How to Spot & Avoid the Latest DocuSign Scam

Cybercriminals are getting craftier, and one of their favorite new tricks is impersonating trusted services like DocuSign. If you’ve recently received an email urging you to sign a document or verify your account, think twice before clicking! The latest wave of DocuSign email scams is designed to steal your personal information and compromise your security.
How the DocuSign Email Scam Works
Scammers send fake emails that appear to be from DocuSign, using official-looking branding and urgent messaging. Here’s how the scam typically unfolds:
- Fake Email Notification – You receive an email that looks like it’s from DocuSign, requesting you to review or sign a document.
- Urgency & Pressure – The email often claims the document requires your immediate attention, creating a sense of urgency.
- Malicious Links – Clicking the link redirects you to a fraudulent website that mimics DocuSign’s login page.
- Credential Theft – If you enter your login details, scammers steal them to access your DocuSign or other linked accounts.
- Malware Installation – Some scams include attachments or links that, when clicked, install malware on your device.
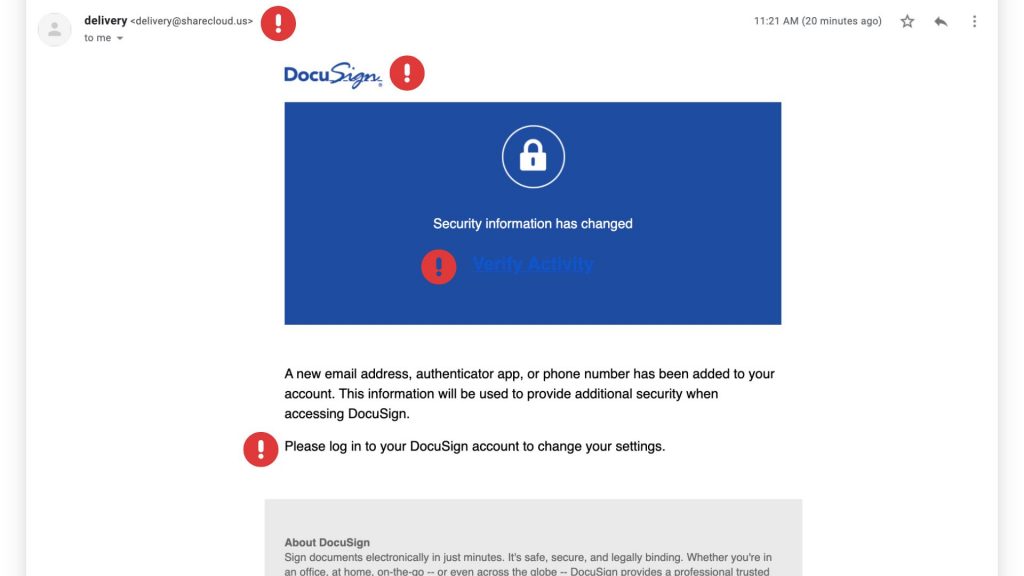
Red Flags to Watch For
These scams can be convincing, but there are a few telltale signs that can help you identify them:
✔ Suspicious Sender Address – Official DocuSign emails come from @docusign.com or @docusign.net, not random or misspelled domains.
✔ Unusual Language or Errors – Many phishing emails contain typos, grammatical mistakes, or odd phrasing. Look for fake logos as well!
✔ Unexpected Requests – If you weren’t expecting a document, verify with the sender before opening anything.
✔ Fake Links – Hover over any links in the email (without clicking) to see the actual URL. If it’s not docusign.com, don’t trust it.
✔ Generic Greetings – Scammers often use “Dear Customer” instead of your actual name.
How to Stay Safe
Protect yourself and your business from falling victim to these scams by following these best practices:
🔹 Verify Directly – Instead of clicking email links, go to www.docusign.com and log in to check if a document is waiting.
🔹 Enable Multi-Factor Authentication (MFA) – Adding an extra layer of security can prevent unauthorized access to your account.
🔹 Report Suspicious Emails – If you receive a fraudulent DocuSign email, forward it to spam@docusign.com and then delete it.
🔹 Keep Security Software Updated – Use up-to-date antivirus and security software to detect and block phishing attempts.
🔹 Educate Your Team – Ensure employees know how to recognize and avoid phishing emails.
Texas Strengthens Cybersecurity with New State-Level Command Center

In February 2025, Texas Governor Greg Abbott announced the creation of the Texas Cyber Command, a state-level initiative headquartered in San Antonio.
This command center aims to enhance the state’s ability to anticipate, detect, and prevent cyberattacks, leveraging local expertise from institutions like The University of Texas at San Antonio. The Texas Cyber Command will collaborate with state universities, Regional Security Operation Centers, and various local and state agencies to create a unified defense against cyber threats.
Key objectives include promoting cybersecurity awareness, conducting simulation exercises, and providing forensic analysis for post-attack investigations. This development underscores the growing importance of state-level initiatives in safeguarding digital assets and infrastructure.
For a visual overview of the Texas Cyber Command, you can watch the following video:
ExchangeDefender WebUI: New Features & Enhancements! 🚀

As mentioned in the previous blog post, our new Web Services infrastructure is coming with a ton of new features, new UI, and new faster way of rolling things out that can help benefit & secure everyone.
In the previous post we discussed the scope of the update – rolling up over a decade and a half of legacy features, hacks, services, automations – all into a modern web services world where we can start rolling out features faster.
The biggest problem we are trying to solve now is how to quickly deploy efficient solutions. Most of the development time isn’t in actual coding or rollouts, most of the time is in design and confirming that users are able to quickly and effortlessly rely on them. Past service design was built over the years, as we helped our clients mitigate one security problem after another. Restructuring it will make things far smoother and easier to use.

Note the three single icons next to teach message checkbox. Tapping them on a touchscreen interface or with your mouse triggers the action to Release, Allow Sender, and Review. Icons aren’t very intuitive though – so we see people click on the checkbox and scroll all the way to the top to release a message.

Consider a new modern UI where icons become buttons. Would that change user behavior? Good news is that this will no longer be subject to opinion or guess but hard data as every element of our page will give us actual feedback about how the new feature is being used and how it’s performing:
By leveraging actual usage statistics and better insight on the backend, we can rely on AI to provide a far better level of service with a way faster delivery. In other words, we can respond to security problems faster.
Blue Cross Blue Shield Phishing Scam on the Rise

Blue Cross Blue Shield (BCBS) phishing emails are fraudulent messages designed to trick recipients into providing personal information, such as login credentials, Social Security numbers, or financial details. These emails often appear to come from BCBS but are actually sent by scammers aiming to steal sensitive data.
Common Tactics Used in BCBS Phishing Emails:
- Fake Account Alerts – The email may claim there’s an issue with your BCBS account, such as suspicious activity or a need to update your information.
- Urgent Payment Requests – Scammers may say you owe money for coverage or claim a payment failed, urging you to click a link.
- Fake Benefits or Refunds – Some phishing emails promise refunds, benefits, or changes to your health plan, requiring you to enter personal details.
- Malicious Links or Attachments – These emails often include links that lead to fake BCBS login pages or attachments containing malware.
- Spoofed Email Addresses – The sender’s email address may look official but often has subtle misspellings or extra characters (e.g.,
support@bcbs-secure.cominstead ofsupport@bcbs.com).

How to Spot and Avoid BCBS Phishing Emails:
✅ Check the Sender’s Email – Verify the email address carefully. Official BCBS emails come from legitimate domains.
✅ Look for Typos & Grammar Mistakes – Many phishing emails contain odd phrasing, spelling errors, or unprofessional formatting.
✅ Hover Over Links (But Don’t Click!) – Hover your mouse over links to see the actual destination URL. If it looks suspicious, don’t click.
✅ Never Enter Personal Info via Email – BCBS will never ask for sensitive data like passwords, Social Security numbers, or banking details via email.
✅ Contact BCBS Directly – If you’re unsure, call BCBS using the official number on their website, not the one in the email.
What to Do If You Receive a BCBS Phishing Email:
📌 Do NOT Click on Any Links or Attachments
📌 Report the Email – Forward phishing emails to BCBS’s fraud department or report them to the FTC at reportfraud.ftc.gov.
📌 Delete the Email Immediately
📌 Monitor Your Accounts – If you accidentally clicked a link, change your BCBS password immediately and watch for unauthorized activity.
Always stay cautious—cybercriminals keep improving their scams, but with awareness, you can protect yourself from falling victim! 🚨
Smishing: The Text Message Scam You Need to Know!

Cybercriminals are always looking for new ways to trick people, and one of the latest and most dangerous scams is smishing. But what exactly is smishing, and how can you protect yourself? Let’s break it down in simple terms.
What Is Smishing?
Smishing (a combination of “SMS” and “phishing”) is a type of cyberattack where scammers send fake text messages to trick people into giving up personal information. These messages often pretend to be from legitimate sources like banks, delivery services, or even government agencies.
The goal? To get you to click on a malicious link, call a fake customer service number, or reveal sensitive details such as passwords, credit card numbers, or Social Security numbers.
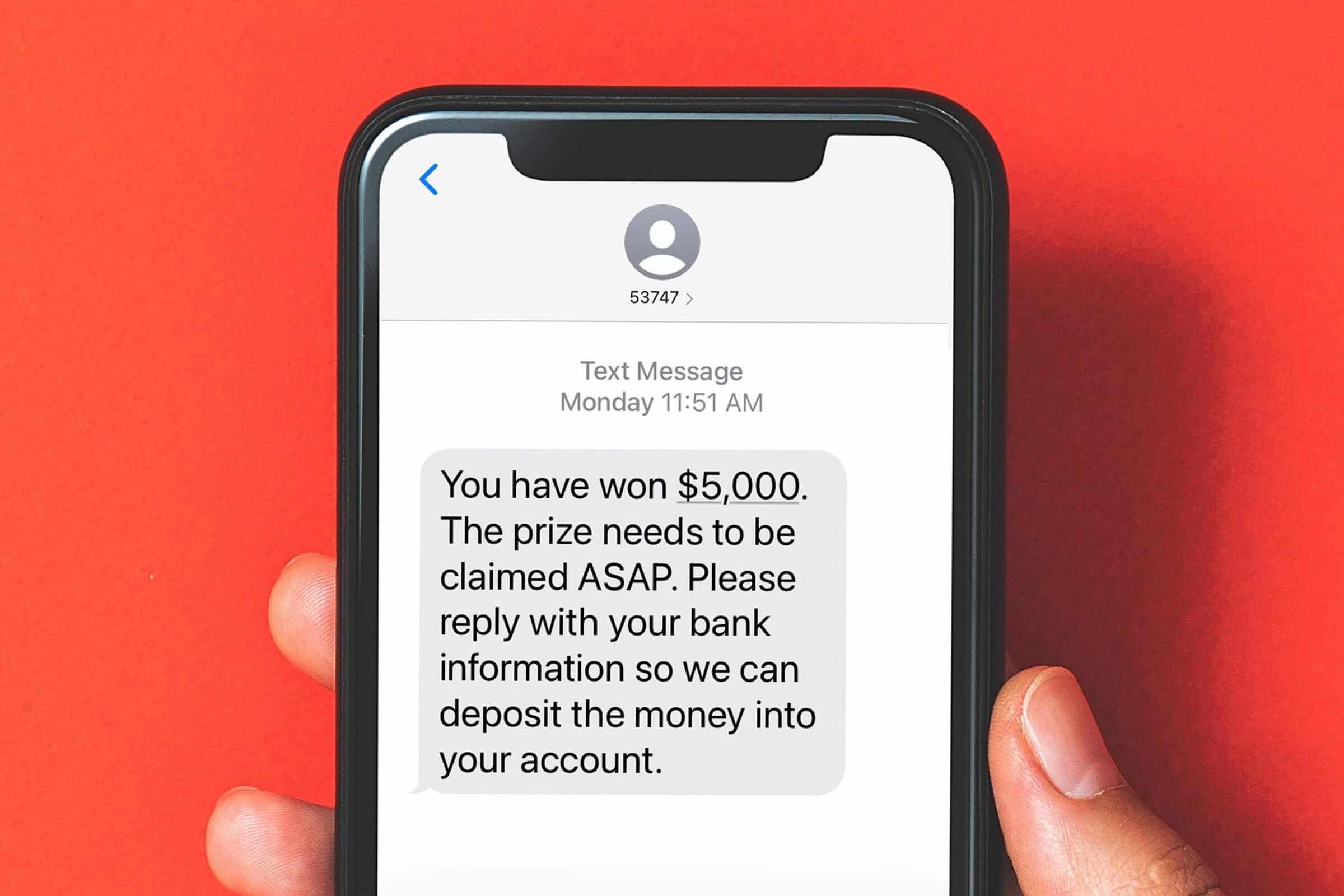
How Does Smishing Work?
Smishing messages typically create a sense of urgency, making you feel like you must act immediately. Here are a few common examples:
- Bank Alerts: “Urgent: Your account has been compromised. Click here to verify your identity.”
- Delivery Notifications: “Your package is delayed! Click this link to confirm your details.”
- Government Scams: “You are eligible for a tax refund. Claim it now by following this link.”
Once you click on the link, you might be taken to a fake website designed to look like a real one. If you enter your information, it goes straight into the hands of cybercriminals.
How to Protect Yourself from Smishing Attacks
- Don’t Click Links in Unsolicited Messages – If you receive a text from an unknown sender with a link, be cautious. Go directly to the company’s website instead.
- Verify the Sender – If a message appears to be from your bank or another trusted organization, contact them directly using a verified phone number.
- Look for Red Flags – Watch out for poor grammar, strange URLs, and urgent language designed to pressure you into acting quickly.
- Use Security Features – Many mobile carriers offer spam message filtering. Enable these features to reduce unwanted messages.
- Report Suspicious Messages – Most mobile carriers allow you to report spam texts by forwarding them to 7726 (SPAM).
Smishing is on the rise, but you don’t have to fall victim to it. By staying informed and practicing good cybersecurity habits, you can keep your personal information safe. If you’re ever unsure about a message, always take a moment to verify before responding.
For more cybersecurity tips and updates, stay tuned to the ExchangeDefender blog!
How to Report an Amazon Phishing Email (Step-by-Step Guide)

Have you received a suspicious email claiming to be from Amazon? Phishing emails try to trick you into giving away personal information, such as your login details or payment info. It’s important to recognize and report these scams to protect yourself and others. Here’s how to do it:

1. Identify a Phishing Email
Phishing emails often:
✅ Ask for personal or payment information.
✅ Have urgent or threatening language (e.g., “Your account will be suspended!”).
✅ Contain misspellings or strange formatting.
✅ Include fake Amazon links (hover over them to check the real URL).
2. Do NOT Click Any Links
If you suspect an email is fake:
❌ Don’t click on links or download attachments.
❌ Don’t reply or enter any personal information.
❌ Don’t call phone numbers listed in the email.
3. Report the Phishing Email to Amazon
📧 Forward the suspicious email to stop-spoofing@amazon.com.
🗑️ After forwarding, delete the email from your inbox.
4. Secure Your Amazon Account
🔑 Change your Amazon password if you accidentally clicked on anything.
🔐 Enable two-step verification for extra security.
🛑 Check your account for unauthorized purchases or changes.
By reporting phishing emails, you help protect yourself and others from online scams. Stay alert and stay safe! 🚀 Looking for phishing protection for your business? Go for ExchangeDefender, start with a 14-day free trial!
ExchangeDefender Web Services Update

ExchangeDefender Web Services Update has concluded and the new infrastructure is handling 100% of the ExchangeDefender traffic. So far the new platform is performing exactly as expected and we have already closed several minor bugs. Overall, we are extremely happy at ExchangeDefender today!
We want to take a moment to high-five ourselves and highlight three main areas where our clients and partners are going to benefit from this investment:
1. Enhanced Security
With the changes in the development backend, our platform now utilizes the latest security patches and modern language features, significantly reducing vulnerabilities and providing a more robust threat defense.
Our old platform was also rock-solid in terms of performance and security, but that secure-by-design methodology forced us to reverse-engineer as well as design and manage everything from input validation to report routing. Modern web services take care of these routine things allowing us to spend more time on policy development.
2. Improved Performance
The new infrastructure supports faster processing and is optimized for global operations allowing us to deliver a more responsive and reliable service.
You’ve already seen a hint of this in the ExchangeDefender LiveArchive relaunch as a standalone data vault for cloud operations. By breaking up our infrastructure into microservices we’re able to deliver edge operations closer to where our clients are, we can keep data more securely in your local data geography, and we can delegate away control as required.
3. Features Shipped Faster
By moving away from legacy code and internal systems/plugins for policy and protocol enforcement, we can dedicate more of our development cycles to policies and training that will keep your organization more secure. You will be able to benefit from the latest improvements and security innovations while we deliver more.
Thank you for filling out our survey, if you haven’t done so please take a moment to tell us where we can help. We have intentionally dedicated a large window to bringing the new web service infrastructure online so we do have spare cycles to help alleviate some pain points our clients are experiencing. Please take a moment to fill out our survey
We are hard at work on the new User Interface, we’re nearly ready for the public launch of our Phishing platform, all sorts of goodies are heading your way so once again – thank you for your business and your faith in us to deliver safe and secure email to your organization.
Sincerely, Vlad Mazek CEO ExchangeDefender
What All Phishing Scams Have in Common

Phishing. We hear about it constantly, but with new variations popping up all the time, it can be hard to keep track. While the delivery methods and specific lures might change, there’s a common thread that runs through every single phishing scam. Understanding these core elements is key to protecting yourself and your information.
At ExchangeDefender, we’re dedicated to helping you stay safe online. So, let’s break down the common characteristics that define all phishing attempts.
1. The Art of Deception: Impersonating Trust
The foundation of any phishing scam is deception. Scammers meticulously craft their messages to appear as if they’re coming from a trusted source. This could be:
- Big-name companies: Think PayPal, Amazon, Microsoft, or major banks. Scammers often use logos, branding, and even copy website layouts to create a convincing facade.
- Government agencies: The IRS, Social Security Administration, and other government bodies are frequently impersonated to instill a sense of authority and urgency.
- People you know: Scammers might spoof email addresses or social media profiles to impersonate colleagues, friends, family members, or even your boss.
The goal is to trick you into believing the message is legitimate, lowering your guard and making you more susceptible to their tactics.

2. The Pressure: Creating Urgency and Alarm
Once they’ve established a false sense of trust, scammers introduce a sense of urgency or alarm. This is designed to pressure you into acting quickly without thinking critically. Common tactics include:
- Account alerts: Claiming your account has been compromised, suspended, or limited.
- Security breaches: Warning of a data breach or security incident that requires immediate action.
- Missed payments or deadlines: Threatening late fees, service interruption, or legal action.
- Limited-time offers or prizes: Luring you with the promise of a reward if you act fast.
Scammers hope to bypass your rational thinking and trigger an emotional response by creating a sense of urgency, leading you to make a hasty decision.
3. The Hook: Requesting Information or Action
The final piece of the phishing puzzle is the hook – the specific action the scammer wants you to take. This usually involves:
- Clicking a malicious link: These links lead to fake websites designed to steal your login credentials, financial information, or install malware on your device.
- Opening an infected attachment: Attachments can contain viruses, ransomware, or other malicious software.
- Providing personal information directly: Scammers might ask you to reply to the email with your username, password, Social Security number, or other sensitive data.
The hook is the culmination of the scam, the point where the scammer attempts to extract valuable information or gain unauthorized access to your systems.
Staying Safe: The ExchangeDefender Approach
At ExchangeDefender, we believe that education is the first line of defense against phishing attacks. By understanding these three core elements – deception, urgency, and the hook – you can significantly reduce your risk of falling victim.
Here are a few key takeaways:
- Be skeptical of any unexpected communication, especially those requesting personal information or urging immediate action.
- Always verify the sender’s identity through a separate communication channel.
- Never click links in suspicious emails. Instead, type the website address directly into your browser.
- Enable multi-factor authentication whenever possible for an extra layer of security.
By staying vigilant and informed, you can avoid getting hooked by phishing scams and protect your valuable information. #cybersecurity #phishing #scams #onlinesafety #exchangedefender

