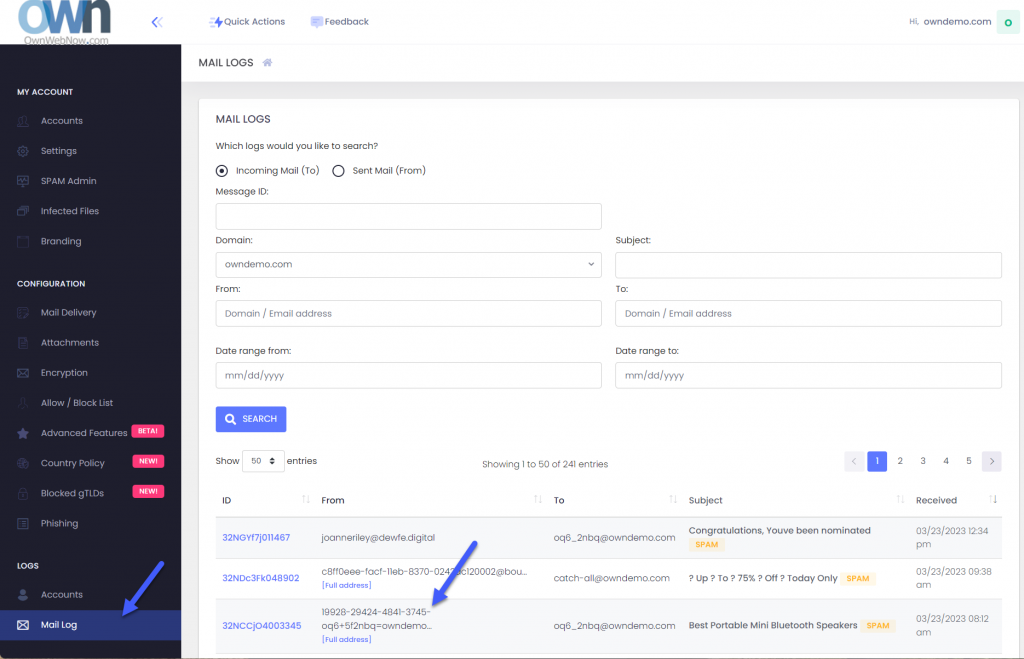
As the Domain Admin you have access to all the email logs for your domains. Click on Mail log and you’ll be able to search for the message based on time, date, subject, etc.
You can also scroll through the mail log. See the [Full address] below some senders? Those are the fake tracking email addresses we’re talking about. Generally you can create a domain-wide allow policy for the entire domain if you trust that the sender isn’t going to send malicious content (we’ll still check if any attachments are infected and apply your file/extension policy).
To sum it up
As an ExchangeDefender Domain admin you have powerful tools to locate SPAM, apply allow or block policies, and to scope them down to the bulk mailer network that is usually the #1 culprit. Go figure, nobody wants these messages and they sometimes get inadvertently reported as junk anyhow.
ExchangeDefender can save hours of going through transaction and message logs by presenting all of your messages in a user-friendly way where you can quickly release them to your user, create an allow policy so it doesn’t get intercepted again, and designate clients trusted partners/networks that should always go straight to their mailbox.
Dude, Where’s My SPAM?
ExchangeDefender protects you from dangerous email by blocking their delivery directly into your Inbox. Sometimes the way your IT admin has configured ExchangeDefender (security policies, admin policies, business restrictions) can become more aggressive and quarantine legitimate email messages. Other times the email sent by a legitimate sender is so misconfigured (broken DNS, email structure, RBLs, etc).
ExchangeDefender makes it easy to secure your Inbox and easy to get to messages that it’s been told to block.
If you’re expecting an important email and it hasn’t arrived read on for how to access it.
ExchangeDefender Quarantine
ExchangeDefender Quarantine is a web app accessible from any modern web browser, desktop and mobile. Not only will it show you everything we’ve kept from your Inbox, you’ll also be able to read/reply/forward/print the messages immediately and make sure they never end up in the SPAM.
First, open a browser and go to https://admin.exchangedefender.com
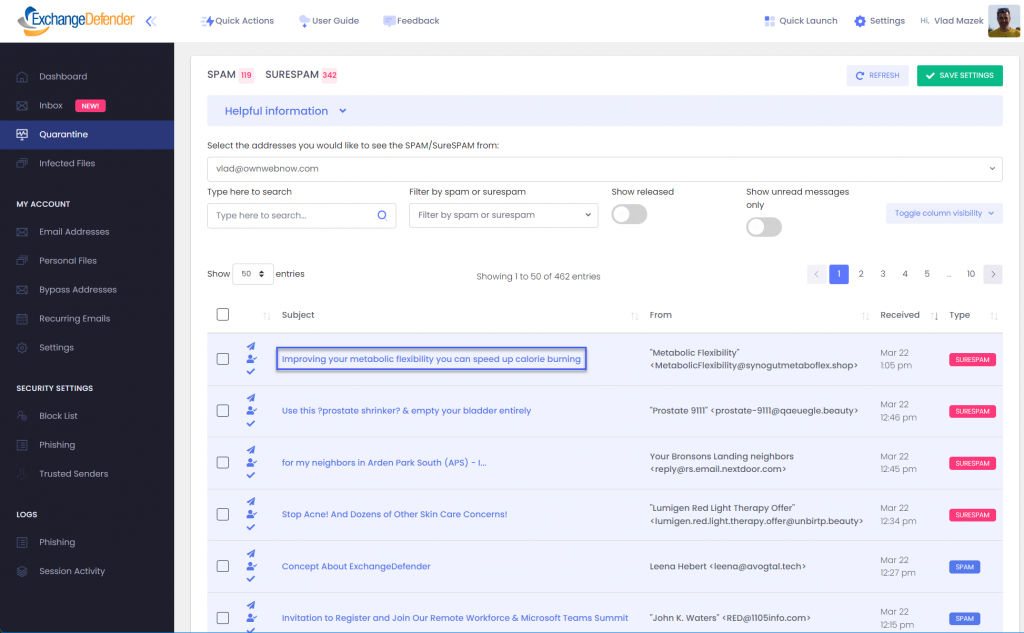
Click on Quarantine and we’ll show you all the messages that are currently waiting. Note that the from address is the real/machine email address, not a fake/forged one you see in Outlook. This will make it easy to tell who is just spoofing and who is legitimate.
If you click on the subject, your message will open and you will able to act on it just like you do from any other email client right there in the same browser window.
If you click on the icon to the right of that (user with a checkmark) the system will create an Allow policy to let messages from this sender skip SPAM checks next time and arrive directly in your Inbox.
Option 2: ExchangeDefender Inbox
Sometimes the message isn’t in the Quarantine and it isn’t in your inbox. So where did it go?
99.9% of the time, the message has been miscategorized by your email infrastructure. This happens often when [relay permissions aren’t configured correctly] or the email itself triggers some other internal security process (desktop AV, firewall, etc) that blocks you from accessing it.
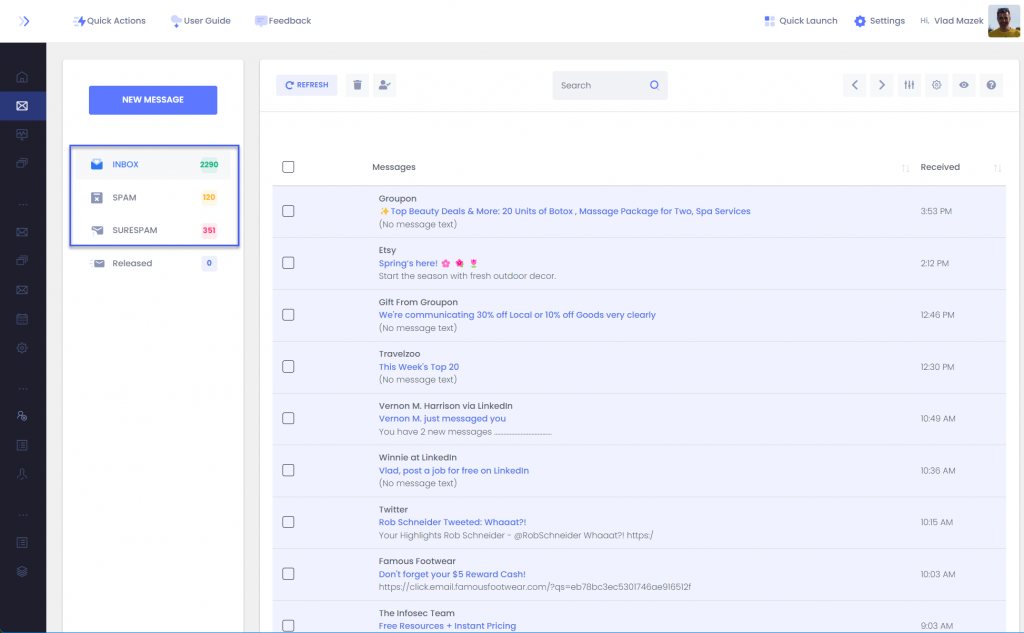
Solution: The best hack to employ here is to rely on the ExchangeDefender Inbox. We cache all the messages going to your server and if you click on Inbox you’ll be able to see messages we sent to your mailbox.
To sum it up
The easiest way to access all the messages ExchangeDefender is keeping from your mailbox is to go to https://admin.exchangedefender.com and click on Quarantine. For messages that don’t get delivered after they’ve been processed by ExchangeDefender stay on https://admin.exchangedefender.com and click on Inbox.
For more information about ExchangeDefender web app
Still can’t find the message? Tune in next week to see how your [domain admin] or [service provider] can help.
How to access ExchangeDefender Raw Email Logs
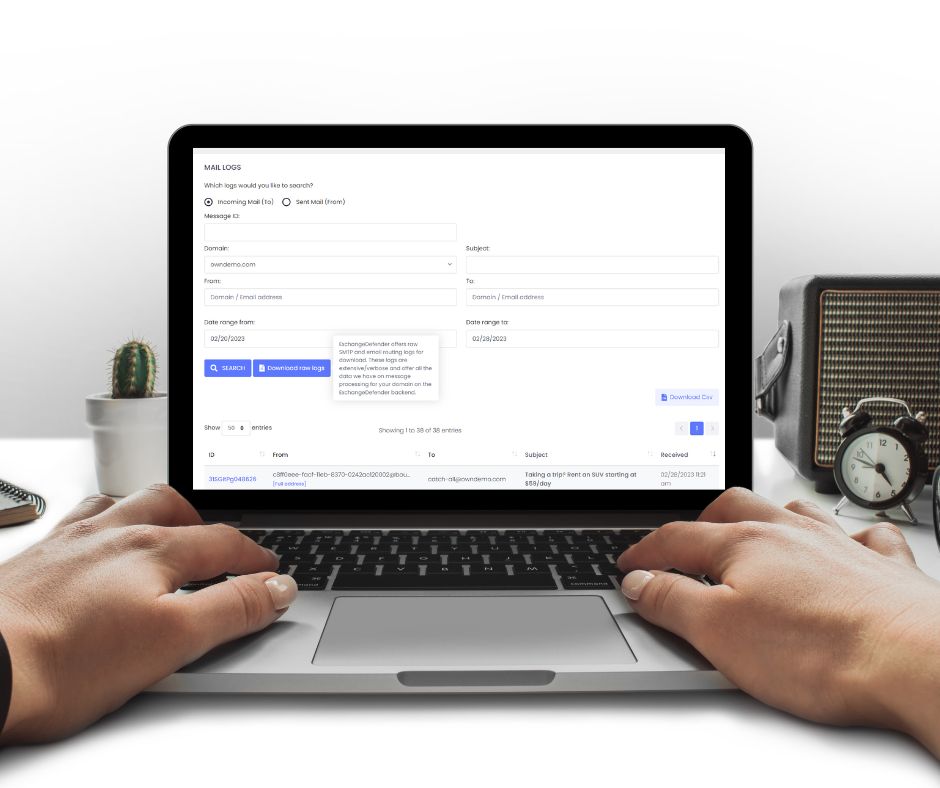
ExchangeDefender has been holding Service Provider (MSP/VAR) Focus Group meetings this week and we’re beyond excited to hear what we can build to make your and your clients lives easier with ExchangeDefender.
One of the most common pieces of feedback from the *Service Provider crowd so far has to do with log access and particularly low-level log access that can give further insight into problems and message routing.
Allow us to introduce you to Raw SMTP Mail Logs which will give our partners direct access to the low-level SMTP transaction and error logs. It’s located in the same location where you currently have service provider logs at admin.exchangedefender.com
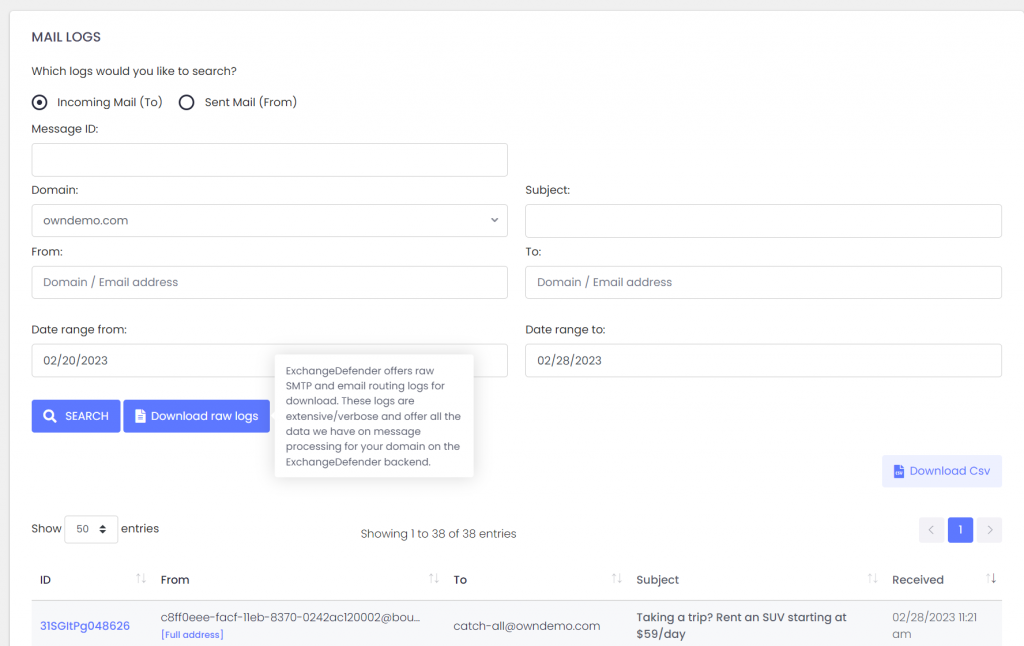
In addition to the live search which will give you an interactive access to our logs, you can see the button to Download raw logs.
Set your search criteria (at the very least a domain name and the direction of the search: inbound/outbound) and click on the button.
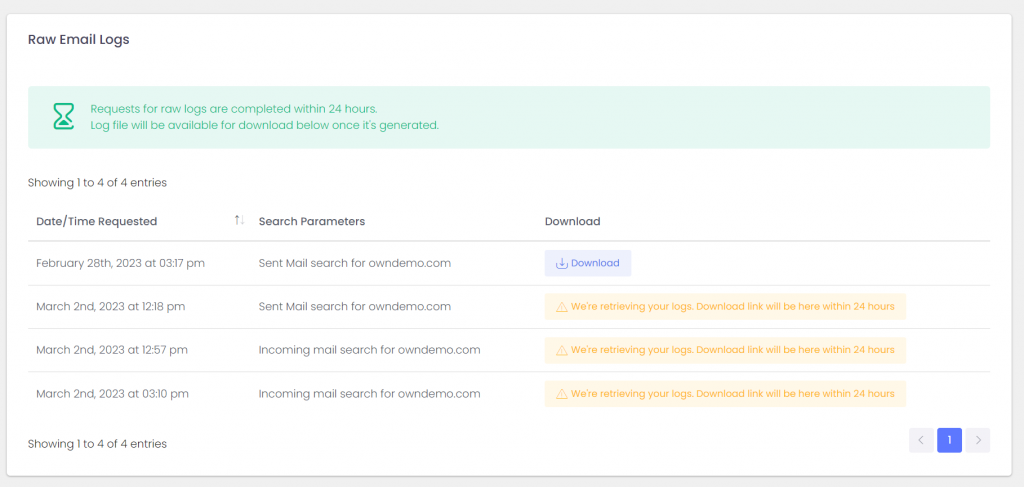
Logs will get pulled from all our services and will be available for download within 24 hours. Don’t let the boilerplate distract you, almost all of our clients will get their logs within the hour.
From there you can load the logs into your favorite analytics tool and dig for the errors and problems in the mail flow.
P.S. If you’re interested in contributing to our Service Provider Focus Groups please let us know!
Q: What is the difference between “Download raw logs” and “Download .csv”?
A: .csv export will save the current search results in a .csv file that can be used with Excel and other spreadsheet products. Search logs include to/from/subject/date/score/status only and are great for centralized analysis of messages that ExchangeDefender processed. By comparison, raw logs include SMTP protocol-level transactions/errors/notices that can help diagnose delivery and routing errors. So – .csv for Excel view for business analytics, raw log SMTP transactions for technical troubleshooting.
New Release: ExchangeDefender Inbox M365 Hybrid Solution
Huge and most demanded feature from our community has finally shipped.
No more PowerShell. No manual steps. It’s all automated.
When you create a mailbox on ExchangeDefender Inbox the service creates your users M365 account, enables mail forwarding, maps the email addresses correctly, updates routing and signing.
Anyone can manage Inbox with far fewer IT skills than are needed for the most basic of M365 deployments!
We’re seeing ExchangeDefender Inbox mailboxes used in companies with high turnover, in companies that are trying to save money (Inbox could save over $300 / employee every year!), for mailboxes that get a ton of traffic but are mostly for logging (necessary but rarely ever logged in), temps, external users that need email at that domain but shouldn’t be given an entire M365 license or be exposed to all the data you have on your M365.
So.. if you’ve been keeping your own Exchange server barely alive just for these types of use case that M365 isn’t ideal for (or worth the $), let’s have a call and save some of your IT budget!
How easy is it?
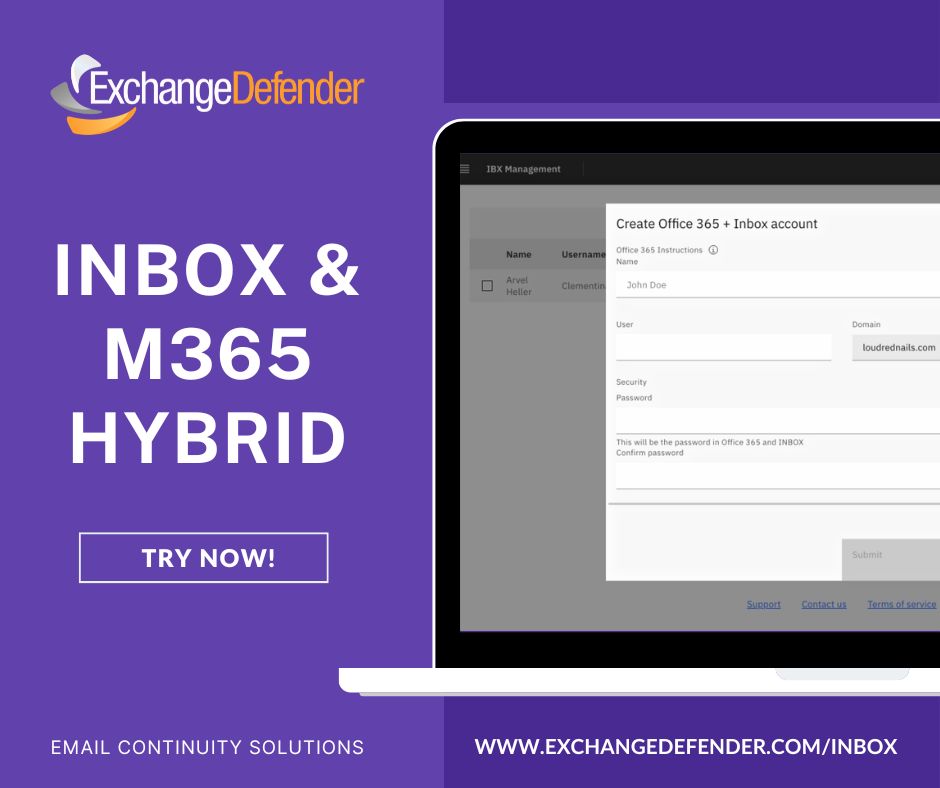
Login to your ExchangeDefender Inbox admin account and choose a tenant to create a user.
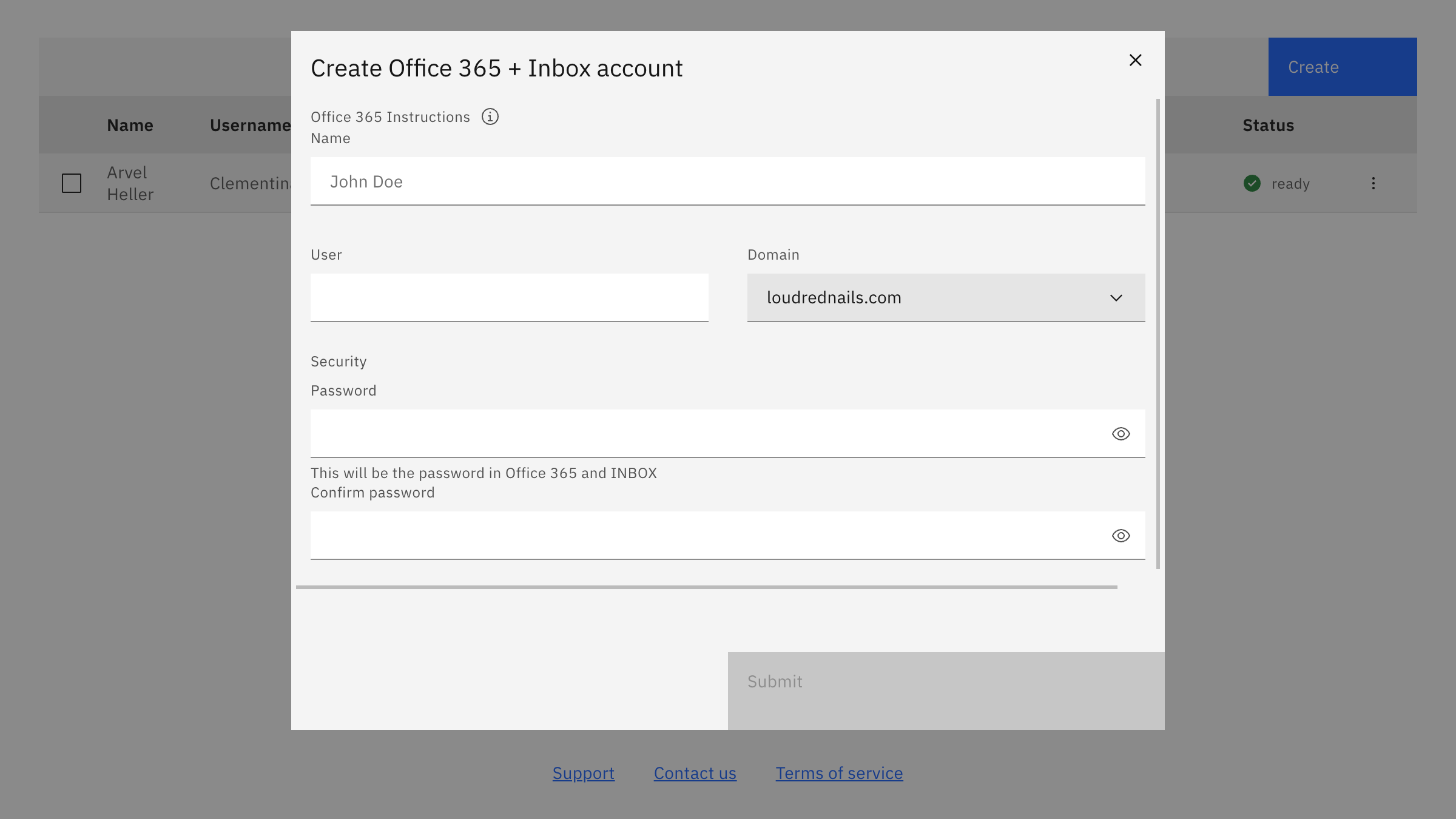
ExchangeDefender Inbox does all the heavy lifting under the hood instantly. Using a combination of Remote PowerShell, Microsoft Graph, and Microsoft’s API for Exchange/M365 we’re able to create the user, setup forwarding, update address books on both sides and keep everything in sync. The admin doesn’t have to deal with any of that, they just see that it’s done:
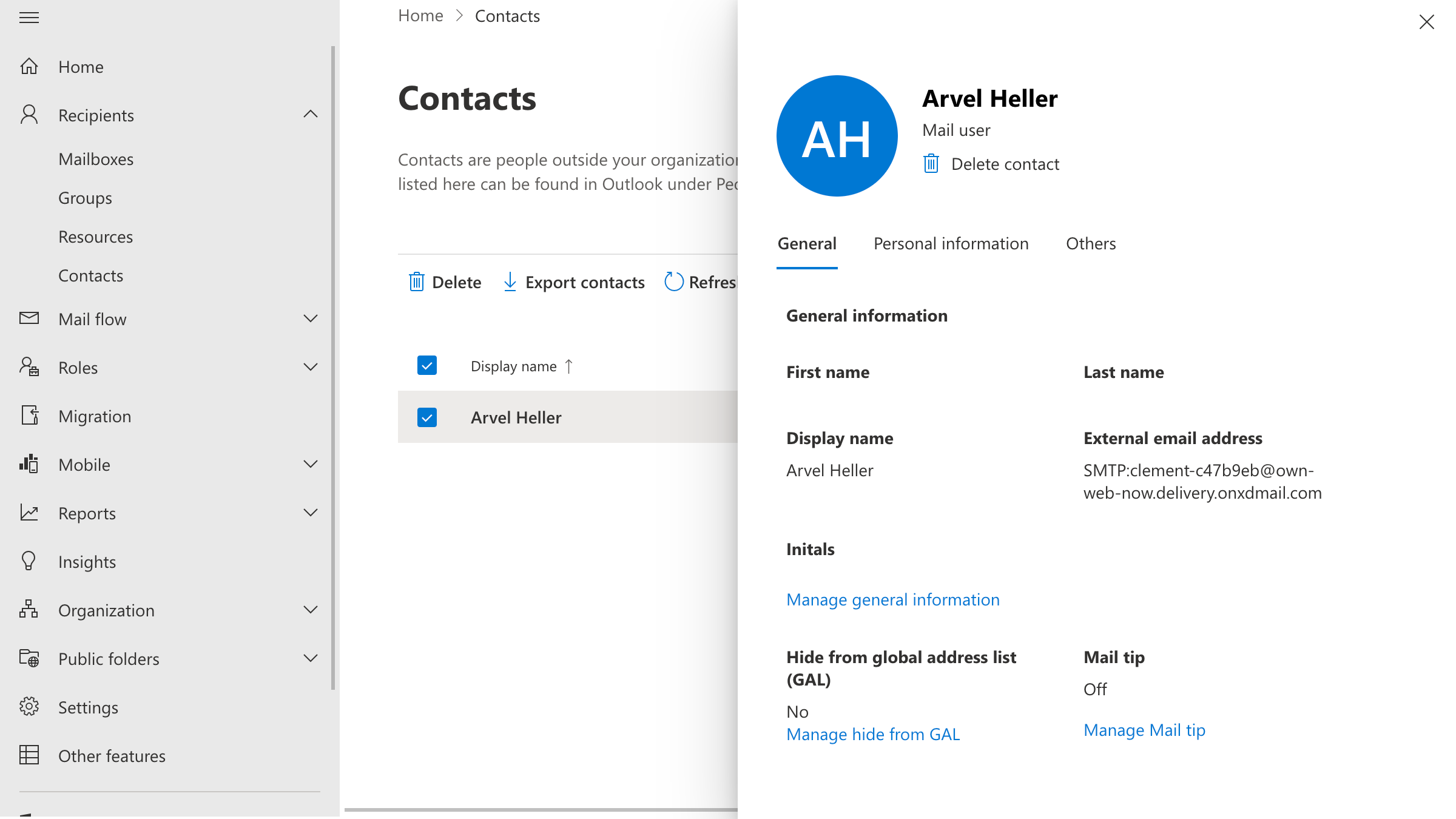
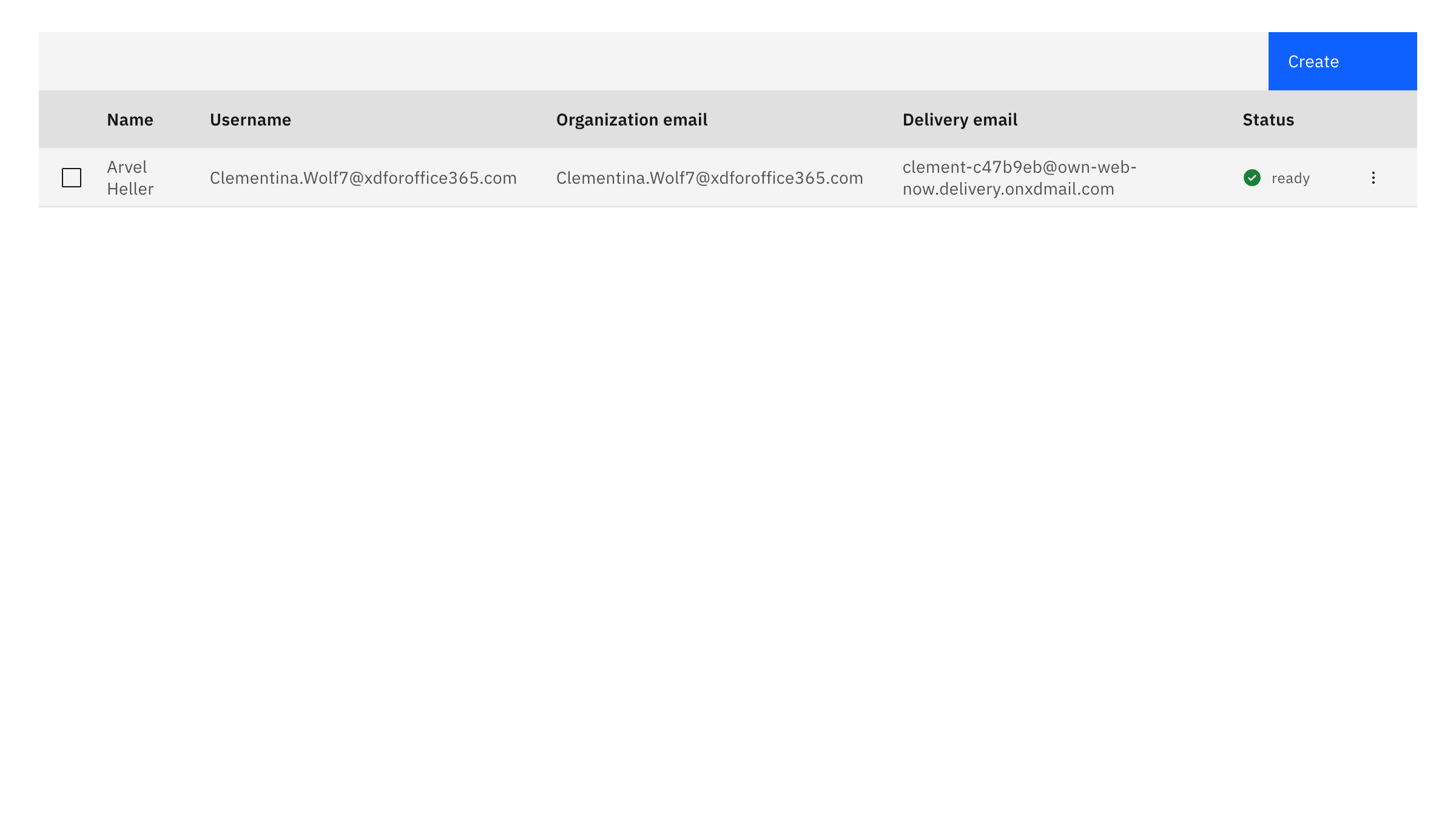
That’s all it takes to create a mailbox and share the domain with a M365 tenant in hybrid mode. Everyone is on the same domain, everyone has the same format email address, it’s practically the same thing but saves your organization up to 95% every month.
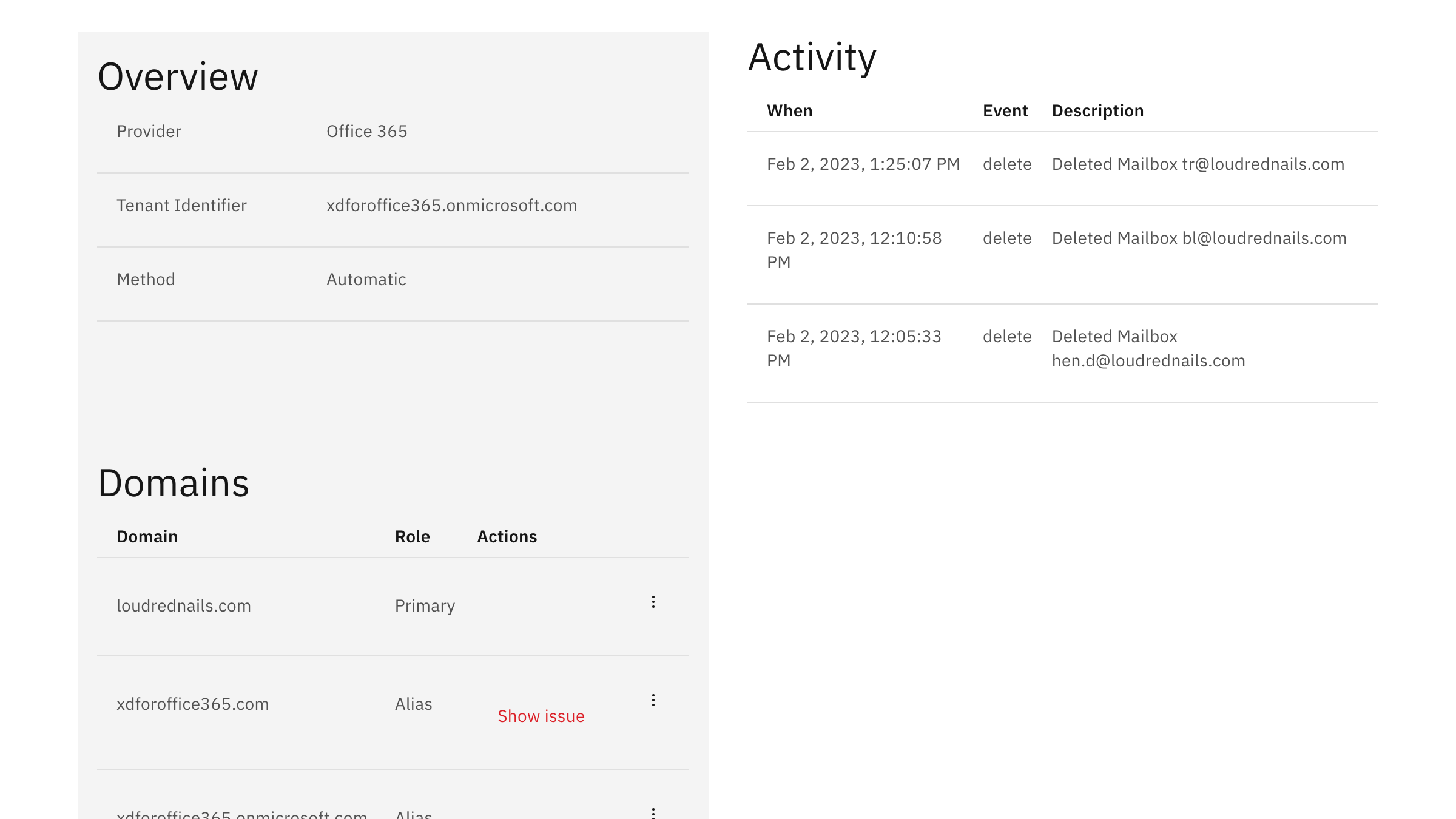
Everything on the backend is tracked and kept in compliance. Best part – we do not use delete statements anywhere so you never have to worry about ExchangeDefender Inbox creating problems and issues at M365.
Try Inbox today for free! Login to your ExchangeDefender Admin account to get started.
ExchangeDefender URL Rewriting Tips
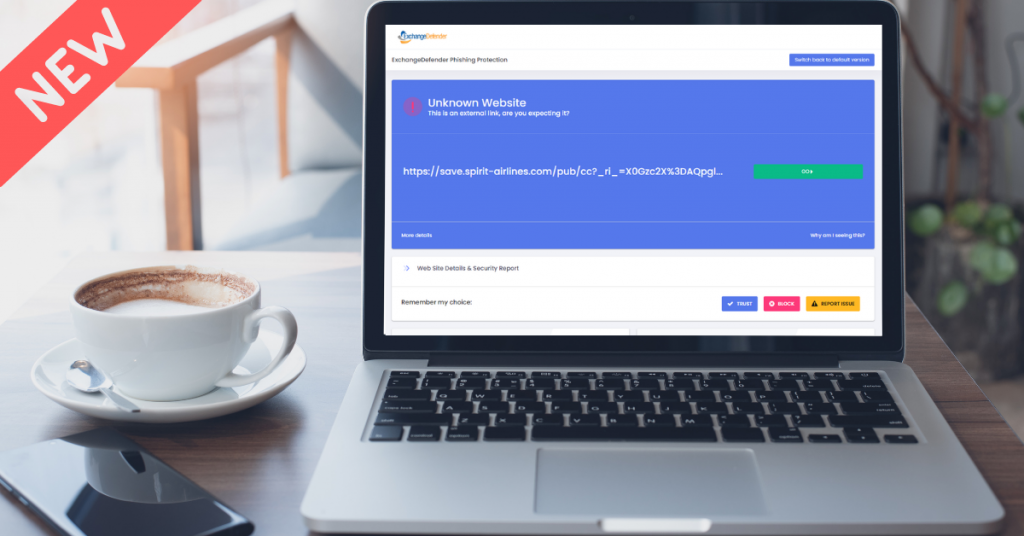
No matter how much money you waste on cyber training, someone, somewhere, innocently or intentionally, will eventually click on a link that can take your network down.
ExchangeDefender protects you from malware and phishing threats by rewriting web traffic through our security service called ExchangeDefender Phishing Firewall. The process is very simple, we analyze the email message as it goes through ExchangeDefender and rewrite the URLs so that when you click on them on your Outlook or phone you’re redirected to a site that your organization manages and that you can customize for your personal liking.
Remember, over 91% of cybercrime starts with a link in an email! ExchangeDefender helps stop that.
We also roll up OSINT and public reputation lists that give you an idea exactly what you are being directed to. We check if the site is known for spreading malware, if there is a recent incident report, if the site is brand new – and you can quickly decide to click on a button to proceed one time or you can add it to your safe list and then you’ll automatically get redirected to the real site.
Problems and Challenges
URL rewriting is an industry standard practice and almost all large mail service providers feature similar “safe links” technology.
As helpful as it is in disarming dangerous content, it can at times cause a support issue as well when the link gets broken or when the site gets wrongly listed for hosting dangerous content (hint: we don’t host anything, we just redirect the link). The process of delisting can take some time and sometimes misconfigured devices and services can cause additional problems. Just last week we dealt with an issue at Comcast/AT&T xFinity Business SecureEdge service and the only workaround is to turn that service off.
Workarounds and Quick Fixes
The quickest way to work around this is to ask the sender to email you at your bypass email address you create for this interaction. Simply go to https://bypass.exchangedefender.com and follow the directions from there.
Optionally, but as the last recourse only you can turn off the ExchangeDefender Phishing Firewall (see https://www.exchangedefender.com/docs/domain for instructions) but doing so also lowers the level of protection and support you’ll be getting from ExchangeDefender.
We have a week of client/partner development focus groups, March 6th-7th and if you’re interested please ping us at events@exchangedefender.com. What we’re currently beta testing are provider or domain redirection portals so that you’re not stuck sharing r.xdref.com or d.xdref.com with millions of your closest email neighbors. This way any problems with the site listings or DNS hijacking (in SecureEdge’s case) would be limited to your clients and it would be easier to pick out and mitigate any malicious reporting activity.
If you’re looking to make ExchangeDefender work better for you, please join us for the focus group. We’d love to help you protect your clients mail flow better.