ExchangeDefender Phishing Firewall and Microsoft Defender
Now and then Microsoft Defender will encounter something potentially dangerous when it’s processing your browsing activity. Most of the time it is just the URL of a site they’ve blacklisted.
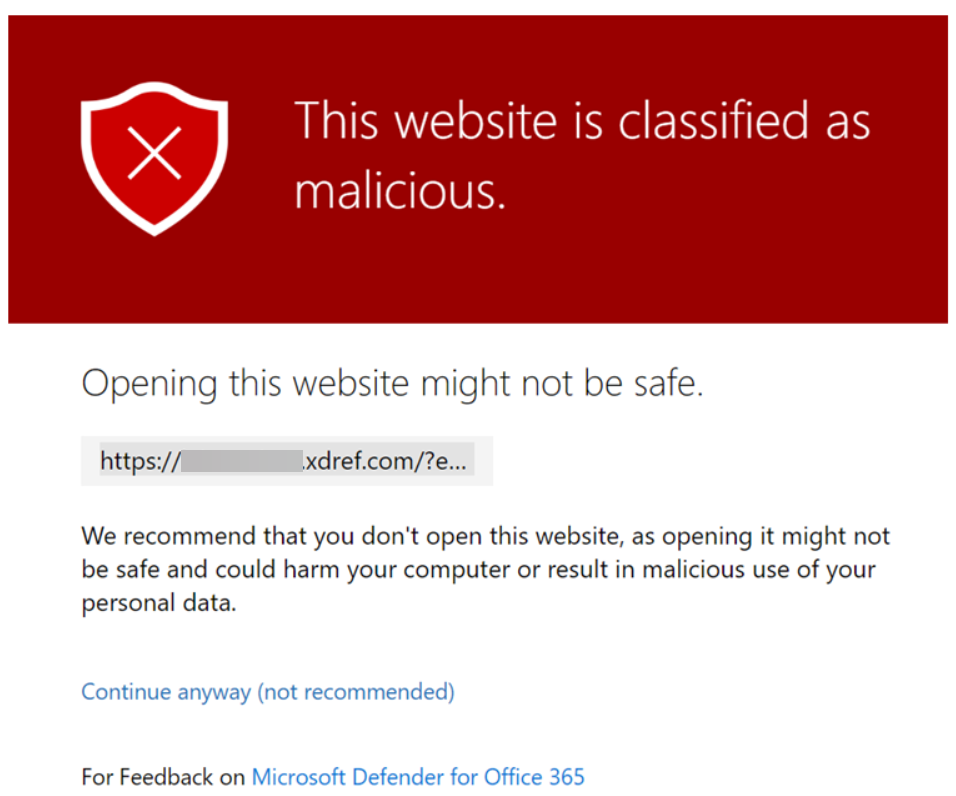
Enter ExchangeDefender Phishing Firewall. We rewrite every URL going through our service to give our users an extra layer of security and prevent malware and phishing. If you’ve seen the xdref.com links in your email, that’s US keeping you from accidentally clicking on a legitimate link and getting a zero-day exploit compromising your PC. Well, Microsoft Defender looks at the same link and its contents and can flag an entire URL of your phishing firewall. Then you end up seeing this:
How do I get this resolved?
Since this URL is exclusively used by you and your clients, make sure you’re using ExchangeDefender Outbound Service to route outbound mail (our outbound service strips all the xdref.com URLs).
Next, please report the problem with the URL to Microsoft at this location:
https://security.microsoft.com/reportsubmission?viewid=url
How do I fix it?
There are two ways to solve this problem within your tenant at Microsoft 365. The fastest way is with PowerShell:
New-TenantAllowBlockListItems -ListType Url -Allow -Entries ~xdref.com~ -NoExpiration
The more user-friendly way to allow the URL is through the Microsoft Defender Portal at the following URL (make sure you’re logged in first):
https://security.microsoft.com/tenantAllowBlockList
Microsoft tends to move its security components around a lot so if the URL changes login to the Microsoft 365 Defender Portal and go to: Policies & Rules> Threat Policies > Rules section > Tenant Allow/Block Lists.
To learn more about Microsoft Defender and how to manage its security policies on this topic please see the following KB article.
Tip: ExchangeDefender recommends executing this process when the client is onboarded, but it will work at any time.