What Is a Watering Hole Attack (and Why You Should Care)
Ever heard of a watering hole attack? It sounds like something from the wild, but it’s actually one of the sneakier tricks in the cyber world. Watering hole attacks are most commonly classified as a supply chain attack (or strategic web compromise).
Instead of chasing their victims, cybercriminals set a trap where they know their targets will go, just like predators waiting at a watering hole for unsuspecting animals to stop by for a drink.
In tech terms, that “watering hole” is a trusted website, one you visit all the time for business, industry news, or client services. Attackers quietly infect it with malicious code, and when you or your coworkers visit it, bam you’ve just been compromised.
How It Works
- Reconnaissance: The attacker figures out which websites your team visits regularly—like a vendor portal, industry association, or community forum.
- Compromise: They hack that website and inject malware or exploit code into it.
- Infection: When someone from your company visits, their browser runs the hidden script, downloading malware in the background.
- Exfiltration: Now the attacker has a foothold on your system or network, ready to steal data or credentials.
And the worst part? Because it’s coming from a legitimate, trusted website, traditional filters or security systems often don’t raise a red flag.
Why It’s So Dangerous
Watering hole attacks are hard to detect because everything looks normal—until it’s not.
- You’re hit through websites you trust.
- The malicious code is often hidden in legitimate content.
- Multiple users can be infected at once.
- The attacker can remain undetected for weeks or even months.
These attacks are increasingly popular among state-sponsored groups and targeted business espionage, especially when the goal is to infect an entire sector (like defense, finance, or law).
How to Protect Your Business
Here’s how to keep your team from “drinking from the wrong watering hole”:
- Keep software and browsers updated – Patch vulnerabilities fast; attackers love outdated plugins.
- Use advanced endpoint protection – Behavioral security catches weird activity that signature scanners miss.
- Segment your network – Limit how far an infection can spread.
- Monitor your vendors and partners – Make sure the sites you rely on aren’t compromised.
- Deploy DNS and email security solutions – Stop malicious redirects, attachments, and spoofed domains before they ever reach your team.
- Educate your staff – Even legit-looking sites can be hijacked; stay alert for unexpected downloads or pop-ups.
How ExchangeDefender Helps
At ExchangeDefender, we’re big believers in layered defense—because one tool can’t stop every type of threat.
- Our email security blocks phishing and malware before they hit your inbox.
- Our DNS protection helps stop users from reaching malicious or hijacked websites.
- And our policy controls give admins the ability to manage block and allow lists across entire organizations—no guesswork, no chaos.
It’s all about closing the gaps between trust and risk—so you can browse, click, and communicate safely.
👉 Learn more about securing your communications: www.ExchangeDefender.com
ExchangeDefender Rolls Out Advanced ‘Reject Policies’ for Safer Inboxes
At ExchangeDefender we’ve always seen ourselves as the firewall that keeps unwanted email content entering or exiting our clients network. To keep compliance simple we never deleted emails – if the content was objectionable we would scan it, log it, and let org and user policies choose what happens to the message.
As the email world becomes more dangerous, with AI capable of conducting social engineering scams at scale, IT teams are looking for new policies that can handle it.
At ExchangeDefender we work closely with our partners around the world and this feature is courtesy of Tommy from Twisted Networx.
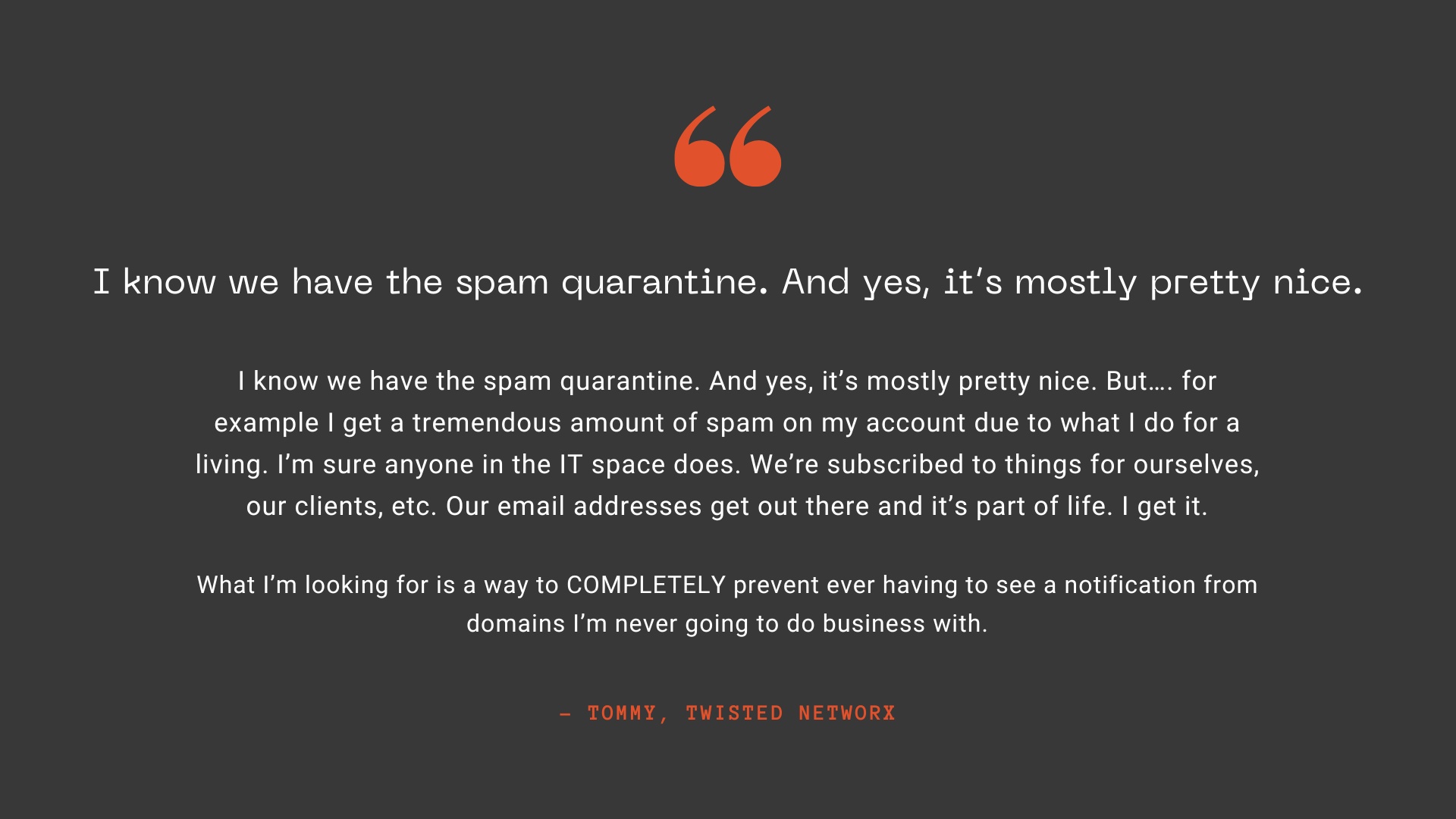
Tommy is hardly alone when it comes to this issue, some businesses pride themselves on the amount of money they spend on aggressive marketing via email. Ghost resubscribes, unsubscribe pages not working, confusing UI to trick you into buying or sharing info, and endless scams are just a part of business on the Internet these days. It’s something ExchangeDefender can help you fix.
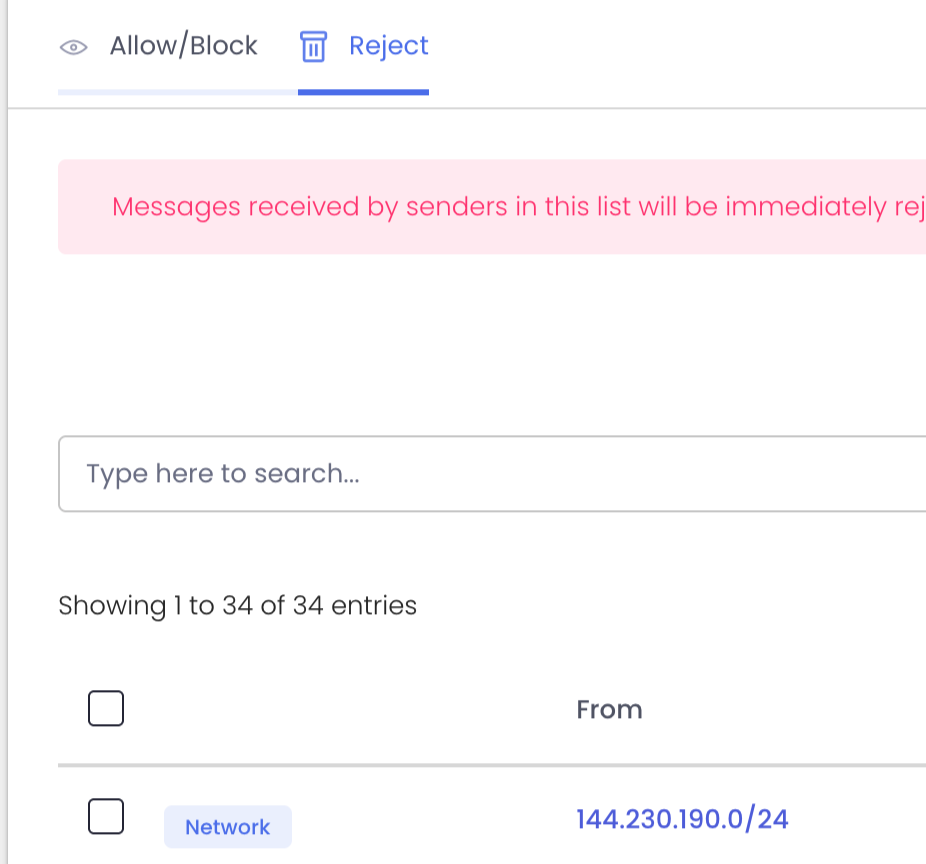
We’re introducing Reject Policies.
If you’ve identified an organization you do not want to communicate with for any reason, or if you have a network you want to keep out, or if you just want a quieter quarantine: ExchangeDefender will now reject the email on your behalf and you will never have to see it again.
For compliance purposes we will of course log the rejection in the Domain Admin logging facility at https://admin.exchangedefender.com but the message meta and any data will be rejected at the edge of the ExchangeDefender network. This way you will still be able to troubleshoot mail flow and make adjustments as needed.
We’re building a more flexible, powerful ExchangeDefender to meet real-world business challenges—and your feedback plays a big part in that. If you’ve got ideas that could make your email experience more secure or productive, we’d love to hear them.
New features and updated policies are rolling out later this fall. Stay in the loop by visiting https://support.exchangedefender.com, checking out our blog, or following us on social media.
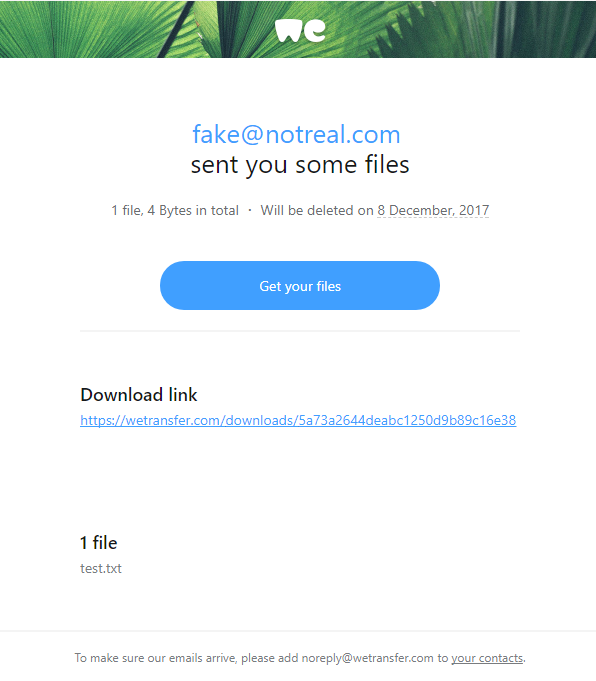
Hackers Use Fake WeTransfer Emails to Steal Your Information
If you’ve ever shared a big file online, chances are you’ve used WeTransfer. It’s quick, it’s easy, and most importantly—it’s trusted. And that’s exactly why scammers love it.
Lately, there’s been a wave of phishing emails that look like they’re coming from WeTransfer. You get a message in your inbox saying something like:
- “You’ve received files”
- “Here’s your invoice via WeTransfer”
- “Download your contract now”
Sounds legit, right? The problem is, those links don’t actually take you to WeTransfer. Instead, they lead you to sketchy sites designed to steal your email login, personal info, or even infect your computer with malware.
Fordham Edu
https://medium.com/@resonance.security
So, how do you spot a fake?
Here are some quick red flags:
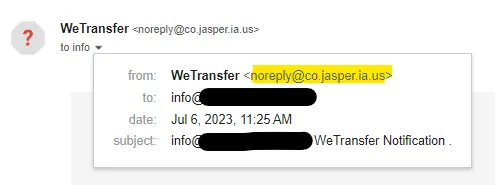
- Check the sender’s address. Real WeTransfer emails come from
@wetransfer.com. Anything else? 🚩 - Hover over the link. If the URL doesn’t point to
wetransfer.comorwe.tl, don’t click. - Unexpected transfers. If you weren’t expecting files, especially invoices or contracts, double-check with the sender.
- Scare tactics. If the message pressures you with “download immediately” or “expires in 1 hour,” take a breath. That urgency is a classic trick.
- Attachments. WeTransfer usually gives you a download link, not random attachments with .zip or .exe files.
What’s at risk if you fall for it?
A lot, unfortunately. Clicking on a fake transfer can mean:
- Your email or cloud account gets hacked.
- Sensitive data leaks into the wrong hands.
- Your device gets hit with malware (worst case: ransomware).
How to protect yourself
The good news? Staying safe is pretty simple:
- Verify before you click. If someone says they sent you files, confirm with them outside of email (call, text, Teams, Slack—whatever you use).
- Turn on MFA. Multi-factor authentication makes it way harder for scammers to break into your accounts.
- Keep your guard up. Train yourself (and your team, if you’re running a business) to spot phishing tactics.
- Update your devices. Security patches and antivirus tools help catch threats before they cause real damage.
How ExchangeDefender Helps
Here at ExchangeDefender, we take phishing attacks like these seriously. Our filters flag suspicious links, block spoofed domains, and keep bad emails out of your inbox before you even have to think about them. Plus, we love keeping you in the loop with updates like this—because knowledge is one of the best defenses.
Our Expert Tip:
WeTransfer is a great tool, but remember: scammers always follow trust. The more popular a platform is, the more likely it’s going to be abused. So next time you see that “You’ve received files” email—pause, hover, and think before you click.
Sources
What Happens After a Cyber-Attack? The Real Cost for Small Businesses

Let’s face it—most small businesses don’t wake up thinking today will be the day they get hacked. But when it happens, the impact can be swift, serious, and long-lasting.
A small business has suffered from a cyber-attack—what could be the resultant damage?
Spoiler: It’s a lot more than just a locked computer screen.
Let’s break it down in plain English.
Financial Fallout
Hackers love going after small businesses because defenses are often weaker—and payouts can still be big.
- Ransomware may demand thousands just to give back access to your files.
- Phishing or business email compromise could lead to fraudulent money transfers.
- Remediation costs (forensic investigation, legal help, software cleanup) stack up fast.
And while you’re fixing all that…
Time Is Money—And You’ll Lose Both
Most small teams rely on a few key systems to keep things moving. When those go down, so does your ability to do business. Orders get delayed. Calls go unanswered. Work comes to a screeching halt. And while the tech side gets untangled, your customers? They’re already wondering what’s going on.
You might be offline for hours. Maybe days. Either way, your clients won’t wait forever.
It Gets Personal Fast
A lot of cyberattacks aren’t just about locking up files—they’re about stealing data. That could mean employee records, customer information, payment details, contracts, or anything else sensitive. If that data ends up exposed, you may have to notify everyone affected. In some industries, that’s not just a courtesy—it’s the law.
And if clients lose trust? That can cost far more than any ransom demand.
The Recovery Isn’t Just Technical
Once the threat is handled (and your blood pressure returns to normal), you still have to deal with the cleanup. That might mean replacing devices, hiring an expert to audit your systems, redoing your cybersecurity setup, or retraining your team.
The worst part? This whole situation was probably preventable.
You Don’t Need an IT Department to Be Protected
Most small businesses don’t have a dedicated IT team—and that’s exactly why hackers love targeting them. They count on people being too busy, too stretched, or just unaware of the risks.
That’s where we come in.
ExchangeDefender is built for teams like yours—small, mighty, and ready to protect what matters. From secure file sharing to bulletproof email protection, we make cybersecurity simple, affordable, and human.
5 Hidden Email Problems Encryption Solves Instantly
(and why ExchangeDefender is your easiest fix)
For most small businesses, email is the default way to communicate, send documents, close deals, and support clients. It’s fast, familiar, and convenient.
But under the surface? It’s also where some of your biggest risks live—risks that most SMBs and MSPs don’t see until it’s too late.
That’s where ExchangeDefender Encryption comes in. It’s not just about locking emails—it’s about solving the real problems you didn’t even know you had. Here are five issues it tackles the moment you turn it on:
1. You sent it to the wrong person
Mistakes happen. But when they involve sensitive info, they can turn into major incidents.
ExchangeDefender Encryption makes sure that even if your email ends up in the wrong hands, it can’t be read without proper authentication.
2. Your attachments are exposed
Contracts, client data, tax info—your attachments carry the good stuff. And without encryption, they’re easy targets.
With built-in attachment protection, ExchangeDefender keeps your files locked tight during transit and storage.
3. You have zero visibility
Standard email doesn’t tell you what happens after you hit “send.” Did they open it? Forward it? Screenshot it?
ExchangeDefender gives you detailed tracking and read receipts, so you stay in the loop.
4. Your team uses different email platforms
Some use Outlook. Some use Gmail. Others are mobile-only. Security gaps are everywhere.
ExchangeDefender works seamlessly across all platforms—no special downloads, no learning curve, just secure email everywhere.
5. You’re worried about compliance
HIPAA. GDPR. CMMC. It’s a lot. And falling short isn’t an option.
ExchangeDefender offers auto-detection, policy enforcement, reporting, and message expiration tools to make compliance a breeze.
Bottom line
You don’t have to overhaul your email system to get secure. With ExchangeDefender Encryption, you protect sensitive data, build client trust, and avoid costly mistakes—with one simple solution.
Browse Online Like a Boss: Our Cybersecurity Experts Share Top Tips

Phishing scams and malware lurk everywhere online, even in emails. But fear not! Here at ExchangeDefender, our cybersecurity experts have compiled their best practices to keep you safe while browsing from email links:
1. Check Before You Click:
Hover over the link to see the actual URL. Does it match the text displayed? Mismatched text is a red flag!
2. Know the Sender:
Don’t click links from unknown senders. If it’s from someone you don’t recognize, contact the sender directly to confirm the email’s legitimacy.
3. Look Out for Lookalikes:
Be wary of emails with seemingly familiar sender addresses. Typos or slight variations can indicate a spoofing attempt.
4. Beware of Urgency:
Phishing emails often pressure you to act quickly. Take a breath, verify the sender, and don’t be afraid to delete suspicious emails.
5. When in Doubt, Throw it Out:
If you’re unsure about a link, err on the side of caution and delete the email. It’s better to be safe than sorry!
BONUS TIP: Enable strong spam filtering – tools like ExchangeDefender can significantly reduce phishing attempts reaching your inbox.
Enhanced Security: ExchangeDefender Now Supports Custom Authenticator Apps for MFA!

ExchangeDefender has recently enhanced our MFA features (multi-factor authentication) to help you enforce domain-level MFA compliance and to make it easier for users to be enrolled and protected by a layered authentication process automatically.
Simply put, we’re making it easier for you to keep everyone protected.
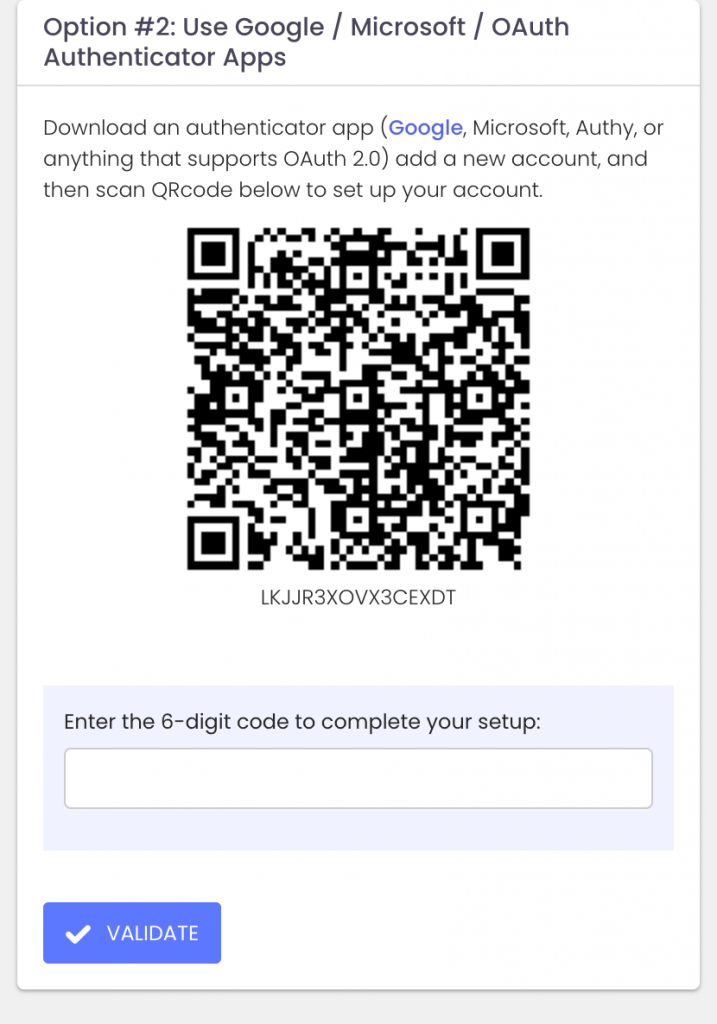
Today we are announcing ExchangeDefender MFA support for custom authenticator apps. By now everyone is familiar with our typical MFA functionality, available under your Settings at https://admin.exchangedefender.com. Just scan the QR code on your device and you’re set!
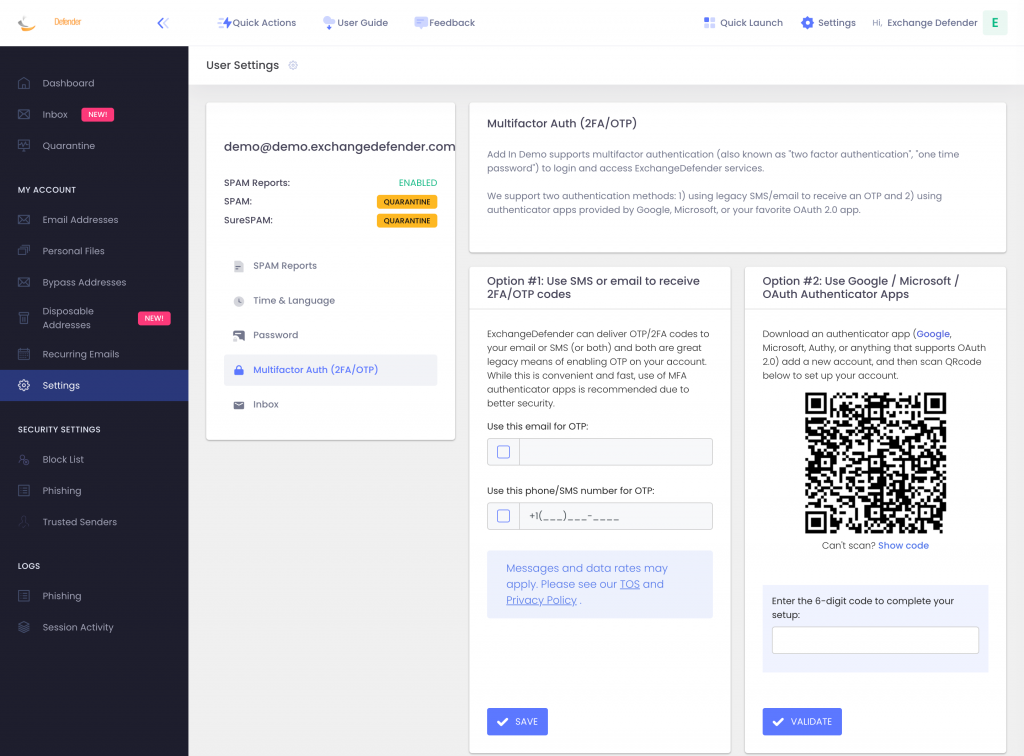
BUT WHAT IF YOUR DEVICE DOESN’T HAVE A CAMERA?
ExchangeDefender now supports MFA app enrollment using a QR code. This is great for scenarios in which:
– You don’t have a camera on your device
– The QR code doesn’t seem to scan (problems with the camera or monitor)
– You want to use a text-based MFA app
– You want to integrate PowerShell/no-code with MFA
– You want to share your MFA codes with others
If you’re in one of those scenarios, note the text under the QR code when you start the enrollment:
Click on the Can’t scan? Show code link and you’ll get the TOTP secret (aka secret code, MFA code). Paste it in your solution and paste back the 6 digit code it generates. That’s it, you’re done. MFA is now enforced and ExchangeDefender will rely on the codes generated by your app to validate MFA and grant access to your account.
All our features come from user feedback so if there is something we need to be doing to keep you more secure please let us know!
Enhanced MFA Enforcement Policy: Strengthening ExchangeDefender Security Measures

For years, ExchangeDefender users have enjoyed enhanced login security via multi-factor authentication security (aka MFA, 2FA, OTP). In our March feature update, we hope to improve your security and enhance MFA enrollment to keep you and your data safe. Allow us to introduce to you the new MFA Enforcement Policy!
Note from the boss: Before we get to any discussion of policies, our official recommendation is to enforce MFA on every service we provide and to rotate passwords at least once a quarter. I know, nobody likes the second validation prompt but this is a standard in the industry and I can’t think of a bank or a vendor that doesn’t require it. Maybe I’m jaded because we’re a cybersecurity company.. and with all the layers of MFA/VPN/auth we have in place I spend an insane amount of time trying to find my key or wait for the new pin to display in my authentication app. Because when I interact with a vendor that holds my information and they have no login security.. all I can wonder is what else they’re not doing to keep my data safe? Is this a real business or some WordPress plugin?
At the same time, I understand we have a ton of customers in SMB space where sometimes (obnoxious) tech can be slow and difficult to implement. But you pay us to keep you safe – and to keep your backups safe, and to keep your business continuity safe, and to do that we absolutely must require MFA. But we also can’t expect staff who have clicked on a Release/Trust link for over a decade to be cool with suddenly being forced into MFA enforcement workflow on Monday. So we designed a compromise. I hope it fits your organization and I hope you adopt it as fast as possible.
Sincerely,
–Vlad Mazek, CEO Own Web Now Corp.
In March 2024 you will have the ability to enforce or require MFA enrollment at the domain level. What this means is that you’ll be able to require MFA enrollment with an authenticator app for everyone with just one click at https://admin.exchangedefender.com:
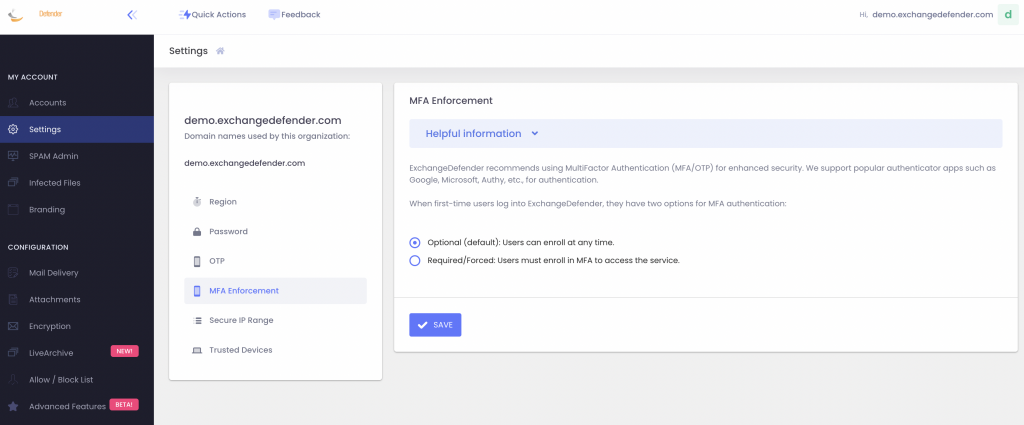
With this policy, you can secure your users’ login with multi-factor authentication without making them enroll a device.
How does it work?
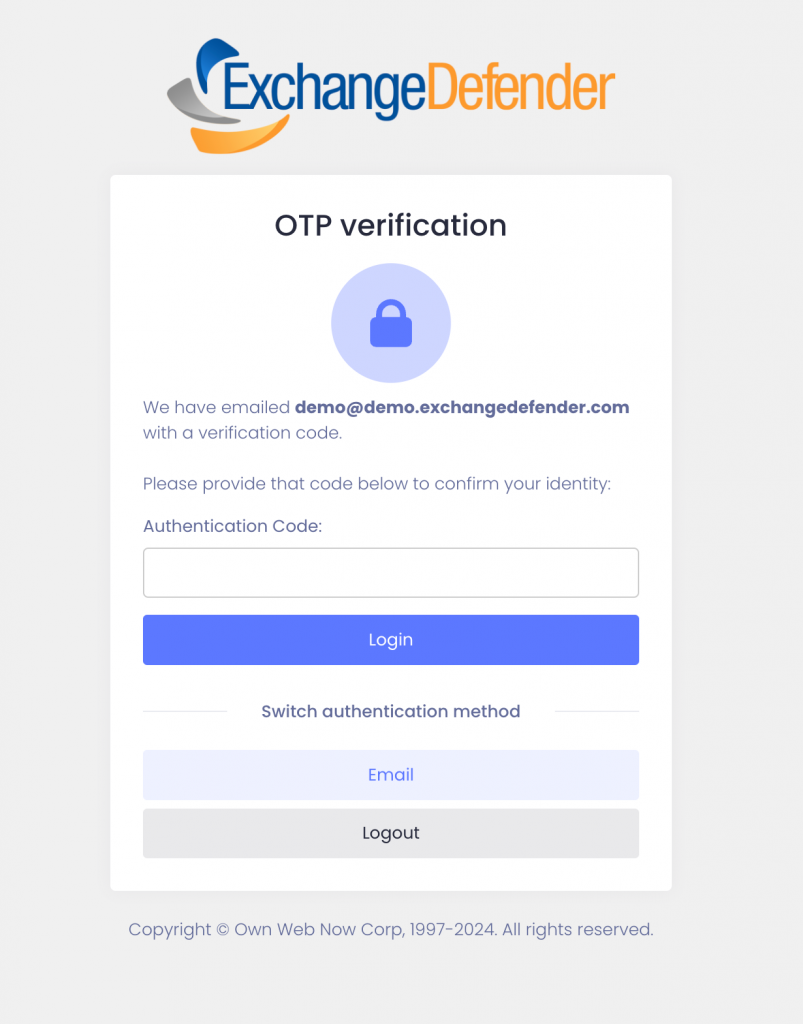
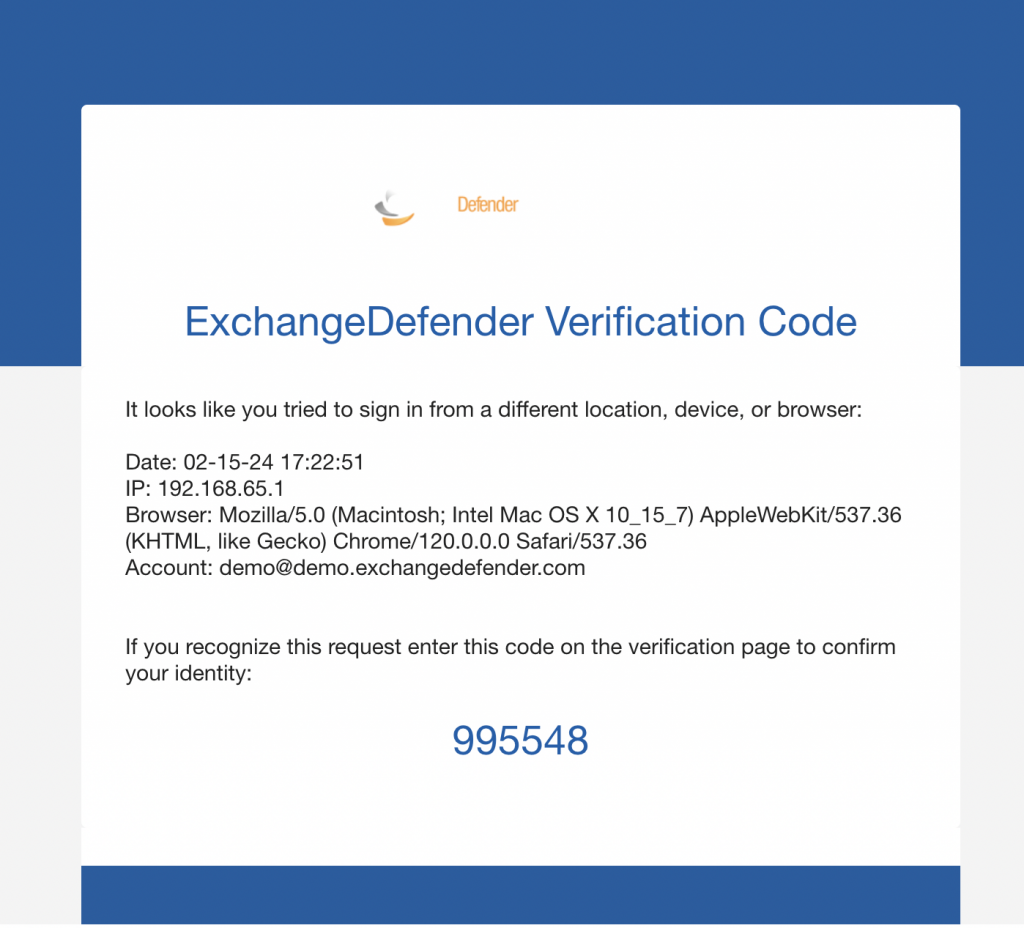
When your users go to admin.exchangedefender.com and attempt to access Inbox, WFS, or LiveArchive we will check their MFA enrollment and if none is found we’ll just tell them we have to verify their identity:
When they check their mailbox they’ll see an email from ExchangeDefender and just provide the code back.
This way your ExchangeDefender login is technically secured at ExchangeDefender with MFA even if you haven’t enrolled a device in MFA yet. There is no way to get into the secure areas of your account without enrolling into MFA. But what if someone guessed the password, they can just enroll a device and hijack the account, right? No.
When you set MFA Enforcement to Required/Forced, all your users are automatically set into an MFA mode that relies on their email address for secondary verification. When they visit admin.exchangedefender.com for the first time and provide their username and password the system will check their MFA enrollment and if email MFA is detected the system will send them an email with a verification code to proceed. This way we’re using the email MFA as a way to verify their identity and then we enroll their authenticator app as usual by scanning the QR code.
ExchangeDefender Quarantine Reports behavior will not change at all as a result of the change in the MFA Enforcement policy. ExchangeDefender Quarantine Reports do not rely on the login system at all as the user is never prompted to authenticate to trigger the release of the message. Instead, quarantine operations are tokenized and one “release” request does not automatically grant any other release or trust requests with the same token. It also doesn’t automatically log them into ExchangeDefender so there is no getting by the MFA!
Secure your logins now
It’s 2024 and the world has changed when it comes to authentication and identity when dealing with services online. Experiencing a cybersecurity threat or compromise is an incredibly expensive and frustrating experience that can easily be avoided by requiring an ID check before granting access to sensitive information. ExchangeDefender MFA Enforcement Policy is your way to protecting your organization from unauthorized and unverified access.
Improved SPAM Release Security: Quick Release

ExchangeDefender is giving users more power to lock down their valuable data. Now that ExchangeDefender handles business continuity and backups for M365/Gmail tenants there is even more information in ExchangeDefender that demands more flexibility with security policies. First, let’s talk about the upcoming feature that allows you to lock down your ExchangeDefender SPAM Quarantine Report activity.
Bit of background: ExchangeDefender Quarantine Reports are an immensely popular ExchangeDefender feature (coming up for an upgrade this spring btw!) that sends users a list of quarantined messages with a set schedule. Users tend to rarely look in Junk Items or review SPAM unless they are waiting for something so this is a cool feature that our users just love. Scroll down the list of quarantined messages and release or trust just by tapping the link. Super convenient, but does it meet your security requirements?
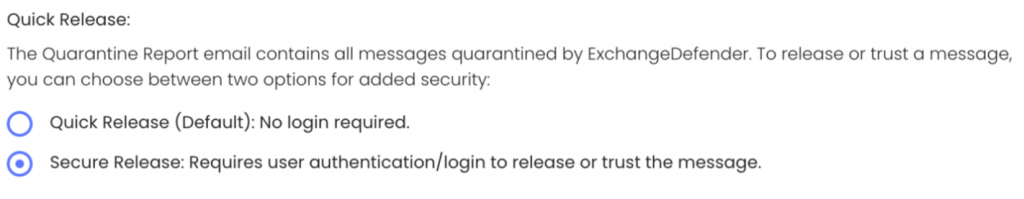
ExchangeDefender Quick Release feature now enables you to choose between convenience and a more secure release process. For many organizations, having the message released or get added to trusted senders with just a click is a huge time saver and user convenience. But if your Microsoft M365 / Gmail account gets compromised (which happens ALL the time) or you deploy a new security/business/CRM (mostly AI stuff) that scans links then this “convenience” can turn into an Inbox packed with SPAM messages that some hacker/service inadvertently released.
If this happens to you, know that ExchangeDefender can help with the “Secure Release” setting. By enforcing Secure Release, when the user clicks to release or trust a message they will be prompted to authenticate before they can release/trust the message. This way if you get hacked or install link scanning/crawling software in your tenant will not be able to access the messages without a password.
Now please, go setup your favorite authenticator app with ExchangeDefender MFA (next up, you can set it to be mandatory/required)
ExchangeDefender Phishing Firewall and Microsoft Defender
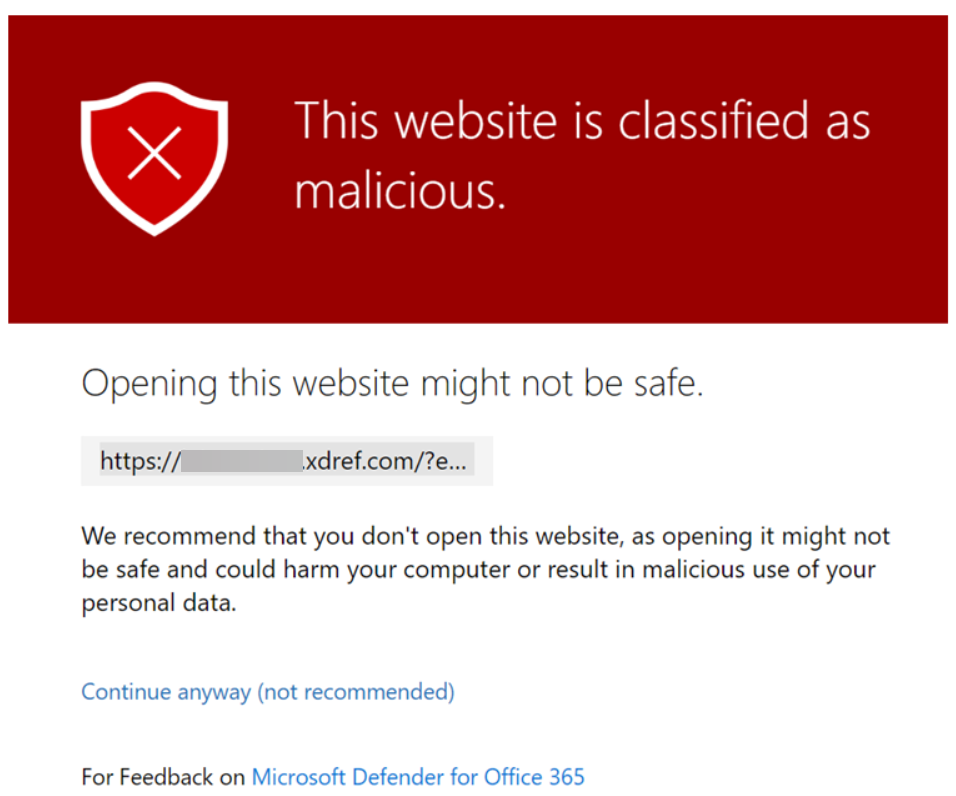
Now and then Microsoft Defender will encounter something potentially dangerous when it’s processing your browsing activity. Most of the time it is just the URL of a site they’ve blacklisted.
Enter ExchangeDefender Phishing Firewall. We rewrite every URL going through our service to give our users an extra layer of security and prevent malware and phishing. If you’ve seen the xdref.com links in your email, that’s US keeping you from accidentally clicking on a legitimate link and getting a zero-day exploit compromising your PC. Well, Microsoft Defender looks at the same link and its contents and can flag an entire URL of your phishing firewall. Then you end up seeing this:
How do I get this resolved?
Since this URL is exclusively used by you and your clients, make sure you’re using ExchangeDefender Outbound Service to route outbound mail (our outbound service strips all the xdref.com URLs).
Next, please report the problem with the URL to Microsoft at this location:
https://security.microsoft.com/reportsubmission?viewid=url
How do I fix it?
There are two ways to solve this problem within your tenant at Microsoft 365. The fastest way is with PowerShell:
New-TenantAllowBlockListItems -ListType Url -Allow -Entries ~xdref.com~ -NoExpiration
The more user-friendly way to allow the URL is through the Microsoft Defender Portal at the following URL (make sure you’re logged in first):
https://security.microsoft.com/tenantAllowBlockList
Microsoft tends to move its security components around a lot so if the URL changes login to the Microsoft 365 Defender Portal and go to: Policies & Rules> Threat Policies > Rules section > Tenant Allow/Block Lists.
To learn more about Microsoft Defender and how to manage its security policies on this topic please see the following KB article.
Tip: ExchangeDefender recommends executing this process when the client is onboarded, but it will work at any time.