Large Scale Migration
 The most important aspect of a large scale migration is communication. This can make a migration that either turns you into a trusted company relationship or the most recent “IT guy” that was fired by that company. There is a delicate balance that you must preserve between the needs of the technology and the needs of the business owner. The best way to do that is to be as meticulous as possible with your communication process.
The most important aspect of a large scale migration is communication. This can make a migration that either turns you into a trusted company relationship or the most recent “IT guy” that was fired by that company. There is a delicate balance that you must preserve between the needs of the technology and the needs of the business owner. The best way to do that is to be as meticulous as possible with your communication process.
Prep work, communicate.
The first thing you must do is map out an initial time line and start testing the process. This time line will start solely based on the IT departments recommendations. These recommendations are generally based on the hardware or support life cycles and the length of time to complete it. Once you have that sorted out, you probably want to add another two weeks to a month of notice and relay that information to the decision makers at the affected company.
Test, communicate.
Once you’ve received a response, you make adjustments as necessary to your schedule and begin a live test where permissible. We also see excellent guides on the internet on how to do any migration imaginable; the most important point to consider is that no two are alike. So you found a frame work to use on the internet, so you have to take the next step. What we typically do is use test mailboxes, we migrate them individually, and then we move them as batches, repeatedly. The bottom line is this; the more work you do before the migration the less likely you will have to pay overtime for a botched migration.
Execute, communicate, then communicate again
Once you’re satisfied, you reach out to your clients again and confirm that you’re ready to start as you previously agreed. This is where the process will vary when dealing with end users versus an IT partner. We can get away with the following notices: an announcement, a reminder, a start, a mid-point, a completion and a couple of follow-ups. We are about to do this due to the fact that we’re dealing with top notch technology professionals. However, with end users you have to have a more controlling approach, depending on the size of the business, you may opt to have everyone come into the office and leave their mobile devices with you for the migration, or you can do appointments. The most important thing in the process is to check as often as your staffing will allow it, that everything is going smoothly and that the expectations you set are being met. I would even advise a follow up call at 1 week and 2 weeks out to pick up the “slow to report issue” folks.
Taming Your Email
If I ever opened Outlook in the mornings and saw a slew of emails (unread or read) in my inbox, I’d get depressed. Seriously, how can one not feel anxious when seeing (1,323) unread messages sitting in their inbox? If you need a full searchable, secured, and compliance archive solution; then take a look at our long-term Compliance Archive service. Otherwise, take a look below at some of the things I do to prevent email from taking over my life:
• Operate a Zero-Sum email policy. If an email arrives in your inbox, address it, file it, or delete it. In simpler terms, my inbox is not a storage folder–it’s an inbox.
• Never use your Deleted/Trash folder as a storage folder. If you need to file that piece of mail somewhere other than your inbox, then create a folder for that specific purpose. Your deleted folder should be empty most of the time. In fact, you can configure most email applications to remove all contents in the Deleted/Trash folder when you exit the application. Those still reading this probably just laughed at me for suggesting that an email application is ever closed. Which brings me to my next suggestion…
• Close your email application when you are finished working. Trust me when I tell you that your email is still flowing. The brain operates on triggers. By closing down your email application at the end of the day, or when you are not using it tricks your mind into relaxing a bit. Granted, it will probably take your brain a few days to stop freaking out that the email application has been closed; but you will thank me later. We have conditioned our brains to a pavlovian response: Tingle Dingle, check email, tingle dingle, check email, tingle dingle, check email. Get the picture? Your brain is on high alert, waiting for that sound. Close down the app, place your device on silent, and relax.
• Unsubscribe. Most SPAM really isn’t SPAM at all, it’s BACN (pronounced Bacon). If you are unfamiliar with this term, BACN is email that has been subscribed to, but most likely never gets read–think newsletters, sales ads, etc. Now, why they call this BACN is a mystery. Personally if I ask for bacon, I eat the bacon; but I digress. If an email that appears to be BACN arrives into your inbox and you have no desire to ever read these types of emails again from this particular business; unsubscribe. If you received an obviously suspicious piece of email from someone you do not recognize, do not unsubscribe – report it as SPAM. Many spammers use recognizable names to embed their advertising but the unsubscribe link on the bottom just takes you to their site that confirms your email address as valid. Soon after you click it you’ll see an exponential increase in SPAM.
Needless to say, ExchangeDefender is a great solution to keep the email overload from impacting your productivity. Through use of web file sharing to send important documents, compliance archiving to keep 10 years of email and locate anything you need instantaneously, encryption to protect and secure data, we are continuously looking at how we waste time in our Inbox and we fix it with ExchangeDefender.
Michael Alligood
Partner Account Manager
michael@ownwebnow.com
877-546-0316 x707
Competing with Office 365
 Almost on a daily basis I get the question: how do you compare to Office 365? Microsoft’s $6.00 offering is making it hard for a lot of MSP’s to compete, or provide something other than 365, but that shouldn’t be the way it works. As always we are here to help, so I have compiled a list of top three selling points for why ExchangeDefender is the best choice. Use these and you will close the sale with ExchangeDefender, not Office 365.
Almost on a daily basis I get the question: how do you compare to Office 365? Microsoft’s $6.00 offering is making it hard for a lot of MSP’s to compete, or provide something other than 365, but that shouldn’t be the way it works. As always we are here to help, so I have compiled a list of top three selling points for why ExchangeDefender is the best choice. Use these and you will close the sale with ExchangeDefender, not Office 365.
White Label:
Everything we do is completely white label, you can brand ExchangeDefender and make it your own. For branding in the admin panel simply login using your SP credentials, click on the configuration tab, then branding. You can brand the portal with your logo, tagline, and even your customized name for the product.
In addition to all of our services being white label, we also offer free brandable marketing collateral. For free collateral just visit http://www.exchangedefender.com/marketing_xd.php and click on the product you wish to brand. Just click on the download button and you can add your logo, your colors and anything you wish to make this truly a part of your overall solution.
Remember: Your client or prospect is talking to you for a reason – your products and solutions need to reflect your key advantages, not someone elses. After all, if you are just going to resell the same solution anyone can buy at any time then why should anyone do business with you or consider your expertise?
24/7 Support through us
Small businesses are always concerned about the cost. Many business owners are very price conscious and want to find the best bang for their buck. Microsoft charges your client on a per request basis, so each time they call in they’re charged a support fee. I think this is a very important factor to stress, because the end user goes with the notion that they will not experience any problems or it will be tiny enough they won’t have to pay an arm and a leg, or they think it will still be cheaper in the long run, but bad news for them, it won’t be. Depending on your business model, you either include so many hour of support, or you bill in additional blocks of time, this way the customer has more control and the rates are a lot less than what Microsoft would charge. The customer needs to know that in the long run they will end up paying out more to Microsoft for support than what they’re saving on the monthly fee.
In addition to saving money on support, you will also save time. With Microsoft the client must call their support department directly which can create headaches and completely waste all of the end users time. As the servicing partner you can open a ticket with us or speak to our support staff directly, this leads to a quicker resolution time and a more satisfied customers.
Everyone goes into the cloud expecting the best case scenario. Truth is, all technology is susceptible to failure and the bottom line is that you have a plan for how to deal with things like outages, DDoS attacks and communicate effectively with your clients about their service. When you’re “just a reseller” you get none of the profit and all the blame.
Personal Relationships
At ExchangeDefender we make it our priority to build personal relationships with each and every one of our partners. We are always available, someone will be here to answer your questions. Speaking from the business side I know many of our partners and speak with them on a regular basis to make sure that everything is going smoothly and to offer any help that I can. As far as the support staff goes, they’re readily available through the portal 24/7 and by phone from 4 am EST to 7:30 pm EST. Over time you will become familiar with them the more you speak with them on the phone or deal with them directly in the portal. With Microsoft you are unable to have this personal relationship, every time you call you speak to someone different. Not to mention you’re lucky if your previous issue was documented or that the person you’re speaking to has the level of knowledge to resolve your issue.
So the next time you’re in a situation where you’re against Office 365, just remember these key points and you’ll be able to close the sale with ExchangeDefender!
As the cloud solutions emerge and mature quickly it is important to know who you work with, know that you can count on them and expect them to work with you not against you. These are just the top 3 of our competitive advantages of why you should consider us, next week I will write about the top three reasons your client should chose your ExchangeDefender Hosted Exchange, Sharepoint and Lync offering instead of Microsoft.
Anastasia Wiggins
Partner Account Manager
anastasia@ownwebnow.com
877-546-0316 x739
Motivate Employees By Posting Performance Graphs
 The health and performance of a company is a measurable and dynamically changing set of information, which can be easily created and viewed by management. Many MSP’s have already found that posting call performance, ticket handling times, and managed services metrics, helps to give employees an insight into how they are performing from a technical aspect; but what about the general revenue trend and health of the company?
The health and performance of a company is a measurable and dynamically changing set of information, which can be easily created and viewed by management. Many MSP’s have already found that posting call performance, ticket handling times, and managed services metrics, helps to give employees an insight into how they are performing from a technical aspect; but what about the general revenue trend and health of the company?
People by nature are competitive. This is why sales organizations, or departments often post large boards with information labeling the sales leaders and their numbers. These boards are meant to motivate individuals to strive to be at the top and spark the competitive nature of individuals to strive to be better. You see this in almost every industry, even retail and food service industries post motivators like, top sales and employee of the month boards in their respective break rooms or employee common areas.
Though sales and technical performance is commonly shared with employees, most SMB businesses rarely share overall company revenues, growth, or health with the employees that help to make up the business. Since, every person in an organization has a vested interest in seeing a company succeed, sharing this information may help to motivate employees as a team, much like the individual sales and technical motivators do.
The biggest concern that most business owners and managers have for not sharing vital company information is potential animosity. It may be thought that if a company is doing well and employees gain insight into numbers, they may be more likely to expect larger salaries or increased pay for their work. Though this may be an initial thought if this information is posted, it will not be the norm after it is part of normal routine. This means that once you are posting information regularly, it just becomes second nature.
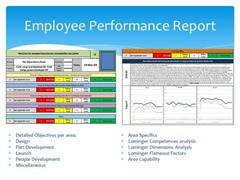 This information becomes significantly important to employees especially if there is a downward trend in the business. This new insight can help to explain management decisions, cut backs in hours, as well as hiring freezes, or any other things that may affect their day-to-day job based on a slow down in business. It also becomes a motivator and visual proof that everyone needs to step it up to increase efficiencies, sales, and revenues.
This information becomes significantly important to employees especially if there is a downward trend in the business. This new insight can help to explain management decisions, cut backs in hours, as well as hiring freezes, or any other things that may affect their day-to-day job based on a slow down in business. It also becomes a motivator and visual proof that everyone needs to step it up to increase efficiencies, sales, and revenues.
The easiest way to implement and post this information is by creating a visual graph that can be hung up in employee common areas. Most spreadsheet and word processor programs allow easy creation of these graphs, which can be printed out and posted. Some companies choose to post this information monthly, where others choose to post quarterly. This becomes an internal decision, but note that monthly provides better motivation.
It is recommended to include overall revenues along with the graph, though again this is an internal decision. This can provide indicators and trends as well as insights; providing employees with information that would have only previously come as management hearsay or owner propaganda. It is not recommended however to send this information via email. In email form, the information is less likely to have an impact or be read, and will not be visually represented daily for all to see and discuss.
By providing company performance information to employees, not only are you making them an accountable asset to the business, but you are also running the business like an enterprise. Corporate public companies must divulge all of their numbers and performance publically, giving everyone deep visibility into the health of the company. Your employees will find motivation in the information, camaraderie, and be proud to help the business grow.
ExchangeDefender SQL Balancer Maintenance Window
This Friday, July 19th, 2013 we will be conducting an upgrade, stress testing and DDoS simulation against ExchangeDefender SQL backend, load balancer backend and the overall infrastructure fault tolerance starting at 3PM and ending at 6PM EST.
During the maintenance window mail flow will not be interrupted and mail delivery will not be delayed. Access to email, LiveArchive, mobile services and so on will not be interrupted either. Access to https://admin.exchangedefender.com site, including the ability to make configuration changes or release SPAM, will be interrupted periodically. Again, no email will be lost or delayed.
Following the upgrade our capacity across the core ExchangeDefender network will be increased which will enable us to launch additional services that will be discussed in the upcoming webinar. We apologize for the inconvenience this causes your clients as they may be presented with the message “We are currently conducting routine maintenance, please try your request again in a few minutes”
Scope of the effort
Isn’t this something you could do outside of the peak hours?
Yes, and we routinely make changes and upgrades during the standard weekend maintenance intervals.
For the purposes of this upgrade and an assessment of the new failover systems brought to the new version of ExchangeDefender, we wanted to run a maintenance interval during the peak usage and ascertain both our ability to handle traffic with the brains of the system offline (ExchangeDefender SQL) as well as test geographic redundancy during peak hours.
We felt it was better to have this done at the same time on a scheduled and controlled circumstances than under the unplanned service outage or DDoS.
As I will discuss next week, we have spent a fair amount of money and time upgrading the network not just to be able to sustain excessive outages but also distributed attacks, hacks and so on. We expect to be able to operate the network in a distributed and autonomous environment should we experience massive changes in Internet routing and availability of global networks. If you’ve been paying attention to the news, international government response to NSA espionage, rise in sophisticated hacking and network exploit activity, the reasons and the manner in which we are executing this maintenance window should be self explanatory.
As always, our staff will be available in higher than usual counts so please count on us.
We will also be providing a play-by-play updates as usual via NOC and our @xdnoc twitter.
Sincerely,
Vlad Mazek
CEO, ExchangeDefender
877-546-0316 x500
ExchangeDefender – Outlook/Desktop Add-Ins
This past week we published updates to our ExchangeDefender Outlook 2007, Outlook 2010 and Desktop application. We collected information that was submitted throughout bug/feature section inside of our support portal. We’ve cleaned it up and implemented the features you’ve been asking for:
Below is a list of bugs/features that we have addressed.
· Upon attempting to shut down the computer, the application would hang and prevent the system from shutting down.
o This issue has been resolved. The application will now terminate correctly upon system shutdown or application exit.
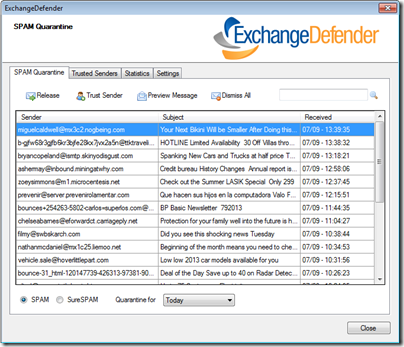
· Spam/SureSpam
o These were not being displayed correctly under the appropriate section.
o There was also an issue preventing some subjects/senders from being shown.
· Releasing Messages
o All issues regarding the release of messages have been fixed.
· Some users complained about the 2007 version now loading.
o This issue has been resolved.
· Application icons / installation banner.
o The icons and installation banners have been updated to our standard ExchangeDefender images.
Remember, the download center for all ExchangeDefender software is available on our web site by clicking on Documentation > Downloads.
Hank Newman
VP, Development
hank@ownwebnow.com
The Price Is Right–Maybe
 Before joining ExchangeDefender and Shockey Monkey full time in September 2012, I was a business owner of two I.T. VAR/MSP businesses spanning over a decade. That said, I am fully empathetic of the decisions that have to be made by all who hold that position. Being one of two Partner Communication Managers working for OwnWebNow Corp. (Anastasia Wiggins being my colleague), I speak with our partners on a daily basis. Inevitably, one of the subjects that come up doing a partner conversation is how much they are charging for services rendered–whether we are discussing our services or labor costs in general. Ultimately the conversation starts by the partner asking me what the going rate is for other partners reselling our services. My answer is always the same: It depends…
Before joining ExchangeDefender and Shockey Monkey full time in September 2012, I was a business owner of two I.T. VAR/MSP businesses spanning over a decade. That said, I am fully empathetic of the decisions that have to be made by all who hold that position. Being one of two Partner Communication Managers working for OwnWebNow Corp. (Anastasia Wiggins being my colleague), I speak with our partners on a daily basis. Inevitably, one of the subjects that come up doing a partner conversation is how much they are charging for services rendered–whether we are discussing our services or labor costs in general. Ultimately the conversation starts by the partner asking me what the going rate is for other partners reselling our services. My answer is always the same: It depends…
The reason for such a vague answer is because the answer primarily involves taking into account two major considerations:
1. The location the service is being rendered, i.e. city/State, and/or region; and
2. The time/complexity it takes to render said service, e.g. setup time, monitoring time, complexity of the technology, etc.
Let’s delve further into these two considerations and come to a more defined answer for your particular business.
The Location of Render Services.
As Partner Communication Manager, one of my jobs responsibilities is to attend I.T. events that ExchangeDefender and Shockey Monkey sponsor. These events are held all over North America. The summer months have definitely tested my love of travel. However, by visiting these different cities and regions of the United States; I have come to understand that Midtown New York can charge $3.50 for a 20 ounce Coke Zero that costs me $1.50 in Schaumburg, IL. The same is true with virtually every product or service between the two aforementioned locations. Similar to the real estate market, the location (location, location) will greatly dictate your pricing. Densely, fast moving cities tend to price higher than more rural, spread out towns. The reasoning is maddening to understand because most times it simply boils down to the fact that people are willing to pay more for services rendered in cities that never sleep. Even stranger, this can be totally independent concerning the amount of competition available to the customer. By that, I mean even if there are numerous competitors in the area, people will still pay an inflated price in bigger cities. This is due to something called involuntary competitive pricing. This is where a price for a particular service was set by a business and the competition set their pricing +/- 10% to show an added value or discounted price while maintaining close proximity to similar business offering like services.
The Time/Complexity to Render Services.
The old adage still applies: Time is money. And when the complexity of the service rendered increases, ultimately the time it takes to implement and/or monitor said service increases as well. As a result, you could be looking at a nice pay day. However, the inverse is also true. If your service can be seen as less a specialty and more a commodity, you may have to supplement your income to make ends meet. How can your services be seen as commodities? Increased competition, for one. The lack of complexity is another. If end-users are willing to take on the additional pain of implementation and monitoring services to reduce their operating budget, there isn’t much you can do to win that business except provide additional value added services they may not get by taking on the responsibility themselves. Be careful of this, however. If you give away too much, you will end up working twice as hard for less money. Never, ever, ever work for free. Assuming you are a for profit business, never forget that one of the primary reasons you started a business was to make a profit!
The Sales Pitch (You can skip this part if we ever spoke on the phone about ExchangeDefender services.)
ExchangeDefender is a partner-driven company–meaning without our partners, we might as well close shop and sell empanadas. We price our services to you with the idea that you can make as little or as much as these two considerations allow. I have seen markets where partner can make as much as a 33% profit margin on our products and services. Other partners literally give our products away as value added services in order to balance out their labor costs. The latter is normally performed to illustrate good form in giving something to the customer at no charge to you. In other words, they simply pass on the cost of the product to the customer or carry the cost themselves in order to sign an annuity contract. Point being, if you need assistance in reselling any of our products, pick up the phone and give me a call. You have 99 problems as a business owner, but making money off our services shouldn’t be one of them.
Michael D. Alligood,
Partner Communications Manager
ExchangeDefender | Shockey Monkey
877-546-0316 x707
How do I get more referrals?
 You’ve all seen the commercials; it starts something like, “refer a friend and get $50 off your next bill” or something of that nature. In traditional consumer-based businesses, this type of targeted marketing may have its place, but in SMB and B2B businesses it just comes off as desperate. Of course, this is not to say that it may not have worked for your IT business, but hoping to bribe a customer to give up a referral is not good practice.
You’ve all seen the commercials; it starts something like, “refer a friend and get $50 off your next bill” or something of that nature. In traditional consumer-based businesses, this type of targeted marketing may have its place, but in SMB and B2B businesses it just comes off as desperate. Of course, this is not to say that it may not have worked for your IT business, but hoping to bribe a customer to give up a referral is not good practice.
Another common but bad business practice is asking for referrals upon closing a sale. Whether a salesman hands you a paper and asks you to write down some friends who might also be interested in their product, or one that simply asks for a referral at the signing, this practice is not only useless, but makes for a bad first impression. The problem is that the salesperson, and more so the company has not yet proven their service, so asking for a referral at this point in the game is bad practice.
There are a few ways of getting referrals without the used car approach:
1. Refer Business to Your Customers – Referrals are a two-way street, start by sending business to your customers. Set up meetings and soft introductions to introduce people to your loyal customers. Not only is this a good business practice, but also your customers will reciprocate.
2. Ask When Receiving Good Survey Results – Surveys are a great way to gauge how you are performing for your customers. When receiving good reviews simply ask customers if they know anyone that might also be interested in getting excellent service as well.
3. Face-to-Face QBR’s – A good time to ask for referrals are at face-to-face QBR’s, or quarterly business reviews. Make it a part of your QBR to ask for referrals at the end of every QBR. It may seem like much to do it every time, but getting a hot referral can be all about timing.
The majority of MSP’s would tell you they get the majority of their business from referrals. This makes practicing good referral gathering techniques an important aspect of your business. Be sure to only ask for referrals once you have established a relationship with a customer, and create a documented process for your salespeople to follow.
Compliance Promotion Is Ending Soon
It’s summer time and we are promoting two products for the month of July! Right now we are offering fifty percent off Corporate Encryption and Compliance Archiving. Not sure if these services are right for your customers? Here’s a brief overview of each.
Compliance Archiving
Two things to consider when wondering if this is something your clients need or should consider:
1) The name of the product speaks for itself, compliance. ExchangeDefender’s Compliance Archiving service is compliant in accordance with HIPAA, FINRA, SOX, and SEC as well as many other standards that are published by nearly every industry. Compliance works through the Exchange journaling technology; once the service is set up all messages sent and received will be delivered to the compliance service. In addition to meeting requirements of archiving all inbound and outbound mail, Compliance Archiving also covers interoffice email which can help your clients in HR disputes and lawsuits.
2) Don’t worry about storage costs. There are other products on the market similar to ExchangeDefender’s Compliance Archiving, but those products require contracts and additional storage fees forcing you to compromise on the length of storage or which data gets archived. ExchangeDefender provides unlimited storage and stores ten years worth of email beginning on the date the service is set up (p.s. We can also import your old mail as well). Compliance Archiving allows you to offer your clients a long term storage solution in addition to giving them access to years’ worth of emails at the click of a button without a compromise of excessive storage fees or selective archiving of only the “important stuff” because when people get in legal trouble everything becomes important and relevant.
Compliance Encryption
Corporate Encryption is especially important for those clients in the health care, financial and legal field or anyone who is in charge of sensitive information. ExchangeDefender’s Corporate Encryption is able to encrypt based on message patterns (lexicons, dictionaries) as well as preset patterns like social security, credit card and sender/recipient email addresses. If you need to block data leakage on a more sophisticated level, such as custom account numbers, we can help you there as well. Encryption is a product we take extremely seriously and it takes about a week to get all the paperwork, testing and implementation completed so please call us ahead of time to get it all set.

Don’t let this slip by you, you have until July 31st. If you have any questions, please feel free to contact me directly at: Anastasia@ownwebonw.com, or 877-546-0316 x 739.
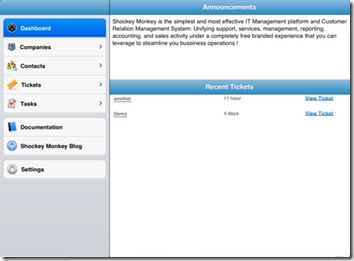
Shockey Monkey Mobile
Over the course of this year we have been working on a slimmed down version of ShockeyMonkey that we’ve been porting to native applications instead of HTML5 or web kit hacks. Native applications offer the benefits of speed and integration with the device that is not possible with web apps running in a web shell. We took advantage of our current open and free API, to integrate these features into the mobile applications and can be extended to leverage the API functionality fully for those of you that want to build custom applications that tie into Shockey Monkey. These slimmed down versions offer a few core features on a much smaller scale, while still allowing you to perform with basic functionality.
Important
Our design and mobile strategy for iPhone, iPad and Android devices is to empower clients with quick access to core functions of Shockey Monkey that are likely to be accessed on the go – client data, company data, tickets, ability to track time and create/complete tasks. Due to the low screen resolution and real estate it is not possible to create very feature rich application that will also be quick to access (imagine the frustration of having to keep on clicking and waiting for menus to show up for some obscure information) and constantly connected to the portal.
We understand some power users may have different needs and want full access to all that Shockey Monkey has to offer – we agree and we hear you! Shockey Monkey can be accessed in it’s full glory from an HTML5 device giving you the exact same experience you have on your desktop on the go. You’ll have to scroll around a bit but that’s the compromise between power and performance.
You can perform tasks such as:
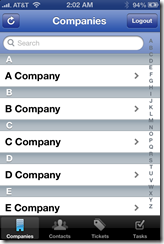
· Viewing companies
· Viewing contacts
· Viewing & Updating Tickets
· Viewing & Updating Tasks
We wanted to keep it simple at first and master the core functionality. After these applications have been in circulation for a while and more people use them, we will gather feedback. We will then work towards eliminate any bugs that are present in the current release. Then expand with additional feature requests, in the future.
Device Support
· iPad
We released the iPad version on 03/01/2013 and it currently available in the ITunes Store (Free).
· iPhone
This was our next release and is in the iTunes store waiting for approval. This version is an updated/enhanced version of the original iPad application.
· Android
We are currently working on this release, it’s very close to being finished and should be published to the Android market place by the end of the month.
· Everything else
HTML5 app is at https://yourportal.shockeymonkey.com/mobile and supports virtually the same feature set as the rest of our native applications.
Hank Newman
VP, Development
hank@ownwebnow.com