Webinar RECAP: Introducing Brand New Admin UI and New ExchangeDefender Services
On Wednesday, November 13th, I got the pleasure of introducing our partners and clients to several new services from ExchangeDefender:
– New ExchangeDefender UI for users
– New Wrkoo Calendar and Appointment Booking feature
– New Postmaster support service for Exchange/ExchangeDefender Pro
Our development team has been working like crazy to bring all these features to our clients and we’ve had a ton of beta testers enjoying both solutions for weeks with no major problems (but lot’s of feature requests that we look forward to adding to the product).
ExchangeDefender UI / UX Upgrade
Our current strategy is to make sure the ExchangeDefender service enters 2020 with the brand new UI across all login levels and services. All these new services are coming with improved security, more functionality, and are significantly faster.
Wrkoo Calendar & Appointment Booking
Our strategy of rolling some Wrkoo features to the ExchangeDefender client base continues with our calendar module. In addition to the Password Vault, which is also available free of charge to our ExchangeDefender Pro clients, Calendar and Appointment Booking modules will be available for free as they are key to our strategy of offering a full groupware solution by January 2020.
The calendaring option adds everything you’d expect from a modern calendar and appointment sharing application, but built for groups and businesses. A public appointment setting site is integrated, allowing web site visitors to request an appointment after seeing the available schedule – with Wrkoo handling all the collisions, registering users, setting up meetings and free/busy status.
In terms of scope, this is the largest non-ExchangeDefender to date and a requirement for our new groupware service. In terms of feature set and functionality, it significantly exceeds what is currently available.
Postmaster Support
ExchangeDefender has spent 2019 improving support and troubleshooting automation which has resulted in savings of thousands of hours and support requests. We’re stepping it up even further with a concierge service to help with message tracking, NDRs, and DNS-related email delivery problems.
The new site will help users automatically detect common problems with their setup or configuration. After collecting basic information, it will then be assigned to a case manager that can effectively work with sender, recipient, and other interested parties to resolve the problem.
In conclusion
Take a moment to watch the webinar. There is so much context and background to our strategy.
https://www.exchangedefender.com/media/XDUICalendar.mp4
As this is our last webinar for 2019, I wanted to personally thank you for all your business and your trust. We have worked like crazy this year to get these features to you before 2020 and in our opinion we are light years ahead of where we were at this time last year. I’m sure you can tell from the excitement in my voice that we believe these new features will be significant game changers for our partners and clients and we’ll continue working on developing solutions to the continuing challenges in security and in productivity.
Sincerely,
Vlad Mazek
CEO
ExchangeDefender
ExchangeDefender Phases Out “Essentials & Exchange Hosting Essentials” Services

Everyone on record by December 31st, 2019 will be grandfathered into the service.
You’ve got 45 more days to sign up for ExchangeDefender Essentials and Exchange Hosting Essentials in their current form with all the current benefits and features.
In 2020, we will start offering a new Essentials service that is more competitive with the entry level offerings from Microsoft, Google, etc.
New accounts will not be compatible with Office 365, Gmail, or other cloud based email services, a territory that ExchangeDefender Pro is far better suited for.
The service will be slightly more affordable but will no longer have options to add on Encryption, Web File Sharing, LiveArchive, Compliance Archive, corporate & MSP branding, and other enterprise-ish features. If these features are important to you and you have open leads, please make sure the orders are placed by Christmas.
Between the lines:
ExchangeDefender Essentials line has had a great run but over the past two years we’ve noticed a trend – clients are either going for the cheapest option, or they are signing up for all the bells and whistles that come with the Exchange and ExchangeDefender Pro line of services. The original intent behind Essentials was to create a “make it your own” version where companies that didn’t need Encryption or LiveArchive could save a few bucks and get an enterprise product that scaled with the organization as it’s demands grew.
We’re hoping that announcing the phasing out of the current licensing will give existing leads an incentive to get signed up and grandfather in the features at a discount.
How to Protect Yourself from Domain Spoofing and Phishing with ExchangeDefender

At ExchangeDefender we want you to be safe online. One of the biggest and best steps you can take towards that goal is to both protect your domain from being “spoofed” (forged by a spammer) and to block any such forgeries from arriving into your mailbox.
About Spoofing
Spammers and hackers routinely abuse domains that do not have a SPF or DKIM record. They configure their email software to use your domain name for a SPAM campaign or to launch sophisticated phishing attacks. If you’ve ever received an email from yourself, or from a forged government or corporate entity, you’ve been a victim of spoofing. If you’ve ever received thousands of rejections and delivery receipts for messages you never sent, you’ve been a victim of spoofing. Because so many domain owners do not take responsibility for their DNS configuration, this is the most widely abused mechanism.
Good news is, ExchangeDefender can help protect you from these attacks and brand misuse through implementation of SPF, DKIM, and our corporate policies.
SPF (Sender Policy Framework)
ExchangeDefender uses SPF to verify that the email is coming from a source that your organization trusts to send messages. This is typically your email server, our email server, and sometimes a business application (like a hosted CRM) that sends email using your domain name. All others get rejected as forgeries.
How do you setup your SPF record? Simply go to wherever your domain name is hosted (your name server) and add this TXT field to your zone. You may need assistance from your ISP, domain registrar, or whoever is actually running your name servers. If you don’t know who that is, or they are too difficult to use, ExchangeDefender will host your domain free of charge. The TXT record will not have a hostname and the value should be set to the following:
Hostname:
Record type: TXT
Value: v=spf1 include:proxy.exchangedefender.com -all
DKIM (Domain Keys)
ExchangeDefender uses DKIM to validate automated digital signatures. We also sign messages for all customers that rely on ExchangeDefender to send outbound mail (pretty much everyone). This is a 2 step process similar to SPF.
Step 1: Request public key
Go to https://support.ownwebnow.com and open a ticket requesting signatures of your outbound mail. Please specify which domains you wish to sign because each domain must have its own set of keys.
Step 2: Create a DKIM public record
Go to wherever your DNS is hosted and just like in SPF, create a DKIM record:
Hostname: default._domainkey
Record type: TXT
Value: v=DKIM1; k=rsa; s=email; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC0SXzBGHoJcBVKyNEntvTiMtoSIH4uiuY6i5hzF47
A2eYb4pB/gtsHpP1vpDgzZvwVLz65nQwnm4wvSFsarKwCyWYyvGwPvBd9+v2Jcrk5dsfHioUDZo5oSvbRY
+e8AD7eo42A/pYdgZxL9KRyZbMsCtHJrAqvYB6LZP0SFVvkYQIDAQAB
Important: This is just an example. You will need to use your own public key generated in Step 1 and provided by us. Also, the value of the TXT record has to be on the same line, if there are any line breaks (if you copy it from an email or web page) please remove them.
Step 3: Update the ticket with us to test deployment
After the DNS record has been created for your domain, we will validate it and if configuration is valid we will start signing your outbound messages going through ExchangeDefender.
After the DNS record has been created for your domain, we will validate it and if configuration is valid we will start signing your outbound messages going through ExchangeDefender.
ExchangeDefender Policy
While we encourage all of our clients to implement both SPF and DKIM, we understand that there are sometimes business scenario cases under which this is impossible. If you find yourself in this predicament you should immediately change where your name servers are hosted and take full control of your organizations identity online. But if that is still something you may not be able to do, ExchangeDefender can still protect you from phishing attacks and spoofing launched using your own domain name. If you’ve ever received email from yourself or from a colleague (but the email actually came from a server in Poland) then this setting will help you.
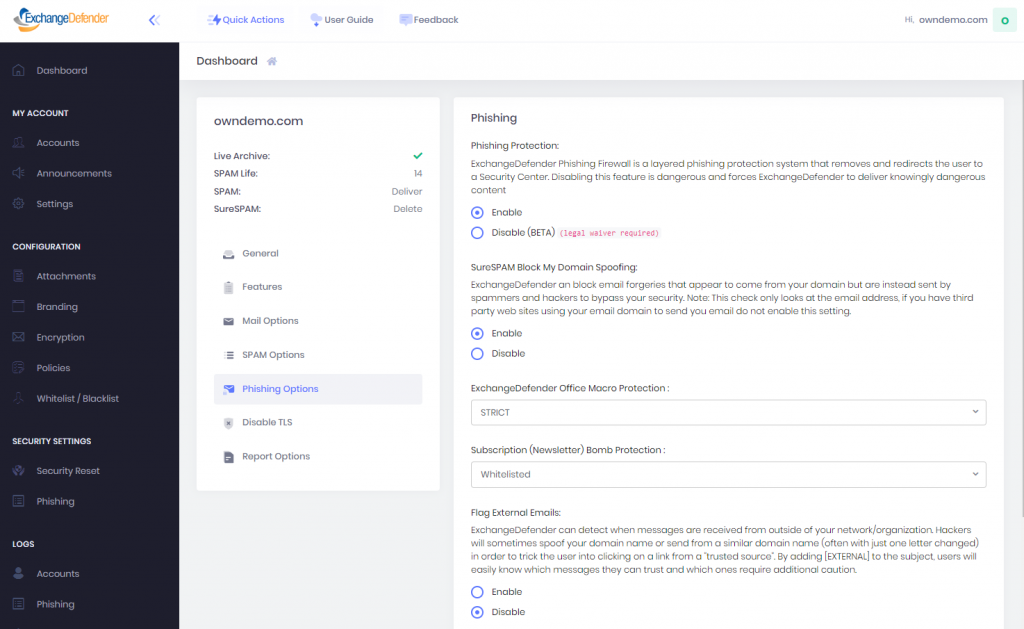
Go to https://admin.exchangedefender.com and login as the domain administrator (username is your domain name).
Click on Security Settings > Phishing
Under “Flag External Emails” click on Enable and then Save.
After this setting is applied, all messages from your domain that were sent from outside of the ExchangeDefender network will go into the SureSPAM quarantine. Just tell users not to trust, whitelist, or release messages that are coming from your own domain because they are certainly not legitimate.Note: This is the option of last resort and will not stop hackers or spammers from abusing your domain for phishing, spamming, or hacking. However, it will stop those messages from arriving directly into your users mailbox. If you already have a valid SPF record (with -all, not ~all) and DKIM in production, this setting is not necessary as ExchangeDefender will automatically reject messages that fail SPF/DKIM validation.
If you have any questions or concerns about ExchangeDefender and implementation of SPF, DKIM, or phishing policies please feel free to contact us.
ExchangeDefender vs. Hacked Exim/cPanel servers

ExchangeDefender has been seeing an elevated amount of malware originating from hacked Exim mail servers. While we tend to score those messages higher by default to keep our clients protected, one of our clients discovered a scenario in which a user could get a dangerous payload through our scanners (requires multiple manual steps and a sophisticated recipient with imaging software willing to go through multiple hoops). Which this is exceptionally unlikely, we wanted to address a few of the topics anyhow.
1. CIOs, MSPs, and Domain Administrators can manage attachment policies
If you go to https://admin.exchangedefender.com and login as the Domain Administrator, you can manage attachment policies under Configuration > Attachments. You can find more about ExchangeDefender configuration at https://www.exchangedefender.com/docs/domain#configuration
2. We do not deep-scan file system images (.iso/.img)
As a policy we do not deep scan .iso or .img file system images. The files themselves are scanned for both malware, viruses, and other parameters (for example, if someone renames a .exe to .img, or embeds malware in one we will still filter it out) but we will not mount file system images and go through each file inside. This is not a popular attack vector (requires multiple actions by the user and most will require Administrative access and specialized software) but it is technically possible.
3. You should implicitly distrust anyone on hacked Exim servers
ExchangeDefender cannot globally block Exim servers (because there is always going to be that one “business case scenario!!! we cannot block our $2 cPanel VPS!”) but if you can possibly block them – by all means do. While this is generally not necessary (ExchangeDefender maintains a proprietary list of pwn3d Exim servers and routinely moves them to SPAM or SureSPAM), it’s a good idea not to accept any mail from these servers at all.
4. You should implicitly junk SPF failures
Same as #3, it’s a really good idea if you have the luxury of not dealing with people that shouldn’t be running an email server. ExchangeDefender tracks SPF failures and notes them in the headers that can be used to aggressively filter out messages sent out from invalid ranges. Just look for a “Received-SPF: softfail” in the message headers.
Received-SPF: softfail (inboundXX.exchangedefender.com: domain of transitioning postmaster@gmail.com does not designate 67.82.55.11 as permitted sender)
What this means is that the organization has designated an IP range that legitimately relays messages, and this message came from an IP address outside of that range. 99.99999% of the time it’s a spammer. 0.00001% of the time it’s just a poorly configured server. It’s your choice to assess the risk and implement this if possible and we recommend it.
Finally, if you are actively monitoring security and communicating with your clients, we do manage a NOC site that logs major issues at https://www.anythingdown.com. If you’re one of our MSP or enterprise clients, you also have a branded version of this software free of charge at https://www.xdnoc.com that you can attach your domain name to and offer these alerts to your clients without copying and pasting around.We hope this helps and we appreciate your trust in keeping you safe online.
For more information, please see our ExchangeDefender Guide for Domain.