ExchangeDefender Phishing Firewall FAQ
ExchangeDefender Phishing Firewall officially launches tomorrow, June 12th, 2019.
Every service provider and every user will be contacted with the information about the new service. Since some users may see the redirection site, we wanted to assure everyone was aware of the service, how it works, what it looks like, and what it does to protect them.
Note from Vlad: We hate changing the user experience. We understand that every time we change anything there will be an issue, folks don’t like having their cheese moved, I get it. However, this isn’t a futile exercise in self-promotion, up-selling, cross-selling, or useless noise: we are doing this to eliminate the problem that 90% of security compromises are triggered by. This implementation comes down to ethics: If I know that something is 90% likely to hurt you, and I have the means to protect you, and I choose to let you get hurt anyhow… why would you ever do business with me or ExchangeDefender? I understand we may lose some business over this, and I am willing to make less money in order to do a better job for people that trust us with their business.
Here are the answers to some questions we’ve already received:
Q: Does ExchangeDefender PF work on every device I receive email on?
A: Yes, ExchangeDefender PF automatically encodes all links sent through our system in HTML messages and redirects them through ExchangeDefender PF. This means that the link will be secured no matter which device you use to access your ExchangeDefender-protected email.
Q: Does ExchangeDefender PF protect me from non-email links?
A: ExchangeDefender only protects you from email links in HTML messages sent to your email address through ExchangeDefender. If your mail client downloads mail from 3rd party external services (Yahoo,
AOL, Microsoft, Google) that are not protected by ExchangeDefender, you will not be protected.
Q: Is ExchangeDefender PF available in ExchangeDefender Essentials?
A: ExchangeDefender PF is only available in ExchangeDefender Pro and ExchangeDefender Enterprise.
Q: Is there any way to turn off URL encoding for specific domains or users?
A: ExchangeDefender encodes the URL at the edge, as the message is being scanned for malware and other phishing forgeries.
Q: I don’t want to see the ExchangeDefender PF warning/site, can I bypass it?
A: Yes, you can simply whitelist the domain and ExchangeDefender PF will not be displayed. Whitelisted domains are automatically displayed without ExchangeDefender PF. ExchangeDefender maintains a list of known good/legitimate domains so the likelihood that you will see a dangerous (or questionable) website is very low. Additionally, your IT department or IT Solution Provider has access to organization-wide whitelist and can bypass ExchangeDefender PF to any site you need to visit.
Q: Is it possible to still get hacked/compromised even with ExchangeDefender PF?
A: ExchangeDefender PF simply applies your organizational policies to traffic and gives you additional information about the link you have clicked on. If you ignore warnings, or if you proceed to a dangerous site as a part of your organizational policy, you can still be compromised.
Q: Is there anything special I need to do on my network in order to support the redirection?
A: No, you should not have to make any modifications to your clients network in order to support this. If you do something exceptionally unusual (we would have contacted you separately, DoD requirement) and only have an allow access policy while blacklisting the rest of the Internet, redirection happens through https://r.xdref.com domain that needs to be in the safe sites.
Q: Can I turn URL rewriting off?
A: The ExchangeDefender URL rewriting code is implemented at the edge without regard for domain/user policies. In order not to introduce delays in processing, this is a global rule. If you are concerned about your clients seeing the redirection screen, whitelist the domains they typically go through. If we get complaints about it, we will look at deploying this policy further down in the scanning path which will slow down processing times for domains that opt out of the service and that feature is already in the development queue.
Q: Can I see the copy of the messages you are sending users, so I know what to expect?
A: Here is a copy of the message in PDF and Outlook format.
Q: Will the links stay live for X number of years for compliance purposes?
A: There is no expiration date for the links, as clearly stated in our Privacy Policy we do not collect or archive the links that you click on or that we encode, they will stay in your downloaded / cached / archived messages. While many regulatory requirements have message retention policy expectations, those requirements do not extend to external content, ie: you have to archive the message, you DO NOT have to archive the documents that are externally linked on third party sites. Either way, messages will continue to redirect as long as we stay in business.
Q: Can I get a list of good/bad sites for my compliance records?
A: Please contact our compliance officer at compliance@ownwebnow.com with the letter from your regulatory body and we will do our best to provide this confidential information ASAP.
Phishing: Beware of Strangers
This Thursday, June 6th, we will be announcing a major overhaul in the way we deal with spear phishing SPAM. No, it’s not a mind-blowing patent-pending stroke-of-genius sort of stuff, it’s much closer to what your parents told you growing up: Don’t get into a car with strangers don’t click on links or open attachments from strangers.
In a way, ExchangeDefender has had protection from this issue for years. If you had a decent IT Solution Provider implementing ExchangeDefender for you, they would have setup your SPF record and eliminated this issue – but many don’t. Or they would have turned on ExchangeDefender protection where all messages spoofing/forging your domain would automatically get junked – almost none of them do. Which is why ExchangeDefender as a service has become less of an IT tool and more of an end user suite of services to get stuff done.
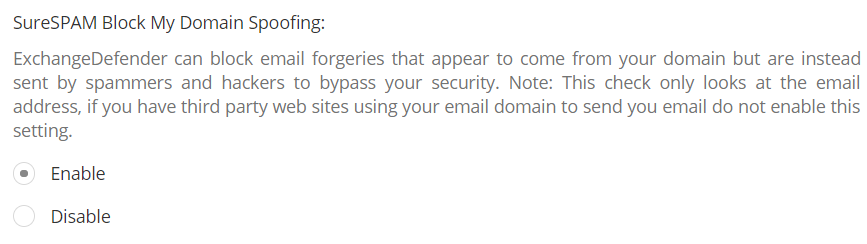
When features like this are left disabled “because they might become support issues” it becomes really difficult to secure users. But I get it, IT companies have a business to run too, which is why we’ve really stepped up our support efforts and are going to be there to help folks get things done without becoming an additional problem for the IT department. Doing so has really made us rethink how we implement features and how the service behavior needs to speak the same language as the end user. Which brings me to phishing beyond forgeries.
Can you spot a stranger?One of the new phishing protection features in ExchangeDefender will allow you to flag messages that are coming from outside of your organization. You will have two settings – to modify the subject and to modify the header of the message so when you look inside of your mailbox you’ll know what came from a stranger right away. Try it:
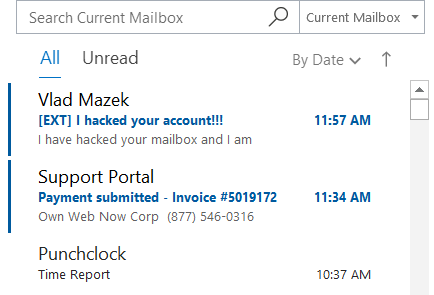
Even from the message listing you’ll know which messages shouldn’t even be opened. But suppose you ignored even that – you can set another warning, printed inside of the message, giving the user even more of an instruction of what to do.
Warning: Message was sent from outside of the organization. Do not click on links or open attachments if you don’t recognize the sender.
Far from subtle. And it has to be – because most people check email quickly, between tasks, or are simply interrupted by it. ExchangeDefender has your back, and we’ll make sure we alert you to possible issues before they become problems. Which we hope everyone will be aboard with.

Please join us, June 6th at Noon, for our NEW webinar featuring ExchangeDefender’s Phishing and Spoofing protection, plus see what’s new with Encryption, WFS, and Wrkoo!
Managing User Notifications
It’s no secret to anyone that’s been paying attention to this space that ExchangeDefender is getting a lot more user friendly – both in service and in design. We’ve been improving the way we communicate with our clients and our partners through efforts like embedded help, in-line training and support, real-time chat support, self service portals, NOC sites, etc
Next week we will launch a major feature in ExchangeDefender. It will address one of the biggest pain points in email security and it will give users a ton of control that will help close what is currently the biggest exploitable hole in email security: spear phishing. This will require us to give users a heads up about what they are about to see and training/documentation about how to use it to the fullest.
Which is where we have to make sure our partners are a part of the process too. During the webinar we’ll go over the details about how to insert branding and a message/note at https://admin.exchangedefender.com. This is generally not a big issue, since almost all of our partners would rather have us do more work for them than less, but if you’re really sensitive about this topic make sure you’re in the webinar to see what options you have and how to best leverage them for your own business purposes.
Looking forward to showing you all of this, and the redesigned ExchangeDefender Encryption product on June 6th at noon. https://register.gotowebinar.com/register/198414968804117507
General Data Protection (GDPR) and ExchangeDefender: Get your resources to demonstrate compliance
ExchangeDefender, at it’s core, is all about protecting our clients: it should come as no surprise that we are big fans of GDPR. If you haven’t been inundated by GDPR, or by a million “we’ve updated our privacy policy” emails from every web site you’ve ever signed up for, or you’ve landed here simply because the deadline is tomorrow, Friday, May 25th: rest assured we’ve got you covered.
ExchangeDefender is 100% compliant with GDPR. You are covered as are your clients on ExchangeDefender and we have presence across European Union to handle any issues or complaints that come up as a result of GDPR implementation.
What you need to know
GDPR, essentially (and no, this is not legal advice), is a European Union data privacy regulation that turns the tables on marketers and gives residents of EU very specific rights and control over their personal data. The regulation is very broad in terms of scrutinizing everyone that may be holding (controller) or managing/processing (processor) personal data and ExchangeDefender fits both of those roles at times depending on the product or service we’re talking about.
If you’d rather do without me talking at you for 6 minutes, we have a ton of other resources that you can share with your clients. I would start with this document available for download here:
What you need to do now
1. Start by reviewing our new Privacy Policy. I know, I know, you’re done with
2. Contact us if you’re seriously building out a business around GDPR and get our marketing folks to hook you up with branded collateral (minimum client count
3. Review our GDPR collateral, particularly the webinar with the deep dive of the ExchangeDefender implementation. This is the most important thing you could do but it’s 27 minutes long and I know everyone doesn’t have that kind of time or attention span – I get it – but if you’re seriously working with us and need GDPR assistance, you will have to go through the training eventually.
Where to go next
We are very excited about GDPR and have put significant resources to design our products and services around the regulation because we believe it will have a broad impact well beyond Europe. Privacy, data integrity, right to be forgotten, right to withdraw consent, right to find out what sort of information companies have about you – those are fundamental rights in our opinion.
And if you ignore them the penalties are going to be extensive.
What we’re choosing to do at ExchangeDefender is to create a service around protecting people on the Internet – not just from SPAM but really safeguarding all communication you do as a business. Take a look at our GDPR resources and see how we can get you started on the same path – at the very least you can use our reach and resources to comply with GDPR.
Top 5 Mistakes Companies Make With Compliance
ExchangeDefender Compliance Archive was designed as a blend of services and products to help organizations achieve regulatory compliance. This complex process is always evolving with new regulatory requirements, changes in organization structure, and unique reporting requirements.
At ExchangeDefender we specialize in helping organizations with their eDiscovery needs. Here are the biggest fallacies we hear all the time:
“We have a backup”
Email backups are not sufficient for nearly any modern regulatory compliance requirements for email retention. Not only can the messages be deleted before backups run, but running reports across the entire organization is next to impossible, not to mention excessively expensive. We recently assisted a partner managing a small 15 employee office in their backup and restore process to locate a message from 5 years ago, costing the organization over $18,000 in IT labor alone.
“We have a product/compliance service”
Having a product or a service subscription is different from being in compliance with regulatory requirements. The difference between having a product and being in compliance is similar to “We have a CPA” and “We have filed our tax returns on time” – mistaking the two can be costly and dangerous.
“We are never going to need that”
Most organizations downplay the importance of long term email archiving and eDiscovery. An overwhelming majority of subscribers to our eDiscovery service don’t have a specific regulatory requirement at all, they do it to effectively defend themselves from legal threats that are all too common these days. With email being the gateway for all corporate communication, it is the first place record retentions, legal holds, and subpoenas are issued for electronic records and there needs to be a system in place to effectively deliver that information.
“What we have is enough”
Regulatory compliance goes far beyond poorly interpreted recommendations and laws. It is a process of producing reports, identifying problems, and assuring that corporate communications policies are being followed, or at least addressed, in case there is an issue. If the organization does not have people in charge of managing the compliance on a monthly basis or there are no current reports searching for dangerous or sensitive content or there is no ongoing maintenance or an established incident record – the organization is likely out of compliance even if they purchased the right software or signed up for the right service at one point.
“We have a someone managing that”
Someone is not a good person to rely on when you get a subpoena and they are even more difficult to get into a courtroom. Plus, how much would you trust them to demonstrate expertise and defend the implementation of the compliance archiving and eDiscovery solution? Many organizations make a mistake of thinking that just signing up for a service or purchasing a product is sufficient for compliance but it’s really just a starting point. You need the personnel, product, service, and reporting to fully achieve regulatory compliance.
ExchangeDefender Compliance Archiving and eDiscovery are a part of a professional service that helps get your organization and its means of communication on path to achieving regulatory compliance. Whenever someone is fully confident that they have their compliance in order we simply ask them to “show me your last Compliance Officer Report” and almost everyone struggles to produce the report or even name the Compliance Officer, the processes being used for archiving, the type of data protection, or the way in which the entire process is tested and audited. With ExchangeDefender Compliance Archiving, you not only get a service, you get a partner that will work with you every step of the way in achieving your regulatory and organizational needs for proper record keeping.
Achieving eDiscovery and Compliance Archiving requirements in 5 steps
 Signing up for the Compliance Archiving service is the first step in reaching regulatory compliance when it comes to email retention and eDiscovery. The following five steps will put you on the right path of achieving and maintaining that compliance:
Signing up for the Compliance Archiving service is the first step in reaching regulatory compliance when it comes to email retention and eDiscovery. The following five steps will put you on the right path of achieving and maintaining that compliance:
1.Understand what you need to keep and for how long.
Your regulatory/oversight body will provide details about how long you are required to hold on to your email. In our experience with Compliance Archiving, you also need to pay attention to the Statue of Limitations that your business may be liable for. Very often the discovery process for lawsuits includes legal hold requests and record requests that are longer than regulatory requirement.
2. Get the right product and implement it correctly.
Your compliance has to be all encompassing – all email must be archived. With ExchangeDefender Compliance Archiving all of your inbound, outbound, and interoffice email is collected, archived and protected in the cloud. You can search for any document at any time and be certain that it has not been tampered with and that no emails have been deleted – something that sets our eDiscovery/archiving apart from backup solutions.
3. Keep an eye on it to make sure it works
Just setting up a compliance archiving solution is not sufficient enough. there is no protection for technical negligence in regulations. You are expected to keep your mail server and everything connected to it secure. Penalties for data loss, compromised credentials, and data leakage are severe and are not a valid excuse for not having compliance.
4. Create Compliance Officer reports frequently.
Compliance Officer within your organization must create reports on a monthly basis to assure no confidential information is allowed to leave the organization. Some industries have an even more specific and severe restriction on the type of communication that can take place over email and what sort of information can be sent – compliance officers run eDiscovery reports to assure nothing confidential is being shared and address problems and exceptions routinely
5. Routinely audit the entire system to maintain compliance.
Organizations grow and change over time and remaining compliant with new regulations is key. ExchangeDefender Compliance Archiving service often sends out advisories, best practices, tips and suggestions to adjust your process because you are always expected to be in full compliance with the latest requirements. Every time you add a new employee or change your mail server configuration or new lines of business – compliance must extend to cover these new records that may be of interest to someone down the road.
“One of the biggest mistakes organizations make with regulatory compliance is thinking that it’s a service, product or a one-time effort: quite the opposite!”
Achieving regulatory compliance means implementing the right product, conducting routine audits, complying with changes in regulations and having full control of the environment where messages are stored as employees come and go.
In the event of an audit, you will be asked to produce record and you will be judged on your ability to provide specific records that are requested, not the best effort you made in trying to achieve compliance. Considering the fines and legal complications, it makes sense to revisit the five steps outlined here annually and make adjustments as necessary.





