Three Simple Ways To Begin Regulatory Compliance Archiving
Have you been putting off offering or relying on Compliance Archiving to meet regulatory compliance requirements? If so, you’re among friends as most businesses tend to view it as a form of a backup until they receive a letter from a law firm. Recently we published a quick and informal techie-free post about business continuity and we wanted to do the same for archiving because the #1 thing that will keep you out of trouble is making sure your entire organization is on the same page.
With that in mind, here are three steps that your organization needs to follow to get started with Compliance Archiving:
Step 1: Understand how your organization communicates
If you only knew what everyone did and what they had access to, things like security and compliance would be a non-issue. In the real world, organizations have a revolving door of staff, vendors, clients, laws, and projects that is constantly spinning. The notion that you can get something to manage it all, held together by IT staff and automation, is nothing short of a fantasy. Or rather, a nightmare, because you’ll get in trouble over one thing that was missed and went wrong not a million things that went right.
Our Compliance Archiving touches every message in your organization: doesn’t matter if it’s a message you sent to a client, a message you received from a vendor, or an interoffice email you sent to a coworker – we get them all. The important thing in step one is identifying the people and making sure that the way you communicate is set in stone: “We communicate with everyone through @ownwebnow.com email addresses, every ticket, every update, every inquiry, every quote, every bill pay – everything either comes from or is cc’d to an @ownwebnow.com address.”
Step 2: Get a grip on your devices, apps, and processes
Convenience is the enemy of order. And if you’re going to run a business, you cannot have everyone do exactly what they want to do. Yes, Subway will make your sandwich any way you want them to, but if you walk in and order a key lime cheesecake you’re going to be hungry. Same method applies to all the devices, apps, processes, etc. The simplest, most common sense, most effortless thing to do is to just give everyone that works on your behalf an email address on your infrastructure and have them use that email for all company communications.
If they use something else, and for some reason you wish to permit that rule change in your business, request that everything is cc’d to a local shared mailbox where you can keep ownership of it. Don’t make a big deal out of it – we get our office beer and red solo cups from Costco – and believe me we don’t have a massive asset inventory tracking system around it with people signing off on stuff left and right. We just take a picture of the receipt/order form and email to a receipts@ address – done.
Step 3: Get a regulatory compliance plan
The worst thing you can possibly do is start thinking about a plan when you’ve received a request for information or a legal hold. The good news is, step #3 is the simplest one because it’s just a matter of calling us at 877-546-0316 and talking to someone about implementing the Compliance Archiving solution. The complexity isn’t in the technology, it’s with the people and the constant sprawl of apps and devices that hold vital corporate information.
The great news about what we offer with our partners is that anything going in and out of your company can be screened, monitored, reported, and produced on demand or automatically for just a few bucks a month. The biggest challenge is knowing what to do – and you have to actually get started.
We look forward to serving you and making regulatory Compliance Archiving a breeze.
Top 5 Mistakes Companies Make With Compliance
ExchangeDefender Compliance Archive was designed as a blend of services and products to help organizations achieve regulatory compliance. This complex process is always evolving with new regulatory requirements, changes in organization structure, and unique reporting requirements.
At ExchangeDefender we specialize in helping organizations with their eDiscovery needs. Here are the biggest fallacies we hear all the time:
“We have a backup”
Email backups are not sufficient for nearly any modern regulatory compliance requirements for email retention. Not only can the messages be deleted before backups run, but running reports across the entire organization is next to impossible, not to mention excessively expensive. We recently assisted a partner managing a small 15 employee office in their backup and restore process to locate a message from 5 years ago, costing the organization over $18,000 in IT labor alone.
“We have a product/compliance service”
Having a product or a service subscription is different from being in compliance with regulatory requirements. The difference between having a product and being in compliance is similar to “We have a CPA” and “We have filed our tax returns on time” – mistaking the two can be costly and dangerous.
“We are never going to need that”
Most organizations downplay the importance of long term email archiving and eDiscovery. An overwhelming majority of subscribers to our eDiscovery service don’t have a specific regulatory requirement at all, they do it to effectively defend themselves from legal threats that are all too common these days. With email being the gateway for all corporate communication, it is the first place record retentions, legal holds, and subpoenas are issued for electronic records and there needs to be a system in place to effectively deliver that information.
“What we have is enough”
Regulatory compliance goes far beyond poorly interpreted recommendations and laws. It is a process of producing reports, identifying problems, and assuring that corporate communications policies are being followed, or at least addressed, in case there is an issue. If the organization does not have people in charge of managing the compliance on a monthly basis or there are no current reports searching for dangerous or sensitive content or there is no ongoing maintenance or an established incident record – the organization is likely out of compliance even if they purchased the right software or signed up for the right service at one point.
“We have a someone managing that”
Someone is not a good person to rely on when you get a subpoena and they are even more difficult to get into a courtroom. Plus, how much would you trust them to demonstrate expertise and defend the implementation of the compliance archiving and eDiscovery solution? Many organizations make a mistake of thinking that just signing up for a service or purchasing a product is sufficient for compliance but it’s really just a starting point. You need the personnel, product, service, and reporting to fully achieve regulatory compliance.
ExchangeDefender Compliance Archiving and eDiscovery are a part of a professional service that helps get your organization and its means of communication on path to achieving regulatory compliance. Whenever someone is fully confident that they have their compliance in order we simply ask them to “show me your last Compliance Officer Report” and almost everyone struggles to produce the report or even name the Compliance Officer, the processes being used for archiving, the type of data protection, or the way in which the entire process is tested and audited. With ExchangeDefender Compliance Archiving, you not only get a service, you get a partner that will work with you every step of the way in achieving your regulatory and organizational needs for proper record keeping.
Achieving eDiscovery and Compliance Archiving requirements in 5 steps
 Signing up for the Compliance Archiving service is the first step in reaching regulatory compliance when it comes to email retention and eDiscovery. The following five steps will put you on the right path of achieving and maintaining that compliance:
Signing up for the Compliance Archiving service is the first step in reaching regulatory compliance when it comes to email retention and eDiscovery. The following five steps will put you on the right path of achieving and maintaining that compliance:
1.Understand what you need to keep and for how long.
Your regulatory/oversight body will provide details about how long you are required to hold on to your email. In our experience with Compliance Archiving, you also need to pay attention to the Statue of Limitations that your business may be liable for. Very often the discovery process for lawsuits includes legal hold requests and record requests that are longer than regulatory requirement.
2. Get the right product and implement it correctly.
Your compliance has to be all encompassing – all email must be archived. With ExchangeDefender Compliance Archiving all of your inbound, outbound, and interoffice email is collected, archived and protected in the cloud. You can search for any document at any time and be certain that it has not been tampered with and that no emails have been deleted – something that sets our eDiscovery/archiving apart from backup solutions.
3. Keep an eye on it to make sure it works
Just setting up a compliance archiving solution is not sufficient enough. there is no protection for technical negligence in regulations. You are expected to keep your mail server and everything connected to it secure. Penalties for data loss, compromised credentials, and data leakage are severe and are not a valid excuse for not having compliance.
4. Create Compliance Officer reports frequently.
Compliance Officer within your organization must create reports on a monthly basis to assure no confidential information is allowed to leave the organization. Some industries have an even more specific and severe restriction on the type of communication that can take place over email and what sort of information can be sent – compliance officers run eDiscovery reports to assure nothing confidential is being shared and address problems and exceptions routinely
5. Routinely audit the entire system to maintain compliance.
Organizations grow and change over time and remaining compliant with new regulations is key. ExchangeDefender Compliance Archiving service often sends out advisories, best practices, tips and suggestions to adjust your process because you are always expected to be in full compliance with the latest requirements. Every time you add a new employee or change your mail server configuration or new lines of business – compliance must extend to cover these new records that may be of interest to someone down the road.
“One of the biggest mistakes organizations make with regulatory compliance is thinking that it’s a service, product or a one-time effort: quite the opposite!”
Achieving regulatory compliance means implementing the right product, conducting routine audits, complying with changes in regulations and having full control of the environment where messages are stored as employees come and go.
In the event of an audit, you will be asked to produce record and you will be judged on your ability to provide specific records that are requested, not the best effort you made in trying to achieve compliance. Considering the fines and legal complications, it makes sense to revisit the five steps outlined here annually and make adjustments as necessary.
Pro Tip: How to Pitch Encryption and Compliance
Here is something that MSPs always get wrong when it comes to proposing Encryption and Archiving (HIPAA, compliance, eDiscovery): You can’t be something you’re not BUT you have to know the service you’re proposing. More on this topic tomorrow (if I can sneak it by the marketing)
Posted by ExchangeDefender on Thursday, April 5, 2018
Here is something that MSPs always get wrong when it comes to proposing Encryption and Archiving (HIPAA, compliance, eDiscovery): You can’t be something you’re not BUT you have to know the service you’re proposing.
Want to see part TWO of this video?
Disclaimer: There is tasteful profanity and light nudity to really drive the point of how to better interact with your clients. 🙂
How to kill SPAM without using ExchangeDefender
At ExchangeDefender we kill SPAM for a living. We spend a ton of time and energy identifying, filtering, and destroying junk mail. If you’ve ever wondered how you could make your email experience better, even without the massive layered security that ExchangeDefender provides, these are the steps you could take today:
1. Configure strict SPF/DKIM DNS records
SPF and DKIM (DMARC) can help you protect your domain name from being used in SPAM mailbombs. Spammers will often use real email addresses and domains to send forged “spoofed” email messages and SPF/DKIM provide a mechanism for identifying which email server/platform you use. By setting up an SPF/DKIM you can tell places that are receiving email from your domain what to do if the message wasn’t actually sent from you. If your inbox is full of email bounces and non-delivery receipts, someone is using your email address to send junk mail and an SPF/DKIM record will practically eliminate bouncebacks.
2. Get rid of generic email aliases
At ExchangeDefender we manually process SPAM complaints from our customers – that’s how we train our system to eliminate messages that otherwise make it through because they are legitimate in every way we can automatically process them. The number one way to get a ton of annoying email that may be on the borderine between legitimate commercial mail and an unsolicited one: generic email aliases. If you get info@, sales@, admin@ or so on, you are painting a giant bullseye on your Inbox and practically begging to be spammed.
3. Unsubscribe from newsletters
I know, I know, everyone that has your email address supports CAN-SPAM , would never send you unsolicited mail, would never sell their client list… and even if you believe all those lies most of the time, people still get hacked. All the time! As do their ISPs and infrastructure along the way. If you want to reduce the amount of junk mail you deal with, simply reduce the number of places that have your email address. Simple!
4. Don’t click on everything in your Inbox
Sometimes SPAM gets through. Sometimes dangerous stuff from your friends and colleagues gets forwarded around. Sometimes your antivirus isn’t up to date. Sometimes the firewall virus protection is misconfigured our expired. Things happen: none are a good excuse for the simplest thing you can do: avoid clicking on anything in messages that look or seem suspicious.
5. Do not blindly whitelist major ISPs
The second biggest source of SPAM complaints at ExchangeDefender is actually completely self-inflicted: people whitelist major email providers and wonder why blatant junk mail keeps on “slipping through” as whitelisted. Go through your whitelist entries in Outlook, etc and make sure you aren’t whitelisting Gmail, Outlook, Yahoo, Verizon, AT&T, Hotmail or any of the widely used and abused email domains. Spammers know your email admin doesn’t want to deal with complaints about messages you’re getting from these platforms so they treat them more leniently – so spammers simply abuse them.
It’s really that simple – following these steps will cut your junk mail pile in half within a day. If you want to reduce it to less than 1%, ExchangeDefender is here for you for less than a buck a month or you can layer it and add more protection if you need it because time is money: but no amount of technology and automation can replace just a little bit of common sense.
Federal Trade Commission
CAN-SPAM Act: A Compliance Guide for Business
The official website of the Federal Trade Commission, protecting America’s consumers for over 100 years.
VIDEO: Live Archive keeps emails up, and running!
So here is something that has always worked for me: everyone hates outages. Regardless of why I’m invited to speak to anyone about ExchangeDefender, and the billion problems we solve, I am here to help you with just one thing: uptime. If things are working, we can sort everything out, but the fear of the new unknown solution causing downtime is the #1 thing your client is thinking about. So address it first.
Posted by ExchangeDefender on Thursday, March 29, 2018
What’s this video about? Live Archive.
So here is something that has always worked for me: everyone hates outages. Regardless of why I’m invited to speak to anyone about ExchangeDefender, and the billion problems we solve, I am here to help you with just one thing: uptime. If things are working, we can sort everything out, but the fear of the new unknown solution causing downtime is the #1 thing your client is thinking about. So address it first.
What is Live Archive?
Access your email via the cloud when outages happen.
Organizations are constantly facing internet and email outages, maintenance cycles and service unavailability. The key to productivity is being able to access your email even when outages happen Exchange Defender LiveArchive Business Continuity is the solution.
As you send and receive email, we make a copy and store it on our network – when you experience an outage you can just pull up a webmail system on your computer, tablet, or phone and continue where you left off.
Visit Exchange Defender: Email Security, Archiving, and Business Continuity solutions
Do’s and Don’ts: Selling your clients on Email Security Solutions
Let’s face it, most IT solutions in the business process fail because users don’t use them. They don’t use them because they see it as another unnecessary time waster in the process they are already accustomed to and count on everything being yet another thing management will soon forget about because they don’t work the same issues all day long. Sound familiar? All the new, cool, better, smarter ways of doing something will always lose to users unwillingness and inability to change. Until someone loses their job or the company gets sued for negligence. Oops!
So, what should you be talking about with your clients?
1. Don’t talk about backups – talk about long term email archiving and ediscovery.
2. Don’t talk about encryption – talk about safely getting data over without getting hacked.
3. Don’t talk about SPAM – talk about fake senders, fake links
4. Don’t talk about Phishing – talk about identity theft, compromised passwords and bank accounts.
5. Don’t talk about Compliance – talk about setting business standards and avoiding lawsuits.
6. Don’t talk about Web File Sharing – ask how they get important documents to their clients or vendors?
7. Don’t talk about Malware – ask them what they currently do to protect their staff from taking down the whole office.
Your clients have been hearing about SPAM and Virus protection for over a decades now, they view it the same way they view every other software license cost – part of doing business. The problem in 2018 is that it’s no longer just the technology complexity dictating business spending, regulatory bodies and government are getting involved in it too. Nearly every industry is subject to some new regulation, record keeping process, security audit, assessment or other “time waster” that they will have to deal with. So start clipping news articles and send them headlines with the message “We really need to set you up with ExchangeDefender so you don’t end up in the next article” – and I don’t mean it in a sarcastic or fear mongering way at all, nearly a quarter of my office time goes to time travel discussions and things businesses wished they had in place before they got in trouble. Talk to them now.
The Bottom Line:
Businesses you are trying to sell technical solutions to are already dealing with a lot of nightmares related to technology. They don’t want another thing to manage, report, customize, tweak and learn: they want something that reduces all of that work. That something is ExchangeDefender, all-in-one, end-user friendly email solution that removes things they don’t need to look at and makes stuff they are looking for easy to find.
I encourage you to talk to your clients less from a technical solution standpoint and more from the business process implementation. Yes, they may trust you because of your technical expertise but what you need them to understand (and what will ultimately earn you the business) is which business issues are going to be addressed by spending a few dollars a month. If they can identify with the problem, they will pay for it to go away because everyone is always trying to reduce costs and labor is the biggest one of them all. Help make them more productive.
ExchangeDefender growing from Essentials to Compliance
 As you’ve heard us repeat often in 2016, Essentials and Compliance are our fastest growing services and our partners have been using them to grow their business in very creative ways. We’ve interviewed our top partners about how they price, position and market these offerings and we would love to share the business model behind these offerings to help all of our partners find more success with ExchangeDefender in 2017.
As you’ve heard us repeat often in 2016, Essentials and Compliance are our fastest growing services and our partners have been using them to grow their business in very creative ways. We’ve interviewed our top partners about how they price, position and market these offerings and we would love to share the business model behind these offerings to help all of our partners find more success with ExchangeDefender in 2017.
ExchangeDefender growing business from Essentials to Compliance
Thu, Mar 16, 2017 12:00 PM – 1:00 PM EDT
https://global.gotomeeting.com/join/598282197
Webinar will be recorded (and available to partners shortly) but to get the marketing collateral and anything else we cover in the webinar, you have to attend live. Bring your beer and get an early start on St Patrick’s Day, you can always blame it on Vlad.
How ExchangeDefender Protects You From Ransomware
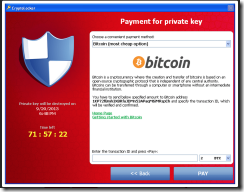 There has been a lot of news coverage of the new wave of ransomware infecting businesses, encrypting hard drives and data on network shares and creating a “ransom” demand in order to unencrypt it. Initially these viruses traveled as typical viruses do – as executable attachments or inside zip files. Most popular of these was CryptoLocker which has made millions of dollars from businesses that didn’t have adequate protection, most recently from a Hollywood hospital that paid $17,000 to get it’s data back. But ransomware has taken a more evil turn – traveling not as an executable that users have been trained to avoid but as a macro inside Word and Excel documents that users often open without a second thought.
There has been a lot of news coverage of the new wave of ransomware infecting businesses, encrypting hard drives and data on network shares and creating a “ransom” demand in order to unencrypt it. Initially these viruses traveled as typical viruses do – as executable attachments or inside zip files. Most popular of these was CryptoLocker which has made millions of dollars from businesses that didn’t have adequate protection, most recently from a Hollywood hospital that paid $17,000 to get it’s data back. But ransomware has taken a more evil turn – traveling not as an executable that users have been trained to avoid but as a macro inside Word and Excel documents that users often open without a second thought.
As with any threat, it’s important to layer protection and defend your business with a good firewall, good desktop security product as well as a perimeter scanning service we provide through ExchangeDefender.
ExchangeDefender Layered Protection
Before we discuss how ExchangeDefender protects you from ransomware, the most important aspect of IT security isn’t prevention – it’s education:
If you receive an attachment of any kind from a source you don’t recognize: do not open it.
If you receive an attachment from a source that you do recognize but it looks and feels suspicious: do not open it. If the email address looks wrong, if there are misspelled words, unusual formatting or unusual activity: stop.
But let’s talk about prevention. Our partners have many options of using ExchangeDefender to stop the spread of dangerous malware.
Attachment & Content Type Blocking: The following process is the most flawless, but most disruptive, way to address an epidemic. You can choose to let ExchangeDefender block attachments that are used by Microsoft Office documents. We do not recommend this route but it’s nice to know it’s there for the events in which people are getting infected and virus scanning has not been able to pick up threats faster than they are infecting systems.
OLE Virus Filtering: ExchangeDefender will block macro (.vbs) attachments outright. But with the rise of Locky ransomware we now also scan Microsoft Office documents and look for infected and dangerous malware placed in those.
Known Threat Sources: ExchangeDefender also blocks dangerous content before it’s even an issue. Most of the threatening content is sent from the same sources that are popular with spammers, hackers and malware distributors: hacked PCs, servers, and blog sites. We maintain a realtime list of networks that spread dangerous content and routinely block their ability to infect our users.
Firewall & Site Blocking: Ultimately, the largest single source of infections isn’t the ExchangeDefender protected or hosted mailbox – it comes through Yahoo mail, Gmail and other non-business email service. If you aren’t blocking those at your work you need to be.
What else can be done?
As mentioned above, client education is the #1 way to address these. Contact our marketing department and ask them to build you a branded best practices flyer for email and Outlook (Hosted Exchange clients only). There are very simple ways to tell when a message is not from your bank or from UPS.
Establish a regularly scheduled backup system for all critical client PCs.
Layer your antivirus protection. No, one AV vendor is not enough and ExchangeDefender uses several commercial and dozens of proprietary data sources to detect and isolate dangerous content. No matter how much you love your single AV vendor and they claim they are the best – like everyone else they will have an infection evade their scan. If you only have one AV engine, consider adding something like ClamAV to your arsenal.
Establish a review of policies and security implementations. We often see that partners rarely configure ExchangeDefender or monitor it in a way that gives them actionable intelligence. The same can be said for client PCs: Are you monitoring your AV implementations? Are you checking that users aren’t turning off AV or firewalls? Are you looking at strange traffic patterns, use of private proxy or VPN networks to evade network security policies?
CryptoLocker and Locky are neither the first nor the most dangerous threats networks face. But with ExchangeDefender, education and layered security we can keep most online outbreaks from affecting business operations.
ExchangeDefender World Tour
Our world tour kicked off in Chicago in January and I’m about to leave Australia for Dubai. It’s simply amazing to see how well our solutions are received worldwide and how the migration product message resonates with solution providers worldwide.
Australia (Sydney & Melbourne) – February 3-8
Dubai – February 9 – 11
UK (London & nearby) – February 12-16
USA – All day every day
While we are primarily promoting our migrations service, the second most discussed solution concerns Compliance Archiving and helping companies deal with compliance and locating what is becoming a growing problem in businesses small and big: information overflow. I’ve been sitting down with partners and discussing common challenges they face in helping small businesses not only operate better but also manage the mountain of information they have built up. As one partner noted: “Years ago they had one filing cabinet for the whole company and a single person could locate any contract or agreement. Now each employee has dozens of cabinets of their own and discovering who said what and when is turning into a logistical nightmare”; I can personally relate to this a lot and I’m very happy to go over how we can help businesses manage this better and have a private Google of their own for the business intelligence they have collected.
The 365 Elephants In The Room
Technologically, I have nothing against Office 365. Exchange is Exchange no matter where it is. Even business-wise, I think their plan selection effectively separates big business from consumer levels.
My main message to partners and my biggest point of differentiation is that our solution is built for a business. From the ground up everything is designed, supported and documented in a way to facilitate business critical operations where one minor issue immediately becomes an emergency as the whole business runs on it. This is where our differentiation and our people and our process and our LiveArchive make an enormous difference and where we ultimately build our solution.
Unfortunately, many discover this differentiation once the consumer solution fails them. When they have to spend time on the phone waiting for support, or a random outage takes hours or days to resolve. At that point they realized they are running business critical systems on a consumer platform with the customer service and support that explains the low end pricing. Everything is great until you need something and then realize that what you have doesn’t fit your needs.
That said, the entry level Exchange and low pricing is not a compromise we will be pursuing. In all of my discussions with service providers these cloud services are already included in the managed services cost. How do more sophisticated partners handle inquiries about Office 365 or Google Apps?
We have a solution that uses exactly the same technology on the backend but it’s build for business by the partners that we have worked for years and we trust. In addition to what you see with Office 365 you also get 1 year of business continuity so when there is a service interruption you can continue to send and receive email. There is also encryption in the product as well as advanced junk mail management so you never miss important messages. And we should also discuss compliance.
Need a desktop version of Office? We can either get you a subscription for $99/year or buy one outright that you own.
It’s that simple.
Migrations = Revenues
It’s a thrill to hear how my message in the presentations across the globe resonates with partners. Everyone sees a different value in ExchangeDefender handling the mail moving portion of the job. Some see additional revenues. Some see decreased costs. Some see more customers faster.
Everyone sees the opportunity to grow. Which is why we chose to dedicate so much of our effort to it.
As I like to mention in my presentations, the secret to success and profits is two fold: “Either find a way to make your revenues by doing less, or find a way to sell more at a higher cost.” With pricing being the eternal argument, the only way we can make our partners grow consistently and quickly is by helping do more of your work. Migrations are just the start and we are doing remarkably well with it worldwide. With each project we get better and learn to manage expectations better and improve our process – something that our partners hopefully never have to go through again. With us handling Outlook/Exchange and partners managed offerings taking care of the user/desktop, the ability to move to the cloud quickly and grow your client base as fast as you can reach/sell them is simply a recipe to follow in 2014.
We are simply making it impossible for you to turn this down in 2014.
I’m happy to say that I’m hearing that loud and clear on two continents so far ![]() Now off to Dubai and Europe.
Now off to Dubai and Europe.
Sincerely,
Vlad Mazek







