Network Upgrades at ExchangeDefender
Many IT professionals have gone through a lifecycle infrastructure upgrade – the all important cycle of improving the infrastructure as the vendors push down new features with ever increasing resource demands. We’ve been doing that since 1997. One thing that has changed in the past 20 years is the scope and magnitude of both attacks and the network demands to manage them all. We’ve done an excellent job keeping up with them all, with our last major outage (that lasted nearly 4 hours) back in 2011. We learned a lot that day – and rolled it up into our products and services that many of our partners have experienced. These days, with the cloud services, the game is completely different.
I hope you have a moment to join our WEBINAR next Thursday, April 11th, at noon
Register here: https://attendee.gotowebinar.com/register/5700720797827651073
It won’t be the usual rah-rah new features new stuff show. I will speak candidly about how we’ve managed to overcome and triumph in the “Cyber” security game and how we’re still always one step behind whatever 0-day attack vector comes down. I’ll be discussing (somewhat intimate) details about the performance issues, DNS issues, DC issues, subscription issues, 3rd party IP issues, and how all of these have become both an IT management issue and customer service nightmare. I truly hope you join us. I know your time is valuable and schedules get tight so if you can’t make it, the recording will be posted in our portal as usual.
What we learned last week – for the millionth time – is that communication in cases of issues is paramount. When things appear to go down, people panic. They require not just information but reassurance, confidence, and a plan required to address issues. For smaller companies, that’s a matter of just falling back to a cell phone – for larger ones (if it’s not already you, it definitely is something to consider for your clients) that is simply not an option and the volume of activity will easily and quickly overwhelm you. I used to see it every day – when issues come up for our partners, their clients call us.
We’ve made an overwhelming investment – not just in technology and features but manpower – that has fueled our growth for the last few years. I want to share, personally, exactly how we operate and how we’ve been able to both prioritize and execute some of the more impressive infrastructure enhancements and how they are going to be here to serve you for years when something happens.
And then I hope to offer you the same – as a token of our appreciation for your business and your loyalty through the years. Pretty excited, I hope you can join us.
Sincerely,
Vlad Mazek
CEO
ExchangeDefender
ExchangeDefender Exchange Account Lockout
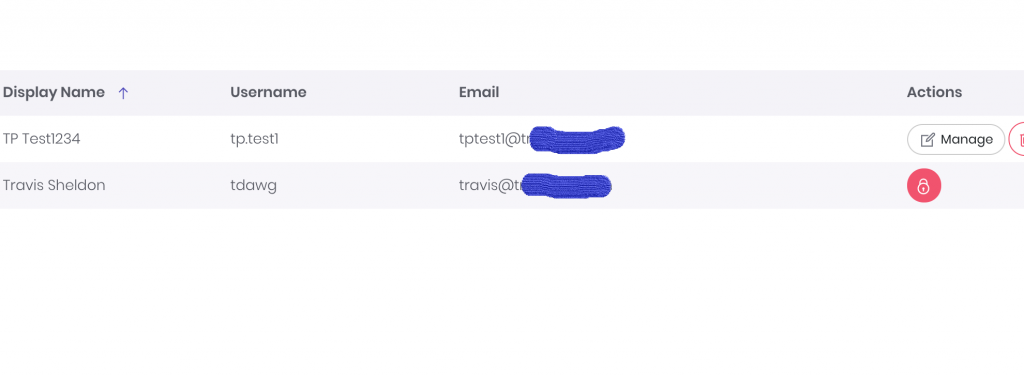
ExchangeDefender is relieved to announce the availability of automated account lockout notifications. Our clients now have the ability to automatically locate, secure, and unlock email accounts that have been locked down due to too many bad login attempts.
You will now notice a red lock icon next to any accounts that have been locked out and you can choose how to proceed in terms of restoring account access:
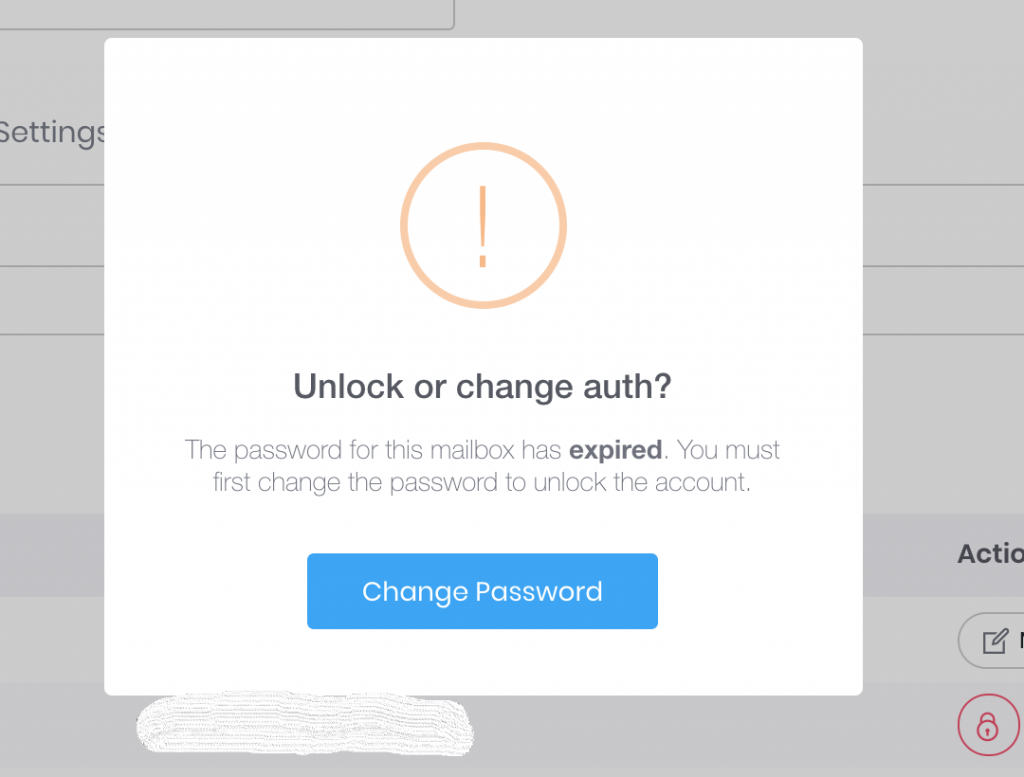
Password hacking and guessing is rampant, and has only been getting worse through 2018. Thankfully, we’ve automated the process of unlocking and changing authentication credentials in 2019.
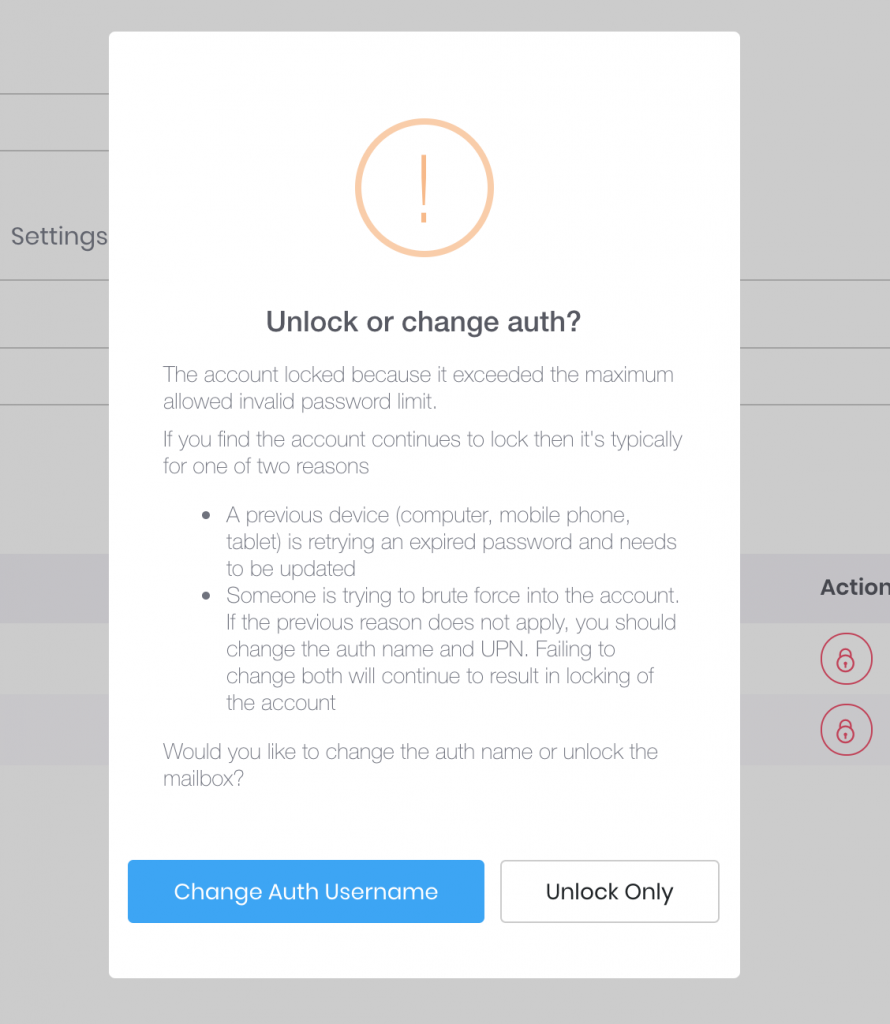
However, there is a special case in which just “Unlock Only” option may be the best.
Suppose you have a power user that has a desktop at work, at home, a laptop or two, 2 iPads, iPhone, Galaxy S9 and a miscellaneous other device that is set to sync mail every minute. Totally not talking about our CEO. But suppose that is the case and you just changed the password – well if all these other devices are trying to authenticate with the old password you may actually trip your corporate policy for the unlock limit and lock the account again.
We hope this automated system will save our partners a ton of time and make managing security and security incidents a breeze. We wish we could have delivered this much sooner but as anyone involved in cybersecurity will tell you, priority #1 is always mitigation of the issue (which we’ve done through all our Exchange 2016 UI and management discussed in our webinars).
This feature will go live later this week (Feb 21, 2019) – please give us feedback and suggestions on what more we can do to give you more power or save you time.
UPDATE: ExchangeDefender Enterprise Security Features
To say that our security webinar went well is an understatement – partners actually loved it. It’s a strange and welcome departure from how my security and hacking conversations usually go (nobody ran away from me crying and screaming into their cell phone) and I cannot tell you how gratifying it felt to introduce security features and have people line up to offer them.
Frankly, it was time. The state of email (and email security) is unsustainable if we let the users and infrastructure we manage act like account security is an afterthought – that just leads to more compromised endpoints that just amplify the next attack that will be more sophisticated, harder to defend – AND – will eventually lead to increase in costs as more infrastructure is needed to protect users who want to act the same ways spammers do. We’ve put a smart lock on the door, it’s your choice whether you want to lock it.
That said – all these features are a part of the ExchangeDefender Enterprise which is designed for very large companies and government where organizational policies override any complaints and gripes end users may have with the security inconvenience. Which is exactly the opposite from the small businesses that MSPs tend to manage.
We get it. And we’re not giving up.
In the nearly two weeks that we’ve been rolling out the new security features to the MSP/SMB UI, we’ve noticed some severe pain points for our users that we’ve moved very aggressively to address and mitigate. Which is my commitment to you – we will keep on stepping up the security and we will find ways to mitigate some of the prompts, alerts, and notifications along the way if you don’t want your users to be aware of what is going on under the hood.
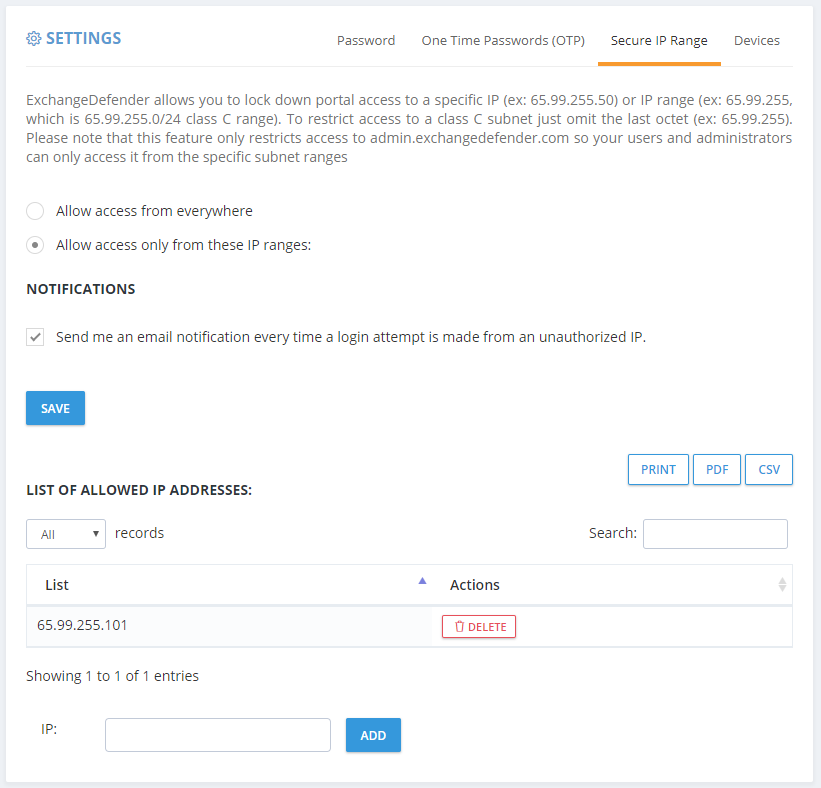
First up, if you’ve chosen to lock down ExchangeDefender admin panels to the restricted IP range you own, you now have the option to turn off email notices every time a login attempt is made from outside of this range.
We’re in progress of making additional changes and exceptions to the IP address restriction policy and removing it from the SPAM release process – so if your employees are mobile or working from home they will soon be able to release a legitimate message (false positive SPAM) from anywhere even with IP restrictions in place. They won’t be able to login to the control panel and make modifications or see other settings but they will be able to get to their email.
We hope this feature enhancement will reduce the amount of email notifications – you will still see them in your event logs.
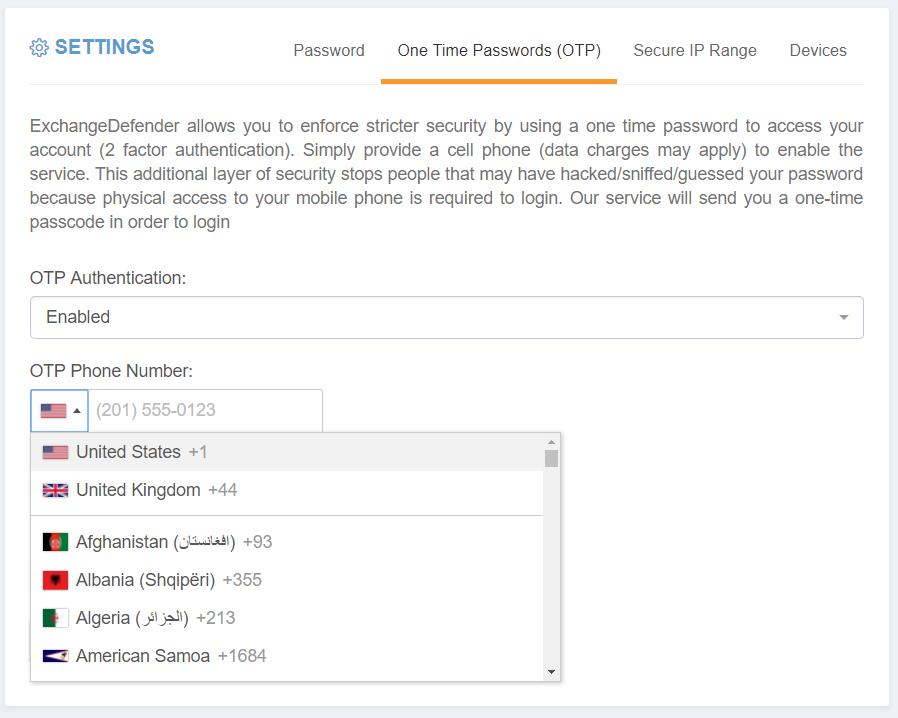
Second, we have opened up our OTP/2FA infrastructure to the whole world.
Finally, the alerts on the clients dashboard. I am going to phrase this carefully as I’m not happy to announce this and will likely change it eventually: You can turn that alert off and stop users from being required to change their passwords very X days. Just set the value to 0. We will revisit this within 30 days but as a mitigation to any unwelcome support calls, yes 0 will just turn it off.
We’ve been working on the announcement and training features for quite some time now and we hope that they will make security implementation and support a problem for ExchangeDefender to handle, instead of burdening our partners with it. In an ideal world, those features would have launched first and we’d slowly trickle down ExchangeDefender Enterprise. Unfortunately, another 600+ million usernames, passwords and other PII has been leaked last week from some very popular sites and the odds that those users and passwords have the same credentials there as at ExchangeDefender are pretty good.
My point is, we are paid to protect and lock down your organizations communication and secrets, something we take extremely seriously. In order to protect all the data you trust us with, we have to lock things down. And as we do so, we will keep user experience front and center.
Thank you for trusting us with your data and thank you for your business.
Sincerely,
Vlad Mazek
CEO
ExchangeDefender
Better Password Policies
ExchangeDefender has been SMB friendly – to a fault, but the era of terrible passwords and plain text passwords is finally over. Not a single piece of ExchangeDefender stores (or offers) user credentials in plain text anymore. We’ve made the transition exceptionally smooth as well, requiring no changes or IT intervention at all.
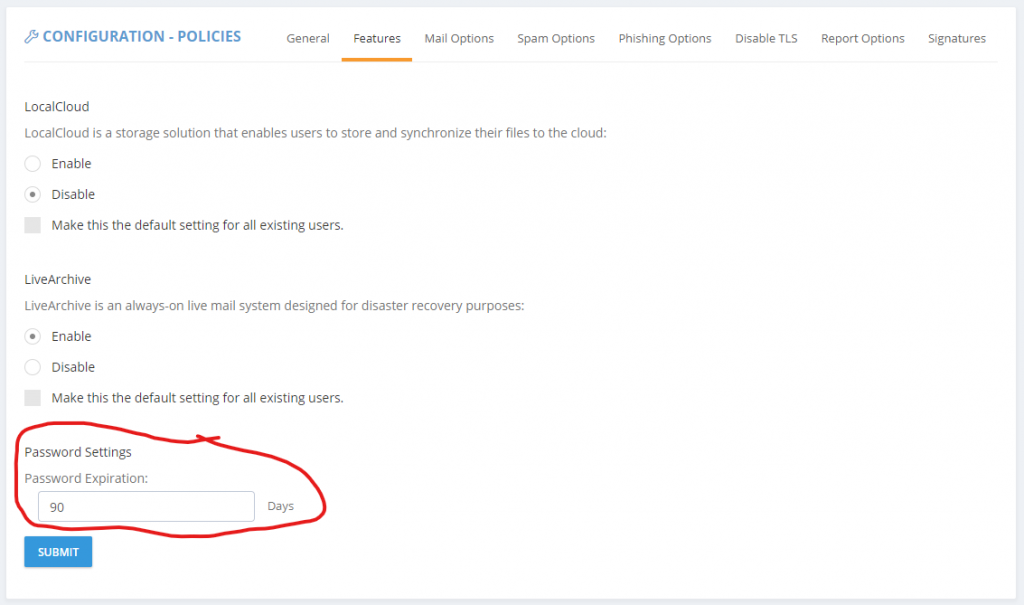
But we cannot encourage it enough. And over the next year you will see us introduce several features meant to help you lock down ExchangeDefender and use it to lock down your overall IT security strategy. We’re happy to introduce password age configuration that allows you to force users to reset their passwords automatically.
This setting can be accessed from the Domain Administrator > Policies > Features section of admin.exchangedefender.com
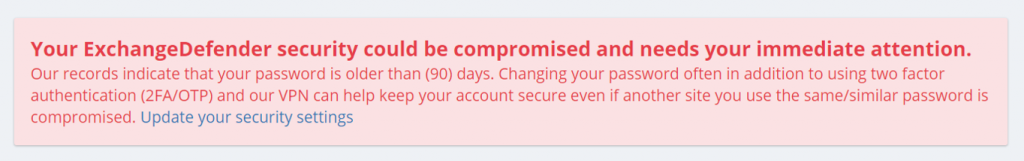
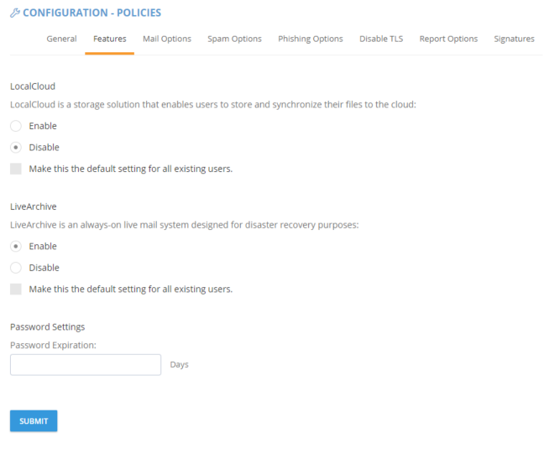 When the password is older than your preset number of days (by default, 90) the user will see an ugly red notice telling them to update their password.
When the password is older than your preset number of days (by default, 90) the user will see an ugly red notice telling them to update their password.
If you set the password expiration to 0 days you will turn this feature off entirely but we cannot discourage it more. The feature is there to help your users avoid having their accounts compromised.
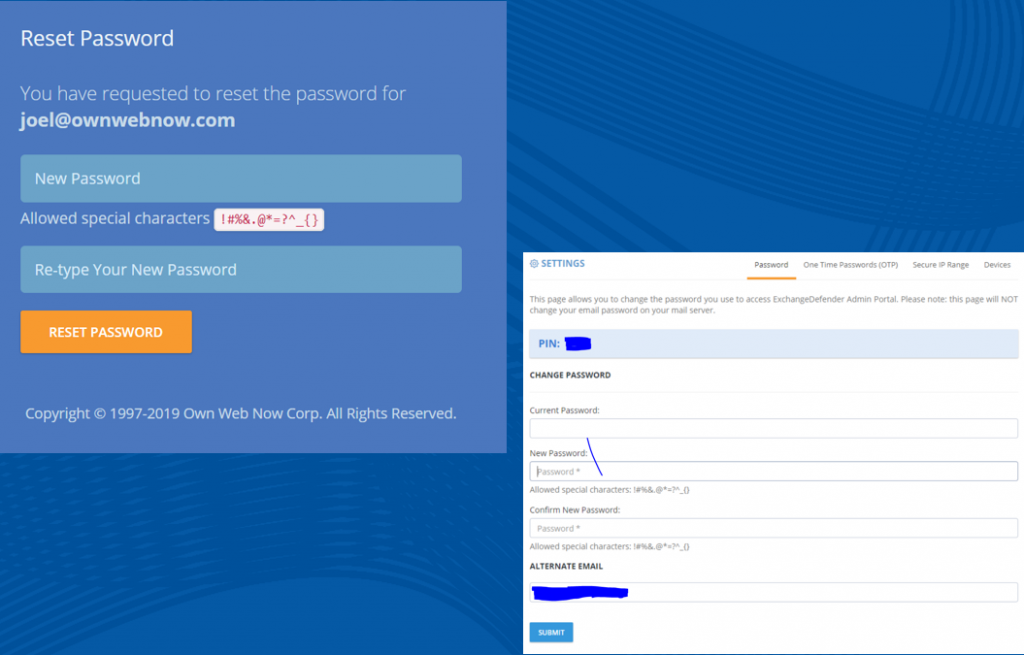
If you implement some of these stronger security features we’ve also got you when it comes to minimizing account management – users can reset their password at any time if they have their PIN on them. So even if their mail server is down, having their PIN handy will let them reset the password without additional authentication. Forgot your pin? No problem, we can email you a reset link to a known email address.
As you can tell, ExchangeDefender will go the extra step of helping your users configure a strong password. It will also keep memory of recent passwords so that they can’t just rotate it back and forth between the same two passwords they use elsewhere.
As you’ve seen with mass password resets , access to advanced access logging , known trusted devices and IP restrictions , we are adding more, and more, of our enterprise features to the ExchangeDefender Pro product.
To hear about all these new security features in more detail please check out the webinar that covers our current security portfolio and how these features make sense.
ExchangeDefender IP and Device Restrictions
ExchangeDefender IP and Device Restrictions
ExchangeDefender is continuing it’s march to becoming your central point of secure communications by bringing even more of our custom Enterprise features down to the SMB/MSP space. As of today, you will start seeing another section added to the Service Provider screen specifically to house our advanced security settings.
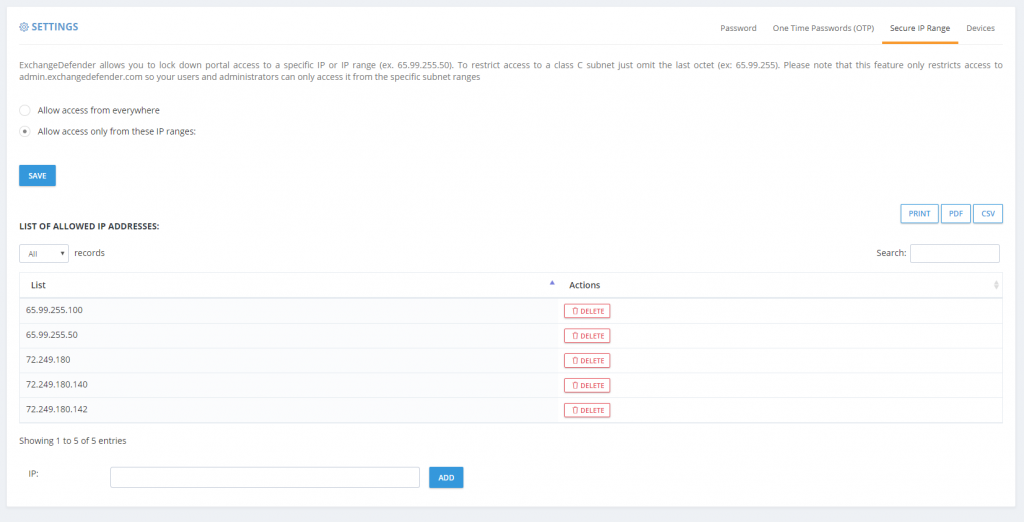
Restrict ExchangeDefender access to your IP range
All large organizations that depend on ExchangeDefender have static IP addresses and IP ranges assigned to them by the ISP. ExchangeDefender has the power to restrict access to your organization (all domain and user logins) and only allow access from your offices.
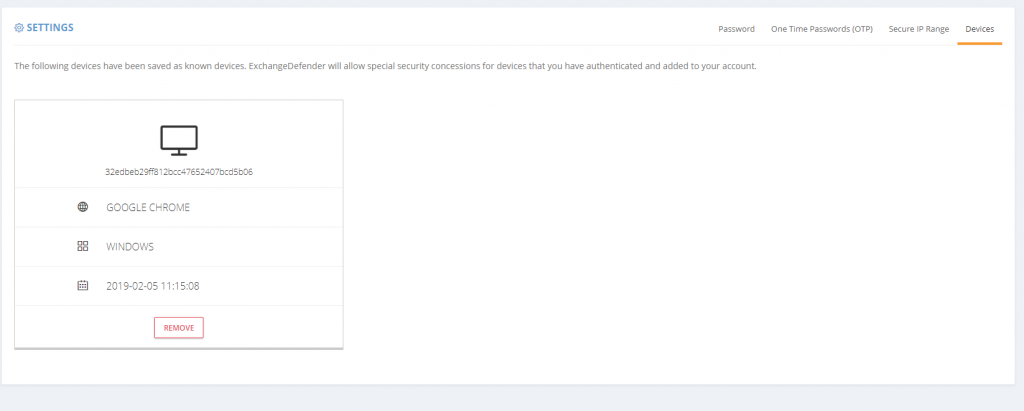
Add Trusted/Known Devices For Easier Access
People love the notion of security until that security gets in a way by prompting them. We only want our security infrastructure to get in a way of hackers and to slow down and annoy people that want to do us harm. Good news is, now you can add devices you know to known and trusted device list.
Doing so will minimize some of the additional checks and verification (such as 2FA/OTP one time password checks when you first log in from an unknown address). As an additional bonus, ExchangeDefender will start to deliver notifications and alerts whenever the system is accessed (successfully, meaning they know your password) from an unknown/untrusted device, giving you the first alert that there is a security issue to address.
As you’ve seen with mass password resets, access to advanced access logging, we are adding more, and more, of our enterprise features to the ExchangeDefender Pro product. To find out what else is on our road map, and how ExchangeDefender will evolve in 2019 to serve your other security needs, please tune into our webinar:
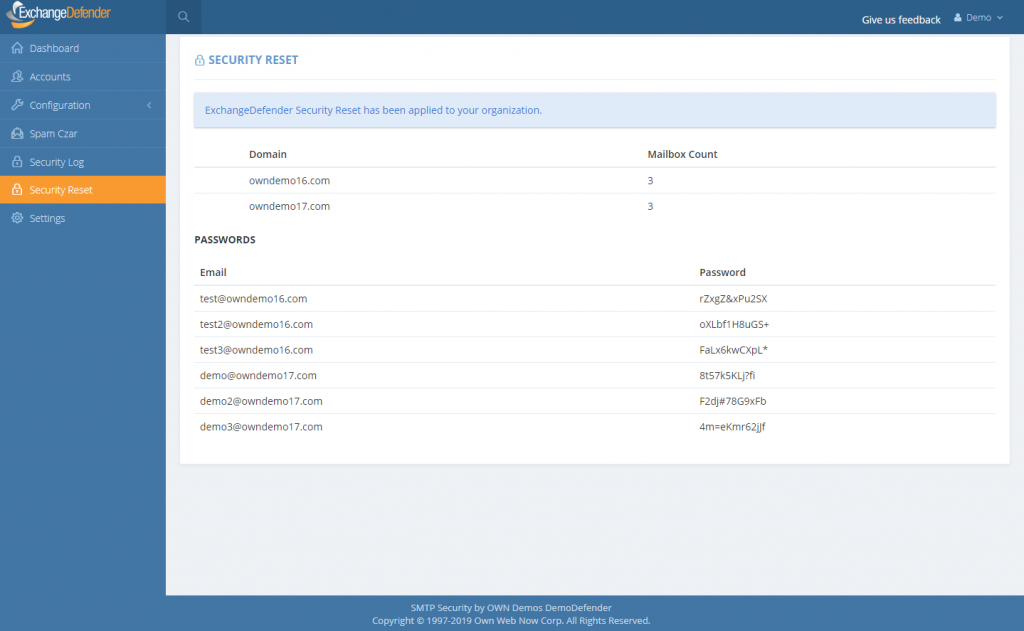
ExchangeDefender Mass Password Reset
ExchangeDefender has always been a great friend to the SMB community where folks hate passwords and password complexity right until the moment their password gets compromised. Once that happens, it’s up to the MSP or poor IT guy to sit around and reset all the passwords in the organization.
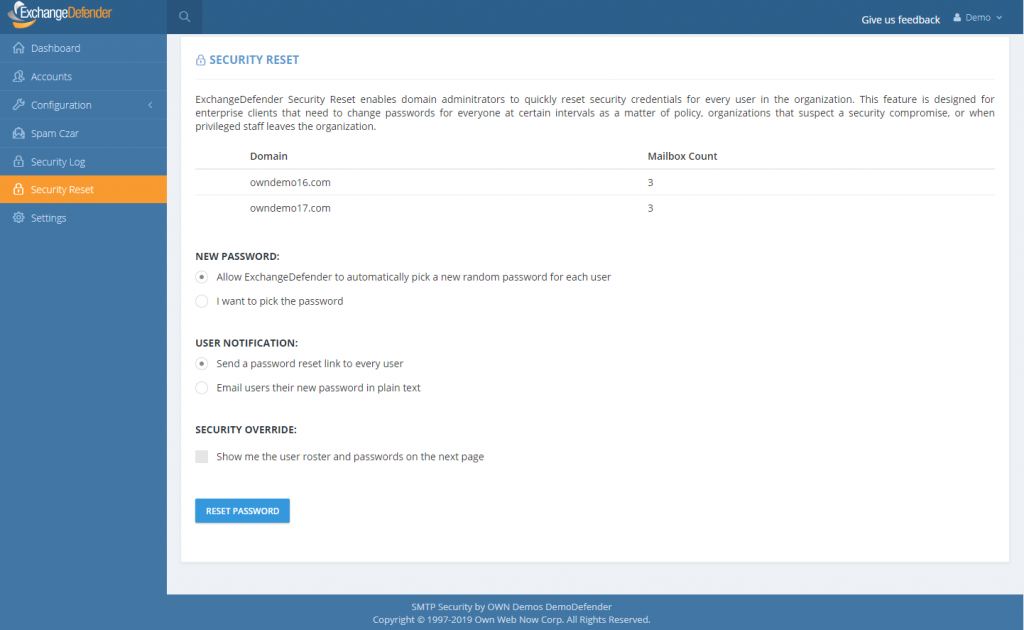
As mentioned previously, a number of ExchangeDefender Enterprise features is being delivered to ExchangeDefender Pro so now you’ll have the ability to reset every single users password quickly.
Under the domain login you will now see a “Security Reset” link that will allow you to either randomly assign a strong password (smart) and send your users a reset link or pick the same password for all users (outright idiotic but “business requirements”).
If you are an MSP assisting a client during an outage and this is the first time you’re making your users aware of ExchangeDefender LiveArchive for business continuity, you can also print out the passwords and/or email them to your users in plain text. This is a horrible, terrible, idiotic, really bad idea that virtually guarantees you’re going to get hacked but we are here to serve and Howard is a really good friend so here it is:
Just a word of warning: If you select to send your users a new password in clear text, and show the roster with the plain text password on the next page, for whatever ungodly reason, please add a note to come back later and lock your users down. Most MSPs keep the same password for ExchangeDefender and Exchange, and these services also affect ExchangeDefender Encryption, LiveArchive, WebFileShare, Compliance Archive, eDiscovery, FailPOP, mobile, etc and leave you open for collateral damage. Unless you’re using 2FA/OTP, restricting IP address ranges, rotating passwords frequently, I can guarantee that your passwords will be compromised. Please, please, please don’t do this, we are only making it available as the feature of last resort.
As we add these advanced security controls into ExchangeDefender Pro (and some even for Essentials) we will be tightening the security of the platform around. To hear more about our plan for 2019, please sign up for the webinar on February 6th at noon EST. Click the banner below to reserve your seat.
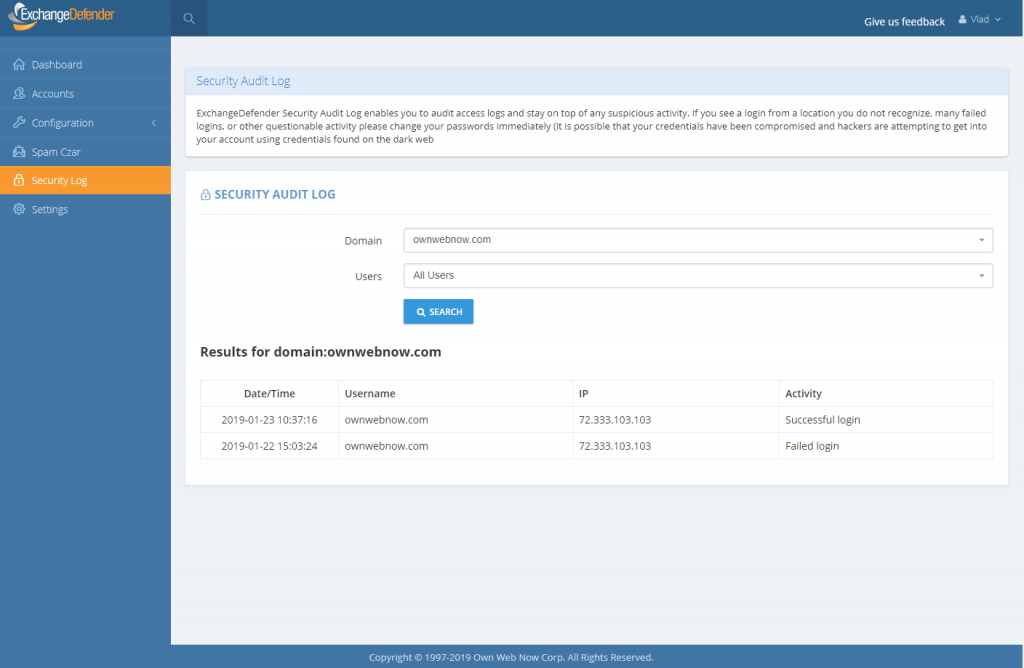
Introducing ExchangeDefender Security Audit Logs
ExchangeDefender launches New Security Logs
I have some great news – ExchangeDefender security logs are now available for all users of ExchangeDefender. This move is a part of our larger security ambition for 2019 to introduce Enterprise features of ExchangeDefender across our lower MSP, SMB and retail tiers in order to improve service security.
One of the biggest things in 2019 is the end of the era for plain text passwords. People love them, MSPs rely on them, they are super convenient for everyone including… the hackers that are looking to break in. But more on that in a minute.
The single simplest way to stay on top of account security… is identifying break-in attempts. ExchangeDefender Enterprise logs every event, login, escalation (and so, when you as the enterprise administrator or organization owner choose to automatically login as the user for support purposes) attempt.
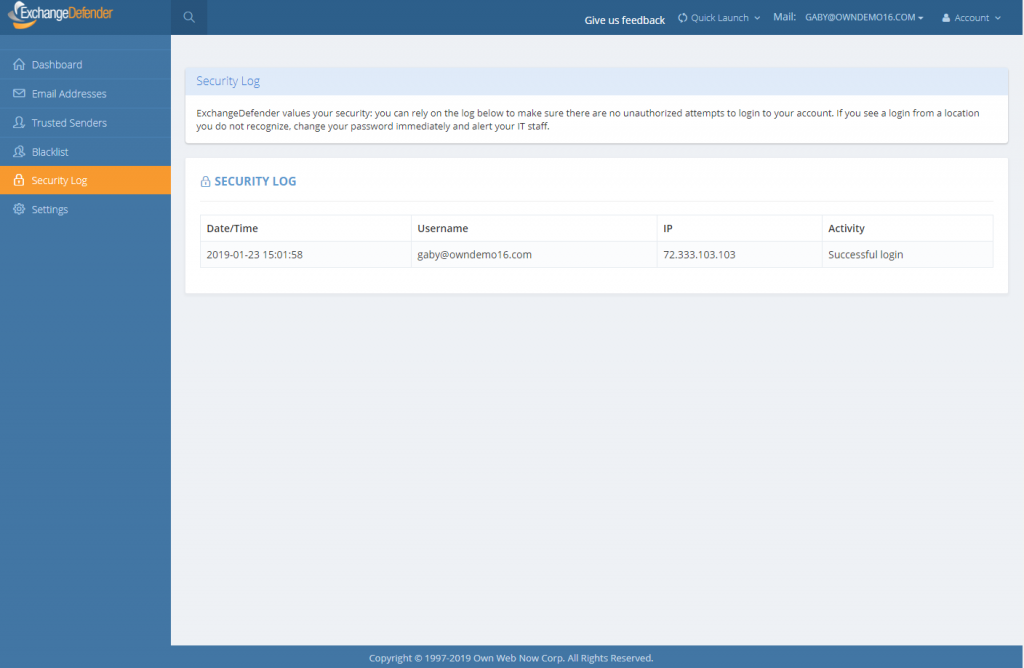
We’re happy to bring this feature in across both the service provider, domain and user login. Free of charge.
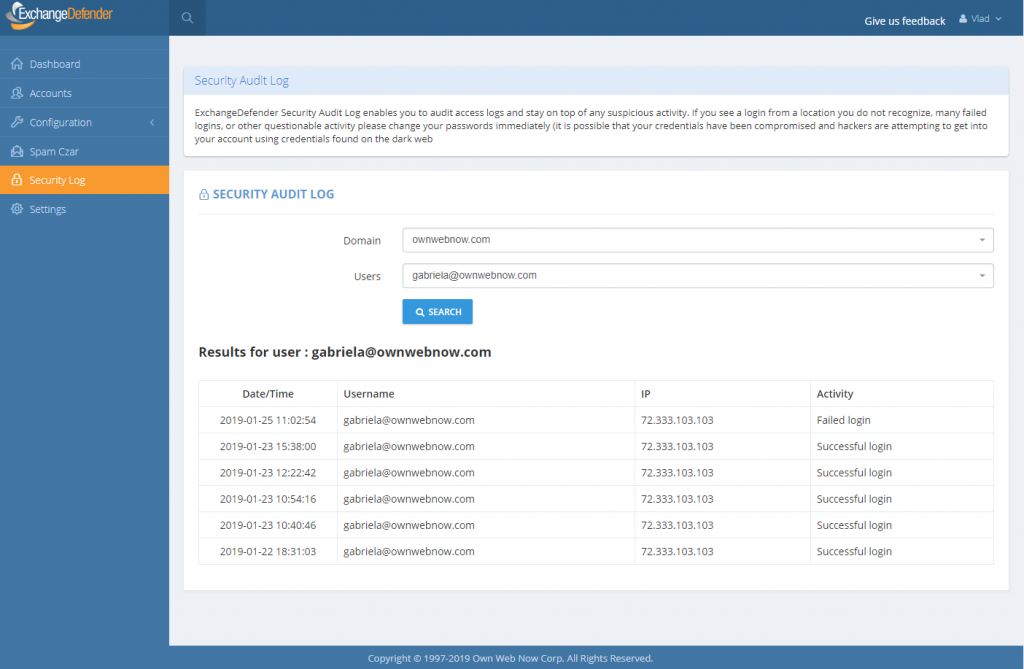
As the admin or service provider you also have the ability to search the account log for specific user or address that is causing problems. In the Enterprise version you have the ability to further lock things down based on IP, location, charset, and more. But if/when there is an issue, you can clearly see if the account has been compromised. At all other times, you can see login failures that are a good indication that there is a problem.
This feature, and a whole lot more, is coming down to the ExchangeDefender SMB land. While all these features were a premium in the past, the extent to which everything from your PC and the network devices that surround you are susceptible to compromise – we have to treat these features as what they are – essential to your security. As a matter of fact, we’ll be discussing this next Wednesday in our webinar:
When:
Noon, Wednesday, February 6th
Where:
https://attendee.gotowebinar.com/register/4562047862967330307
Hope to see you there.
Sincerely,
Vlad Mazek
CEO
ExchangeDefender
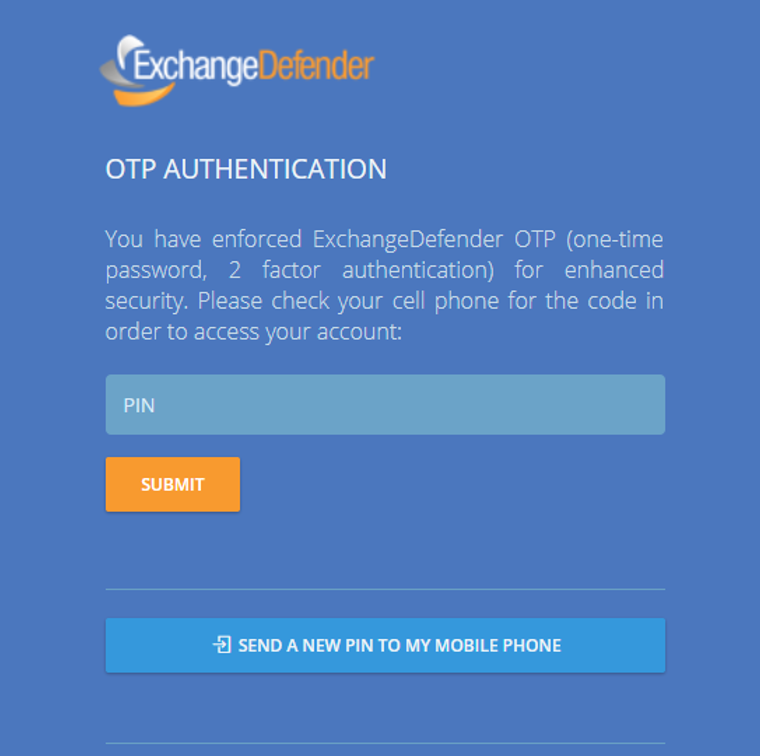
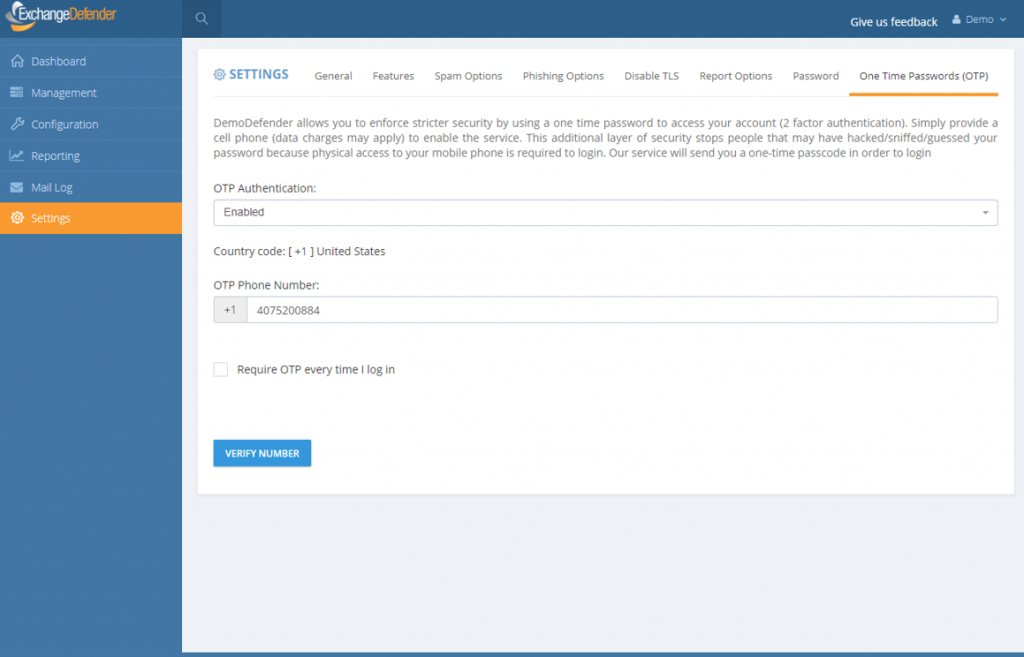
ExchangeDefender launches 2 Factor Auth / OTP Service
Introducing ExchangeDefender 2 Factor Authentication / One Time Password Service
ExchangeDefender Pro is proud to announce the launch of a free 2 factor authentication / one time password service that will help our users better protect their ExchangeDefender accounts. Most people use the same password everywhere and if your password is compromised anyone can login from anywhere – what 2FA/OTP service enables you to do is use your cell phone as a secondary ID check.
When you login to ExchangeDefender, the system will immediately text you a 4 digit PIN to your cell phone. This way even if someone were to guess or steal your password, they will not be able to login without having access to your cell phone as well.
As we blogged about implementing advanced password security, plain text passwords are a thing of the past and the whole universe is moving towards having that additional layer of security to make sure unauthorized changes aren’t being made.
This is why we are making ExchangeDefender 2FA/OTP free for ExchangeDefender Pro and it works at all three levels – Service Provider, Domain administrator (domain.com login) and individual end user accounts at https://admin.exchangedefender.com. Once you’ve authenticated with a PIN on the top level you will not need to re-authenticate in order to manage and support your MSP clients or the end users so by all means enable it for everyone.
We hope you enjoy this feature and start relying on it, don’t worry this is no bait and switch, we do not intend to start charging for it down the road – it’s all about improving security and keeping our clients protected. It’s just what we do!
Dealing with Newsletter and Subscription bombs
Dealing with Newsletter and Subscription bombs
ExchangeDefender now protects you from malicious subscriptions to newsletters and emails you never opted into through “Subscription (Newsletter) Bomb Protection” available at admin.exchangedefender.com. By enabling the feature all newsletter “CAN-SPAM” “legitimate sender” content that you don’t want in your mailbox will automatically be filtered out as SureSPAM by ExchangeDefender.
The Bomb Issue
Hackers are currently exploiting security issues in newsletter software that allows them to add your email address to a mailing list without validation. If you’ve signed up for anything recently you know that you’re generally sent a confirmation email to validate you own the email address — well, hackers have found a way to add your email to the list without that step. Repeated thousands of times, it gives hackers a way to blow up your mailbox through a broadcast storm by otherwise legitimate senders who cannot tell your email address from thousands of others on their mailing list.
The ExchangeDefender Solution
ExchangeDefender already has a built-in newsletter management software (where you can have all of your newsletters skip your inbox and be available for reading online). We can effectively quarantine all the newsletters for you and allow you to read them online without them hitting your inbox and putting you over the quota. With the Subscription Bomb protection we go an extra step and outright classify these newsletters you haven’t subscribed to as SureSPAM. You can still access them but they won’t bother you or damage your Inbox or productivity.
There are 3 options:
Enabled: Protection is turned on and any newsletter will be flagged as SureSPAM. We do not recommend this option as it will catch all newsletters, whether you’ve subscribed to them or not.
Disabled: No protection. This is the default setting at the moment for all domains.
Whitelisted: Protection from newsletters but whitelisted ones will still get through. This allows you to have the best of both worlds: protection from newsletters you didn’t subscribe to but newsletters you want and have whitelisted will still come through. On January 1, 2019 this will be the default setting.
What do I tell my clients?
ExchangeDefender can now protect you from SPAM being generated by legitimate newsletter and subscription providers – if someone steals your identity (your email address, name, etc) they can subscribe you to newsletters without your knowledge or permission. Because the sending and management of these lists is automated, hackers can get an innocent third party to send you thousands of newsletters to clog up your inbox, make you wait for your email to download, and just make your email experience miserable.
ExchangeDefender can detect newsletters and “legitimate marketing emails” with unsubscribe or newsletter control keywords and automatically filter it out from you. Messages aren’t gone, you can still access them through admin.exchangedefender.com in realtime and on demand, but your Inbox will stay clean.
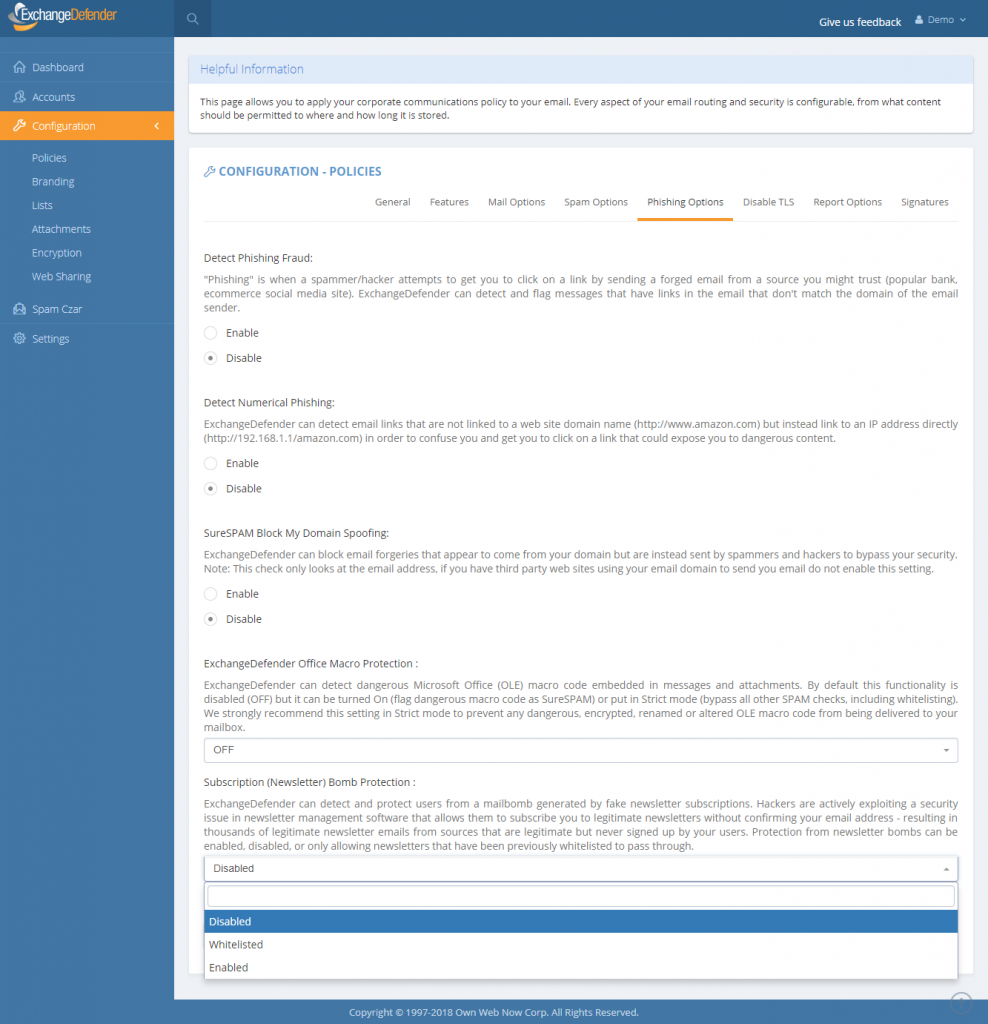
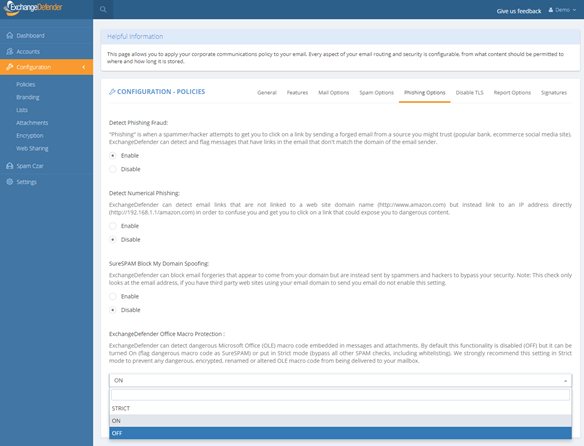
ExchangeDefender Office Macro (OLE) Dangerous Content Filtering
ExchangeDefender Office Macro (OLE) Dangerous Content Filtering
ExchangeDefender now includes advanced protection from dangerous Microsoft Office macro code (OLE). Since usage of Office macro code is very limited (and seldom moved via email) it’s almost universally used as an attack vector by hackers who send malicious macro code embedded in Microsoft Office documents that target vulnerabilities in Outlook, Word, Excel, Powerpoint, and more.
Specifically, our service scans the following attachments for the presence of dangerous, encrypted, malformed, malicious, or suspicious code: doc,dot,pot,ppa,pps,ppt,sldm,xl,xla,xls,xlt,xslb,docm,dotm,ppam,potm,ppst,ppsm,pptm,sldm,xlm,xlam,xlsb,xlsm, and xltm. If we detect something suspicious or dangerous the message will not be destroyed or quarantined (as is the case with virus or infected attachments) – rather we just filter it to SureSPAM.
Managing Your OLE Protection
We will start strictly enforcing macro protection on January 1, 2019. However, the feature is available now and can be enabled at any time by going to https://admin.exchangedefender.com and logging in as a domain administrator (if you don’t see the setting, you aren’t logging in with your domain account but your personal or service provider account).
Click on Configuration > Policies > Phishing Options.
At the bottom of the form you will see “ExchangeDefender Office Macro Protection” section that is currently (October 2018) set to Off. The following options are available:
Off – Turns off ExchangeDefender Office Macro (OLE) protection
On – Turns on the protection but whitelisting the domain/email will bypass it
Strict – Turns on the protection and ignores whitelists
ExchangeDefender recommends this setting be configured as Strict in order to protect from spoofing where clients own domain or vendor (that doesn’t have SPF/DKIM implemented) address is used to deliver a dangerous attachment. Using “Strict” setting bypasses whitelist checks so if the message contains dangerous content it will automatically go into SureSPAM even if the domain is whitelisted.
What do I tell the users?
First, set the setting to Strict. Then, adjust the date in the message below and make sure SureSPAM settings are set to Quarantine.
“Starting with January 1, 2019, ExchangeDefender will protect you from dangerous attachments that contain rarely used Microsoft Office macro (OLE) code. If dangerous macro code is detected in an attachment, message will go into SureSPAM category and if configured to quarantine the message will be accessible at https://admin.exchangedefender.com in the SureSPAM quarantine. We have enabled the protection for you. If you ever see a familiar contact/domain but you were not expecting the message, it’s likely being spoofed/forged in order to trick you to click on a dangerous attachment. Take an extra step and contact the sender asking them if they sent you a document. If not, delete the message.”
We hope this helps keep your users more secure and in our production use so far it’s helping stop 100% of dangerous content