Introducing 365 Defender Referral Program
ExchangeDefender recently launched affordable cybersecurity service plans for small businesses, learn more. The pandemic showed us a lot of security and technical vulnerabilities that our third-party clients were experiencing. This is why we created service plans that would benefit businesses directly. We love our partners, and our partner program and have no plans to change it. 365 Defender is our solution to those businesses that can’t afford an MSP, or are only looking for specific services.
At ExchangeDefender, it makes us really happy after hearing that a client has referred us on to someone else. In fact, it makes us so happy that we decided to reward those who are helping spread the word about our services.
How the Referral Program works
We made sure to make things as easy as possible. First, you identify a possible referral. Second, the referral goes online to signup for 365 Defender services. Third, you get paid commission for the sales amount. It is that simple!
How to get started
First, you’ll want to join our referral program. To submit a referral, simply enter a support ticket (as an inquiry is fine too) with the prospective sales information. We will contact the lead you provided us, and when a subscription is confirmed, we will provide you a one-time commission fee equal to the sales amount.
Ideas on where to gossip about us
- Your website / blog
- Reddit profile
- In your email signature
Some ideas on what to say
- Looking for a powerful anti-spam software that is budget-friendly? You’ll want to check out 365 Defender.
Message us to get a free trial code!
- Don’t have a budget for an MSP but need security services? Try 365 Defender. Message me to get a
7-day free trial code!
What is Phishing? (a simple explanation)

According to recent reports from the FBI, Phishing has become the most common form of cyber attack in 2020 and 2021. Phishing is a method that hackers use to steal your sensitive information like usernames or passwords. It is most often used for identity theft, where cybercriminals send a phishing campaign (via email) to gain access to your bank accounts, personal information, and more.
The goal of a Phishing attack is to: gain credentials like bank pin numbers, usernames and passwords, gain personal data like your name, home address, and email, and also medical PHI information like treatment information and insurance claims.
Where does Phishing happen?
Approximately 96% of phishing attacks are delivered by email. In 2020, it was estimated that 1 in every 4,200 emails was a phishing email according to a Symantec report. To put the numbers in perspective, for ever 1 second of internet activity, 3.4 million emails are sent.
There are also fake websites, social media accounts, and phone calls that are used by criminals to try to steal lucrative information. Beware of these websites, always check for the lock sign in your URL, and make sure that the spelling is correct.
What does Phishing look like?
Inside of a Phishing email you’ll find a malicious link, that (when clicked) will transfer you to a fake website that will request your credentials in the form of “logging in”. Most phishing emails, when you look at the subject lines, you’ll find that the following keywords are present, like:
- Urgent
- Request
- Important
- Payment
- Attention
The email would appear to be from a brand that you trust, like Amazon, Microsoft, or Facebook. The email “from” address is not actually from the brand, but rather faked to appear like it is.
What happens when a Phishing attack has been successful?
2020 Phishing statistics show that about 90% of users cannot identify a sophisticated phishing email. It’s not because we’re dumb, its because the attacks are executed so well. It is becoming increasingly difficult for companies to secure their data because office workers are human, and humans make mistakes. After a successful phishing attack, about 60% of organizations lose their data, 50% are infected with ransomware and get their credentials or accounts stolen.
Need Phishing protection for your business? Keep your company and data safe with ExchangeDefender PRO!
Interested in learning more about Phishing protection, click here.
Orlando’s #1 Cybersecurity provider launches small business plans

Orlando, Florida – Smaller businesses can now secure their employees, email, and data for less than $5 a day. Orlando’s top cybersecurity provider, ExchangeDefender has just launched affordable cybersecurity services for small business via its sister company – 365 Defender. Dubbed the “original email experts”, 365 Defender protects businesses against data leaks and email threats like SPAM, phishing, spoofing, malware, and much more!
9 out of every 10 cyber-attacks start with just a simple email. Over half of all U.S businesses lack proper security, making them an easy target for cyber-attacks. 365 Defender is designed to offer SMBs the ability to protect themselves without having a hefty IT budget.
“We are a small business ourselves. We know that most SMBs don’t have a big budget for IT, or cybersecurity. This is why we leveraged ExchangeDefender technologies and expertise to create reasonable options via 365 Defender.”
– ExchangeDefender CEO, Vlad Mazek
Service offerings range from Email Security for Outlook and Gmail, to Encryption software that can send secure messages to emails, urls, and text messages. The monthly fees are small business friendly with the cheapest service being just $3 per user, per month. There is no yearly contract commitment, giving businesses complete flexibility to satisfy their ever-changing IT needs.
To learn more about 365 Defender, and to subscribe to a service plan, please visit our website www.365defender.com. Get a free 14-day trial for your business today!
365 Defender is owned and powered by cybersecurity leader, ExchangeDefender. ExchangeDefender specializes in providing email and data security to enterprise since 1997. Headquartered in Orlando, Florida – the IT firm has just launched service plans for small business in hopes of keeping companies safe regardless of their size and budget.
ExchangeDefender CEO talks email-borne threats with Cybernews
Recently, Cybernews reached out to ExchangeDefender CEO, Vlad Mazek to learn more about how we keep businesses safe from cyber-attacks using top of the line security solutions. The informative discussion centers around the topic of cybersecurity, and what that means for the modern business.
With the recent rise in phishing attacks, it is smart to double-check if it’s really your coworker that emailed you.
By now, it’s probably hard to find an Internet user who has never received emails from someone claiming to be a long-lost relative who wants to share their fortune. While the majority of us are familiar with this type of malware, phishing attacks shouldn’t be underestimated. Nowadays, when threat actors start to include more personal details, posing as coworkers or even bosses, staying vigilant is key.
To discuss the topic of cybersecurity and phishing prevention, we reached out to Vlad Mazek, the CEO of ExchangeDefender, a company eliminating email threats before they even reach your inbox.
ExchangeDefender has been providing various security solutions for more than 2 decades. What was your journey like throughout the years?
We originally started ExchangeDefender to improve the reliability of our Microsoft Exchange servers by offloading all the security tools to a more scalable infrastructure. Over the years we’ve expanded our security portfolio to protect other email servers, as well as deliver more secure ways to rely on common office tasks such as file sharing, collaboration, and compliance.
Can you tell us a little bit about what you do? What are the main problems you help solve?
We used to say “We kill SPAM for a living” and to this day we simply eliminate common threats that lead to security compromises and service outages by providing email encryption, long-term archiving & eDiscovery.
We make it easier to rely on email for secure and reliable communication; which we do by keeping potentially dangerous content away from your webmail, mailbox, desktop, or phone. Simply put, we make it easy to get things done more securely.
What technologies do you use to detect and stop threats in their tracks?
We primarily rely on our internal early warning system which tracks unusual activity from known threat actors. Because of our size and client base, we often have the luxury of being among the first to be targeted which helps us identify safe and unsafe developments before they go “viral”.
We also participate in many proprietary, open-source, and data/intel sharing projects that help raise the security profile of everyone involved.
How did the pandemic affect the cybersecurity landscape? Were there any new features added to your services?
Pandemic actually improved the security landscape for our clients because they suddenly had to shift to a remote work model which inherently came with more stringent security requirements and more awareness for security policies and secure collaboration.
We noticed a significant shift from traditional office communication methods to SMS/TXT and we moved quickly to make all of our services SMS-aware. Mobile phones have become a security identification token, a mobile presence device, and far too often a failover computer. That’s why we invested heavily in extending our services to meet our clients’ needs to go beyond just sending email messages.
What sectors (for example, financial, healthcare, etc.) do you think should put extra attention towards email security?
The best way to answer this question is to think like a hacker because for them it’s not personal, it’s business.
Organizations get compromised for one of two reasons:
- They have assets (data) that are valuable
- They have a reputation that is valuable
If you have a lot of valuable data or a trustworthy relationship with your clients, you’re a valuable target regardless of your industry. It would be difficult to hack a financial institution because they have dedicated IT and security teams, go through routine audits, and can respond to threats quickly. Compare that to a small CPA firm that uses standard tools and an antivirus bundle that came with their PC.
When it comes to cyber threats carried out via email, what are the most common ones?
Email is the most popular way to get cyber threats into an organization, according to a recent study over 90% of security compromises started with email and it has not changed significantly in the past few years: the #1 cyber threat is from spear phishing. Spear phishing is a practice of forging the identity of the sender and the look of the email to something the recipient would find trustworthy enough to click on. What has changed significantly is the end goal of spear phishing:
- Deployment of RAT (Remote Access Trojan) software
- Theft of PII (personally identifiable information)
- Theft of security credentials
This list actually flipped in the last two years mostly due to the sophistication of RAT software that can give an attacker access to the entire network instead of just a single PC or cloud account. The latest variants target UEFI bios which keep the threat in place even after you get rid of the infected hard drives. As these threats evolve, they also highlight other security issues on the network which makes them difficult to remove and require constant monitoring.
With so many teams working remotely nowadays, what are the best practices when it comes to secure file sharing?
The single most important recent advancement in overall IT security that really deserves wider adoption is the use of MFA/2FA/OTP: multi-factor authentication that requires secondary verification before accessing any sensitive system or information. Working remotely, outside of a managed network and access to IT staff, creates a new universe of security threats that should be mitigated by:
- Deploying & requiring MFA for access
- Deploying a more aggressive backup and imaging solution
- Controlling and reducing the attack surface (by limiting access only to required web sites & services)
Besides secure collaboration solutions, what other security measures do you think modern companies should invest in?
You are probably already spending too much on overlapping, redundant, and underutilized security solutions.
The best security investment you can make today is to get an audit of your existing security portfolio and its integration. Being secure doesn’t come simply from paying for a security software/service license – it has to be properly integrated, configured, and monitored in order to truly keep users away from dangerous content. Due to the chronic lack of security focus and the habit of deprioritizing security for the sake of end-user comfort, many organizations find themselves in a perilous situation with cyber insurance demands.
We are seeing organizations getting compromised not because they don’t have security solutions or adequate training but because they don’t take the time to properly and fully implement the security solutions they are already paying for. An overwhelming majority of ExchangeDefender subscribers rely on less than 30% of the security features they already pay for.
Can you give us a sneak peek into some of your future plans for ExchangeDefender?
Our biggest technical investment for 2022/2023 is to make it possible to access external content (email attachments, files, messages, sites & services) in a secure online sandbox environment where dangerous content wouldn’t even have a chance to reach the user’s desktop, phone, or network.
Our biggest investment is in the area of security audits and assessments. While there is always a shiny new tool or service that promises better security, our data indicates that it’s rarely the lack of a tool, and more often the lack of proper deployment and management of sensitive information that leads to a security compromise.
We’ve helped countless businesses that have been compromised over the years and it usually comes down to neglect of security processes combined with a lack of a plan to respond and recover from a hack. Our future plans are to help organizations change that scenario because cybersecurity isn’t something you buy, it’s something you do.
To celebrate the launch of our new small business service plans, we are currently offering 30-day free trials for any service. Interested in ExchangeDefender? Please visit www.exchangedefender.com/business to request your free trial today!
Stop Spam in Its Tracks: Why Unauthenticated and Unauthorized Emails Are Unwelcome

Every day hackers make email security on the Internet worse and every day more organizations adopt strict requirements for DMARC – DKIM and SPF records. Now that major mailers (like Gmail and Microsoft) are starting to automatically junk messages that fail authorization and authentication checks more IT teams are becoming familiar with the concept of deliverability and adhering to all the mailing rules so you end up in Inbox.
For the most part, this is a quick task an IT person can address by updating the DNS records and creating entries for SPF and DKIM. In simple terms, SPF controls which organizations can send messages for your domain and DKIM uses public-key cryptography to sign messages as they leave your email server. Both have the same goal: block third parties from spoofing/faking your domain and pretending to send messages as you.
Please adopt SPF and DKIM for your domain. Instructions on how to do that are at https://www.exchangedefender.com/docs/dmarc
Unintended casualty: Mail-enabled contacts
One of the favorite legacy email features was giving individuals an email address on your domain but not creating an entire mailbox. This way you can have a Bill@YourDomain.com but messages are automatically forwarded to BillG2051@yahoo.com.
That is no longer possible. While your organization will accept the message and attempt to forward it to the recipient’s actual email address, their server will see the message coming from your email organization and rejecting/junking it immediately. This is because the sender has published an SPF/DKIM record that authorizes only their servers to send messages, and you attempting to forward it looks like a forgery to the recipient’s mailbox. Most of the time the message bounces back to the sender or simply errors out.
4 cybersecurity stats that every lawyer should know

Cyber-attacks on the legal sector are on the rise. Legal practices are big targets for hackers due to their access to sensitive information, and severe lack of security.
Here are four statistics that ring alarm bells in the industry:
Number one: One in four law firms have experienced a security breach of some kind. Even more have had malware or viruses according to a 2019 American Bar Association survey.
Number two: Data breaches cost your local small practice an estimated average of $36,000 dollars. To put in perspective, a new legal assistant salary for the year would costs the firm about the same price. Also, at least 31% of their clients terminate their relationship with the firm afterwards.
Number three: 61% of ransomware victims in the legal sector were Law Firms in 2020. It is the highest of the legal profession, with Courts, and Legal Services coming in second.
Number four: 94% of malware and ransomware attacks were delivered by email in 2020. There are new malware and viruses being discovered every day.
The bottom line
Law firms pose a higher risk for data leaks due to their business nature of storing and sharing sensitive information. ExchangeDefender provides affordable email security, email archiving, and email continuity solutions to the legal industry. One of our largest client bases, the legal industry relies on ExchangeDefender to mitigate risks of cyber and email attacks.
Secure your law firm, explore our small business plans today!
Email Security that protects your small business

Running a business isn’t easy, and protecting your business from cyber-threats is becoming increasingly more difficult. Hackers want it all, your personal and business details, your client’s payment information, and so much more! It’s no surprise that small businesses are prime target, about 43% of SMBs lack any type of cybersecurity defense plan. That means almost half of all small businesses don’t have any (cyber) security to protect them against cyber-attacks.
ExchangeDefender PRO is our crowned jewel, our most advanced multi-layered email security suite that protects your business against email-borne threats like SPAM, viruses, malware, phishing, spoofing, and more! Small businesses have smaller budgets, and we understand that which is why our cyber security solution starts at just $5 per user, per month. Adding security to your organization would bring peace of mind as it would safeguard your business against malware and sophisticated phishing attacks. There’s simply no excuse not to protect your business. We tell our clients, if you can afford a Big Mac from McDonalds, you can afford cybersecurity.
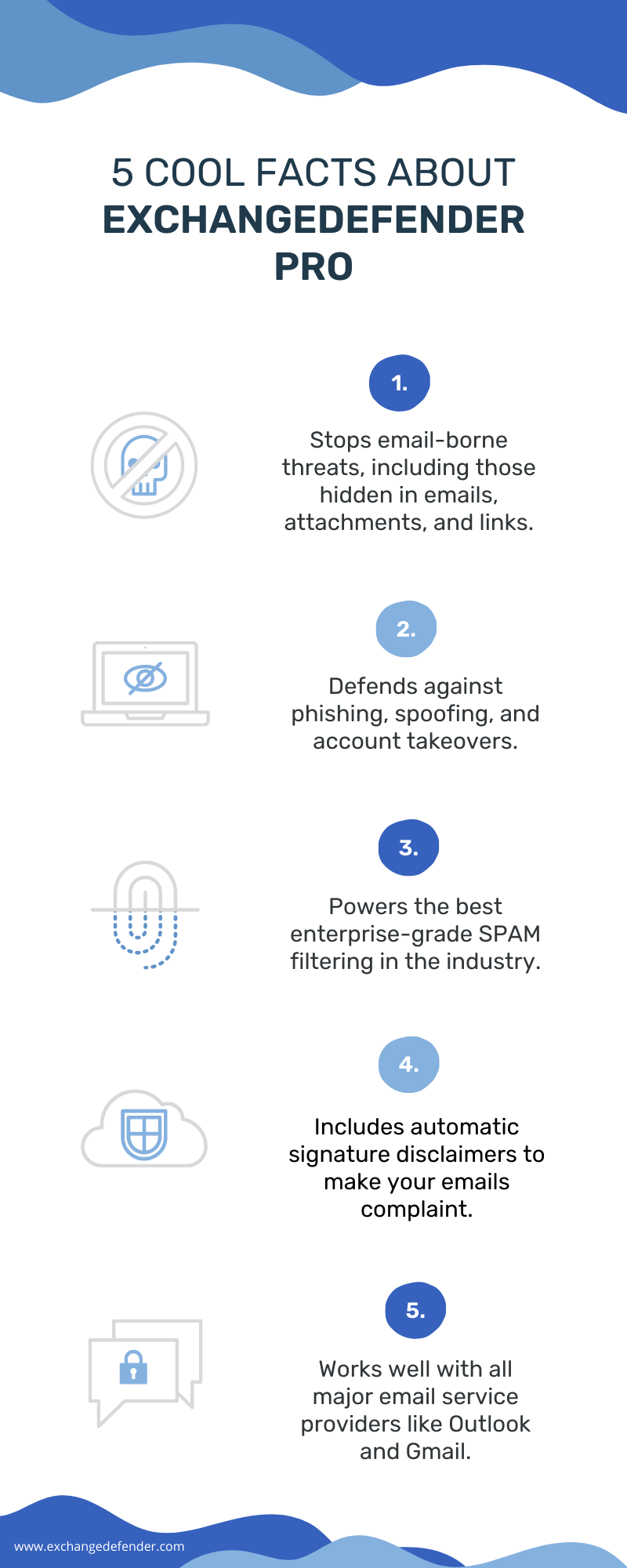
ExchangeDefender PRO stops email-borne threats
ExchangeDefender’s powerful email security suite offers a multi-level protection against email-borne attacks. The advanced threat protection features help defend users against threats hidden in emails, attachments, and links. Approximately 90% of all cyber threats originate via email, which requires businesses to have advanced threat protection. ExchangeDefender’s email protection goes beyond the average spam and virus filtering service.
ExchangeDefender PRO prevents data loss and theft
88% of businesses suffer a data breach due to lack of proper email security protocols. Our email protection enables companies to custom their own keyword policies, along with other sensitive data (credit card numbers, social security numbers etc.) they wish to keep private. ExchangeDefender PRO offers complete enterprise-grade threat protection that can help your company defend against the most sophisticated attacks, in addition to the more traditional threats like spam, viruses, and malware.
ExchangeDefender PRO prevents account takeovers
ExchangeDefender Email Protection keeps businesses a step ahead of hackers with AI-based threat detection. Corporate Account Takeovers has costed U.S businesses millions of dollars in 2019, and therefore has become the new focus of security concerns for SMB. ExchangeDefender PRO provides the strongest defense against spear phishing, account compromise and domain fraud. It offers protection to employees from falling prey to sophisticated email-based attacks.
It’s time for you to feel safe with our full stack email security solution, compatible with all major email service providers – including Office 365, on-premise Exchange, and G-suite for business. Get Started for just $5 per user, per month!
Flexible Allow Policy (Whitelisting) For Mass Mailers / BATS
Caveat: This feature is not recommended by ExchangeDefender, we actively discourage you from using it, and it is disabled by default. At the same time, we understand that sometimes the risk of getting hacked is less painful than arguing with non-technical users… In other words, we got you.
ExchangeDefender is an SMTP proxy security service, we scrub your email and only pass on stuff that doesn’t look like SPAM. In order to make that happen, we use industry standards such as SPF, DKIM and DMARC to make sure the senders are legitimate. (envelope-sender aka “envelope from:”)
The challenge these days is that nearly all the automated email messages (password reminders, marketing messages, newsletters, order confirmations, 2FA/OTP, etc) are sent from a unique disposable email address. Instead of coming from orders@amazon.com (the email you see in Outlook/Gmail) they actually come from something like vlad=exchangedefender-com.23581.i32.1941kab@east-1.aws.amazon.com. These email addresses are automatically generated and only live for a short period of time (less than 24 hours) and are used to track bounces and failed deliveries. However, once you open the email your mail client looks at the “display from” address such as orders@amazon.com. This address can be forged easily by anyone and that is how hackers end up compromising end users easily (cyberattack process better known as “spear phishing“).
ExchangeDefender has a secure facility to manage legitimate newsletter senders and automated email platforms (Domain Admin > Advanced Settings > Bulk Mailer Policy) and we train our partners how to properly create allow policies for<a href=”https://www.exchangedefender.com/docs/whitelist“>Disposable Email Addressing</a>/BATS. If you’re not a fan of using that process, you’re going to love the new From: Policy feature.
ExchangeDefender From: Policy
ExchangeDefender Advanced Features has a new section called “From: Policy” which enables you to create an Allow Policy based on the Display From address (display-from/fake-from). You can find this new setting at admin.exchangedefender.com under Domain Admin > Advanced Features > From: Policy.
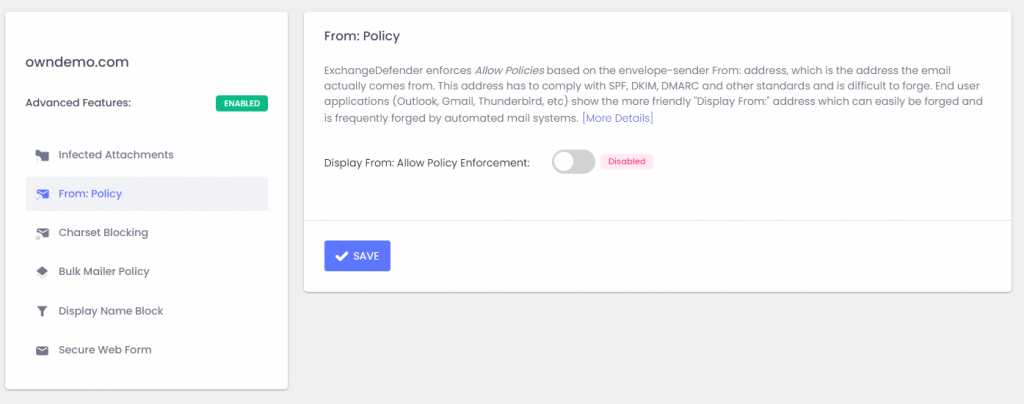
The policy is disabled by default, but if you enable it ExchangeDefender will search the email headers for the From: address and apply your Allow Policy (whitelist) using that address. Allow Policy forces ExchangeDefender to bypass all SPAM checks and will deliver the message to the users Inbox regardless of SPAM content (malware protection, virus protection, file attachment policies will still be enforced).
This feature will make delivery of automated messages (newsletters, password reminders, etc) much smoother with the side effect of making it easier for your users to get spear phished. However, this level of security exactly the same as whitelist/allow policy/trusted senders evaluations consumer email solutions such as Microsoft365/Outlook/Google Apps have, so if you trust their email security you can trust this as well.
-Vlad
tl;dr; You can now whitelist by the fake email address you see in Outlook/Gmail.
ExchangeDefender Recurring Email Scheduler
ExchangeDefender is proud to deliver another new feature to our Pro subscribers – Recurring Email Scheduler.
ExchangeDefender Recurring Email Scheduler feature has been the top request from our clients in 2021 as we continue our work-from-home lives: we are constantly trying to remind ourselves or others about something… and email (soon SMS/text) is the go-to way to do that. Virtually anything you need to remind yourself (or others) about on a consistent basis can be done including:
– Personal reminders
– 3rd party (clients/staff) reminders
– Invoice and recurring payment reminders
– Payroll and HR requests
– Meeting & appointment reminders
– Recurring tasks & maintenance requests
Problem is, most recurring email options require you to keep your PC on at all times. Maintaining and managing them quickly becomes a nightmare. Reporting is virtually non-existent, and creating new recurring messages takes time and skill and you’re in charge of troubleshooting problems with every software update. Or you can spend even more money on a 3rd party commercial solution.
This is where ExchangeDefender Recurring Emails feature shines:
– Create and manage all recurring emails from a single interface
– Create beautiful HTML messages with a friendly editor
– Attachments and multiple contacts are supported too!
– No need for your PC to be on, no DNS changes, no software to install
– Relies on public cloud infrastructure
– Powerful recurring scheduling & control
– Activity log and campaign delivery details (for compliance and troubleshooting)
– Ability to pause and resume campaigns
We’re also hard at work integrating our SMS Proxy solution so that we can extend the reminders framework to help you reach and remind everyone through their preferred contact method. Get started at https://admin.exchangedefender.com by clicking on Recurring Emails. If you can send an email, you can send a recurring email!
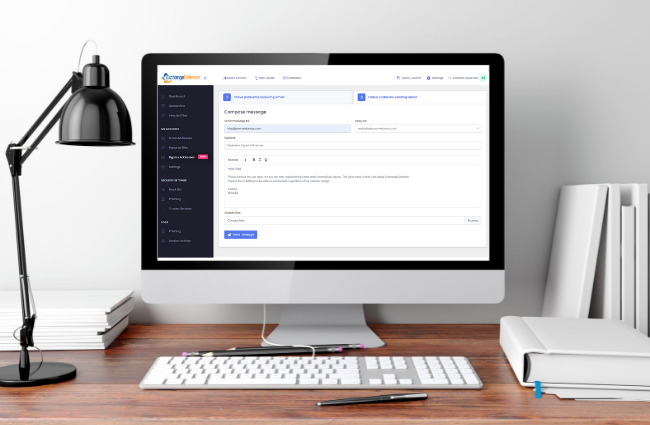
ExchangeDefender Outbound Email Bypass
ExchangeDefender Bypass builds on our commitment to helping users deliver email – not to mention making it easier to troubleshoot and work around mail security restrictions. We’ve all experience the “email bounce” when a message we send to someone promptly returns with some cryptic error and the bottom line is the recipient isn’t getting your email.
ExchangeDefender Outbound Bypass helps remedy this problem.
Email non-delivery can happen for a number of reasons – insufficient resources, misconfiguration, outage, local system policy, etc. When your mail bounces there are no easy ways around it, and most savvy users will just go to their free mail account (gmail, yahoo, ISP) which can cause a number of legal and HR complications. We can do better: with ExchangeDefender Outbound Bypass.
Much like our inbound bypass feature, the mail transiting this system does not rely on ExchangeDefender IP address space, network policies, or restrictions. We further designed it to rely on the public cloud infrastructure which is typically trusted and not subject to extra SPAM check (it’s where all your Amazon receipts & promotions come from).
So how does it work?
Simply open your browser and go to https://admin.exchangedefender.com.
Click on Bypass and select “I have problems sending mail” – fill out the form, attach anything you may need to and the message is sent instantly. When the recipient hits reply the message will go to your regular email address. That’s all there is to it. When the recipient receives your email it will still show your name, your email address, and include any HTML, images, or attachments you’ve put in the message when you composed it. It can also be used to help us open a communication channel with the recipients IT provider to resolve the original bounce as well. We hope this helps our partners troubleshoot problems faster and provide our clients a more reliable and resilient email experience.
P.S. ExchangeDefender Bypass is intended for legitimate, person-to-person email. Use of this system for UCE, bulk, sales, or otherwise commercial mail can expose you to steep fines.