How To Maintain a Company Blog & Why It’s Important
Most companies have great intentions when creating their websites to “get more social.” If you head to most business based websites you will see the usual Facebook and twitter buttons, links about products and services, and then, like a lost puppy all sad and alone there is the blog tab. A click on this link will many times bring you to a page with a number of posts, usually with sporadic dates and the last post being somewhere aroundY2K. Ok maybe it’s not quite that bad but you get the picture.
Many consider blogging to be a difficult task. Most will use excuses like “I don’t have time to write” or “I can’t think of anything to post.” The reality is these are just excuses and there are many reasons for keeping your company blog updated.
Why are Blogs Important?
1. Google loves Blogs
Fresh content to your site is favorable in getting your page organically to the top of Google. The more often you post the better you will fair and being higher on the list equals more business.
2. Blogs help keep customers informed
Though a company blog may not be the best place to open up about social, religious, or political topics; they are a great place to discuss emerging trends, new products and services, as well and local outreach.
3. Self Promotion and Employee Recognition
A blog is a great place to recognize employee accomplishments, announce big wins, and show off work. It adds a touch of personalization and can allow potential as well as current customers insight into the day-to-day business.
How to Maintain a Blog
1. Post something Daily
This may sound harder than it actually is but many of us post to social sites like Facebook everyday so why not to our websites? Easy ways to post daily can be to create photo based posts or video posts not only are these easy, but they are also great for Google.
2. Recruit Employees to Help
Assign employees a day of the week in which they are responsible to have a post written. Make sure that you provide expectations upfront and hold them accountable for the posts.
3. Make a list of Topics
It is much easier to get inspiration when you know what you want to write about. Some people find it easier to write down titles or topics of posts to be written. This can help the creative process and remind you of the things that are most important.
4. Write about your New and Existing Customers
Linking to your customer’s sites and providing promotion is a great way to drive traffic, add exposure, and give customers some additional love. They will appreciate the effort and it will provide an all around good feel to your site.
Either Do it or Don’t
1. Having a Blog post from Y2K as your last entry will not look good to anyone who goes to your blog page. If you aren’t going to be somewhat consistent you may consider removing the page.
2. Don’t get over opinionated in a business blog save those rants for a personal blog.
3. Do provide industry news and trends to keep customers informed.
4. Do have fun!
With a little effort and planning it is easy to turn that blog tab into a thriving part of your website. It will help breathe new life into your business as well as social makeup and give visitors an added benefit to your site. The advantage of climbing the ladder on Google will payoff in more business and revenue. Don’t expect results over night, but if you stay consistent and follow some of the advice outlined, you will be sure to have success with your company blog.
Frank Gurnee
VP, Channel Services, ExchangeDefender
(877) 546-0316 x4777
frank@ownwebnow.com
How Do I Send Emails from Our Scanner/Monitoring/Dog House After Switching to Hosted Exchange?
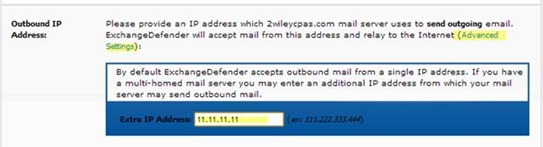
One of the common questions we get asked from partners after setting up Hosted Exchange is “How do I setup XYZ device to send mail now that we switched to Hosted Exchange?” For most setups, the easiest way (if the client has a static IP) is to add the clients IP as an additional “outbound IP” in ExchangeDefender under the domain configuration section.
Alternatively, partners can also refer to the SMTP list for Hosted Exchange for the SMTP settings for each Hosted Exchange network. If the device being setup does not support authentication or SSL encryption then the partner would have to create a support request to see if there is any way we can accommodate the client’s request.
Travis Sheldon
VP, Network Operations, ExchangeDefender
(877) 546-0316 x757
travis@ownwebnow.com
Selling Cloud Services… “Easy as Pie!”
 Cloud services have become a big part of most IT provider’s solution stacks, requiring most to rethink certain sales strategies and opportunities. Traditional means of selling services still apply, but there are a few things that can be tweaked and some things to think about when looking to fill your pipeline.
Cloud services have become a big part of most IT provider’s solution stacks, requiring most to rethink certain sales strategies and opportunities. Traditional means of selling services still apply, but there are a few things that can be tweaked and some things to think about when looking to fill your pipeline.
First, you would be surprised at how many potential opportunities you may have from previous proposals that you may have presented but the options at the time were just not right for the client. This seems to be especially true in the SMB space where it was easy to propose solutions that were outside of small business owners budget. With the adoption of cloud services things like expensive hardware upgrades can be circumvented and easy monthly solutions can now be provided.
You most likely have already created some kind of relationship with these previous potential clients so getting a second meeting to offer a new low cost solution should be as easy as pie. Start by picking up the phone and reaching out, let them know that you were thinking about their situation and came up with a new low cost solution that requires little to no out of pocket investment and will fill all of their needs within their budget. Make sure to let them know that it is “the cloud” that everyone’s been talking about that makes it all possible.
Make sure to go over their previous proposal and convert the solution into a budget friendly cloud opportunity. Be prepared to talk about the cloud and know how to answer potential objections like:
“What is the Cloud?”
“Is my data safe?”
“Am I stuck in long-term contracts?”
“What happens if my Internet goes out?”
Next focus some marketing efforts on cloud services to create new leads. This is another important step to filling the sales funnel. Utilize efforts already provided by large companies like Microsoft, Apple, and Cisco, which are educating consumers about cloud services. Marketing efforts should use the word “Cloud” and play to the lower cost of cloud services.
Do not get too technical! In the SMB space the easier you make any given solution the better. Remember you are not dealing with corporate IT guys but Small business owners that just want a solution for their technology at a fair price. Focus on their problems and how your company will solve them with ease. So pick up the phone and call some of those previous potential clients. What’s the worst that could happen? They say we went with another solution? Or better yet they say, “No come on by we are still looking for something that meets our budget.” You might just be surprised how many people do nothing when presented with something they feel is out of their budget.
Frank Gurnee
VP, Channel Services, ExchangeDefender
(877) 546-0316 x4777
frank@ownwebnow.com
How To Deploy an Ordered Hosted Exchange Account…Without Wasting Time
 Once you have ordered the mailboxes there are two places you (your techs) want to keep handy.
Once you have ordered the mailboxes there are two places you (your techs) want to keep handy.
First you want to keep this page up:
http://www.exchangedefender.com/Exchange+SharePoint_Deployment_Guide2010.php
This link contains a screen by screen walkthrough of the Outlook deployment. These are examples of the information you will need. Now to fill in the blanks you will need the information from the Service Manager:
Go to our support portal at https://support.ownwebnow.com
Click on Service Manager => Hosted Exchange
Click on the blue “I” button.
This will give you all the settings needed for the account in question.
If you need to also set up mobile devices, you can find that in our documentation section. They are there, also screen by screen.
Carlos Lascano
VP Support Services, ExchangeDefender
carlos@ownwebnow.com
(877) 546-0316 x737
Creating an Image Through Dress
IT companies can sometimes get a bad rap for their image, often times being known for or labeled as geeky tech guys, or ultra computer geeks. The truth is that this image is changing. With the education, training, and adoption of managed services, companies found themselves dressing up to be seen as technology consultants rather than techs.
 This “dressing up” had many IT companies wearing business suits and ties to set themselves apart from the everyday competing tech companies, and gained attention both good and bad with clients. The biggest issue with this was many felt it was too dressy, and potential or existing clients would find it uncomfortable, often labeling people with more terms like “insurance salesman.”
This “dressing up” had many IT companies wearing business suits and ties to set themselves apart from the everyday competing tech companies, and gained attention both good and bad with clients. The biggest issue with this was many felt it was too dressy, and potential or existing clients would find it uncomfortable, often labeling people with more terms like “insurance salesman.”
The fact is that there is a happy medium to be found that will suggest professionalism, comfort, style, branding, and confidence. The key is to focus and keep in mind each one of these areas when creating your company image.
Professionalism:
All employees that have customer-facing roles should represent your company in the most professional manner. Generally it is a good idea to provide a standardized dress for these employees. A long sleeve business shirt will cover any visible tattoos and provide a level of professionalism.
Comfort:
Ties may be too dressy, uncomfortable, and not practical for technical jobs unless it is tied into your branding and used for image; stay away from ties. Though many technical companies prefer polo shirts, which are comfortable the look is truly synonymous with the stereotypes; try to avoid polos if possible. Slacks are a perfect option for most companies but getting the wrong slacks will cause comfort issues. Look into breathable, moving slacks. Check out golf slacks they tend to be comfortable, have deep and multiple pockets, and are made for an active lifestyle.
Style:
Style is important; you must create a unique memorable style. You want people to know your unique look so your company is always represented. Do something that stands out; black shirts with red buttons or buttons that match your company colors is an idea. Use bold, seasonal colors. Just no bedazzle!
Branding:
Your company must always be represented and your logo and brand is the key to your image. Embroidered logos are far superior to screen printed logos and are well worth the added cost. Make sure to brand shirts with your logo. The standard is on the chest to the left. Play with sizes, designs, and placement; a bold move may be to place a tag line on the sleeve just below the shoulder on the left.
Confidence:
When your employees look good and they are complimented they will gain and represent confidence.
A dress policy is important to creating a standardized image and brand. Have fun with your style but keep it professional while still being memorable. Don’t be afraid to spend a little money on R&D until you get the right mix for the image you would like to portray.
Frank Gurnee
VP, Channel Services, ExchangeDefender
(877) 546-0316 x4777
frank@ownwebnow.com
Think, Change, Implement
Just as people repeat old sayings or theories every day without giving them much thought, people often apply ideas to their business, which they have failed to give enough critical thought to.
 There have been countless times when I have heard people say “We have always done it like this” as a way to justify why they do what they do. Now, if you have always done something a certain way, because you have looked for better ways to do it, and failed, that’s fine. But, to keep on doing something ONLY because of familiarity, makes very little marketing sense. Tell me this, if you continue to do what you have always done how can you expect there to be different results? Change is necessary and vital for “successful marketing”. Leveraging your marketing efforts is a GREAT way for you to change up some things. Effective marketing can be used a tool to reach your customers. It is always important to advertise or market your products and services in a way that is appealing to them.
There have been countless times when I have heard people say “We have always done it like this” as a way to justify why they do what they do. Now, if you have always done something a certain way, because you have looked for better ways to do it, and failed, that’s fine. But, to keep on doing something ONLY because of familiarity, makes very little marketing sense. Tell me this, if you continue to do what you have always done how can you expect there to be different results? Change is necessary and vital for “successful marketing”. Leveraging your marketing efforts is a GREAT way for you to change up some things. Effective marketing can be used a tool to reach your customers. It is always important to advertise or market your products and services in a way that is appealing to them.
It is in the best interest of all parties to regularly review the processes within your business and in your marketing efforts. In fact, it’s hard to make meaningful, ongoing progress, without constantly seeking to improve what you do and what your clients want.
How can we help?
Since we have recently added a few new services to our product offerings we are revamping the marketing materials that we brand and provide free of charge to all of our partners. This is something that we are changing so that you can implement them into your marketing strategies to better help you with your clients. Stay tuned to the Marketing Collateral page of our website for new downloadable templates to brand. All of the Product Guides are now updated and as always if you wish to have some collateral branded please feel free to fill out the form on that page and I will send you new collateral branded just for you with your brand, your logo, and your color scheme within 24 hours!
Stephanie Hasenour
VP Marketing, ExchangeDefender
stephanie@ownwebnow.com
Action Cannot Be Completed. Name Cannot Be Resolved.
Every week we get at least 5-10 support tickets created by partners who receive the error “Action cannot be completed. Name cannot be resolved.” A lot of the times partners may be setting up an additional mailbox for a user, but sometimes it can happen when resetting up the users profile. In this blog I hope to provide some insight on why this occurs.
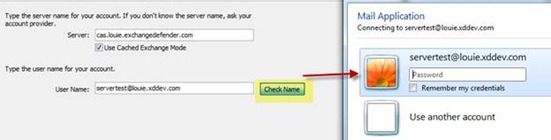
First and foremost, if you do not receive a credential window prompt then you either have a credential conflict or an invalid outlook configuration. I would like to make it very clear…you should always, always see the credential window.
When you hit “Check Name”, Outlook does a user lookup to resolve the input username to a mailbox. Outlook will first attempt to use the users local credentials to authenticate, then any cached credentials (Windows Credential Manager), finally, if no credential entries authenticate then Outlook will prompt the user for credentials.
If a user does not receive the credential prompt and receives the error “Action cannot be completed” a quick fix is to go to More Settings, Security, and then enable the checkbox to “Always prompt for logon credentials.”
When user’s select “Remember my credentials” Outlook then creates a cached credential for windows in the credential manager
Normally, this works as expected.. the next time Outlook launches it will try the cached credential which would authenticate.
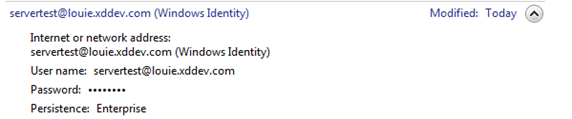
But imagine if you were trying to add a second mailbox to the users profile (Let’s say the CEO has two mailboxes for ‘two different companies’) .. how is Outlook to know that the cached credential for servertest@louie.exchangedefender.com on “cas.louie.exchangedefender.com” isn’t for the second mailbox (Let’s say servertest2@louie.exchangedefender.com)? The answer is..Outlook won’t be able to tell the difference.. The server will respond to Outlook with the message “Access denied” because the cached credentials for mailbox1 does not have permission to access mailbox2 (Think of it as trying to access mailbox2 via OWA, but using the credentials for mailbox1) and then receives the error “Action cannot be completed. Name cannot be resolved” when trying to resolve the mailbox name for mailbox2..the key point is that this failure will instantly occur and there will be no prompt for the user to provide credentials because the error “Access denied” mean “You have a valid account here, but it does not have access to this resource”.
Now let us imagine the inverse where a user gets prompted for credentials every time no matter how many times they select “Remember my credentials” or if they follow our help article “My Windows OS won’t hold the Outlook authentication info!” and manually add “*.exchangedefender.com” to the credential manager.. This is because Outlook is passing off a valid “Account” that has access to the resource (Mailbox), however, the credentials being passed off are incorrect. If Outlook tries to authenticate with invalid credentials the server will respond back with “Invalid credentials”..notice how this isn’t the same error as “Access Denied” which is why Outlook will then prompt the user for credentials. To solve this we tell users to delete all references to any exchangedefender servers in credential manager and then manually add the credentials (following the above blog post) and then adding *.exchangedefender.com to the “Local Intranet” zone in Internet Explorer. This should allow Outlook to trust our servers to hand off the credentials.
Finally, the last common scenario for the two failures (either no credential prompt or reoccurring credential prompts) is if the local users login name matches a username on the server. Remember, Outlook will first try the local logged on users credentials. Now imagine if my local login name was servertest@louie.exchangedefender.com… then any time I attempted to add an Outlook profile I would either instantly authenticate or I would always get the credential prompt. Can you guess why? Its because either the local users credentials (Either their local computer user name or an active directory account) match the servers credentials.
Active Directory:
· Username: servertest@louie.exchangedefender.com
· NT Username: servertest
· Password: 123456
Exchange:
· Username: servertest@louie.exchangedefender.com
· NT Username: servertest
· Password: abcdefg
In the above, the server would always prompt for login credentials because the credentials are mismatched. But let’s think back to our first example of adding the users second mailbox to their profile and imagine we had the same credential conflict as above, except the exchange user is servertest2… Outlook would again instantly fail because the local login credentials does match an exchange account, but does not have access to the resource (The second mailbox, servertest2).
In the case of opening multiple mailboxes in one profile the only way to get Outlook to not prompt for credentials for each mailbox is to grant full access permission from one user to another…so if you cached the credentials for one mailbox (ie., servertest) and then granted servertest full access credentials to servertest2 (second mailbox) then outlook wouldn’t receive the “Access Denied” error when trying to access servertest2 with the cached credentials of servertest.
Travis Sheldon
VP, Network Operations, ExchangeDefender
(877) 546-0316 x757
travis@ownwebnow.com
Compliance Archiving FAQ
 Our compliance product has been growing quickly of late and as the volume grows you start seeing common questions come up in mass.
Our compliance product has been growing quickly of late and as the volume grows you start seeing common questions come up in mass.
I’ll take this opportunity to address the most common ones that we’ve seen come up.
I. When setting up and on premise (meaning not hosted with us) Exchange server for compliance. When you’re setting up the Journal mailbox, you have to be very careful in Active Directory. Please make sure to set the account to:
a. Not allow the password changes
b. Password never expires
Remember if we can’t access the journal mailbox, we can’t archive your data. But don’t worry if you did this, the journal information will be intact so you wont be out of compliance but obviously you will just fall behind, but it will catch up.
II. How do I access my archive https://compliancearchive.exchangedefender.com is not showing my customers?!
After the .com append ?spid=YOURSPID
We hope these tips make the experience a little smooth, remember share this stuff with your techs!
Carlos Lascano
VP Support Services, ExchangeDefender
carlos@ownwebnow.com
(877) 546-0316 x737
Selling Confidence
In sales, there are many techniques that people use to make a sale. There have been countless books on the subject of sales, and there are many takes on what is required to become a great salesperson. Though all of these techniques have their place, there is not a single more important aspect in my opinion to the process of a sale, than the ability to portray confidence.
The words “portray confidence” however really do not paint the right picture. Confidence whether it is in yourself, your product, your service, or solution is the wholehearted belief that what you do, what you are, and what you bring are absolutely, without a question, the right thing for your client. This may be a difficult concept for some, especially technically minded individuals to get behind.
The technically minded person will constantly question every aspect of a solution. This is rightfully so, as it is built into their psyche the need to know every aspect, the pros, the cons, and everything in between. This same need for knowledge can sometimes break down the confidence level presented to a potential client and can make sales more difficult for the technical person.
Considering that most IT professionals started their businesses from a technical background, this simple understanding is the key to unlocking sales. Technically minded individuals must be able to believe in themselves, their product, and their solution and be passionate about those things.
 Most people have an outside passion. This may be sports, a hobby, or even a favorite brand. Think of something that you are so confident in and passionate about that you would never lose an argument on that subject. Apply this same type of passion and confidence to your product, service, or solution. It is important to get excited and to feel real passion and emotion. If you can unlock this same feeling you will surely portray confidence, and confidence equates to more sales.
Most people have an outside passion. This may be sports, a hobby, or even a favorite brand. Think of something that you are so confident in and passionate about that you would never lose an argument on that subject. Apply this same type of passion and confidence to your product, service, or solution. It is important to get excited and to feel real passion and emotion. If you can unlock this same feeling you will surely portray confidence, and confidence equates to more sales.
Frank Gurnee
VP, Channel Services, ExchangeDefender
(877) 546-0316 x4777
frank@ownwebnow.com
ExchangeDefender Corporate Encryption
Introducing ExchangeDefender Corporate Encryption! Corporate Encryption is another new addition to the ExchangeDefender Suite!
Corporate Encryption is not replacing the Encryption piece that is already included in the full ExchangeDefender Suite; it is a separate feature that is simply adding a whole new level of protection and control. ExchangeDefender Corporate Encryption provides an easy and seamless way for organizations of all sizes to implement content protection and comprehensive control over information being sent through email.
Highlights
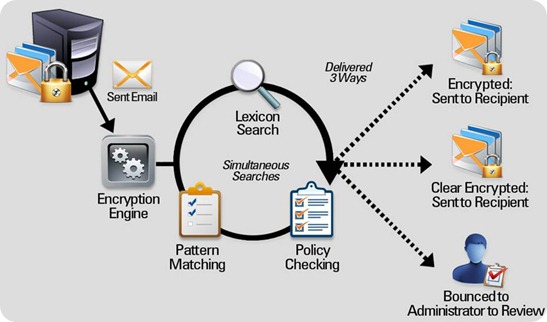
– Pattern-Based Encryption – Pattern Matching can detect patterns inside of outbound email and attachments and categorize them as credit card numbers, social security numbers, dates of birth or other company-specific account numbers. Each pattern can be assigned an automatic action to be taken once the message with protected content is detected.
– Comprehensive Reporting – ExchangeDefender Corporate Encryption delivers sophisticated reporting both on the activity of the users and the compliance officer. You can see at a glance which content is protected as well as which messages have triggered compliance and encryption activity. By reviewing this information you can be assured that any suspicious activity is quickly addressed and that you can respond to inquiries about your regulatory compliance on demand.
– Corporate Encryption Mechanisms – Pattern detection and lexicons provide only for the piece of the encryption puzzle – automating response to potential loss of corporate data is crucial to operational efficiency. Emails that contain sensitive information can be encrypted and sent to the recipient with the username and a password or can be simply emailed with a link to the encrypted message. For additional security, messages can also be forwarded transparently to the Corporate Compliance Officer (CO) who can review the message and then allow it to be sent or block it outright.
– Lexicon Dictionaries – Enables organizations to provide entire dictionaries of words that could indicate data leakage. For example, financial companies working in investments may want to intercept messages that contain words “Guaranteed Investment Returns” or “Insider Information” and assign an appropriate action to meet regulatory compliance.
How It Works…
Corporate Encryption is very easy to promote and it is also extremely easy to add to your solutions set and offer because there are so many benefits associated with using it. When talking with clients the key points to get across is that you understand the needs of their business and their pain points. Also, let your prospects know that you have the product that can provide a solution. Another great thing to point out about Corporate Encryption is the ability to have more control. You can better monitor your network and be aware of things that are going on. You can define keywords and patterns, so that when certain things that you are concerned about happen you will know about them and be alerted. There are also legal and HR benefits of protecting both company data and employees and prevent important data from being leaked or sent out. Corporate Encryption is also compliant with SOX, HIPAA, SEC and local government requirements to provide you with more protection and powerful auditing.
ExchangeDefender Corporate Encryption is only available with the full version of ExchangeDefender and our Exchange + SharePoint offering; it is not available with our Essentials services. Corporate Encryption is available for just $0.99/user/month and there are no contracts and no commitments.
For more information, visit the ExchangeDefender Corporate Encryption page on our website, or feel free to give us a call!
Stephanie Hasenour
VP Marketing, ExchangeDefender
stephanie@ownwebnow.com