The Anatomy of a Phishing Email (With Examples)

Phishing emails have come a long way from the hilariously obvious scams of the early 2000s. Today, they’re more convincing, better designed, and — worst of all — more effective. Knowing how to spot a phishing email can mean the difference between avoiding a breach… or becoming the next cautionary tale.
Let’s break down the anatomy of a phishing email — using real examples and highlighting the red flags you should never ignore.
What is Phishing?
Phishing is a type of social engineering attack where cybercriminals pose as trusted entities to trick people into giving up sensitive information — like passwords, credit card numbers, or access credentials. These emails may look like they’re from your boss, your bank, or even your favorite app.
Key Elements to Watch For
Let’s dissect a classic phishing email and highlight where the danger hides:
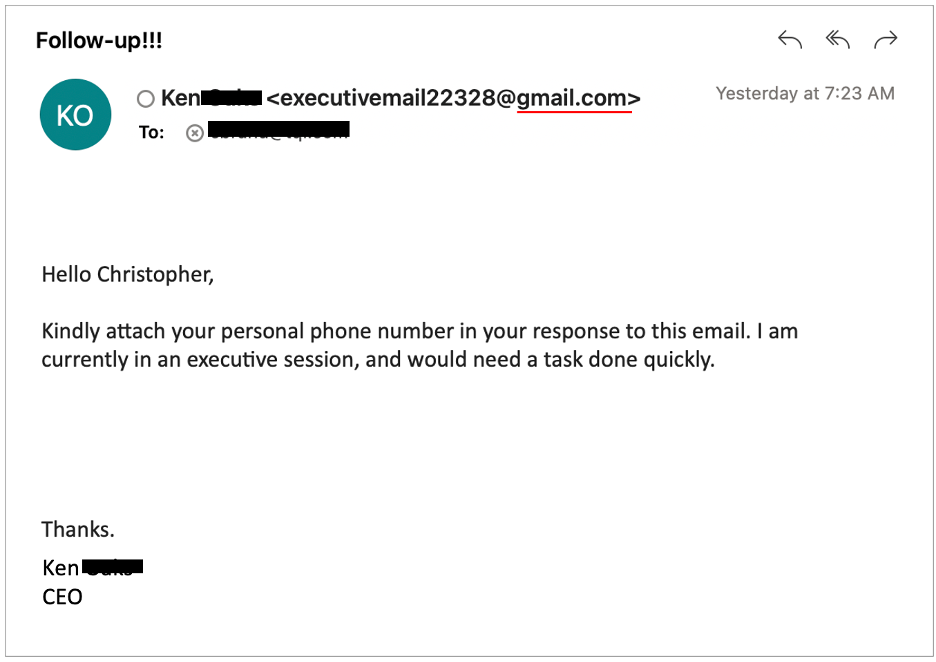
1. Weird or Slightly Off Email Address
Example: ceo@exchanqedefender.com instead of ceo@exchangedefender.com
A single letter can be all it takes to trick someone. Always double-check the sender’s email. If it looks “off,” it probably is.
👉 Pro Tip: Hover over the sender’s email or tap to reveal full details.
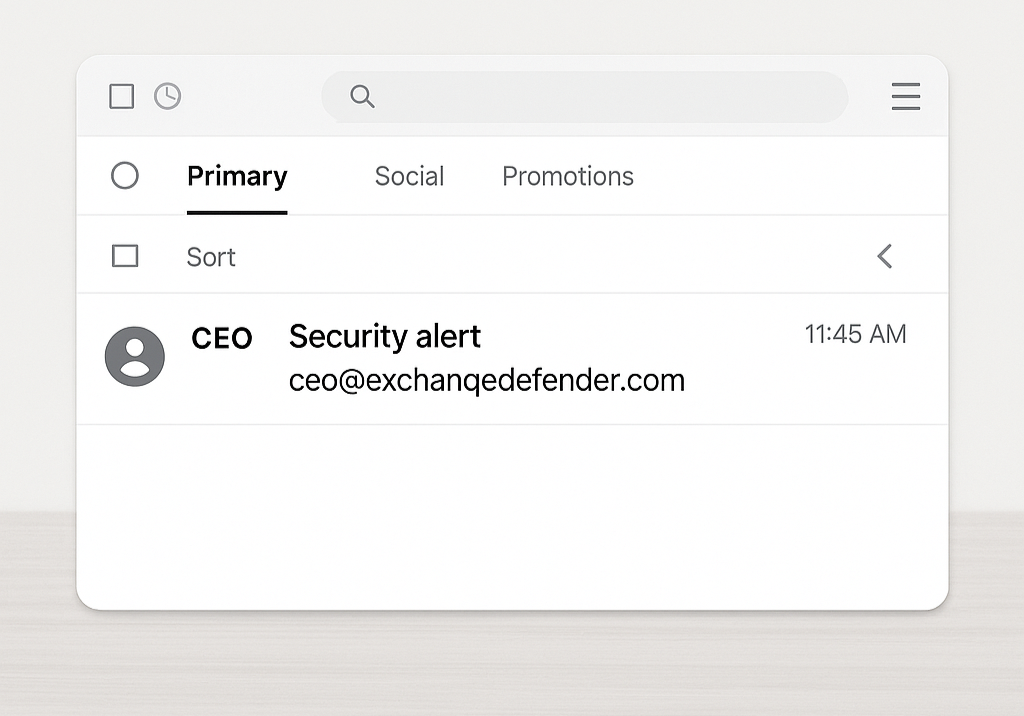
2. Urgent or Threatening Language
Example: “Your account has been suspended due to suspicious activity. Click below to restore access.”
Scammers want you to act fast without thinking. Anything that demands “immediate action” is likely designed to panic you into clicking.
3. Generic Greetings
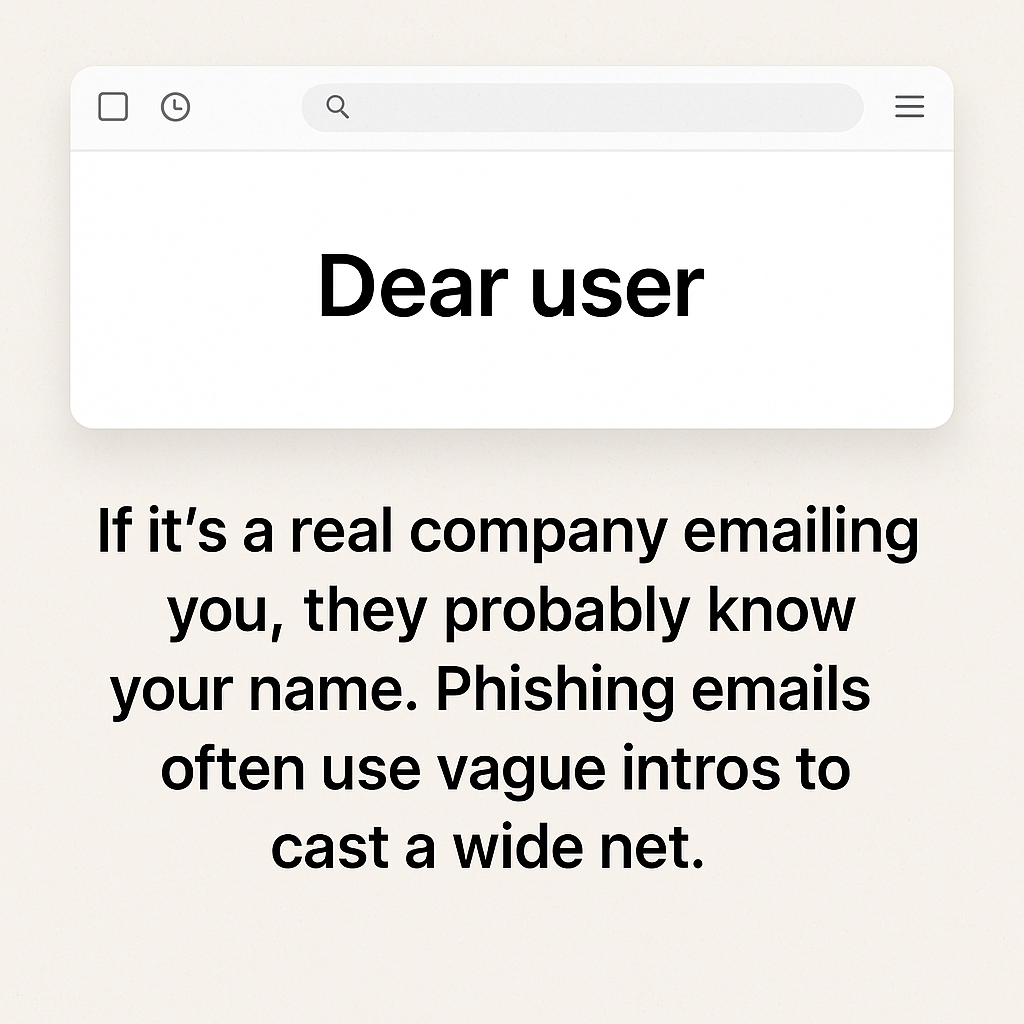
Example: “Dear user” or “Hi customer”
If it’s a real company emailing you, they probably know your name. Phishing emails often use vague intros to cast a wide net.
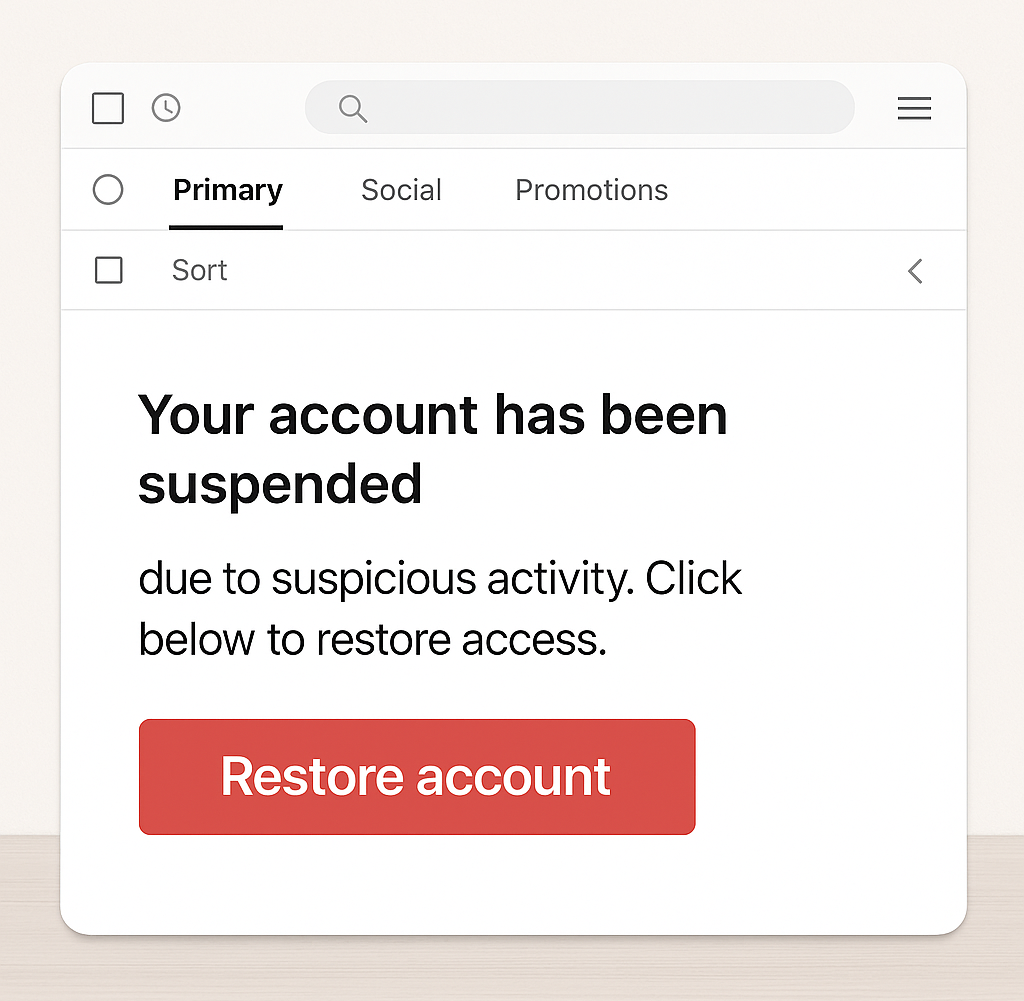
4. Suspicious Links or Attachments
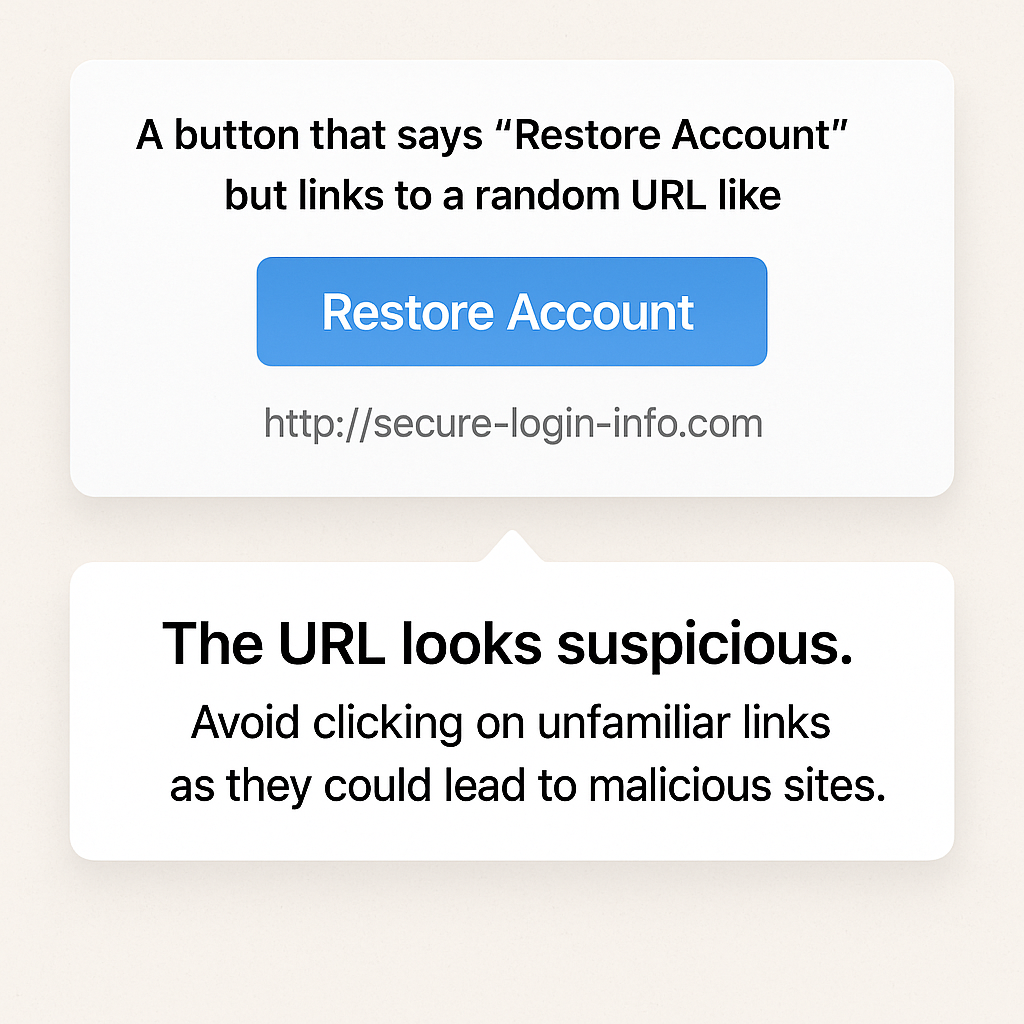
Example: A button that says “Restore Account” but links to a random URL like http://secure-login-info.com
Always hover before you click. If the URL doesn’t match the legitimate site, run far away (and don’t open attachments either).
5. Spelling + Grammar Errors
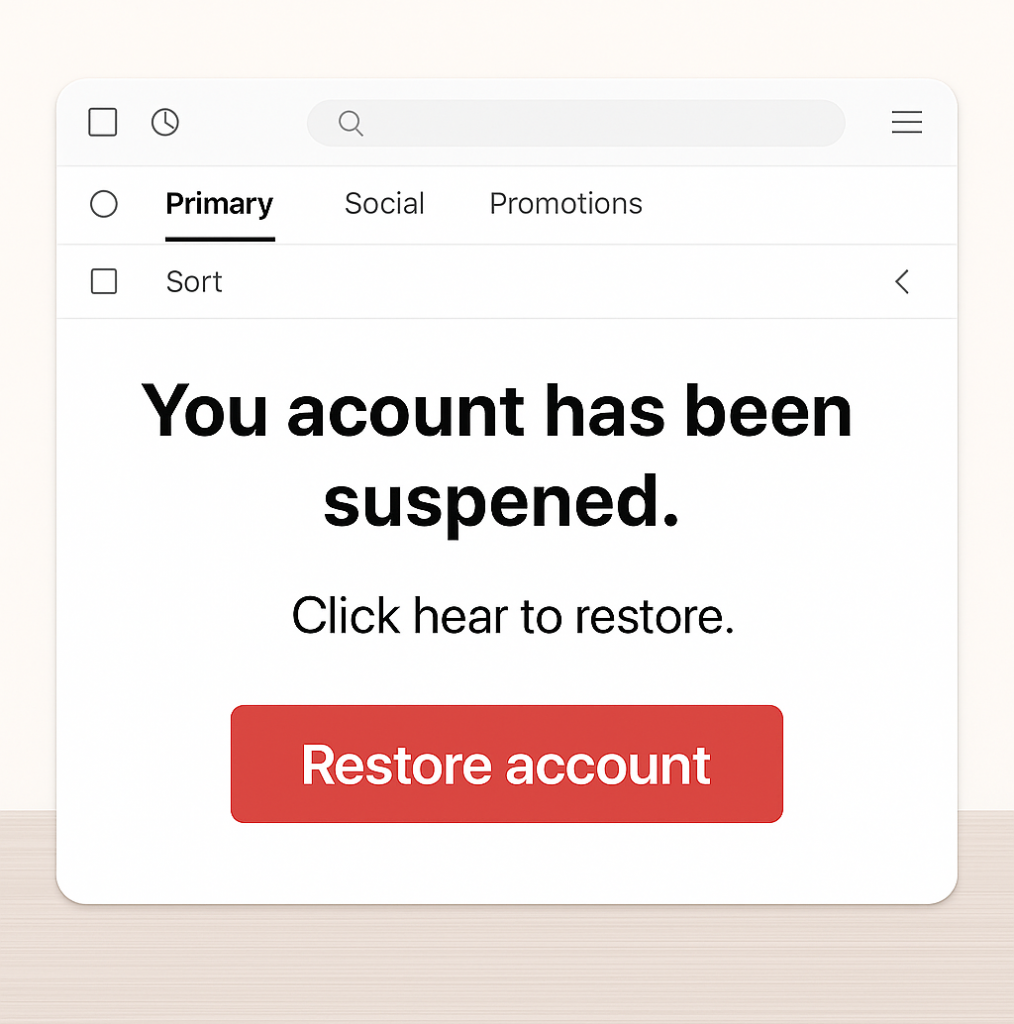
Even today, many phishing emails are riddled with typos and weird formatting.
Example: “You acount has been suspened. Click hear to restore”
You’d be surprised how many people overlook this — don’t be one of them.
✅ How to Protect Yourself
- Slow down. Urgency is a tactic.
- Verify. If in doubt, call or message the sender directly (don’t reply).
- Train your team. Run phishing simulations regularly.
- Use protection. Email filtering tools like ExchangeDefender can stop threats before they hit your inbox.
Phishing emails rely on one thing: human error. But with awareness, training, and the right tools, you can turn your team into a human firewall. Learn what to look for — and don’t let the phish hook you.
Want to test your team’s phishing detection skills?
👉 Try our free phishing simulation today
Stay safe. Stay alert. Stay unphished.
CBE Group Scams: How to Stay Safe from Fake Debt Collectors
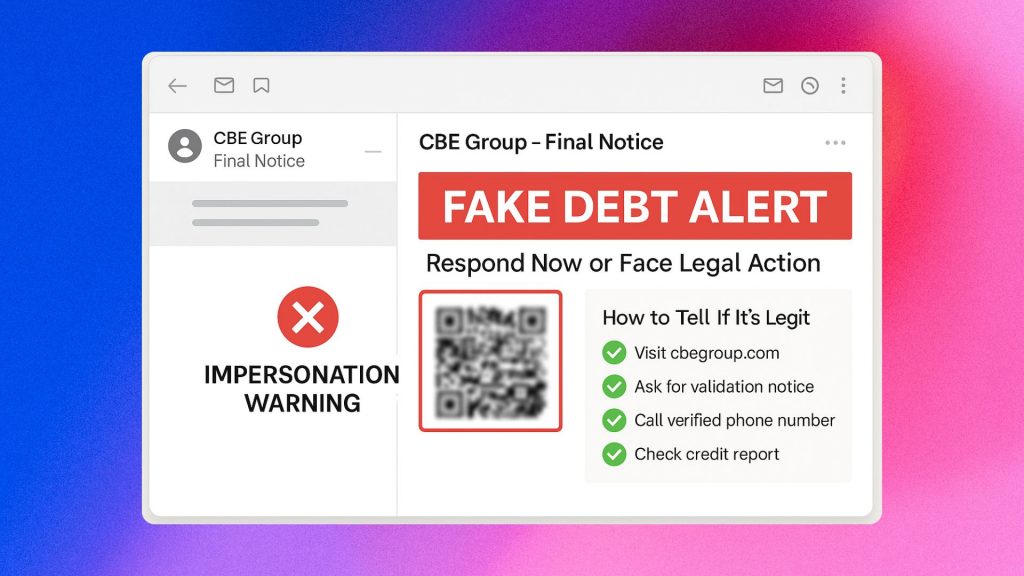
Scammers are getting more creative — and now, they’re impersonating trusted names like The CBE Group, Inc., a legitimate debt collection agency, to defraud unsuspecting victims. These scams are not only spreading by phone but also through email, text, and QR codes, making them especially dangerous for businesses and individuals alike.
At ExchangeDefender, we’re committed to helping you recognize these threats before they do damage.
First, What Is the Real CBE Group?
The real CBE Group is a licensed debt collection company based in the U.S. They work with federal, state, and private creditors, and they may contact you via:
- Phone
- Letter
But here’s the key difference: they follow the law and won’t pressure you into shady payment methods or scare tactics.
Common CBE Group Scam Tactics to Watch For
1. Fake Debt Collection Calls
Scammers impersonate “CBE agents” and use:
- Threats of arrest or legal action
- Demands for immediate payment
- Calls that feel rushed or overly aggressive
2. Spoofed Caller ID
- The call appears to be from a CBE Group number.
- Uses robocalls or a script to lure you in.
3. Phishing Emails or Texts
- Fake QR codes or links saying “Resolve Your Debt.”
- Redirects you to malware, phishing sites, or fake login pages.
4. Unusual Payment Requests
- Gift cards, cryptocurrency, Venmo, or Zelle? 🚫 Huge red flag.
- No legitimate collector will ever ask for these.
5. Bogus Case Numbers or Settlements
- “You’re being sued.”
- “We can settle this now — but you must act fast.”
- These are pressure tactics to catch you off guard.
🔍 How to Tell If It’s Really CBE
Before you respond or pay anything, do your due diligence:
- Visit the official site: https://www.cbegroup.com
- Ask for a written validation notice (required by law)
- Call CBE directly using verified contact info
- Check your credit report — is the debt even real?
⚠️ What to Do If You’re Contacted
If you get a suspicious message claiming to be from CBE Group:
- Don’t click any links or scan QR codes.
- Don’t provide personal, financial, or login info.
- Hang up, then call the real CBE Group or check their website.
- Report the scam to the:
- Federal Trade Commission (FTC)
- Your state’s Attorney General
🛡️ How ExchangeDefender Protects You
Scammers may use legitimate-looking emails, domains, or QR codes to target you. Our advanced threat protection tools filter out spoofed emails, phishing attempts, and malicious content before it ever hits your inbox.
🔐 Want to ensure your organization stays safe?
Reach out to ExchangeDefender today for enterprise-grade protection against phishing, fraud, and impersonation.
New Scam Alert: Coinbase Phishing Emails Making the Rounds
There’s a fresh scam in town, and it’s after your crypto.
Scammers are sending highly convincing emails that look like they’re from Coinbase, warning users of account restrictions or suspicious logins. These messages urge you to “verify your account”—but it’s a trap. A well-disguised one.
What Makes This One So Dangerous?
Unlike typical junk mail, this phishing campaign is:
- Well-designed with real Coinbase branding
- Free of typos and grammar fails
- Carefully crafted to trigger panic clicks
Once you click, you’re led to a nearly identical login page where your credentials (and potentially your wallet) are stolen.
What To Watch For:
- Emails from sketchy or lookalike domains
- Urgent calls to action: “Verify Now”, “Your Account Is Suspended”, etc.
- Fake login pages (hover links before clicking!)
Pro Tip: Coinbase emails always come from @coinbase.com. Anything else = 🚩
🛡️ How ExchangeDefender Has Your Back
When you use ExchangeDefender’s advanced threat protection, you’re not just hoping Gmail will catch it.
You’re getting:
✅ Real-time phishing detection
✅ Dangerous link filtering
✅ Quarantine control with full transparency
✅ Education tools to keep your team aware and alert
We don’t just filter spam—we weaponize your inbox against scams like this.
What To Do Now:
- Update your 2FA and passwords—especially for financial accounts
- Bookmark real login pages—never trust links from emails
- Enable email security tools like ExchangeDefender
- Forward phishing emails to security@coinbase.com
- Educate your users—because one bad click can cost you big
🔐 Stay Safe, Stay Smart
Crypto is exciting—and so are the people trying to steal it. These attacks are only getting smarter, so it’s up to us to stay two steps ahead.
🧰 Want to learn how ExchangeDefender can protect your business from phishing and email threats?
👉 Let’s Talk.
The Truth About SPF, DKIM & DMARC (Made Simple)

Let’s be honest—email security terms like SPF, DKIM, and DMARC sound like alphabet soup mixed with cybersecurity gibberish. But if you’ve ever wondered how spam gets caught, how scammers spoof emails, or why legit messages sometimes land in junk folders… this is for you.
We’re breaking down the big 3 of email authentication—in plain English—so you know exactly what’s happening behind the scenes when you hit “Send.”
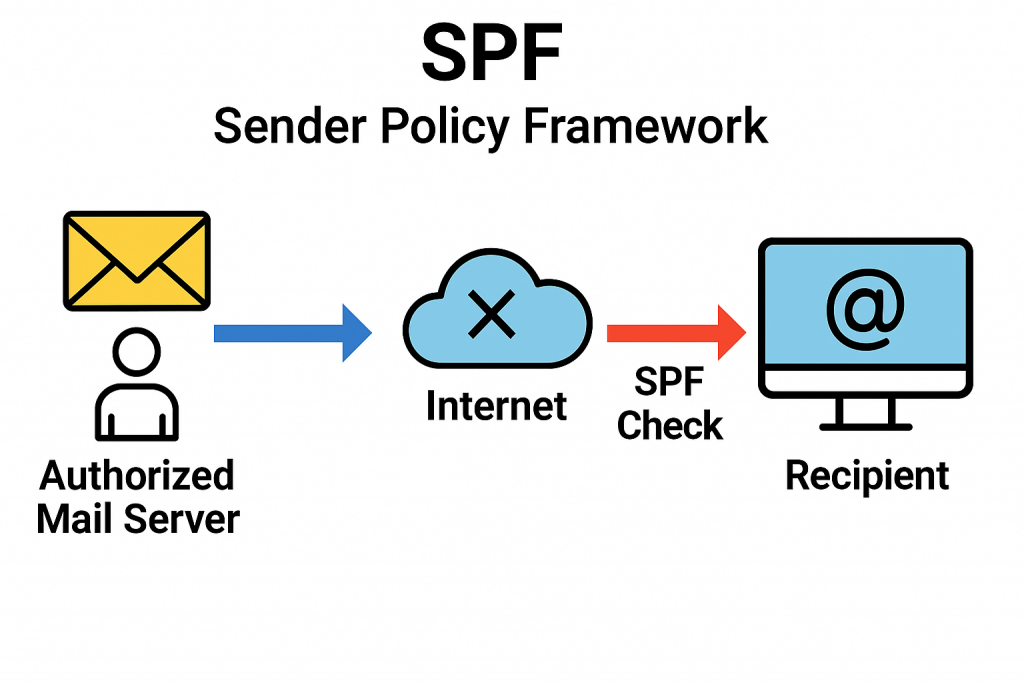
🛡️ SPF – Sender Policy Framework
What it does:
SPF tells the world which servers are allowed to send emails on your behalf.
Real-world example:
Think of SPF like a bouncer at a club. Your email server hands over a guest list (SPF record) at the door. If someone tries to get in wearing your domain name but isn’t on the list? Denied.
Why it matters:
It helps stop spammers from pretending to be you—but on its own, it’s not foolproof.
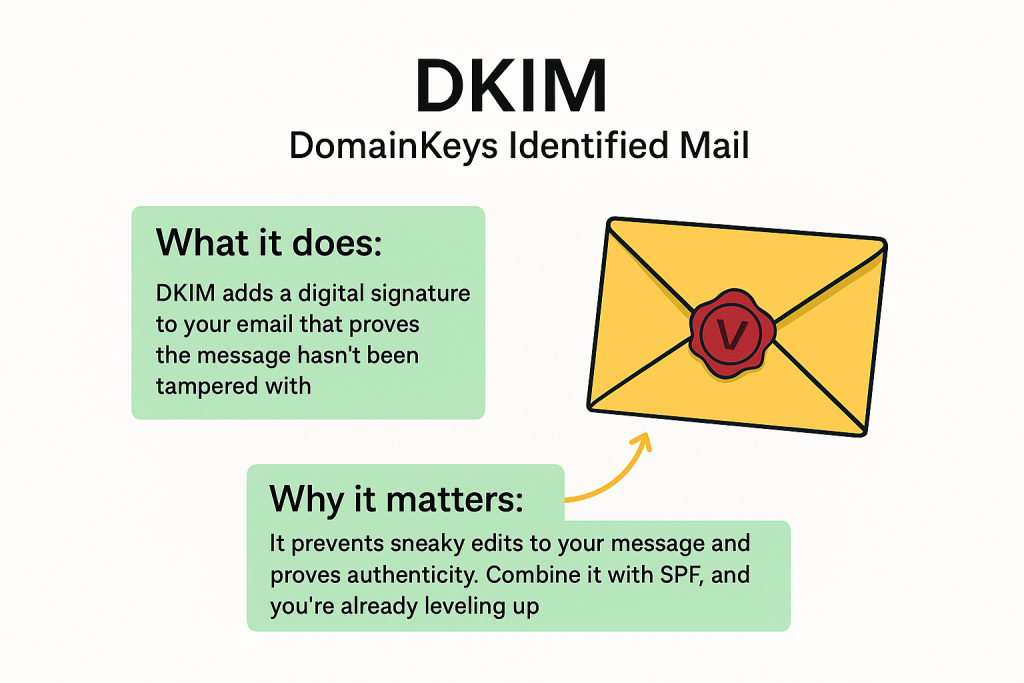
🧾 DKIM – DomainKeys Identified Mail
What it does:
DKIM adds a digital signature to your email that proves the message hasn’t been tampered with.
Real-world example:
Imagine sealing a letter with a wax stamp. If the seal’s broken, you know something’s up. DKIM is your email’s digital seal, verifying that it really came from you—and nothing changed in transit.
Why it matters:
It prevents sneaky edits to your message and proves authenticity. Combine it with SPF, and you’re already leveling up.
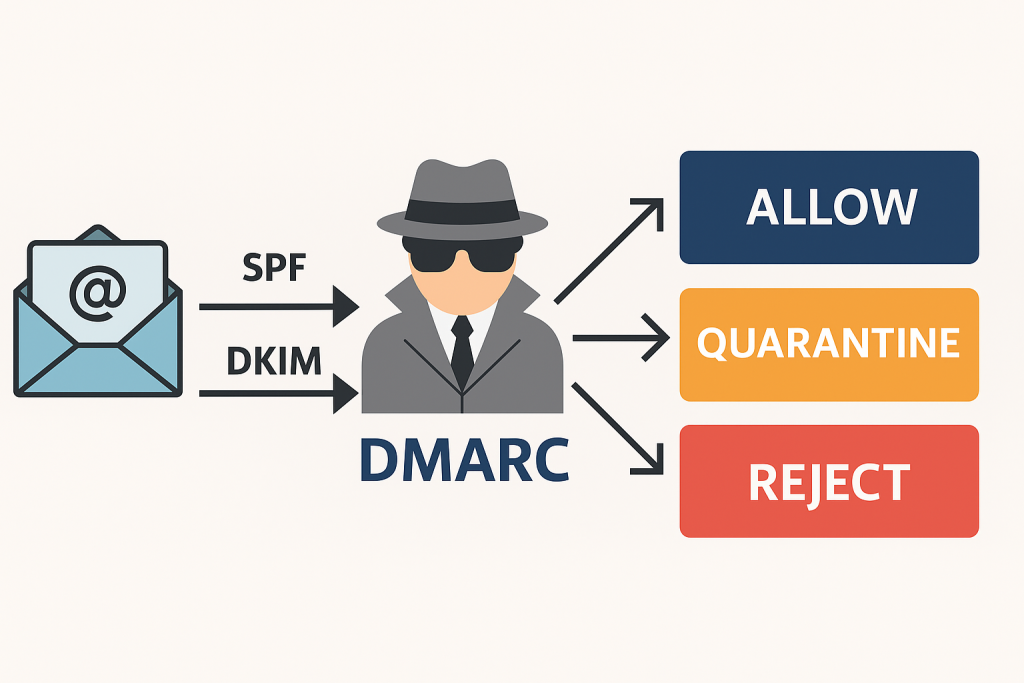
🕵️♀️ DMARC – Domain-based Message Authentication, Reporting & Conformance
What it does:
DMARC is like the manager that makes sure SPF and DKIM are actually being followed—and decides what happens when something fails.
Real-world example:
Let’s say someone shows up at your email club with a fake ID. DMARC is the one that decides: “Should we let this slide, quarantine them, or kick them out completely?”
Why it matters:
DMARC tells mail providers how to handle sketchy emails that claim to be from you. It also gives you reports so you can see who’s spoofing your domain.
🔒 Why Should You Care?
Because your email reputation = your digital trust. If you send emails from your business domain and don’t have SPF, DKIM, and DMARC properly set up, you’re basically telling the internet, “Hey, anyone can pretend to be me!”
That leads to:
- More emails going to spam
- Higher chance of getting spoofed or blacklisted
- Less trust from customers, vendors, and partners
✅ How ExchangeDefender Helps
We make email security easy, even if you don’t speak fluent geek. ExchangeDefender includes tools to:
- Set up and manage SPF, DKIM, and DMARC
- Monitor spoofing attempts
- Keep your reputation clean and your messages trusted
🧠 TL;DR
- SPF = Who can send your email
- DKIM = Prove it wasn’t tampered with
- DMARC = Enforce the rules + get reports
If you’re not using them, your email could be getting filtered—or worse, faked.
Ready to secure your domain like a pro? Let us help → www.exchangedefender.com
Why Email Backup Should Be Part of Your Disaster Recovery Plan

Because when your inbox goes dark, your business shouldn’t.
🚨 The Problem: Email Outages Happen
Imagine this: a sudden power outage, a server crash, or a cyberattack strikes. Your team can’t send or receive emails. Projects stall, client communications halt, and productivity plummets. It’s not just inconvenient—it’s a business risk.
🛡️ The Solution: Email Backup with ExchangeDefender LiveArchive
Enter ExchangeDefender LiveArchive—your safety net when email systems fail. LiveArchive ensures uninterrupted access to your emails, even during outages. Here’s how it supports your disaster recovery plan:
- 24/7 Email Access: Keep your team connected with continuous email availability.
- Seamless Integration: Works alongside your existing email infrastructure without disruption.
- Real-Time Archiving: Automatically backs up emails, ensuring no data loss.
- User-Friendly Interface: Access archived emails easily through a web portal.
📈 Why It Matters
Incorporating email backup into your disaster recovery strategy isn’t just smart—it’s essential. It minimizes downtime, protects sensitive information, and maintains client trust. With LiveArchive, your business stays resilient, no matter what.
Don’t let an email outage derail your operations. Integrate ExchangeDefender LiveArchive into your disaster recovery plan today.
Top 5 Email Threats You Didn’t Know Were Hiding in Your Inbox

Let’s face it—email is the lifeblood of modern business. But behind every “urgent” subject line or familiar sender name, there could be something much more sinister lurking. At ExchangeDefender, we spend our days defending inboxes against threats most people don’t even know exist. So today, we’re spilling the secrets. Here are 5 sneaky email threats that could be hiding in plain sight:
1. Lookalike Domains (a.k.a. Evil Twins)

These emails come from addresses that look legit—maybe a single letter off from your CEO’s real email, or a domain that’s cleverly misspelled.
Why it’s dangerous: They’re made to trick you into clicking links or wiring money.
How we stop it: ExchangeDefender uses advanced domain and sender verification to block imposters fast.
2. Zero-Day Attachments
These are brand-new threats that haven’t even made it to antivirus databases yet. They come disguised as invoices, resumes, or project files.
Why it’s dangerous: Traditional filters might miss them.
How we stop it: Real-time scanning and sandboxing help catch unknown threats before you open them.
3. Credential Harvesting Links
Not all phishing scams are loud and obvious. Some hide in the form of password reset requests or shared documents.
Why it’s dangerous: One click can expose your login—and open the door to your entire system.
How we stop it: Link analysis and real-time URL scanning keep you protected, even from shortened or masked links.
4. Conversation Hijacking
Hackers insert themselves into real email threads and respond like they’re part of your team. Creepy, right?
Why it’s dangerous: You’re more likely to trust something that feels familiar.
How we stop it: Behavioral monitoring flags unusual responses—even when they happen mid-thread.
5. Impersonation of Internal Staff
Ever get a weird request from “Accounting” or “HR”? Sometimes, attackers mimic your internal teams to request sensitive info or payments.
Why it’s dangerous: These attacks rely on trust and internal knowledge.
How we stop it: ExchangeDefender uses AI and policy enforcement to detect when internal communication doesn’t add up.
So, What Can You Do?
Well, you already did the first step: you’re here. 🧠👏
The next step? Put a solution like ExchangeDefender Email Security between your team and the bad guys. We’re built to detect, block, and neutralize all of these threats—before they hit your inbox.
Because email should be for collaboration, not chaos.
👉 Learn more about how ExchangeDefender protects your business: https://exchangedefender.com/email-security
Email Outages Are Inevitable—Downtime Doesn’t Have to Be

We all know that email is the backbone of business communication. A disruption in email services can halt operations, delay responses, and impact customer trust. Recent events, such as the Microsoft Outlook outage in March 2025, left thousands without access to their emails, highlighting the vulnerability of relying solely on a single email provider.
The Business Impact of Email Downtime
When email services go down, the consequences can be severe:
- Operational Delays: Employees unable to access emails may miss critical deadlines and meetings.
- Customer Dissatisfaction: Delayed responses can frustrate clients and damage relationships.
- Financial Losses: Interruptions can lead to missed opportunities and revenue losses.
Introducing ExchangeDefender Inbox
To combat these challenges, ExchangeDefender offers Inbox — a robust email continuity solution designed to keep your business running smoothly during email outages. Inbox provides:
- Uninterrupted Access: Continue sending and receiving emails even when your primary service is down.
- Seamless Integration: Works alongside platforms like Outlook, Gmail, and Yahoo without the need for additional installations.
- Secure Storage: Automatically archives inbound and outbound emails for up to a year, ensuring data is always retrievable.
- User-Friendly Interface: Accessible on all modern devices, allowing your team to stay connected from anywhere.
Stay Prepared with ExchangeDefender Inbox
Email outages may be inevitable, but downtime doesn’t have to be. With ExchangeDefender Inbox, ensure your business remains responsive, reliable, and resilient.
Discover more about how Inbox can safeguard your communications: ExchangeDefender Inbox
Keep up with ExchangeDefender Changelog

When we launched our new user interface infrastructure, we did so that we could run ExchangeDefender at the cutting edge. By bringing all of our apps under one umbrella, we can now monitor and address bugs and performance issues in real-time.
The pace of development has really picked up, and when things are constantly improving, it’s important to keep everyone informed when issues get addressed and bugs get fixed. At https://admin.exchangedefender.com, when you log in as a Domain Administrator, you will now see a new Announcements button on the bottom right.
You can view our announcements on this screen (same content that is available on the login screen) and you can click on the Changelog to see our recent changes. This way you can see what is being added and fixed, and we can track it back to the original issue report.
We owe a huge thank you to our partners and clients for feature suggestions and bug-fix help last month, we are working hard to keep the web apps at the top security and industry standards because this is how people exchange sensitive information and we take great effort to make that easier and more secure.
How Secure File Sharing Enhances Remote Team Collaboration

In today’s increasingly remote work environment, teams often face challenges when sharing large files securely and efficiently. Traditional methods like email attachments or outdated file servers can be cumbersome and pose security risks. ExchangeDefender’s Web File Server (WFS) offers a solution tailored to these needs, facilitating seamless and secure collaboration across different locations.
Challenges in Remote File Sharing
Remote teams frequently encounter issues such as:
- File Size Limitations: Email systems often restrict attachment sizes, making it difficult to share large documents.
- Security Concerns: Transferring sensitive information without robust security measures can lead to data breaches.
- Lack of Real-Time Collaboration: Without centralized platforms, coordinating on document edits and updates becomes challenging.
How ExchangeDefender WFS Addresses These Challenges
ExchangeDefender WFS is designed to overcome these obstacles by providing:
- Unlimited File Sharing and Storage: Users can upload and share files of any size without worrying about storage limits, ensuring that large documents like contracts or design files are easily accessible.
- Enhanced Security Features: With 128-bit SSL encryption, password protection, and auto-destruction capabilities, WFS ensures that sensitive data remains secure during transit and storage.
- User-Friendly Interface: The platform’s intuitive dashboard allows users to create document libraries, manage recipients, and track activity without requiring extensive training or IT support.
- Real-Time Collaboration: Teams can work simultaneously on documents, with features like version control and activity logs keeping everyone informed of changes.
Real-World Application
A local real estate company, Orange Avenue Homes, utilizes ExchangeDefender WFS to share contracts between remote team members and clients. The platform’s ease of use and robust security features have streamlined their document management processes, enhancing overall productivity.
For remote teams seeking a reliable and secure method to share large files, ExchangeDefender Web File Server offers a comprehensive solution. Its combination of unlimited storage, advanced security, and collaborative tools makes it an invaluable asset in today’s digital workspace.
Explore more about ExchangeDefender Web File Server and how it can benefit your remote team at ExchangeDefender Web File Server.
How to Report Phishing Emails in Outlook: A Step-by-Step Guide

Phishing emails are deceptive messages designed to trick you into revealing personal information or installing malicious software. Reporting these emails helps protect your account and assists in improving Microsoft’s security measures. Here’s how you can report phishing emails in Outlook:

For Outlook on the Web (Outlook.com):
- Sign In: Log into your Outlook.com account.
- Select the Email: In your inbox, click the checkbox next to the phishing email you wish to report.
- Report as Phishing:
- At the top of the message list, click on the “Report” button.
- From the dropdown menu, select “Phishing”.
- Confirmation: The email will be moved to your Junk Email folder, and Microsoft will be notified to enhance their spam filters.
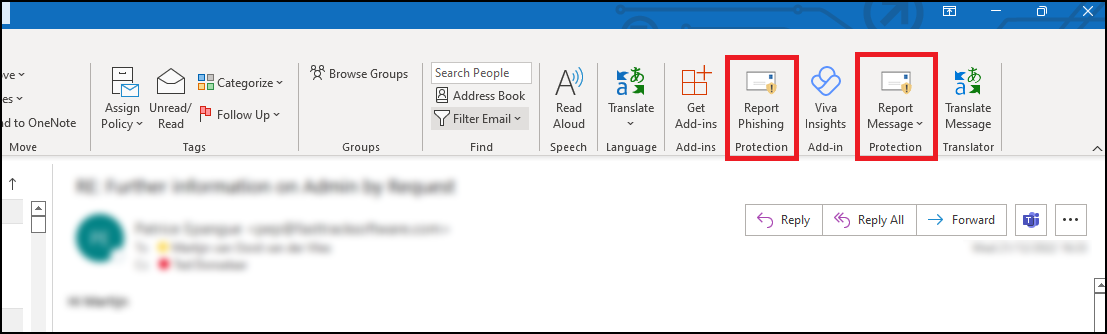
For Outlook Desktop Application (Windows):
- Open Outlook: Launch the Outlook application on your computer.
- Select the Email: In your inbox, click to highlight the phishing email.
- Access the Report Feature:
- Navigate to the “Home” tab in the ribbon at the top.
- Click on the “Report” button. If you don’t see this option, you may need to add the “Report Phishing” add-in:
- Click “Get Add-ins” in the ribbon.
- Search for “Report Phishing” and click “Add.”
- Report as Phishing:
- After adding the add-in, select the phishing email again.
- Click “Report” in the ribbon, then choose “Phishing.”
- Confirmation: The email will be moved to your Junk Email folder, and Microsoft will receive a report to improve their spam filters.
For Outlook Mobile App (iOS and Android):
- Open the App: Launch the Outlook app on your mobile device.
- Select the Email: Tap on the phishing email to open it.
- Access More Options:
- Tap the three-dot menu (⋮) at the top right corner of the email.Microsoft Support
- Report as Junk:
- Tap “Report Junk.”Microsoft Support
- Choose “Phishing” from the options provided.Microsoft Answers+1Gettysburg College+1
- Confirmation: The email will be moved to your Junk folder, and Microsoft will be notified to enhance their spam filters.
Source: Microsoft Support