ExchangeDefender: Expanding Security Portfolio

Our last webinar announced our strategy for expanding the level of protection we offer to our ExchangeDefender users that goes far beyond just email. Our three-pronged approach will now include software, services, and training. We are best known for our email security service “ExchangeDefender” but as the email threats escalate in frequency and evolve in complexity, it is time to add a software component.
Over the past decade we have been developing Wrkoo (codename: “Shockey Monkey”), a business management solution centered around helpdesk and service delivery. As that product has grown to better manage accountability and task tracking, it became a perfect solution for us to use to help our ExchangeDefender users be more secure. Specifically, ExchangeDefender knows about your preferences and security policies – Wrkoo has the capabilities to help your entire organization work better together to create a more secure environment. You will see this distinction and the advantage in action later this week when we announce the Password Vault.
Our implementation is very simple and straight-forward. Every ExchangeDefender Pro protected organization will get it’s own Wrkoo portal (ex: https://exchangedefendercom.wrkoo.com) absolutely free of charge. All the users in ExchangeDefender will automatically be added to the Wrkoo portal and same login credentials will work on both sites.
As we add business-level features that help improve user security, they will be available via https://admin.exchangedefender.com portal under the Shortcuts dropdown (same place you find your Web File Server, LiveArchive, ComplianceArchive, Encryption, etc) as well as via direct login to the Wrkoo portal. This will help our clients quickly navigate between their files, passwords, archives, and all other services.
ExchangeDefender admin portal has been designed from the standpoint of email security and corporate policy enforcement and it is very quick, efficient, and easy to use. Once you look at securing your business beyond just SPAM filtering, things get complex and importance shifts to communication, training, and overall awareness. These are the areas that Wrkoo shines at through its calendars, tasks, tickets/cases/issues, knowledge base, and the ability to help the entire organization communicate and be on the same page. It really is a perfect medium to help everyone in your business manage their information in a more secure and practical user -friendly way.
Our mission remains the same: to keep you safe online. As the threats evolve and management of compliance, reporting, audits, and training becomes more complicated – our solution is there to help you scale and address those issues without spending more money. ExchangeDefender and Wrkoo are here to make that possible.
Password Security Policy Enforcement & Enhancements
Over the past year we’ve been introducing enterprise security measures to help protect our clients from an increasing volume of attacks. Email is the single most abused gateway for email threats – with 91% of corporate breaches starting through email – and it’s only getting worse.
If you’ve used Yahoo, MySpace, or hundreds of popular free web sites (go to https://haveibeenpwned.com/ to see how/who exposed your data) your credentials and other information is available on the web. Hackers are using these passwords and personal information to guess their way into other sites that haven’t been breached – so if you use the same or similar password (or only change the site id, or one number or letter to make it different) then you’re making it very simple for hackers to get into your account.
And we get it. Dealing with security, passwords, and locking down online services is time consuming. But as the company whose main purpose and mission is to keep you secure – we want to help save you time and make it easier for you to be secure.
For the details on all the stuff we’ve got coming in September, we’d like to invite you to our webinar:
ExchangeDefender Security Upgrade
Tuesday, September 10th, 2019
https://attendee.gotowebinar.com/register/6898777257651237900
In the meantime, we’re going to help our partners and clients not make things “stupid easy” for hackers – by globally resetting ExchangeDefender passwords that are older than 1 year. We’ll do this on September 1st, in a very minimally intrusive way, and for those that don’t use ExchangeDefender on the daily basis (and mainly just release SPAM from quarantines) the password change won’t affect them.
Using an OTP/2FA or VPN services or all the free features that are built into ExchangeDefender to keep you secure is obviously our preferred way but as we’ve noted – the realities of SMB concern for IT security – so we need to try something else. We really hope our partners and clients can take the time to attend the September Webinar, as we believe the stuff we’ve built will help lock down your organization and make security manageable again.
ExchangeDefender Phishing Firewall Support (CSO)
Ever since we committed to ExchangeDefender Phishing Firewall as a core feature in ExchangeDefender, we knew that the biggest user benefit will be a trusted cyber-security expert available as a part of the solution. ExchangeDefender redirects all links that pass through ExchangeDefender through our firewall, giving users that click on a suspicious link in their email more information about the suspicious site – for example, if you clicked on a link in an email from Bank of America and are actually going to a web site in Poland, it might be an issue. But who do you turn to when there is an issue?
ExchangeDefender Chief Security Officer is just a click away and so far we’ve handled over a thousand inquiries from our clients and partners. If you’re looking at a link and you cannot tell why we intercepted and flagged the content, just click on the yellow button and fill out a form.

Within 24 hours you’re guaranteed a response from our team. The turnaround average so far has been just 18 minutes!
What happens on the back-end is actually quite hands-on: first we investigate the original email and compare the context with the link target, location, etc. We then open the link in a sandbox (safe environment without additional network connectivity and no data) to see what sort of information the web site collects and attempts to send. We then rephrase it in a non-techie user-friendly way and help the client out.
We’ve been overwhelmed with both skepticism and compliments as a result – turns out most users do not expect a response and are pleasantly surprised when an actual human emails back with useful information. We’ve gotten compliments on our turnaround time, usefulness of information, saving the user from dangerous content, as well as thankful comments about the frustration that phishing in general creates – as we’ve been fine tuning xdref.com our users are seeing it less and less and when they do see it we are happy to help.
The overall value of the service cannot be overstated – we’ve saved our CIOs, partners, MSPs, IT guys and gals hundreds of hours in investigative work alone. We got our clients a security audit that allowed them to continue to work quickly. Not to mention about all the bad links that likely would have lead to a breach or security compromise – that the users and techs never had to deal with.
P.S. Included in ExchangeDefender Pro at no additional cost. If you’re still frustrating your clients with “training” programs/videos/whitepapers that SPAM filters catch and junk anyhow – stop wasting your clients time and money – ExchangeDefender Phishing Firewall is a better, more effective, more affordable solution.
ExchangeDefender Phishing Firewall (EPF): Scary Truth behind Phishing
ExchangeDefender Phishing Firewall has been a huge success in it’s initial roll out and I wanted to take a moment to bring you up to speed on our progress and our end goal: to eliminate phishing and spear phishing as a threat to our clients. I do not intend to mince words here, this is the #1 threat out there – 90% of all compromises and breeches start with a phishing email. Stopping it, as an email security company, is our #1 job and I’m happy to report that initial results are stunning.
Little bit of a rewind: Until now the most popular way to fight phishing and spear phishing was through “education” – there is an entire cottage industry of supposed “phishing education”, testing, refreshers – and it all revolves around training people to hover over links in Outlook, what not to click, what to read. It will not surprise you that such “training” is practically worthless, but they say that a picture is worth a thousand words so here is our phishing book:
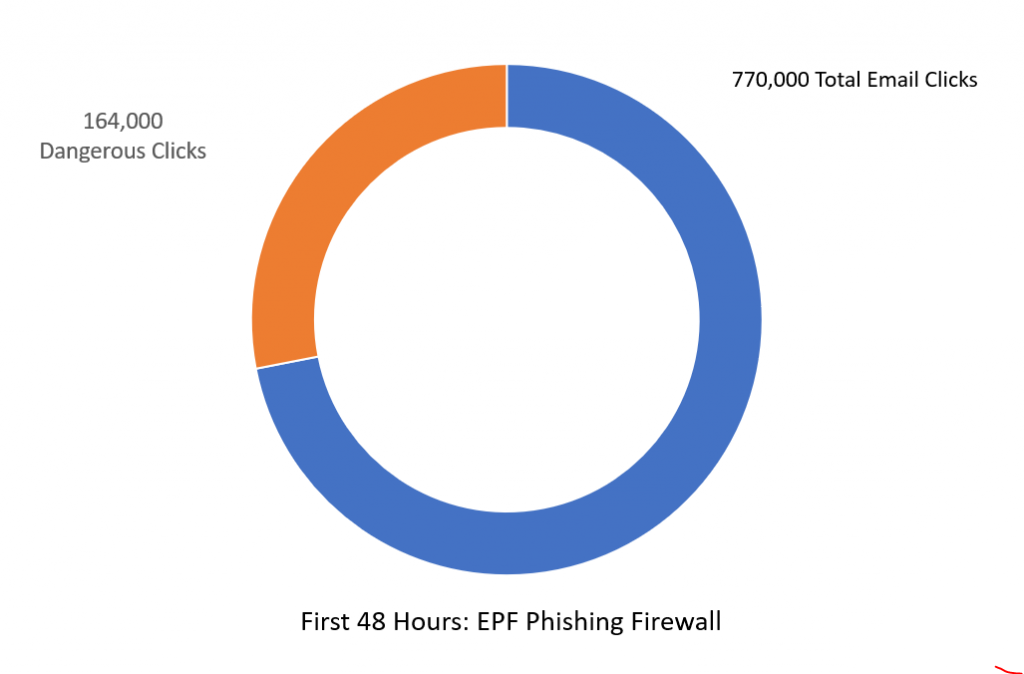
In the 48 hours following 4th of July weekend in United States, dangerous links in the email were clicked on over 770,000 times.
Without ExchangeDefender Phishing Firewall, these links would have redirected our clients to dangerous sites that likely would have lead to a compromise or a security breach. So much for training.
What’s even more telling is that, even with our firewall in place, 164,000 people decided to proceed to a dangerous site anyhow.
If more than 1 out of 5 clicks in your email will take you somewhere dangerous, how well is your training performing?
With ExchangeDefender Phishing Firewall we are enabling companies to setup policies, restrict access, provide intelligence as the user clicks — and we provide logging giving you an idea who attempted to trash your organizations network.
The scary truth behind phishing is that training is only useful in blatantly apparent cases – the kind that will NEVER even get to your inbox. Our SPAM filtering detects dangerous email content and filters it out before it has a chance to get to your Inbox. The stuff that we can flag as dangerous – thanks to user reporting, audits, and look-ahead scanning is far more sophisticated than anything we could pack into a SPAM filter – and it gives your users real intelligence on what they are about to click on. You cannot expect users to remember all their training and to be a web security analyst – their job is acting on the email.
Our job, is making sure the emails get to them clean and free of dangerous malware. Once they click on the links in the email – we are going one step ahead – and leveraging our industry relationships (data feeds and infosec sharing of dangerous content) to make sure you know exactly what you’re clicking on.
Phishing is immensely profitable and far more effective than any other form of hacking – the user literally clicks and gives the hacker the keys to the network – and our ExchangeDefender Phishing Firewall helps remove the danger and reduces phishing to merely an annoyance.
The numbers speak for themselves.
Sincerely,
Vlad Mazek
CEO
ExchangeDefender
ExchangeDefender Phishing Firewall – Report Issue
ExchangeDefender Phishing Firewall continues to impress in terms of performance and user engagement – it’s catching dangerous content and keeping users safe from phishing attacks that often result in security compromises and breaches. Phishing accounts for over 90% of IT compromises, and as we’ve written before more than 1 out of 5 links our clients click on have lead them somewhere dangerous. With those numbers it’s clear to see why hackers are relying on phishing as the first and most effective form of attack – people will click on anything!!! And as intrusive as EPF seems to some (thank you for your feedback), our development team has been working overtime since the launch to make ExchangeDefender Phishing Firewall out of the way when it should be, and in your face when something dangerous shows up.
The goal of ExchangeDefender Phishing Firewall is to keep you safe from potentially dangerous sites and out of the way the rest of the time. You can keep up with our Dev fixes over at https://www.anythingdown.com and keep sending us your feedback. We love to hear it and we love improving the service so it can help keep you and your business safe. We also like to hear what you want us to add to the service that would make it more valuable. One such piece of feedback helped build a “Report Issue” feature:
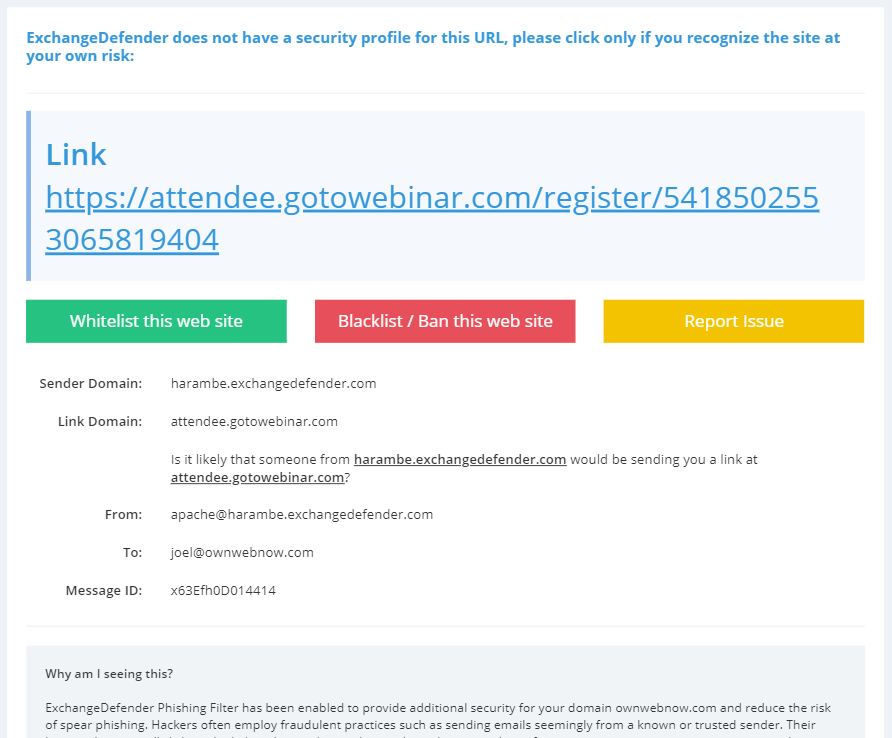
If you click on something that you don’t recognize and you can’t tell what it is – DO NOT CLICK ON THE LINK – we are here for you. Our security concierge will open the link in an isolated virtual environment and see what kind of data is being sent back-and-forth. You will get a response, generally within minutes, with either a thumbs up or thumbs down. How cool is that?
Keep the suggestions coming, we love making ExchangeDefender Phishing Firewall the key part of your defense from phishing.
Phishing Firewall: Should I click on that link?
It is our pleasure to introduce you to the ExchangeDefender Phishing Firewall support services. While the launch of the XDPF has been rocky, we’ve received nothing but glowing reviews about it and the potential behind it to solve other email related issues (more on that in the webinar). Now that most of the dust is settled, we’re moving on to expanding this service to better serve and protect our users and the first feature out of the gate is the most obvious question a user would ask their IT/security person:
“Is this link safe to click on?”
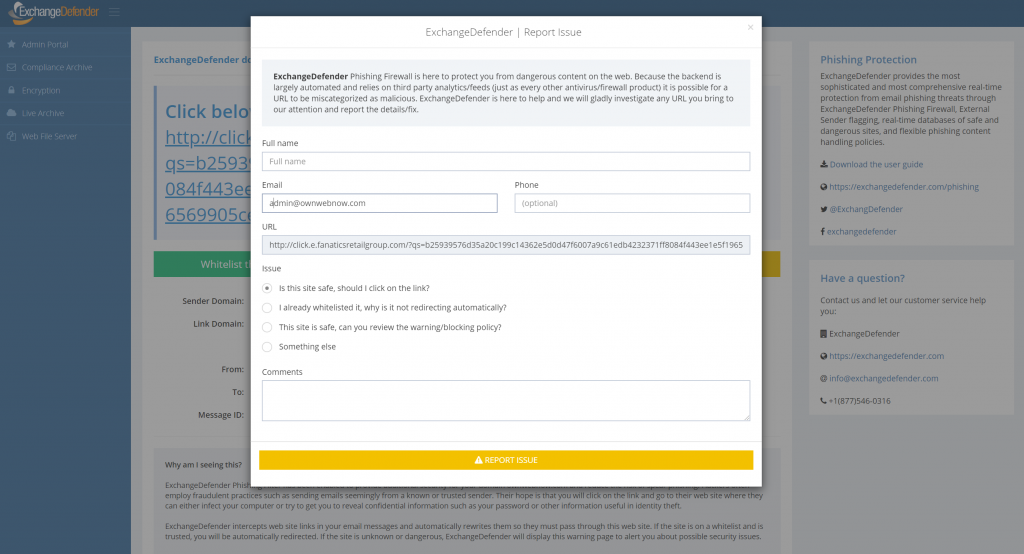
Prior to ExchangeDefender Phishing Firewall deployment, nobody would even think of such a question. You clicked, and if you clicked on something malicious, boom you’re pwn3d. Now you’re presented with the link, the path, and you suddenly have a choice to make: “Do I trust this site?” – well, sometimes it’s hard to guess and we’re here to help. When you click on an HTML link, you will be taken to the ExchangeDefender Security Center and there will be a new yellow button there labeled “Report Issue”:
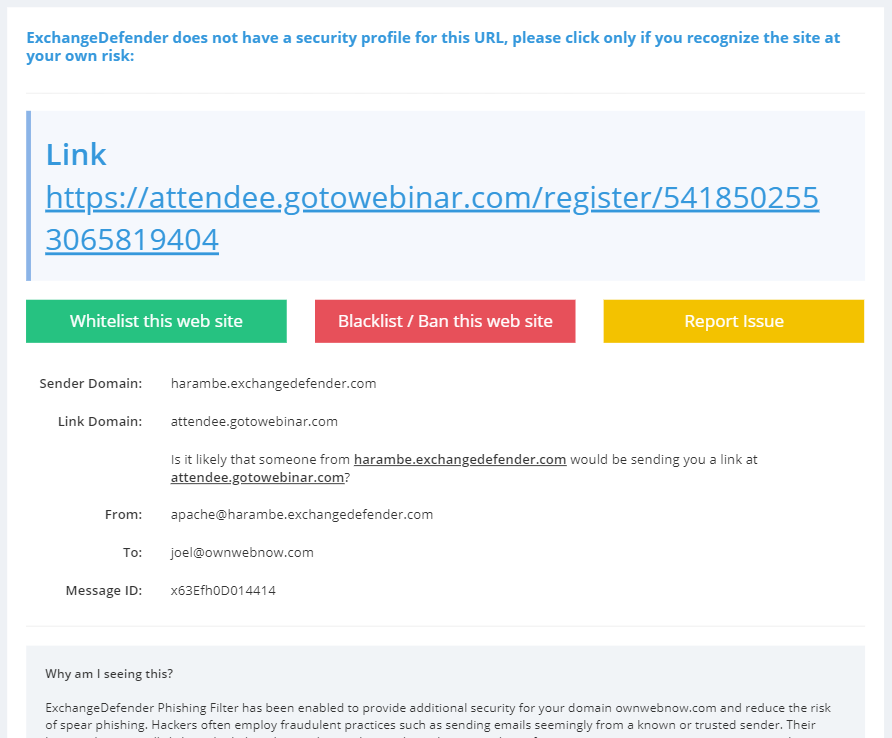
If you click on the yellow button you will be presented with a form to provide additional comments and contact information. After you provide the minimal required information, a service request will be sent to a human being at ExchangeDefender that will evaluate the link for you:
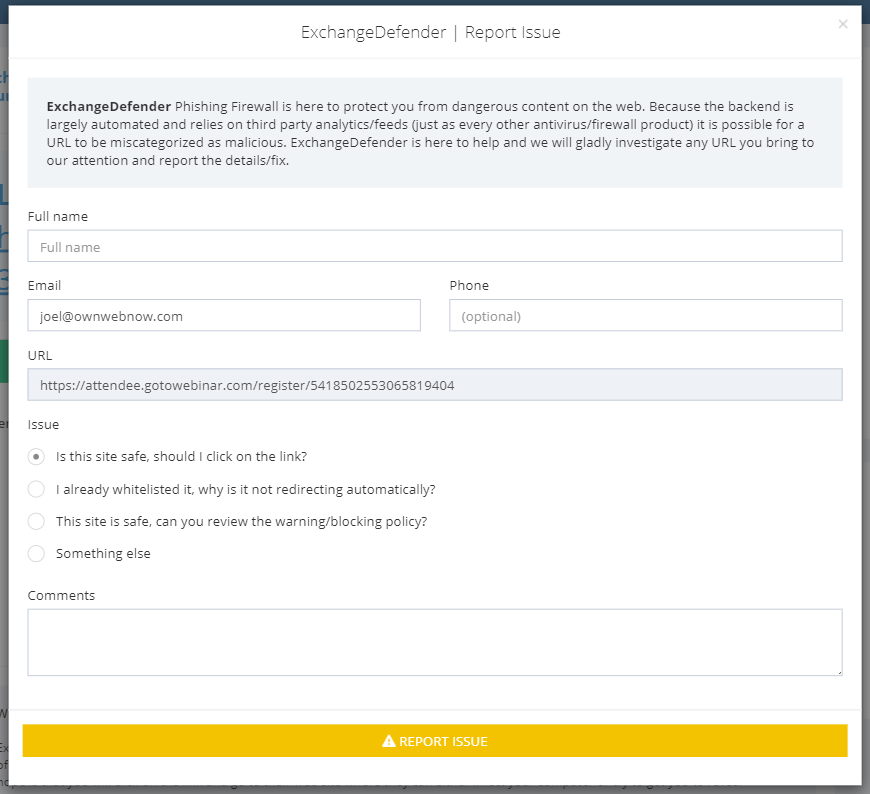
We will basically look at the link and the email data (sender, charset, SPAM data, reputation) as well as the link destination. The link will be opened in a virtual sandbox environment and we will look for any obvious payload that is automatically downloaded or data requested from the browser. We will then report back to you in an email within 24 hours and let you know what we found.
Obviously, we will also be using the same form for any support or issue management, basically setting up the ExchangeDefender Phishing Firewall as a managed, supported, and facilitated service end-to-end.
We will be discussing this feature in far more detail during the webinar on July 10th, 2019: https://register.gotowebinar.com/register/5418502553065819404 but in general terms this is a huge commitment to us that requires us to be available as a Security Officer whenever our clients need us. As a result of managing both the email and the web security incidents, we now have far more data and reputation information that can rely on to help secure our clients in near real-time. As it becomes harder and harder to know who to trust, businesses need security expertise and analysis provided on demand so they can get back to work – phishing is far too profitable and as the #1 attack vector leading to breaches and compromises, it is only going to get worse. With ExchangeDefender, you have a trusted partner that is there to help beyond just another automated security layer, our power is in the people.
New look for ExchangeDefender SPAM Release & Re-directions
It’s been about a decade since our last face-lift to the end-user facing part of ExchangeDefender – suffice to say, lot’s of cool new things are possible with the web technology that wasn’t possible in the past. So, allow me to introduce you to the ExchangeDefender Security Center!
As of Thursday, June 27th, when you attempt to release a SPAM message,
you will see our new security center:
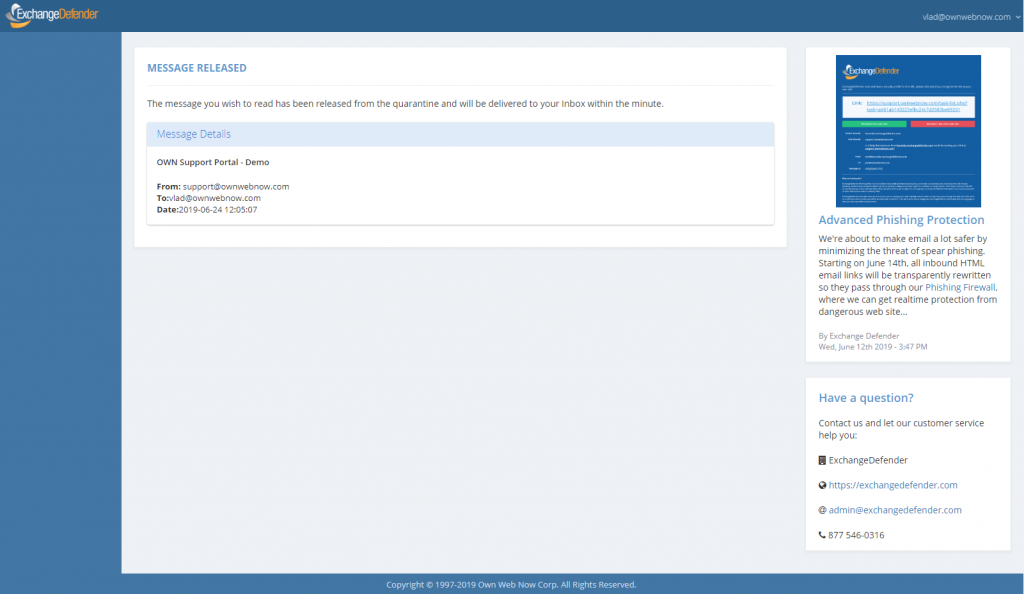
Of course, yours will look a little different. If you have ExchangeDefender from a service provider, it may have their color scheme. You can still upload your own logo (at https://admin.exchangedefender.com).
The idea here is to help connect our self-service portals https://www.exchangedefender.com/ss, our chat, our alerts, and documentation into one spot so when an issue comes up we can help the end user right then and there.
Remember that all of this stuff is data driven, so if you’re one of our partners we encourage you to put up your own announcements, deploy the XD NOC for your organization so your branding is preserved, work with our account managers, etc.
Going forward, this will be the default view for unauthenticated connections – so WFS, Encryption Download, SPAM release, and the Phishing Firewall Redirect.
P.S. How do IP restrictions play into this? They don’t. If you have ExchangeDefender enabled only for Trusted Devices and admin portal locked down to the enterprise IP range, the site will still allow the user to release SPAM from the quarantine no matter where they are (think mobile device access). For other functionality, once they click on Login the same 2FA/OTP/Known Device/IP Restrictions are in play.
ExchangeDefender PTR & RBL Whitelisting

ExchangeDefender is opening a wider beta test of our whitelisting functionality, which allows IT Solution Providers to whitelist sender mail servers that have broken DNS (missing PTR, mismatched A/PTR records) and poor sender reputation (hosts listed on multiple RBL blacklists).
If you have a sender you would like to whitelist against these essential network tests, please open a ticket at support.ownwebnow.com with subject “Whitelist PTR/RBL: IP Address” and provide as much information in the ticket so we can accommodate this specific request. Only hard non-negotiable rejections to whitelist will be for unknown address space and dialup/consumer cable IP addresses (because due to their nature those are typically dynamically assigned address spaces that shouldn’t be relaying mail at all, they should be using their ISP mail server provided smarthost)
Requests will be reviewed and either approved (and enrolled) or rejected within 24 hours by our CSO.
Background: Inability to previously whitelist broken DNS and dynamic IP address space is rooted in our mission statement. We are here, beyond everything else, to help secure the email. We know our partners, IT Solution Providers, VARs, MSPs, etc do not have the skill set, the time to properly research underlying issues, enough data and statistical models to evaluate sender IP reputation, or even the incentive to discern how big of a security threat and compromise a specific IP address with broken DNS or poor reputation may pose to your client.
In fact, you pay us to worry about those things and keep your clients secure. But, sometimes clients like to think they know better than their technology experts, generally accepted security standards on the Internet, and ExchangeDefender. And the client is always right. But, when they get infected attachments, broadcast storm, password dumps, or other security compromises because they insisted on lowering their security – then ExchangeDefender is on the hook for securing them. And we don’t get to say “told you so” nor do we have any rapid means to fix the issue.
Since my retirement, all of those hard-line policies designed to keep clients safe beyond whatever “specific business case requirement” they may have, are slowly going away. Good news for the client, good news for the partners. Good news for us, because going forward we will start providing Email Security Engineering services – so when you get a security compromise or an usual issue and you’ve asked us to compromise your security – we will be able to address the issue on your behalf.
I choose to look at this as a positive – we will help our clients meet their business needs and get the mail they desperately need – and if something breaks we will be there to help assist with the cleanup (for a fee, of course). This, among many other service related things, is just the part of the ExchangeDefender being more responsive and service oriented when it comes to our clients demands as opposed to our expert opinion as a security policy.

New Feature: ExchangeDefender Announcements
ExchangeDefender Announcements
As you’ve probably noticed, our feature development has really picked up in 2018 and we have an even more aggressive product roadmap for 2019. To help make sure everyone is on top of all the new features and that our partners (MSP/VAR) have the best possible way to keep all of our clients informed of the new features, we’re happy to announce the Announcements feature!
Starting in late February 2019, our service providers and CIOs alike will have the ability to post announcements that will be featured prominently on the ExchangeDefender admin login page, inside the user control panel, and in the domain/org control panel. As you can imagine, this feature has a lot of flexibility to help you efficiently target the right organizations and users.
Announcement Feature Highlights:
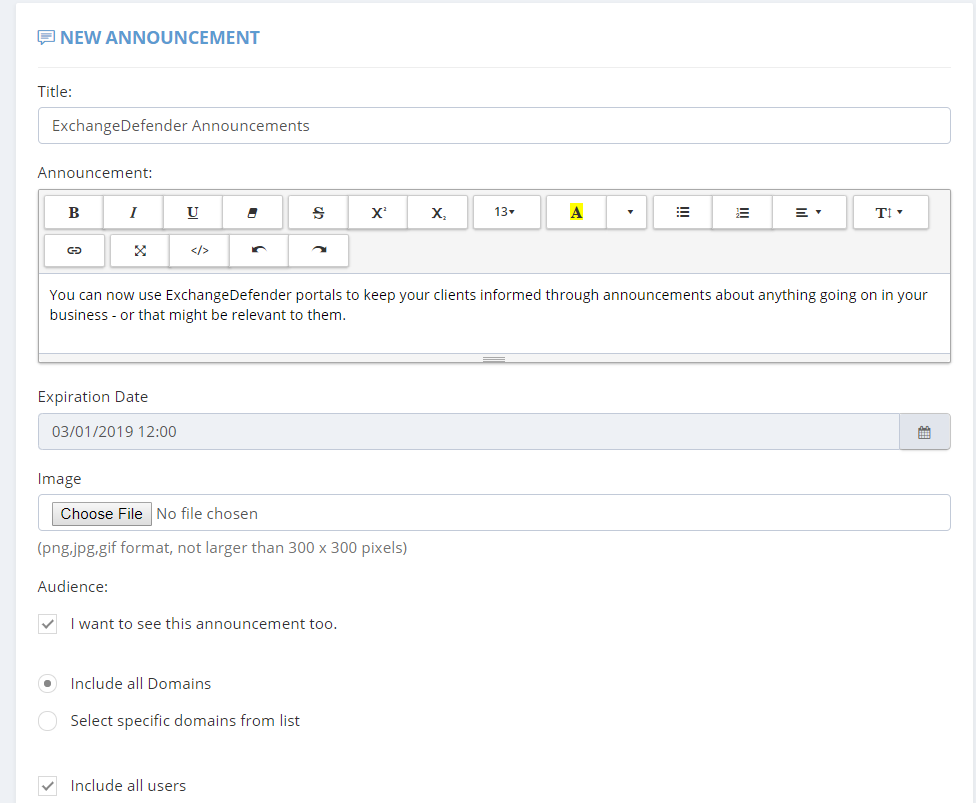
– Announcement title and announcement contents can include HTML and you can even insert a picture for each.
– You can set the announcement expiration date so that the announcement doesn’t show up after a certain date. This is great for sales promotions, webinar registrations, etc.
– You can scope the announcement: It can be global (for all of your domains) or it can be scoped down to a list of domains you choose. As most of our MSPs manage different kinds of organizations, one-size-fits-all announcements rarely work and this feature can help you solve that problem by targeting each organization specifically.
– I want to see this announcement too: If you’re in a larger organization you likely have personnel that is responsible for different departments or companies. Because announcements are visible on the login page of your portal as well as control panels for service provider, domain/org, and end users you have the ability to not show end user announcements to your IT and management staff.
– Include all users: You can even write specific announcements that are targeted at end users.
As ExchangeDefender gets bigger and as the complexity and service portfolio grows, we need to help our partners and CIOs communicate the new ExchangeDefender features more efficiently. Since you control your announcements it is up to you if you use it for ExchangeDefender related stuff or if you use it for your own promotion or if you delegate it to your companies to use it as another outlet to broadcast organization-specific but important news to everyone.
Most ExchangeDefender users interact with the service daily so you have a perfect (captive) spot to reach them about a product they are already interacting with – instead of having it burried in an email newsletter that they likely won’t read. This has been among the most demanded MSP features for years and we’re happy to deliver something with enough power and flexibility that will make both your tech/support people happy (so they can address possible support issues) as well as marketing/sales (so they can better target their message). You can only display up to two (2) announcements at a time though so the only bad news here is that you’ll have to prioritize.
ExchangeDefender Exchange Account Lockout
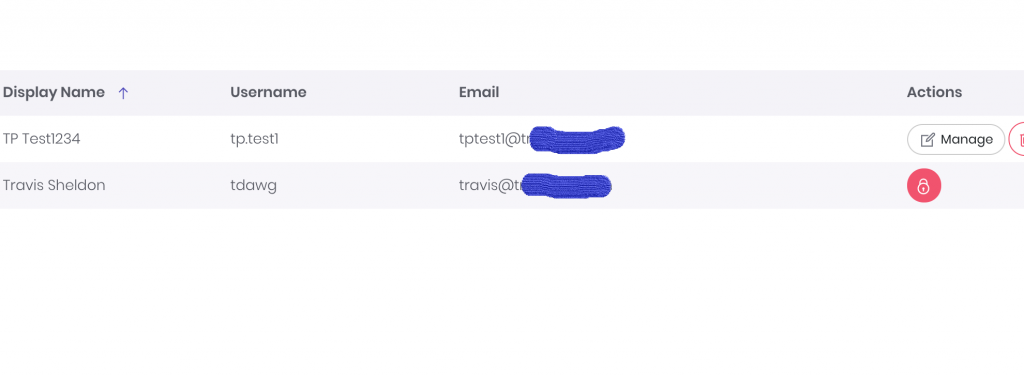
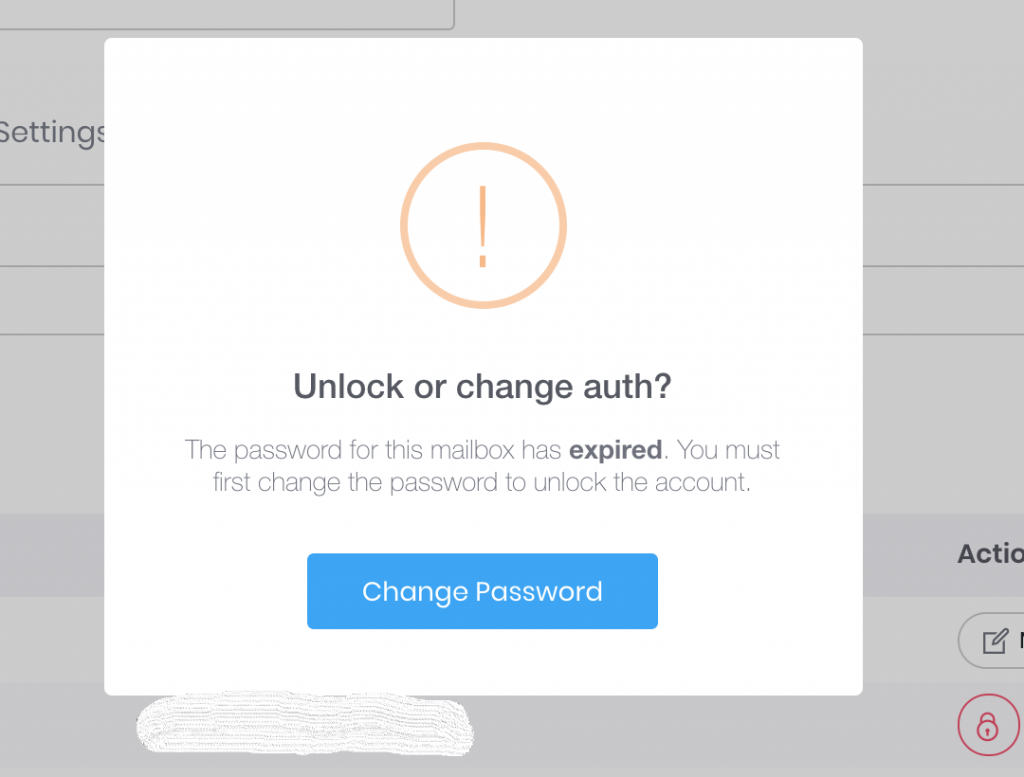
ExchangeDefender is relieved to announce the availability of automated account lockout notifications. Our clients now have the ability to automatically locate, secure, and unlock email accounts that have been locked down due to too many bad login attempts.
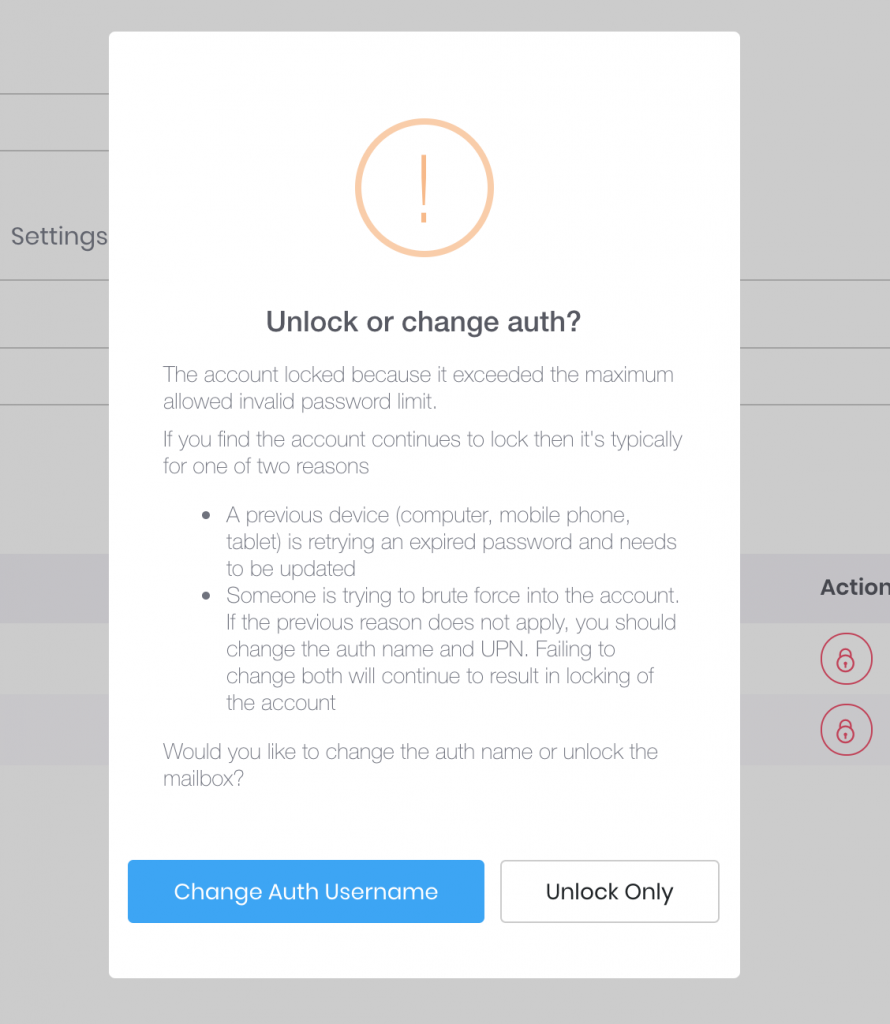
You will now notice a red lock icon next to any accounts that have been locked out and you can choose how to proceed in terms of restoring account access:
Password hacking and guessing is rampant, and has only been getting worse through 2018. Thankfully, we’ve automated the process of unlocking and changing authentication credentials in 2019.
However, there is a special case in which just “Unlock Only” option may be the best.
Suppose you have a power user that has a desktop at work, at home, a laptop or two, 2 iPads, iPhone, Galaxy S9 and a miscellaneous other device that is set to sync mail every minute. Totally not talking about our CEO. But suppose that is the case and you just changed the password – well if all these other devices are trying to authenticate with the old password you may actually trip your corporate policy for the unlock limit and lock the account again.
We hope this automated system will save our partners a ton of time and make managing security and security incidents a breeze. We wish we could have delivered this much sooner but as anyone involved in cybersecurity will tell you, priority #1 is always mitigation of the issue (which we’ve done through all our Exchange 2016 UI and management discussed in our webinars).
This feature will go live later this week (Feb 21, 2019) – please give us feedback and suggestions on what more we can do to give you more power or save you time.