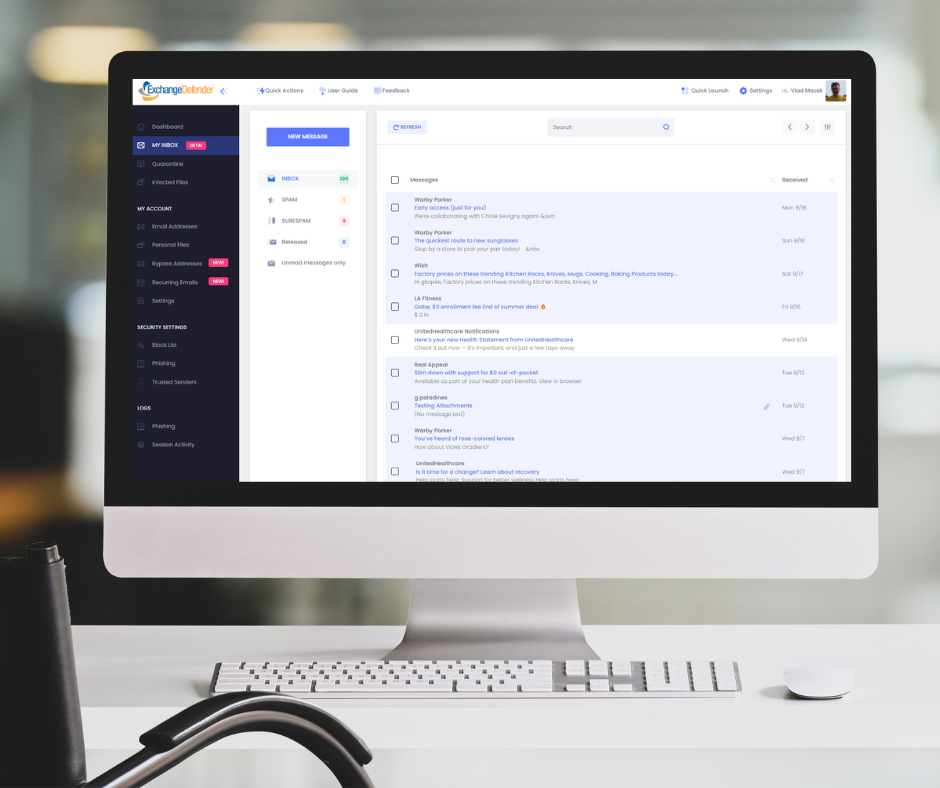
Introducing ExchangeDefender Inbox
Cybersecurity tops the list of IT concerns and spending, with email still being the most popular service with users and hackers alike: over 90% of compromises start with an email. If that sounds familiar you’ve undoubtedly had to deal with new email authorization standards, user training, troubleshooting mail flow, trying to figure out why email to or from certain people is bouncing, reconciling it all with new IT trends, cyber-insurance requirements, marketing. In a nutshell, email security is still a challenge and users just want something that works.
We’ve reimagined what the email security should look like in 2022 and we cannot wait to show it off:
ExchangeDefender Inbox Webinar
Wed, Sep 28, Noon EST
https://attendee.gotowebinar.com/register/1111619875721771023
We hope you can join us for the webinar and see just how we’ve integrated all the ExchangeDefender security and productivity services to give users a single panel of glass to make email work for them even when they have issues with email. Can’t wait till next Wednesday? Shoot us a ticket at support.exchangedefender.com and ask us to enable it for you today!
ExchangeDefender Inbox combines over two decades of email security experience with the modern, mobile-first world of countless email issues. It enables our clients to get things done with email security and work through all the issues without involving IT. Users want a quick and reliable email platform that just works – work around SPAM filters, around SPF/DKIM policies, around bounces – all while leveraging email encryption to protect sensitive data. The service has been enormously popular with our enterprise clients and now we’re bringing it to all ExchangeDefender users – see you next Wednesday!
Data leaks in healthcare is the reason why millions are stolen, no security is the culprit

Most medical offices are prime targets for cybercriminals because they have little, or no security. In fact, in 2020 and 2021, 50 million people were affected by a data breach coming from their doctor’s office or other medical services. Orlando-based Cybersecurity company, 365 Defender wants to help the healthcare industry protect their patient’s data, and safeguard their businesses from online attacks.
“Phishing has become a major threat in every industry. The hardest hit has been healthcare, with about 88% of its workers having opened phishing emails on the job. To be fair, just because they opened it, doesn’t mean they fell prey to the attack. Still, having protection against today’s biggest threats are crucial for survival.” — 365 Defender CEO, Vlad Mazek
Service offerings range from email security for Outlook and Gmail, to email encryption software that can send secure messages to emails, urls, and text messages. The monthly fees are budget friendly with the cheapest service being just $5 per user, per month. There is no yearly contract commitment, giving medical offices complete flexibility to satisfy their ever-changing IT needs.
The need for data security is critical, and protecting patient privacy should be a top priority second only to healing them. To learn more about 365 Defender, and how to get started securing your company, please visit our website www.365defender.com. There is currently a 14-day free trial offer for any 365 Defender service.
—
365 Defender is owned and powered by cybersecurity leader, ExchangeDefender. ExchangeDefender specializes in providing email and data security to enterprise since 1997. Headquartered in Orlando, Florida – the IT firm has just launched service plans for small business in hopes of keeping companies safe regardless of their size and budget.
Limited support for misconfigured services

ExchangeDefender provides technical support and assistance only for the domains that have been properly configured according to our deployment guides (see https://www.exchangedefender.com/docs).
To make sure your domain is properly configured please check https://check.exchangedefender.com
When the required DNS records and inbound/outbound mail isn’t configured correctly our internal troubleshooting tools fail and staff has no way to replicate or diagnose further issues — they are prohibited from guessing or offering informal suggestions as that can cause even bigger issues and cause a liability issue for everyone involved. You’ll get the same answer in the support portal, in the support web chat, and on the phone.
But Vlad!!! What if the client can’t/won’t change their DNS or deploy the service correctly?
I can respect that there is always a business case requirement for doing things the wrong way, and I’ve had plenty of arguments with clients that don’t know how ExchangeDefender relies on all these systems to deliver the best possible protection and functionality. I understand. It might even work!
Just please don’t ask us for help with it when it doesn’t work. Our staff is prohibited from guessing and making the problem even worse. It’s not a BOFH issue, it’s a legal liability issue.
-Vlad
Looking for beta testers: “Project Inbox”
We would like to invite our clients, partners, and enterprise users to a closed beta of Project: Inbox – an affordable email solution that can be used as a standalone solution or in hybrid mode with M365 and G Suite.
If you are interested, please email client.services@exchangedefender.com along with a domain name you will be using for the beta test.
Our CEO recently held a webinar explaining the strategy behind this new service and it has been evolving ever since based on market feedback. Simply put, there is a huge market for affordable mailboxes that still meet the high end security and business requirements like top of the line email security, SSO, IMAP/Outlook/Mobile access, and still use the same domain name as the more expensive Exchange or Gmail office suites.
For an overwhelming majority of users within larger organizations, email is an absolute necessity but the average cost of $150/year/employee is putting a strain on IT budgets. Furthermore, the projected slowdown in the economy will make our clients more cautious about their IT spending. Our models show a trend of more users being mobile-first (with remote work being mobile-only) and a growth of service-related mailboxes is creating an opportunity to help us improve our clients security while reducing their service bill.
If this sounds like a winning opportunity for your business or your clients we hope you’ll join us in building something new and awesome. Those that help us out will enjoy the service for free for a while but we have a limited number of spots depending on industry and seat count so if you’re even remotely interested please email us as soon as possible.
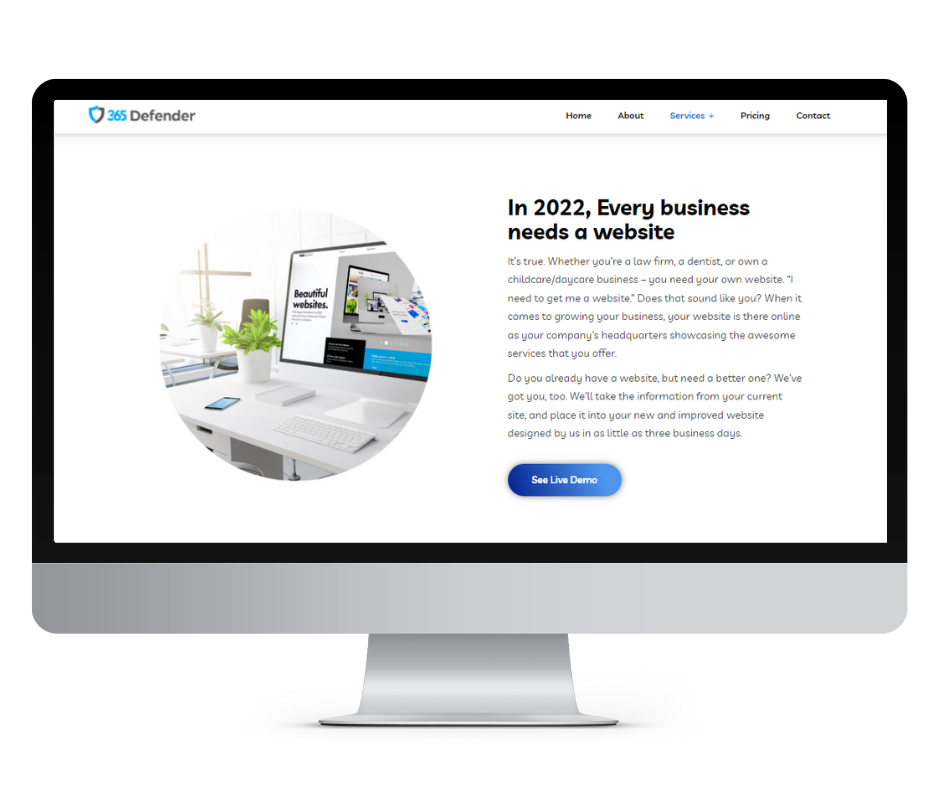
Turnkey professional websites starting at $199
In 2022, every business needs a website.
It’s true. Whether you’re a law firm, a dentist, or own a childcare/daycare business – you need your own website. “I need to get me a website.” Does that sound like you? When it comes to growing your business, your website is there online as your company’s headquarters showcasing the awesome services that you offer.
Do you already have a website, but need a better one? We’ve got you, too. We’ll take the information from your current site, and place it into your new and improved website designed by us in as little as five business days.
The process is simple, here’s how it works:
First, you choose a design package. We offer two types of custom website packages, starting at $199 that includes hosting and support.
Next, tell us more about your business. Answer a few questions about your business, send us your logos, and pictures, and we’ll use it to customize your website. Already have a website but need an update? We’ve got you. We’ll take all the information from your existing website to the new one.
Finally, we’ll get to work on your custom website. We create most websites in just three business days. Once you place your order, we’ll start right away.
Your own professional website, stress-free
Outsource your website design so that you don’t have to worry about whether the colors complement each other, or if the contact form works properly. Looking for website design for your law firm? We’ve got you. Need a professional website for your medical business? Look no further, we have the design experience to make your business stand out!
We know that often the best website design creates extremely high costs that are not small business friendly. 365 Defender is able to keep costs affordable by creating popular templates that can be customized, instead of starting completely from scratch. Ultimately, what you can expect from us is a secure, professional website that is fully managed and supported for you.
Get your own custom website today! Explore our website design packages, click here.
Healthcare: Most popular cybersecurity services in 2022
Better patient care begins with secure, timely, and precise collaboration and communication.
Securing medical companies in 2022 will be crucial for their overall business success. Healthcare is unique as it manages large volumes of sensitive material. Its big data is considered as good as gold to hackers as it contains private information (PHI) about patients like date of birth, social security, home addresses, medical records, and so much more. The nature of the information that the healthcare industry collects, is subject to some of the strictest data privacy and compliance regulations in the United States. However, the lack of security is evident across the medical sector. Approximately 85% of healthcare businesses have suffered some type of security breach in the past two years.
As an industry-leading cybersecurity provider, we highly suggest the following IT services to secure healthcare businesses in 2022.
Email Security (ExchangeDefender PRO)
For just $5 per user per month, our email security suite will secure Outlook or Gmail for business. About 90% of all malware and ransomware attackers in 2020 were delivered by email. Our multi-layer security suite, ExchangeDefender PRO protects company email against SPAM, viruses, malware, ransomware, spoofing, phishing attacks, and more.
Secure my email
Email Archiving and Compliance
Due to the ever-changing, high volume of sensitive information the industry manages, it is crucial that all business communications are saved properly. Our Email Archiving solution stores every single email that is sent and received into the organization. It offers 100% archiving of all inbound, outbound, and internal email for regulatory compliance. It also includes fast eDiscovery search and compliance manager controls.
Start Archiving
Email Encryption
A whopping 70% of healthcare businesses believe that they are at risk of a data breach. ExchangeDefender Email Encryption enables you to send and receive encrypted messages by email, url, or text message. It is easy to use, can auto-detect sensitive data, and offers real time reporting.
Web File Sharing
Our Web File Sharing enables secure collaboration of files and documents of any size from anywhere. Security at its core, WFS protects sensitive information while increasing productivity, getting things done fast. Our user-friendly platform offers a simple, secure way to share files internally and externally.
Interested in securing your medical office? Try a free trial for 30 days! Simply follow us on facebook, and send us a message to get started.
BETA: Advanced Features in Admin Portal
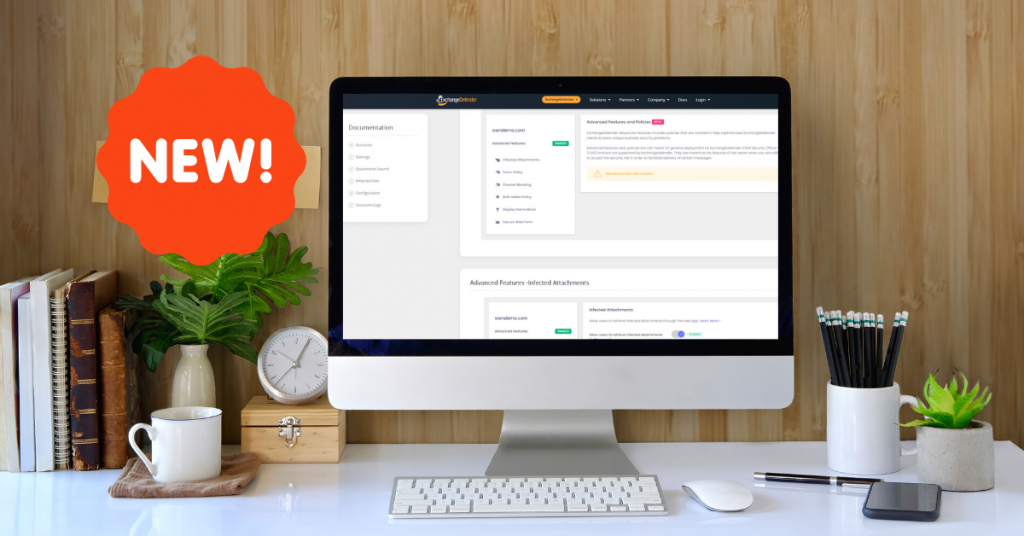
We’re moving things around a little to make the platform easier to use and to expose more of the ExchangeDefender security settings. The threats are only getting worse and we need to be more flexible in order to protect you.
Over the next few blog posts we will be introducing you to a more polished ExchangeDefender look as we consider user feedback and change around the overall user experience. It’s no secret that we’ve been making ExchangeDefender friendlier and friendlier and I can’t wait to reveal why… soon.
In the meantime, allow me to introduce you to the ExchangeDefender Advanced Settings. These settings are controlled under the Domain Administrator section of https://admin.exchangedefender.com:
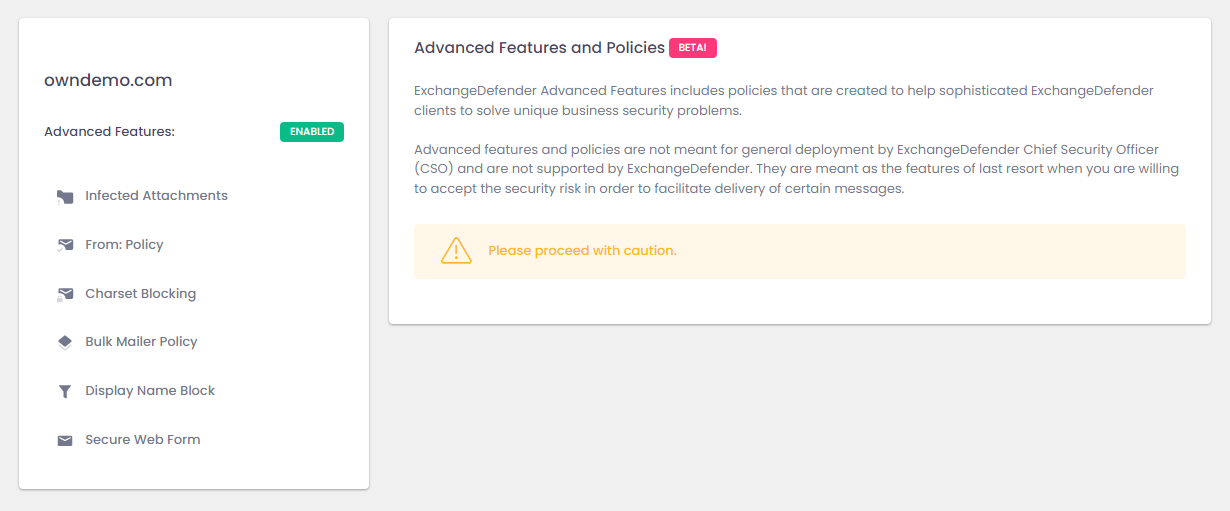
ExchangeDefender helps bridge the need for security and productivity: If the security tool is too convoluted, takes too many clicks, features lots of paragraphs instead of intuitive controls — it’s simple to see why casual users get their security compromised and experience nothing but frustration just trying to get to their email.
We’re changing all that and look forward to introducing you to the new ExchangeDefender shortly.
oAuth Launch Scheduled for May 19th, 2022
In January 2021 we launched *our oAuth implementation* to help clients get rid of passwords. On May 19th, 2022 our legacy systems (existing email/txt 2FA/MFA) will be shut down and all ExchangeDefender services will rely on oAuth for authentication. Clients will not see a major difference and will login the same way they always have at https://admin.exchangedefender.com:
The new authorization backend will help improve the security of all users that rely on ExchangeDefender to keep them safe: better password policies, no need to reauthenticate every time you visit our services, support for hardware authentication devices and tokens, support for software authentication such as Google/Microsoft/Authy authenticator solutions, and a lot more.
The era where someone can get access to all your data just by guessing or hacking your password is coming to an end. More importantly, industry standards and cybersecurity insurance underwriters are requiring 2FA/MFA and this is a huge opportunity for our partners to deploy a more secure access to the arguably most insecure and public endpoint in every organization: email.
We look forward to keeping all your data secure and your users safe from dangerous email exploits.
WEBINAR RECAP: Earn cash rewards, new phishing filter design, and more!
Our latest webinar live session of 2022 just happened a few days ago, and we had so much to share with our partners. Topics covered included our newly launched sister company, 365 Defender, our new referral program that earns you cash rewards, and so much more. Today, we want to share with you the replay of the webinar featuring just the main highlights. You can always watch the replay video anytime by clicking here.

365 Defender – providing affordable cybersecurity services directly to small businesses
ExchangeDefender’s overall strategy for 2022, as we recover from the covid-19 global pandemic, is to focus on enhancing our current cybersecurity services and software. There has been a huge shift in the IT workforce, and IT needs for the common small business which is why we launched 365 Defender. 365 Defender enables small businesses with no IT the ability to access affordable cybersecurity services. Why did we do this? The market demand was overwhelming, especially while we were all working from home. We started getting requests directly from businesses who were in dire need of security. Further, IT and MSP providers providers are specializing in more profitable areas leaving an under-served SMB space.
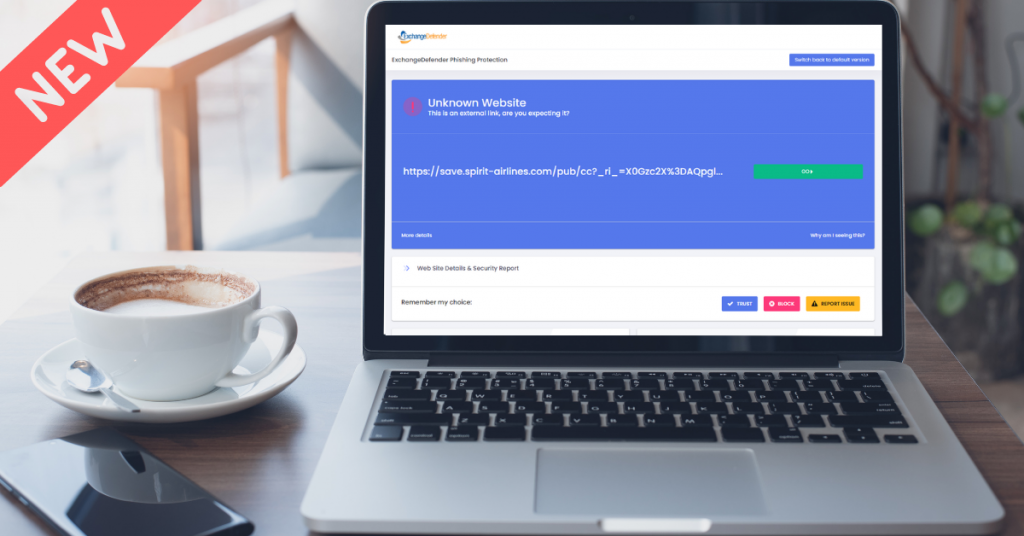
New Phishing Firewall user experience
ExchangeDefender Phishing Firewall has received a major face lift. We’re making it easier to control where your users go when they aren’t paying attention. The new UI enables direct access to malware scans and site security reports. It also features an improved mobile interface with the ability for logging and auditing. Soon, the firewall will also feature phishing and security user training. The new firewall is automatic, and does not require any actions by the user.
In 2022, every business needs a (good) website
We just launched brand new custom website design packages for an affordable price. Currently there are two options: a full one pager website, and a premium three-page responsive website. Pricing begins at just $199, and as a launch promo we are offering our clients the ability to spread the payments over three easy monthly payments. Why did we start offering this service? In a recent survey, tons of partners expressed their website and maintenance frustrations. We knew that we could create a package that includes the website, hosting, and maintenance.
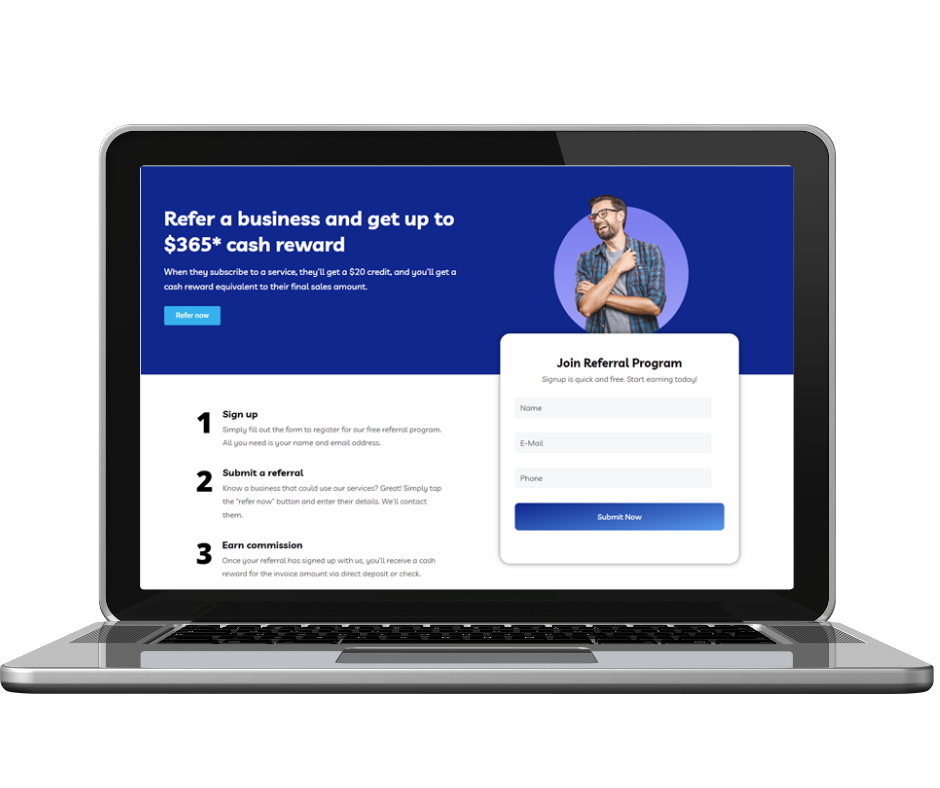
365 Defender Referral Program
Say hello to less work, and more commission with our new 365 Defender Referral Program. Earn up to $365 commission for every referral that becomes a client. When they subscribe to a service, they’ll get a $20 credit, and you’ll get a cash reward equivalent to their final sales amount. The process is simple – sign up for free, submit a company referral, and earn cash.
Introducing ExchangeDefender Phishing Firewall Beta (SEE PICS)
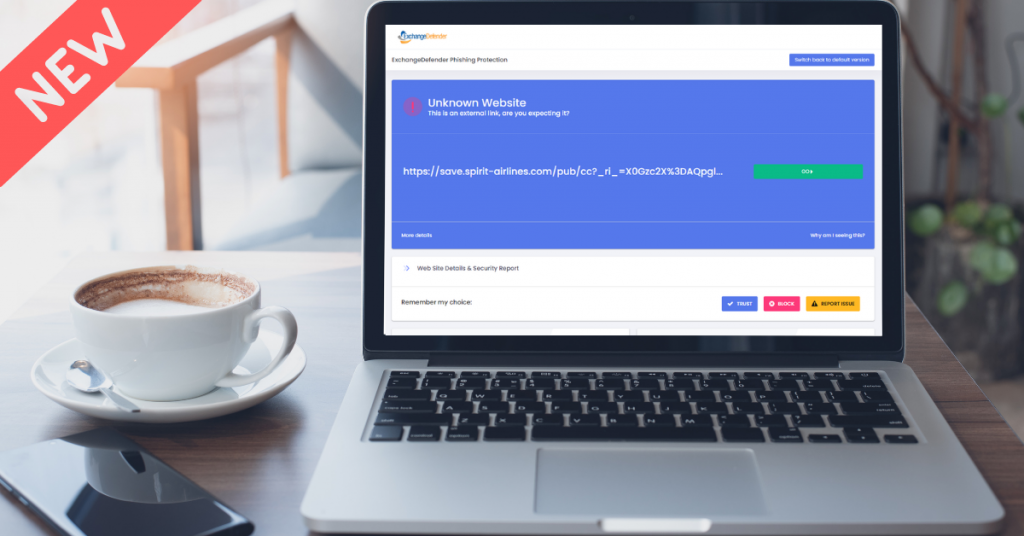
As you may have noticed, we have been focusing on the end user experience a lot more. Over the past few years our service and phishing protection have gone from being an IT tool to a cybersecurity service users interact with on a daily basis. For more details and to find out about all the new features we’re delivering this spring please tune into our webinar:

New Phishing Firewall
As we roll out these changes we’re actively seeking user input and feedback on the changes. We’re also offering a live version of the next stuff that you can test drive. Here is our current ExchangeDefender Phishing Firewall screen:
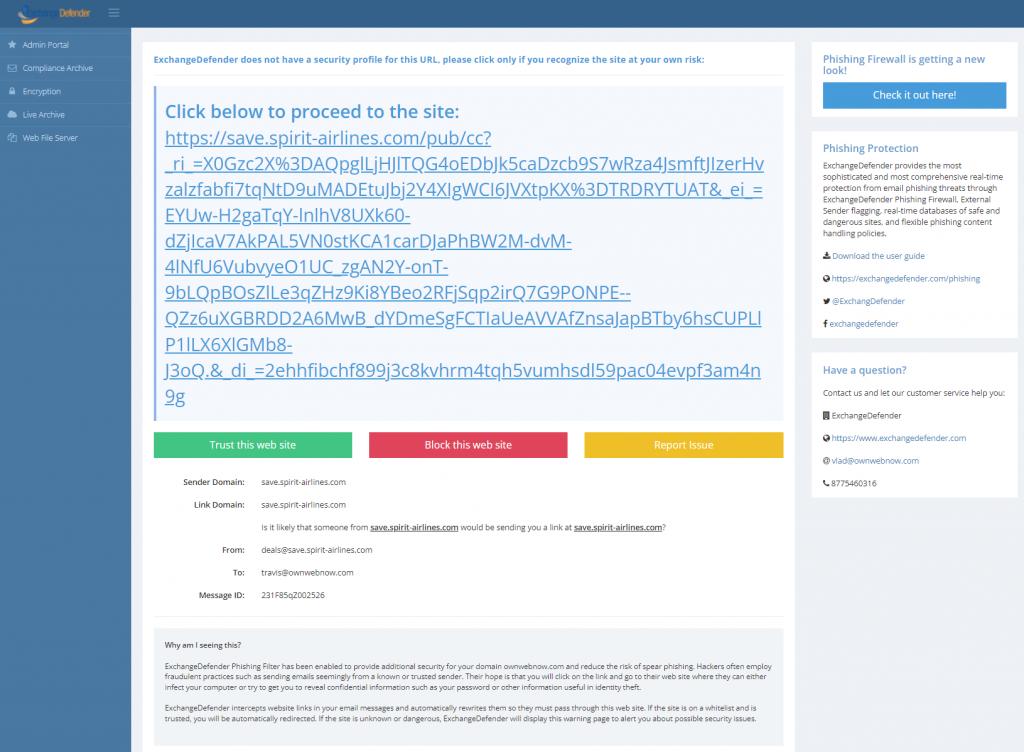
So much has changed since we launched this service years ago and we now have tons of UX data and client feedback that we can use to make the ExchangeDefender Phishing Firewall better for everyone.
Next time you’re on the Phishing Firewall look in the upper left under “Phishing Firewall is getting a new look! Check it out here!”. Clicking on that button will default the firewall to the new version every time you visit (you can roll back as well).
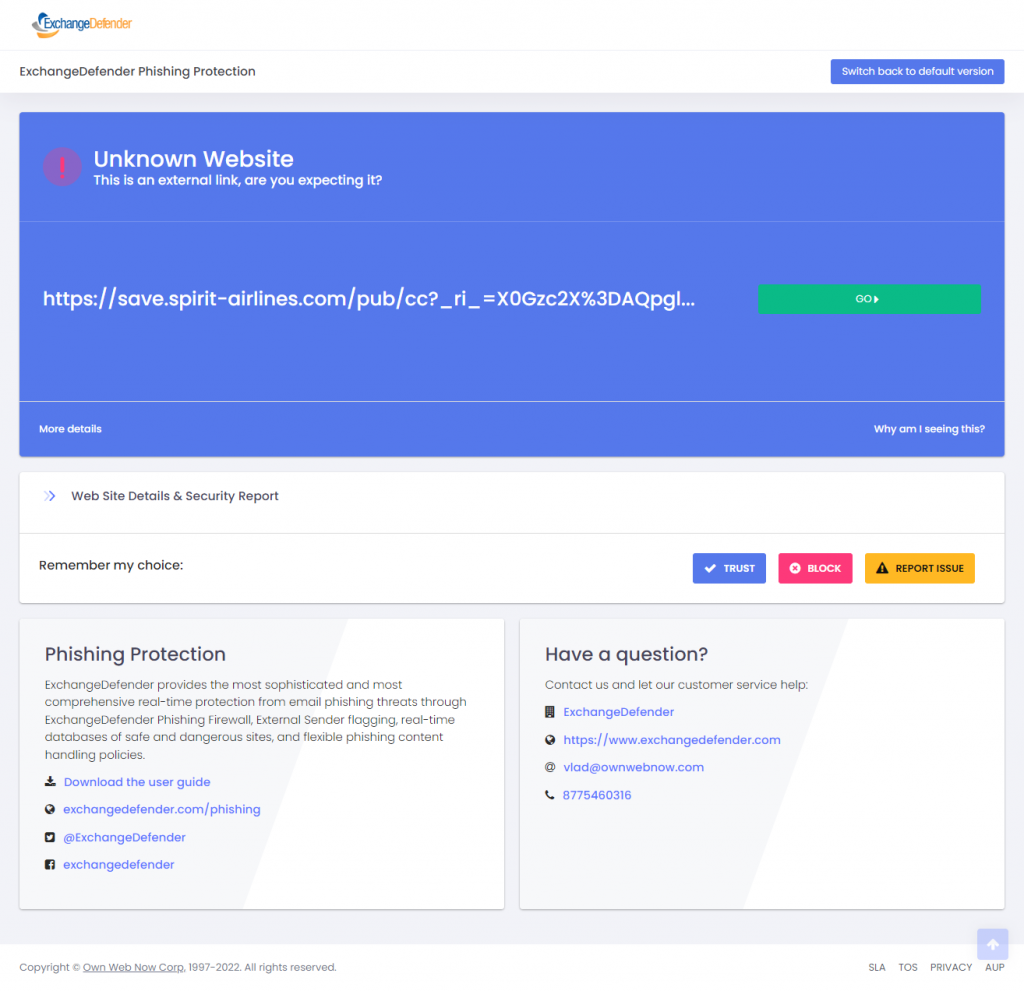
What’s new?
We’ve cleared the clutter and made it very obvious where to click in order to proceed. For the longest time our users didn’t know they could click on the link to proceed :emoji for shrugs:
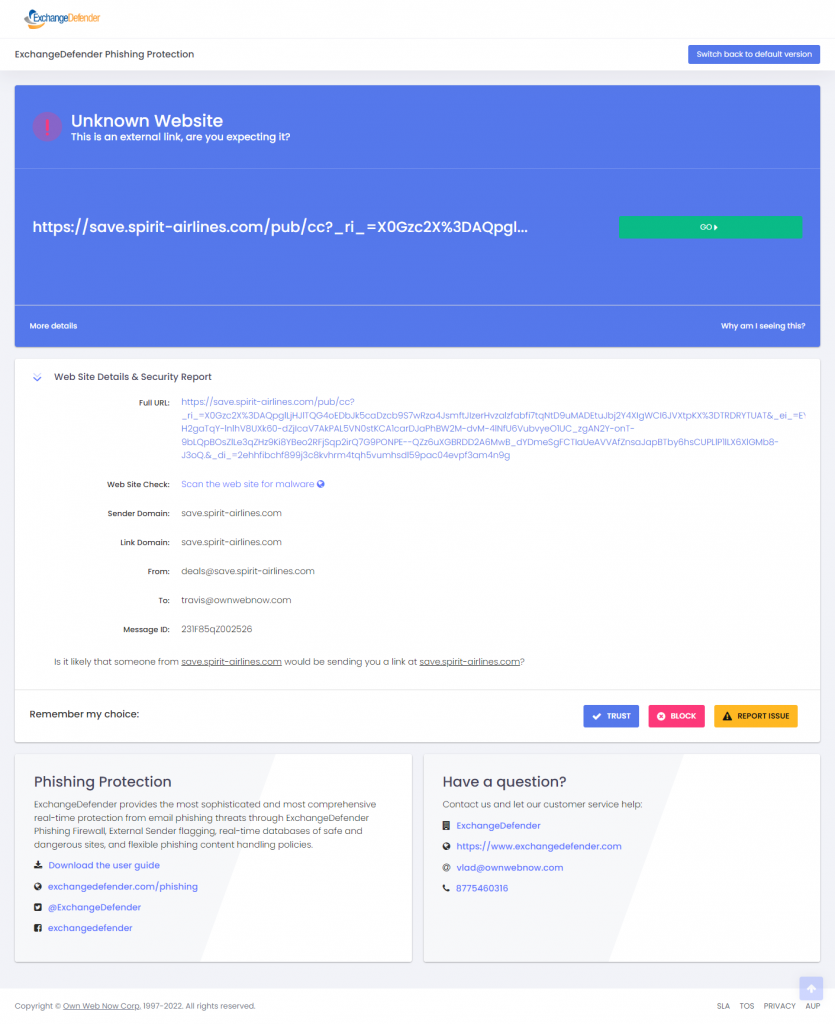
From there we’ve enhanced the process that keeps the user secure. These features require the user to authenticate and all their repeat visits will feature the ability to apply org policies (for safe sites, thus bypassing the screen), manage personal settings and alert the user to potential danger ahead.
We’ve also integrated open security services that can scan any link on demand and identify the site reputation and possible malware content. Our enterprise clients also enjoy the ability to sandbox/proxy link content and to preview the web site without actually clicking it and opening it in the browser. Of course the ability to slipstream your brand and your support into the process is available to enterprise customers as well.
Let us know what you think! We’re looking for all the feedback we can get.