ExchangeDefender vs. Hacked Exim/cPanel servers

ExchangeDefender has been seeing an elevated amount of malware originating from hacked Exim mail servers. While we tend to score those messages higher by default to keep our clients protected, one of our clients discovered a scenario in which a user could get a dangerous payload through our scanners (requires multiple manual steps and a sophisticated recipient with imaging software willing to go through multiple hoops). Which this is exceptionally unlikely, we wanted to address a few of the topics anyhow.
1. CIOs, MSPs, and Domain Administrators can manage attachment policies
If you go to https://admin.exchangedefender.com and login as the Domain Administrator, you can manage attachment policies under Configuration > Attachments. You can find more about ExchangeDefender configuration at https://www.exchangedefender.com/docs/domain#configuration
2. We do not deep-scan file system images (.iso/.img)
As a policy we do not deep scan .iso or .img file system images. The files themselves are scanned for both malware, viruses, and other parameters (for example, if someone renames a .exe to .img, or embeds malware in one we will still filter it out) but we will not mount file system images and go through each file inside. This is not a popular attack vector (requires multiple actions by the user and most will require Administrative access and specialized software) but it is technically possible.
3. You should implicitly distrust anyone on hacked Exim servers
ExchangeDefender cannot globally block Exim servers (because there is always going to be that one “business case scenario!!! we cannot block our $2 cPanel VPS!”) but if you can possibly block them – by all means do. While this is generally not necessary (ExchangeDefender maintains a proprietary list of pwn3d Exim servers and routinely moves them to SPAM or SureSPAM), it’s a good idea not to accept any mail from these servers at all.
4. You should implicitly junk SPF failures
Same as #3, it’s a really good idea if you have the luxury of not dealing with people that shouldn’t be running an email server. ExchangeDefender tracks SPF failures and notes them in the headers that can be used to aggressively filter out messages sent out from invalid ranges. Just look for a “Received-SPF: softfail” in the message headers.
Received-SPF: softfail (inboundXX.exchangedefender.com: domain of transitioning postmaster@gmail.com does not designate 67.82.55.11 as permitted sender)
What this means is that the organization has designated an IP range that legitimately relays messages, and this message came from an IP address outside of that range. 99.99999% of the time it’s a spammer. 0.00001% of the time it’s just a poorly configured server. It’s your choice to assess the risk and implement this if possible and we recommend it.
Finally, if you are actively monitoring security and communicating with your clients, we do manage a NOC site that logs major issues at https://www.anythingdown.com. If you’re one of our MSP or enterprise clients, you also have a branded version of this software free of charge at https://www.xdnoc.com that you can attach your domain name to and offer these alerts to your clients without copying and pasting around.We hope this helps and we appreciate your trust in keeping you safe online.
For more information, please see our ExchangeDefender Guide for Domain.
ExchangeDefender UI is a huge hit!
Last week we launched our new UI framework that will soon drive the primary user experience for all ExchangeDefender applications. The admin portal as a series of web pages that post to one another and remain in constant state of refresh is a thing of the past.
The new user interface is meant to deliver the full power of ExchangeDefender through a browser no matter what device you’re on. To say the new UI has been a hit would be a massive understatement. What we’ve heard the most is: “I love it, but…” and this post is here to give you a little tease about what is coming up next.
Saved, customized views
There are power users that want every bit of data and then there are basic users that are just trying to find a message – and we’ve gotten feedback from both. Good news, everyone will be happy with the addition of customized views:
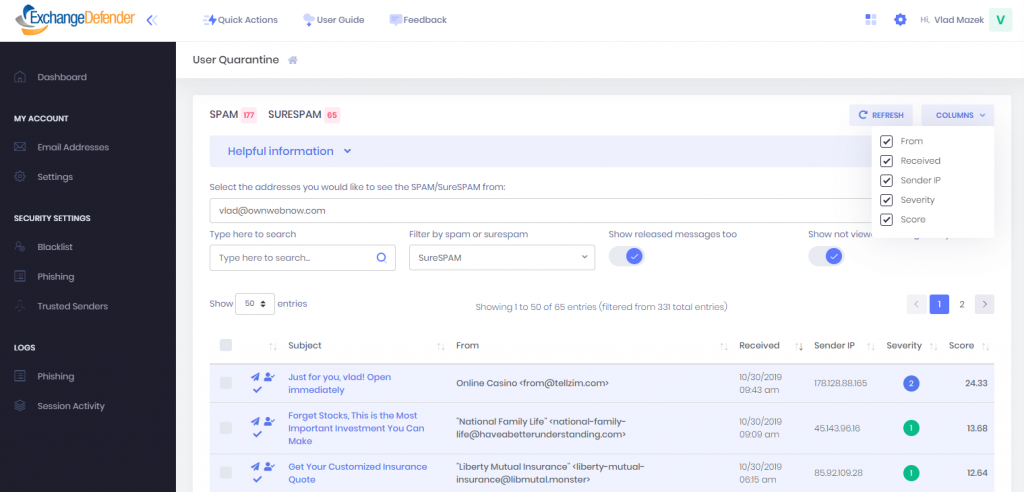
The new SPAM quarantine interface will soon give you the ability to display only the columns you want, show you messages you’ve previously released, as well as showing you only the new messages. Everyone has a preference, and once you set it ExchangeDefender will remember it. Next time you come to the quarantine view, your settings will be automatically saved.
Send emails without having email open
We’ve covered the details of the product road map in our previous webinar but to put it succinctly, not everyone in the organization needs a full 50GB mailbox, and most people rarely use more than 10% of their Outlook – definitely not something worth $180/year. When we designed the new UI we did so with full confidence that one day soon ExchangeDefender will entirely replace fat client apps, and here is a little preview of that: you can now send messages directly from ExchangeDefender:
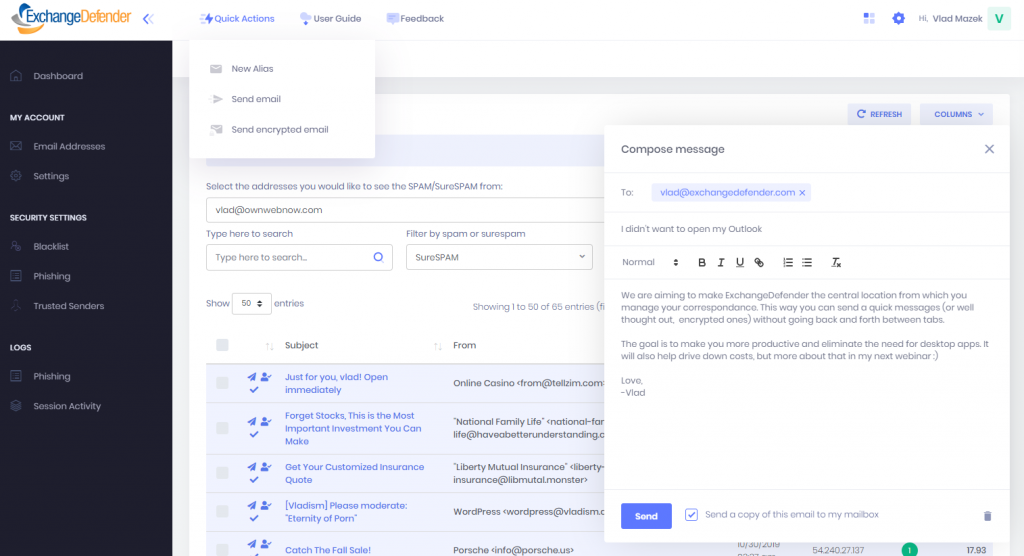
This “Send Mail” and “Send Encrypted Email” (for ExchangeDefender Encryption subscribers) shortcut will be available across the entire service because virtually every interaction ends up in a creation of something – an email response, a task (Hello Wrkoo!), a ticket, maybe even a calendar appointment – ExchangeDefender will be streamlining all of that and don’t worry, a copy of the message will be delivered to your mail server for compliance reasons.
Respond to email in real-time
One of the advantages you get with ExchangeDefender is the embedded phishing protection and security – things that would be designed to attack your Outlook or Gmail for example – will not be active in ExchangeDefender and will keep you safer by default. So if you got a sketchy message and you aren’t sure if it’s legitimate – or you no longer want the message sitting in your mailbox — you can reply directly from the ExchangeDefender message view.
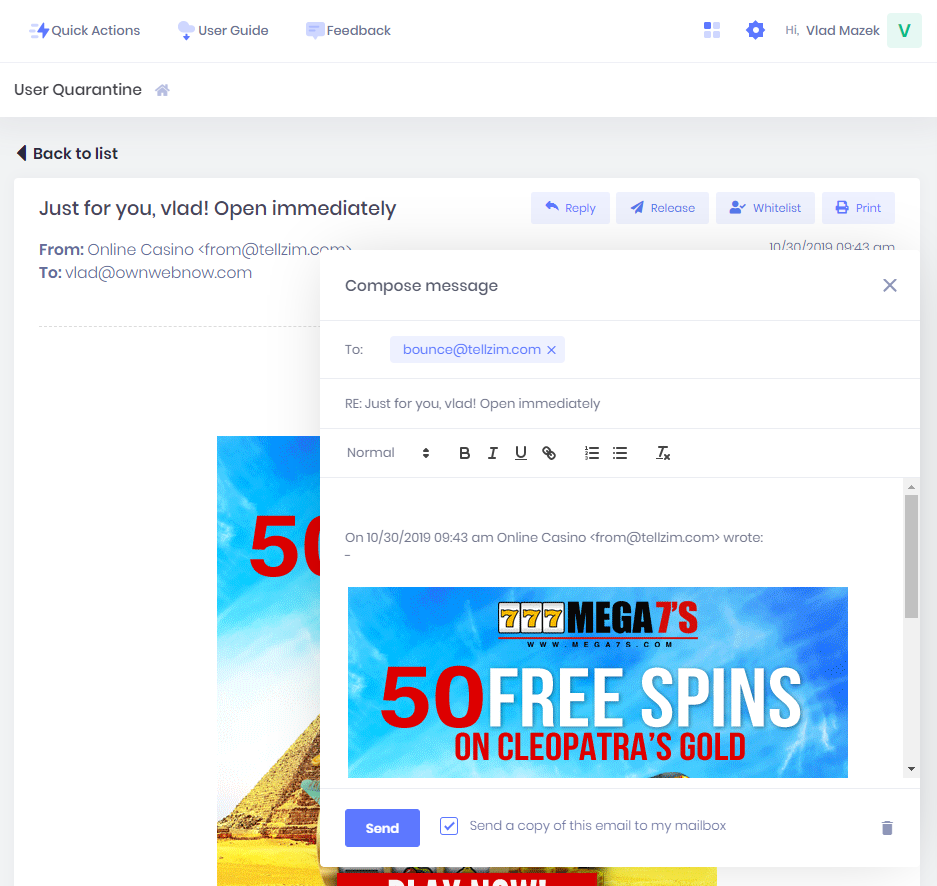
You can also forward and print the message as well, eliminating the need to release or trust a sender that may not be reputable.
Goodbye tabs & sites
We want you to do what you have to do, but faster and without a ton of open tabs. The new Dashboard look is still evolving but here is a sneak peek:
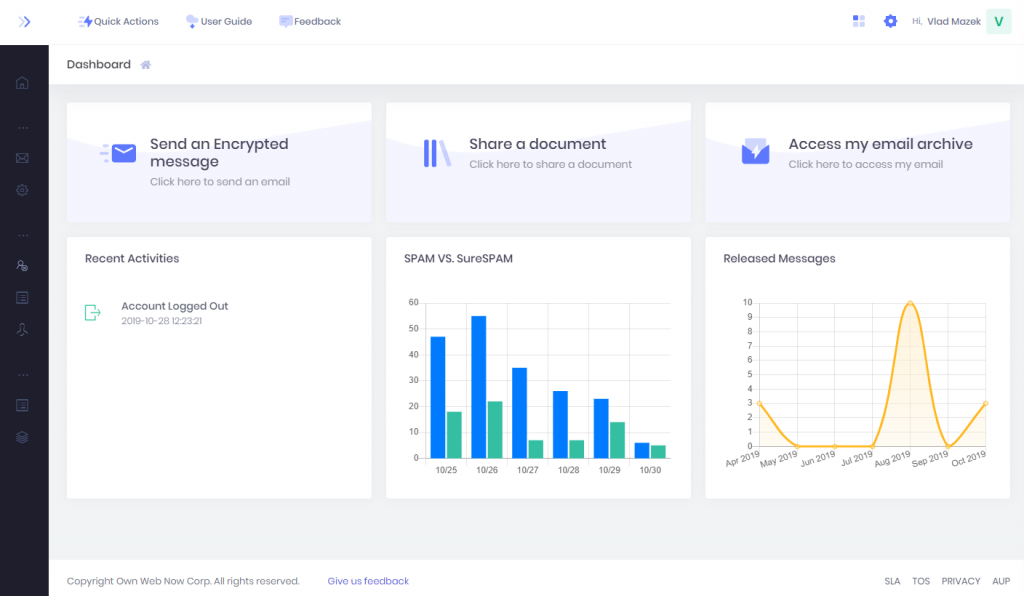
The idea is to present everything you may want to see as far as your activity and the service metrics, but not forgetting what you actually come to ExchangeDefender to do – to communicate and collaborate securely. With that in mind, we’re adding “action tiles” throughout our services that highlight the most popular feature or two. If this was your first time using ExchangeDefender, what would you likely want to do? Check SPAM? Send an Encrypted message? Share a document library? Go through your archives or rely on business continuity because your server or email cloud went down?
We’ve got you covered.
P.S. 100% of these features have come to us by the means of the Feedback link from awesome users such as yourself. We’re a little different in the way we design software, Steve Jobs is long gone and we like to rely on our users and respond to the way you work rather than dictate how you should work. So please, tell us what more we can do and our marketing team will make a pitch to the product teams on your behalf.
Join us 11/13 for our New UI Upgrades & New Features webinar. Get exclusive access to the full design and functionality of the new admin user interface – register here: https://register.gotowebinar.com/register/6850325080298120461
Announcing ExchangeDefender Next Gen User Interface
We are thrilled to announce the launch of our new ExchangeDefender admin user interface, going live on Thursday, October 24th. Check it out:
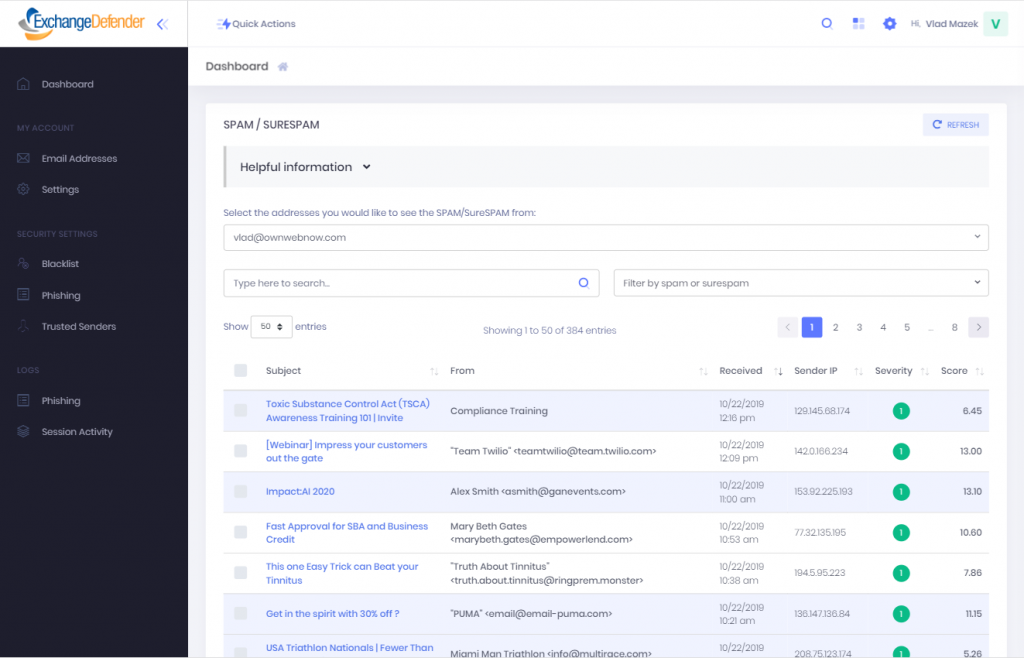
Faster. New ExchangeDefender UI loads exponentially faster than the previous version and feels more like a desktop application than a constantly refreshing web page.
More intuitive. We’ve looked at how our clients actually use the product and we’ve made it much easier to get to the features that users utilize often. We’ve also placed the content front and center while placing all the controls on the same page, so ExchangeDefender will be a breeze to use even for someone that’s seeing it for the first time.
More mobile. No more apps, no more installations, no more add-in’s – we’ve built an application that works anywhere and exposes all the ExchangeDefender functionality on a single panel of glass.
Extensive. Our mission is to help our clients build an office that is secure first. To make that possible, the new UI is actually a framework that makes it easy for users to communicate and collaborate more securely. It also enables our partners to plug their apps into ExchangeDefender and deliver a more complete solution.
No operational change. New ExchangeDefender UI behaves and functions the same way as the old one, making it easier for those that don’t like change to seamlessly continue working in the new UI. We didn’t move your cheese. But we’ve made it much smoother and faster to access so we’re sure you’ll love saving time while you enjoy enhanced security.
Initially the user experience will not change at all – we intend to “soft launch” the new user interface and allow anyone that wants to check out the new stuff in production to do so on demand. We did not want to surprise/shock any of our users with a brand-new look and interface, not to mention without an extended production testing schedule. After about a month (tentatively scheduled for Thanksgiving) the new interface will replace the old one as the default. On Thursday, October 24th you’ll be able to check it out in production:
We’ll have a lot more on the new UI shortly.
Stay tuned for all the details, videos, documentation and so on becoming available soon!
If you’ve attended our more recent webinars, you’re aware of our wider strategy to help businesses build a more secure office. In fact, this UI framework is already in production on the next generation products we launched recently. We would urge everyone to attend our webinar on Wednesday, November 13th where we’ll showcase even more details about our aggressive road-map and all the new features that immediately enable users to communicate and work more efficiently and more securely.
ExchangeDefender UI Upgrades & New Features
Wednesday, Nov 13, Noon
https://attendee.gotowebinar.com/register/6850325080298120461
ExchangeDefender: Expanding Security Portfolio

Our last webinar announced our strategy for expanding the level of protection we offer to our ExchangeDefender users that goes far beyond just email. Our three-pronged approach will now include software, services, and training. We are best known for our email security service “ExchangeDefender” but as the email threats escalate in frequency and evolve in complexity, it is time to add a software component.
Over the past decade we have been developing Wrkoo (codename: “Shockey Monkey”), a business management solution centered around helpdesk and service delivery. As that product has grown to better manage accountability and task tracking, it became a perfect solution for us to use to help our ExchangeDefender users be more secure. Specifically, ExchangeDefender knows about your preferences and security policies – Wrkoo has the capabilities to help your entire organization work better together to create a more secure environment. You will see this distinction and the advantage in action later this week when we announce the Password Vault.
Our implementation is very simple and straight-forward. Every ExchangeDefender Pro protected organization will get it’s own Wrkoo portal (ex: https://exchangedefendercom.wrkoo.com) absolutely free of charge. All the users in ExchangeDefender will automatically be added to the Wrkoo portal and same login credentials will work on both sites.
As we add business-level features that help improve user security, they will be available via https://admin.exchangedefender.com portal under the Shortcuts dropdown (same place you find your Web File Server, LiveArchive, ComplianceArchive, Encryption, etc) as well as via direct login to the Wrkoo portal. This will help our clients quickly navigate between their files, passwords, archives, and all other services.
ExchangeDefender admin portal has been designed from the standpoint of email security and corporate policy enforcement and it is very quick, efficient, and easy to use. Once you look at securing your business beyond just SPAM filtering, things get complex and importance shifts to communication, training, and overall awareness. These are the areas that Wrkoo shines at through its calendars, tasks, tickets/cases/issues, knowledge base, and the ability to help the entire organization communicate and be on the same page. It really is a perfect medium to help everyone in your business manage their information in a more secure and practical user -friendly way.
Our mission remains the same: to keep you safe online. As the threats evolve and management of compliance, reporting, audits, and training becomes more complicated – our solution is there to help you scale and address those issues without spending more money. ExchangeDefender and Wrkoo are here to make that possible.
ExchangeDefender Invoices Got A Makeover!
We have listened to our partners and decided to redesign our invoicing system so it works better for our partners. One of the many benefits of having both Wrkoo and ExchangeDefender teams working together, (more details in our next webinar on September 10th, 2019) is that we can take great ideas from all sorts of businesses and adapt them to serve our IT partners better. Specifically, new ExchangeDefender invoices will be grouped by client:
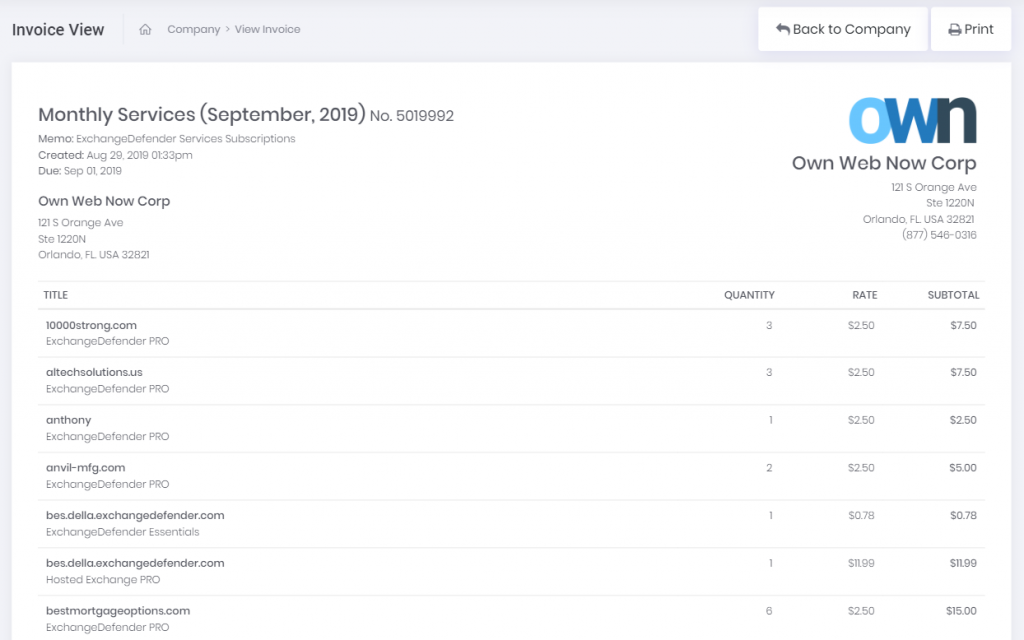
This will give you a clear indication of how many services each client is subscribed to, what type, amount, etc. For deeper dives by your CPA, you can filter and group by service and client so you can get exactly what you’re looking for (by default everything is sorted alphabetically, by the client):
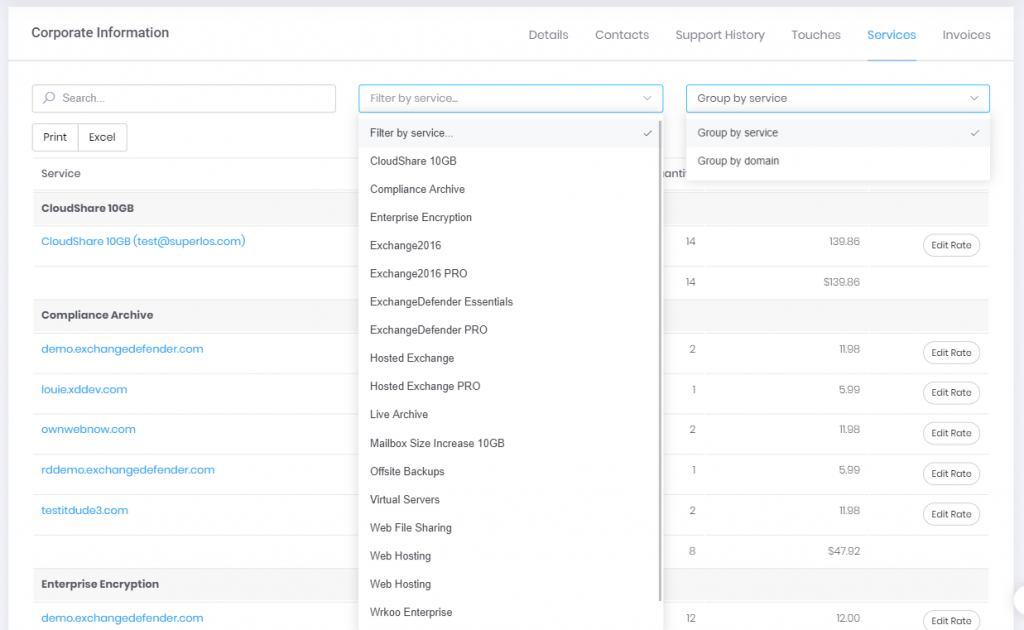
And for the full details, just tap the title:
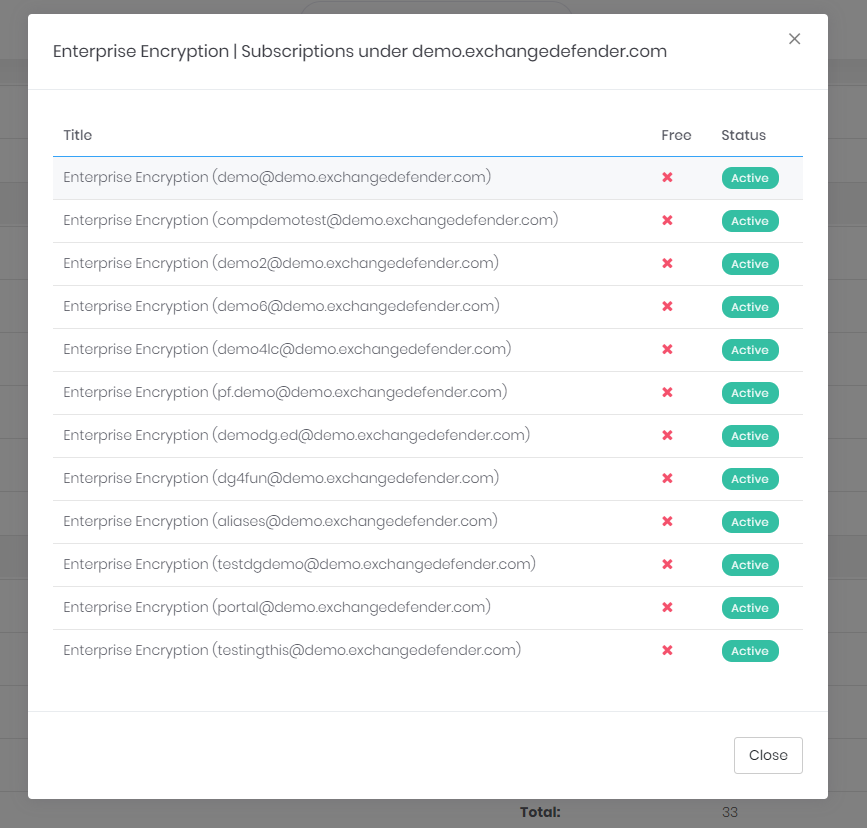
We’ll shortly be adding the ability to move services around, adjust titles, and for even more functionality as well as branding options you will have the ability to customize literally everything in your own Wrkoo portal.
Wrkoo and ExchangeDefender teams have been rolling out new features, listening to our partners needs, and you’re going to start seeing a lot of new features that result from that one-of-a-kind collaborative effort.
The best news though – as this is just a taste of what is coming – you’ll have to tune into our webinar on September 10th at NOON EDT. Trust us, you’re going to love what we’ve got coming!
Managing ExchangeDefender Automatic Account Enrollment
ExchangeDefender recently launched the Automatic Account Provisioning system that replaces our old ExchangeDefender XDSync. The new system automatically finds email addresses that are sending out messages and sends a welcome message to provision the account – the CIO/MSP get a report with a summary of changes and essentially automates the entire process.
For compliance purposes we’re making it super easy to keep track of this process and we’re even providing some tools to help manage accidental activation – for licensing purposes if the email address sends emails out it’s considered a billable user (only inbound aliases/distribution groups/contacts are free)
As a CIO/Service Provider
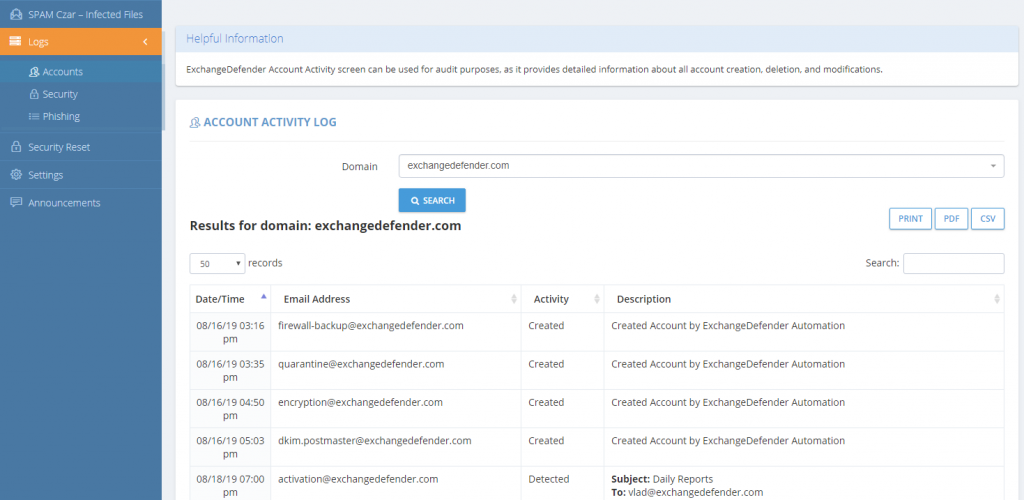
If the email address was provisioned through the automation process, you will see an icon A next to the email address in your portal. To manage the accounts you’ll have to hop down to the Domain Administrator.

As a Domain Administrator
Domain Admin control panel at https://admin.exchangedefender.com gives you more granular controls over Automatic Account Provisioning. Under the Accounts section you will find the same A icon next to the accounts that were provisioned automatically.
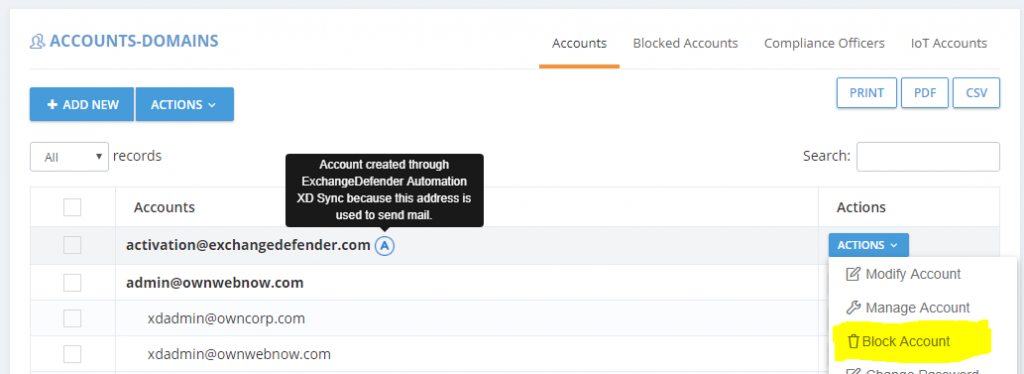
If these accounts were provisioned by mistake and these are not valid users, you can Block them. Blocking an account does two things: it removes the user from the block list so it doesn’t continue to get provisioned after it is deleted and it blocks messages from that user / device / service from relaying mail.
To find users that were blocked from automatic activation (in case that address becomes a regular mailbox/sender in the future) you can click on the Blocked Addresses tab:
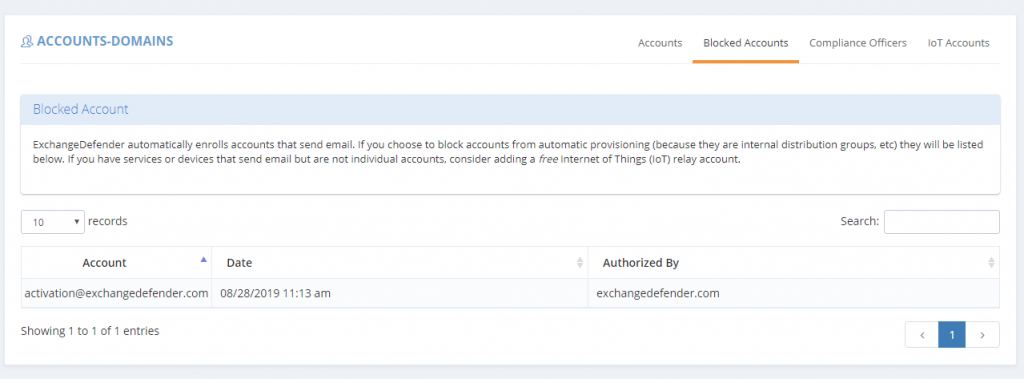
Reporting and activity regarding accounts is still in the same place for both admin levels under the Accounts menu. Accounts that were provisioned through automation will show that they were created by ExchangeDefender Automation, and Blocked Addresses will show the name of the admin that blocked them.
What about deletions? What about turning this system off entirely?
We’re working on it – stay tuned! We’re obviously curious why anyone would want this turned off so if you have a legitimate reason (other than it makes it difficult to cheat on licensing) please let us know. If you have a legitimate use for a service/device to relay mail out, you can always configure it with a free IoT account in ExchangeDefender.
We are also currently working on automatic deletions (based on usage patterns) that will be configurable on a per-domain policy. For example, you’ll have the ability to deactivate accounts that have not sent out any email in 3 months.
ExchangeDefender Account Provisioning Live
As noted nearly two months ago, ExchangeDefender is starting Automated ExchangeDefender Provisioning. In the long, long ago when everyone ran their own Exchange servers, ExchangeDefender offered XDSync to automate creation of ExchangeDefender users as soon as they were added to the Active Directory.
Fast forward to 2019: Few people still run their own Active Directory and most users are now on cloud-based email services that don’t use Active Directory. This puts a burden on our CIO/MSP/IT personnel that has to manage users manually – so we solved that problem with ExchangeDefender. Here is the user experience.
Automated Provisioning – User Experience
When ExchangeDefender detects a new email address from your domain sending outbound mail, it will automatically provision the account for you. This way nobody has to deal with the account management and maintenance, nor do they have to filter and audit the list as local accounts, distribution groups, etc do not send out external emails anyhow. If they do, from the licensing standpoint, it’s treated as a user. When we detect a new user, they get this email:
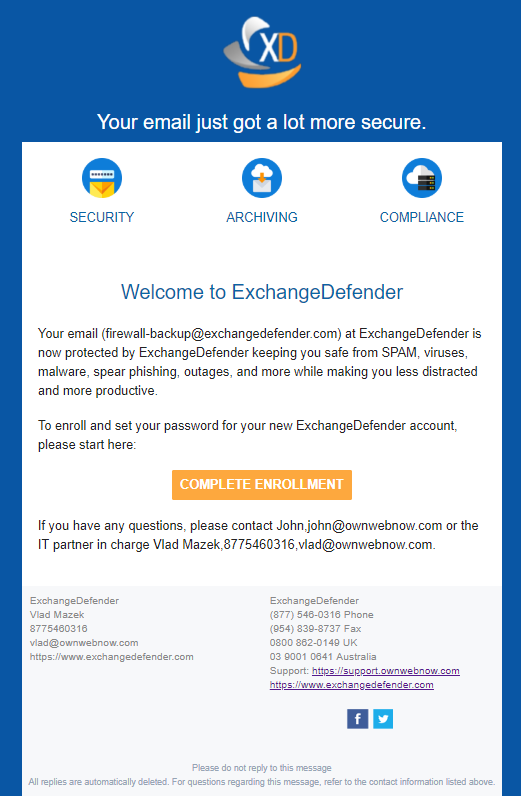
The email contains branding and contact information of an MSP if the client is managed by an MSP. Otherwise, only the domain administrator and ExchangeDefender basic contact info is provided.

At this point, the user is added and configured for ExchangeDefender services according to the domain defaults the IT department configured for this domain.
Clicking on the “Complete Enrollment” button takes the user to the website to setup basic settings. This part is actually VERY cool and something our clients have been begging for – something that shows the user how to actually use the product.
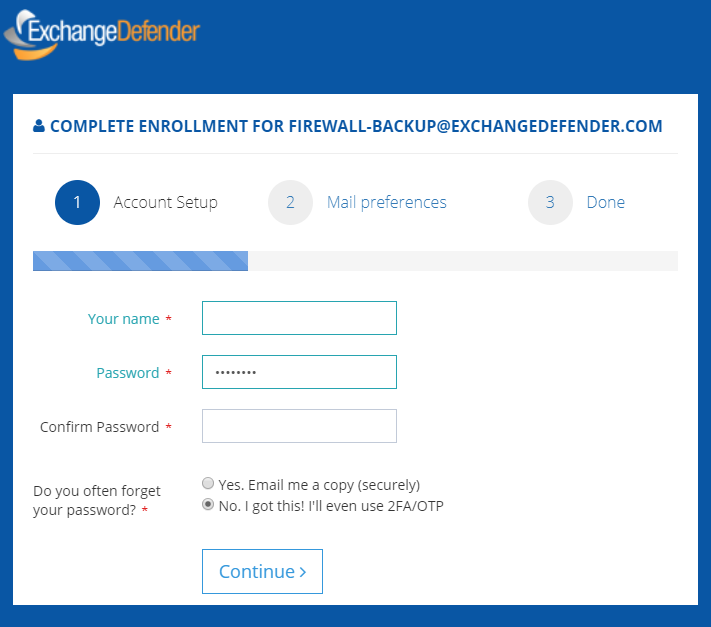
The enrollment wizard is only 2 steps long and gets the essential settings that 99% of users change.
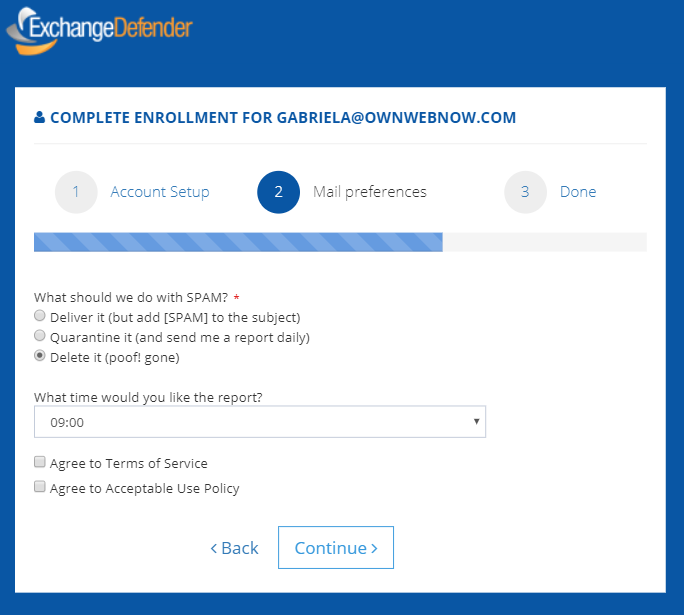
Setup your password, tell us what to do with SPAM, tell us what time you want the email report (if enabled by CIO/MSP/IT) and that’s it – user is done. We’re also working on additional customization/templating of the welcome emails which should be launching later this year.
Password Security Policy Enforcement & Enhancements
Over the past year we’ve been introducing enterprise security measures to help protect our clients from an increasing volume of attacks. Email is the single most abused gateway for email threats – with 91% of corporate breaches starting through email – and it’s only getting worse.
If you’ve used Yahoo, MySpace, or hundreds of popular free web sites (go to https://haveibeenpwned.com/ to see how/who exposed your data) your credentials and other information is available on the web. Hackers are using these passwords and personal information to guess their way into other sites that haven’t been breached – so if you use the same or similar password (or only change the site id, or one number or letter to make it different) then you’re making it very simple for hackers to get into your account.
And we get it. Dealing with security, passwords, and locking down online services is time consuming. But as the company whose main purpose and mission is to keep you secure – we want to help save you time and make it easier for you to be secure.
For the details on all the stuff we’ve got coming in September, we’d like to invite you to our webinar:
ExchangeDefender Security Upgrade
Tuesday, September 10th, 2019
https://attendee.gotowebinar.com/register/6898777257651237900
In the meantime, we’re going to help our partners and clients not make things “stupid easy” for hackers – by globally resetting ExchangeDefender passwords that are older than 1 year. We’ll do this on September 1st, in a very minimally intrusive way, and for those that don’t use ExchangeDefender on the daily basis (and mainly just release SPAM from quarantines) the password change won’t affect them.
Using an OTP/2FA or VPN services or all the free features that are built into ExchangeDefender to keep you secure is obviously our preferred way but as we’ve noted – the realities of SMB concern for IT security – so we need to try something else. We really hope our partners and clients can take the time to attend the September Webinar, as we believe the stuff we’ve built will help lock down your organization and make security manageable again.
ExchangeDefender Phishing Firewall Support (CSO)
Ever since we committed to ExchangeDefender Phishing Firewall as a core feature in ExchangeDefender, we knew that the biggest user benefit will be a trusted cyber-security expert available as a part of the solution. ExchangeDefender redirects all links that pass through ExchangeDefender through our firewall, giving users that click on a suspicious link in their email more information about the suspicious site – for example, if you clicked on a link in an email from Bank of America and are actually going to a web site in Poland, it might be an issue. But who do you turn to when there is an issue?
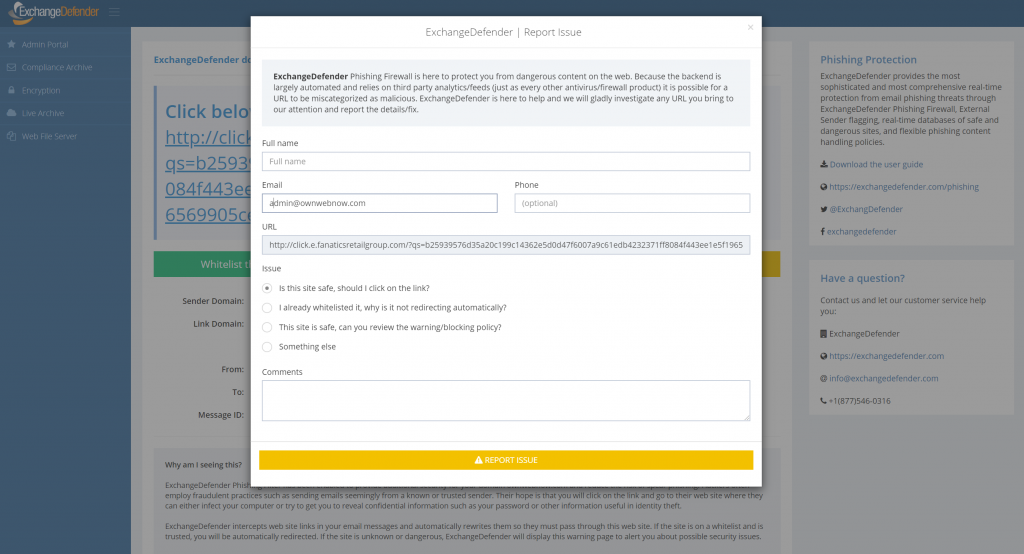
ExchangeDefender Chief Security Officer is just a click away and so far we’ve handled over a thousand inquiries from our clients and partners. If you’re looking at a link and you cannot tell why we intercepted and flagged the content, just click on the yellow button and fill out a form.

Within 24 hours you’re guaranteed a response from our team. The turnaround average so far has been just 18 minutes!
What happens on the back-end is actually quite hands-on: first we investigate the original email and compare the context with the link target, location, etc. We then open the link in a sandbox (safe environment without additional network connectivity and no data) to see what sort of information the web site collects and attempts to send. We then rephrase it in a non-techie user-friendly way and help the client out.
We’ve been overwhelmed with both skepticism and compliments as a result – turns out most users do not expect a response and are pleasantly surprised when an actual human emails back with useful information. We’ve gotten compliments on our turnaround time, usefulness of information, saving the user from dangerous content, as well as thankful comments about the frustration that phishing in general creates – as we’ve been fine tuning xdref.com our users are seeing it less and less and when they do see it we are happy to help.
The overall value of the service cannot be overstated – we’ve saved our CIOs, partners, MSPs, IT guys and gals hundreds of hours in investigative work alone. We got our clients a security audit that allowed them to continue to work quickly. Not to mention about all the bad links that likely would have lead to a breach or security compromise – that the users and techs never had to deal with.
P.S. Included in ExchangeDefender Pro at no additional cost. If you’re still frustrating your clients with “training” programs/videos/whitepapers that SPAM filters catch and junk anyhow – stop wasting your clients time and money – ExchangeDefender Phishing Firewall is a better, more effective, more affordable solution.
ExchangeDefender Phishing Firewall (EPF): Scary Truth behind Phishing
ExchangeDefender Phishing Firewall has been a huge success in it’s initial roll out and I wanted to take a moment to bring you up to speed on our progress and our end goal: to eliminate phishing and spear phishing as a threat to our clients. I do not intend to mince words here, this is the #1 threat out there – 90% of all compromises and breeches start with a phishing email. Stopping it, as an email security company, is our #1 job and I’m happy to report that initial results are stunning.
Little bit of a rewind: Until now the most popular way to fight phishing and spear phishing was through “education” – there is an entire cottage industry of supposed “phishing education”, testing, refreshers – and it all revolves around training people to hover over links in Outlook, what not to click, what to read. It will not surprise you that such “training” is practically worthless, but they say that a picture is worth a thousand words so here is our phishing book:
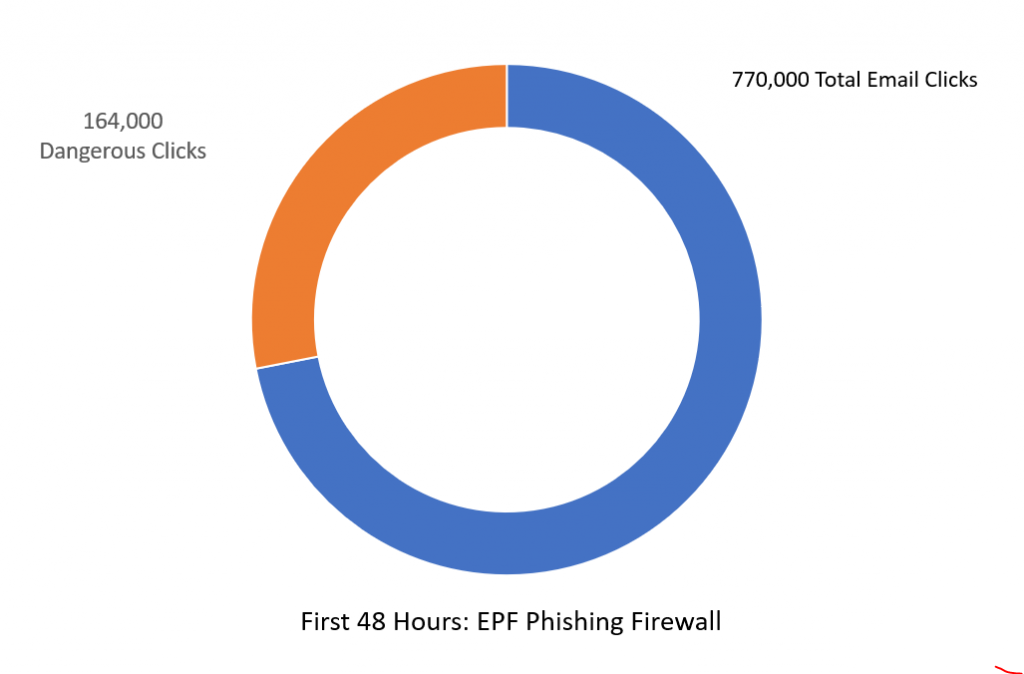
In the 48 hours following 4th of July weekend in United States, dangerous links in the email were clicked on over 770,000 times.
Without ExchangeDefender Phishing Firewall, these links would have redirected our clients to dangerous sites that likely would have lead to a compromise or a security breach. So much for training.
What’s even more telling is that, even with our firewall in place, 164,000 people decided to proceed to a dangerous site anyhow.
If more than 1 out of 5 clicks in your email will take you somewhere dangerous, how well is your training performing?
With ExchangeDefender Phishing Firewall we are enabling companies to setup policies, restrict access, provide intelligence as the user clicks — and we provide logging giving you an idea who attempted to trash your organizations network.
The scary truth behind phishing is that training is only useful in blatantly apparent cases – the kind that will NEVER even get to your inbox. Our SPAM filtering detects dangerous email content and filters it out before it has a chance to get to your Inbox. The stuff that we can flag as dangerous – thanks to user reporting, audits, and look-ahead scanning is far more sophisticated than anything we could pack into a SPAM filter – and it gives your users real intelligence on what they are about to click on. You cannot expect users to remember all their training and to be a web security analyst – their job is acting on the email.
Our job, is making sure the emails get to them clean and free of dangerous malware. Once they click on the links in the email – we are going one step ahead – and leveraging our industry relationships (data feeds and infosec sharing of dangerous content) to make sure you know exactly what you’re clicking on.
Phishing is immensely profitable and far more effective than any other form of hacking – the user literally clicks and gives the hacker the keys to the network – and our ExchangeDefender Phishing Firewall helps remove the danger and reduces phishing to merely an annoyance.
The numbers speak for themselves.
Sincerely,
Vlad Mazek
CEO
ExchangeDefender