Are the BCBS settlement emails legit?

The recent Blue Cross Blue Shield (BCBS) settlement has led to a wave of emails notifying individuals about potential compensation. While many of these messages are legitimate, cybercriminals are using this as an opportunity to launch phishing scams. Here’s what you need to know to protect yourself.
What Is the BCBS Settlement?
BCBS agreed to a $2.67 billion settlement in an antitrust lawsuit alleging the company engaged in anti-competitive practices. Individuals or entities that had BCBS health insurance or administrative services between February 2008 and October 2020 may be eligible for compensation.
The official settlement administrator has been sending notifications via email and mail. Legitimate emails come from Notice@BCBSsettlement.com, and the official website is www.BCBSsettlement.com.
How Scammers Are Exploiting the Settlement
Cybercriminals are taking advantage of this widespread settlement by sending fraudulent emails that:
- Contain suspicious links, such as those prompting users to “request an electronic debit card”
- Use convincing BCBS logos and branding to appear legitimate
- Request personal or financial information
Users on forums like Reddit have reported phishing attempts disguised as official settlement notifications. Clicking on these fake links can lead to identity theft, malware infections, or financial fraud.
How to Protect Yourself
- Verify the Sender – Legitimate emails will come from Notice@BCBSsettlement.com.
- Avoid Clicking Links – Instead of clicking email links, visit the official website directly by typing www.BCBSsettlement.com in your browser.
- Contact the Official Source – If you’re unsure, reach out to the settlement administrator via info@BCBSsettlement.com or call (888) 681-1142.
- Use Email Security Solutions – A robust security tool like ExchangeDefender PRO can help filter out phishing emails before they reach your inbox.
Stay One Step Ahead with ExchangeDefender
With the rise of sophisticated phishing attacks, businesses need reliable email security solutions to prevent scams like these. ExchangeDefender PRO offers advanced phishing detection, real-time email filtering, and security awareness training to keep your organization safe from evolving cyber threats.
Protect your inbox today—ask us for a demo of ExchangeDefender PRO!
How the eBay Phishing Scam Works

The eBay phishing scam is a common cyberattack where scammers impersonate eBay to steal user credentials, financial details, or personal information. These scams often take the form of fake emails, text messages, or websites designed to trick users into providing sensitive information.
In eBay phishing scams, attackers send counterfeit emails or messages that appear to originate from eBay. These communications often contain urgent prompts, such as warnings about account issues or unauthorized transactions, compelling recipients to click on malicious links. These links lead to fake websites resembling eBay’s login page, where users are tricked into entering their credentials. Once obtained, cybercriminals can exploit this information for fraudulent activities, including unauthorized purchases or identity theft.

Red Flags to Watch Out For:
🚨 Generic Greetings – Legitimate eBay emails usually address you by name. Look for fake logos!
🚨 Suspicious Links – Hover over links before clicking—real eBay links should start with “ebay.com.”
🚨 Poor Grammar & Spelling – Many phishing emails have obvious errors. Look for fake phone numbers!
🚨 Requests for Personal Info – eBay never asks for passwords, payment info, or security details via email.
How to Protect Yourself:
✅ Enable Two-Factor Authentication (2FA) for extra security.
✅ Go Directly to eBay – Instead of clicking links, log in at eBay.com.
✅ Report Suspicious Emails to eBay at spoof@ebay.com.
✅ Use Strong, Unique Passwords – Avoid reusing your eBay password on other sites.
Mitigating Phishing Risks with ExchangeDefender PRO
To safeguard against such evolving threats, businesses require robust cybersecurity solutions. ExchangeDefender PRO offers comprehensive email security designed to protect organizations from advanced email-borne attacks. Key features include:
Anti-Phishing Protection: Identifies and blocks phishing attempts, preventing unauthorized access to sensitive information.
Anti-Spam and Malware Defense: Filters out spam and detects malicious attachments, reducing the risk of malware infections.
Ransomware Protection: Guards against ransomware attacks that can encrypt critical business data.
Domain Fraud Prevention: Prevents spoofing and unauthorized use of your domain, protecting your brand’s integrity.
On-Demand Encryption: Ensures sensitive communications are securely encrypted, maintaining confidentiality.
Adding ExchangeDefender PRO to your cybersecurity setup can help protect your organization from phishing scams and other email threats. It’s a smart way to stay safe online and keep your business and relationships secure.
How to Spot and Avoid Geek Squad Email Scams
In recent years, scammers have increasingly impersonated Geek Squad, Best Buy’s tech support service, to deceive individuals into divulging personal information or making unnecessary payments. Understanding how these scams operate and how to recognize them is crucial for safeguarding your personal data and finances.
Understanding the Geek Squad Email Scam
The Geek Squad email scam is a phishing attempt where fraudsters pose as Geek Squad representatives to steal personal information or trick victims into paying for fake services. These emails often appear legitimate, making it challenging to distinguish them from authentic communications.
Common Types of Geek Squad Email Scams
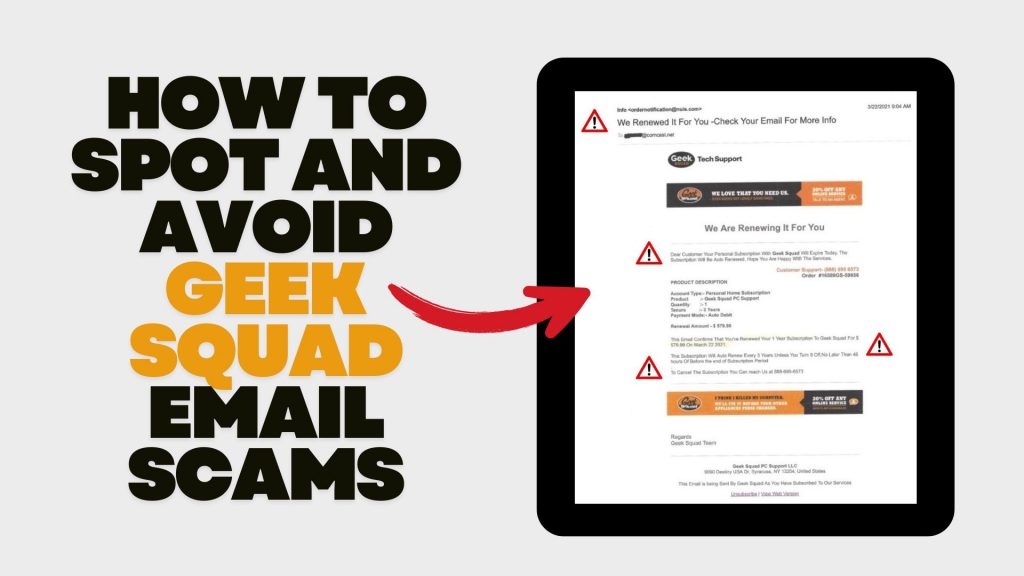
- Auto-Renewal Scam: Scammers send emails stating that your Geek Squad subscription is about to auto-renew at a substantial cost. The email urges you to call a provided number or click a link to cancel the subscription, aiming to extract personal and financial details.
- Fake Antivirus Software Offer: You might receive emails warning of malware infections among Geek Squad customers, offering free antivirus software downloads. However, these downloads are malicious and designed to infect your device, steal data, or gain remote access.
- Password Reset Scam: Emails claim suspicious activity on your Best Buy account, prompting you to reset your password via a provided link. The link leads to a fake website designed to capture your login credentials, allowing scammers unauthorized access to your account.
Recognizing Scam Emails
Be vigilant for the following signs:
- Sense of Urgency: Scammers often pressure you to act quickly, creating a false sense of urgency.
- Suspicious Sender Addresses: Examine the sender’s email address for inconsistencies or misspellings. Official communications will come from a legitimate Best Buy domain.
- Generic Greetings: Emails that don’t address you by name, such as “Dear Customer,” may be fraudulent.
- Poor Grammar and Spelling: Legitimate companies maintain professional communication standards.
- Unsolicited Attachments or Links: Avoid clicking on links or downloading attachments from unknown senders.
Protective Measures
- Verify Communications: If you receive a suspicious email, contact Geek Squad or Best Buy directly using official contact information from their website.
- Avoid Unsolicited Links and Downloads: Refrain from clicking on links or downloading attachments from unknown sources.
- Use Security Software: Ensure your devices are equipped with reputable antivirus and anti-malware programs.
- Stay Informed: Educate yourself about common phishing tactics to recognize and avoid potential scams.
Reporting Scams: If you encounter a Geek Squad scam, report it to Best Buy. Additionally, file a complaint with the Federal Trade Commission (FTC) through their Complaint Assistant.
Avoid Netflix Payment Scams: Recognize Phishing Emails
In recent months, a sophisticated email scam targeting Netflix users has emerged, aiming to steal personal and financial information. These phishing emails closely mimic legitimate Netflix communications, making them particularly deceptive. If you don’t have ExchangeDefender PRO Phishing protection, then here’s what you need to know:
How the Scam Operates
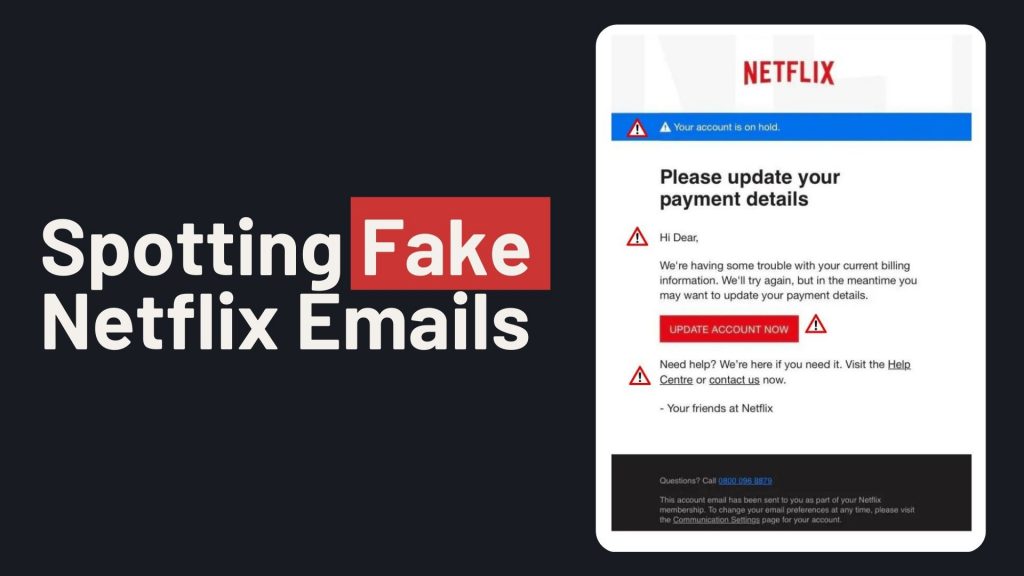
Victims receive emails claiming issues with their Netflix account, such as payment problems or account suspensions. The email urges recipients to update their payment details via a provided link, which leads to a fake Netflix login page. Entering information on this page allows scammers to harvest login credentials and credit card details.
Identifying the Scam
- Sender’s Email Address: Scam emails may originate from unofficial domains, such as an iCloud domain, rather than Netflix’s official domain.
- Urgent Language: The message may claim your account is on hold and prompt immediate action to update payment information.
- Suspicious Links: Hovering over links may reveal URLs that don’t direct to Netflix’s official website.
Protective Measures
- Avoid Clicking Links: Do not click on links or open attachments from unsolicited emails.
- Verify Authenticity: Log in directly through the official Netflix website to check your account status.
- Report Suspicious Emails: Forward any dubious emails to phishing@netflix.com.
- Monitor Financial Statements: Regularly check your bank and credit card statements for unauthorized transactions.
Netflix’s Official Stance
Netflix states it will never ask for personal information, such as credit card numbers or passwords, via email or text messages. By staying vigilant and recognizing the signs of phishing attempts, you can protect your personal and financial information from these scams.
Stay Safe from Zelle Scams: Simple Tips to Protect Your Money

Sending money through apps like Zelle is super convenient. But with that convenience comes the risk of scams. Let’s break down what these scams look like and how you can keep your hard-earned cash safe.
What’s a Zelle Scam?
Scammers have gotten crafty. They might send you a message or give you a call pretending to be from your bank or even Zelle itself. They’ll claim there’s an issue with your account or a suspicious transaction and urge you to act quickly. Their goal? To trick you into giving up personal information or sending them money.
Common Tricks Scammers Use:
- Fake Problems: They’ll say there’s unauthorized activity or that your account will be locked.
- Phony Links: They’ll send links that look official but lead to fake websites designed to steal your info.
- Too-Good-To-Be-True Offers: They might offer amazing deals or opportunities that require immediate payment.
How to Protect Yourself:
- Pause and Think: Don’t rush. Scammers rely on panic.
- Verify Before Acting: If you get a suspicious message, contact your bank
or Zelle directly using official channels. - Avoid Unsolicited Links: Don’t click on unexpected links or download attachments
from unknown senders.
ExchangeDefender PRO: Your Email Safety Net
One of the ways scammers reach out is through phishing emails. To shield yourself from these threats, consider using email security services like ExchangeDefender PRO. It offers top-notch protection against phishing attempts, spam, and other email-based threats. With features like advanced threat detection and real-time monitoring, it acts as a robust defense for your digital communications.
Beware of Toll Road Text Scams: Protect Yourself from Fraudulent Charges

Lately, scammers have been targeting drivers with deceptive messages about unpaid tolls, a tactic known as “smishing.” These fraudulent texts often claim you owe money for tolls and urge immediate payment to avoid penalties. They typically include a link that, when clicked, leads to a phishing site designed to steal your personal and financial information.
How the Scam Works:
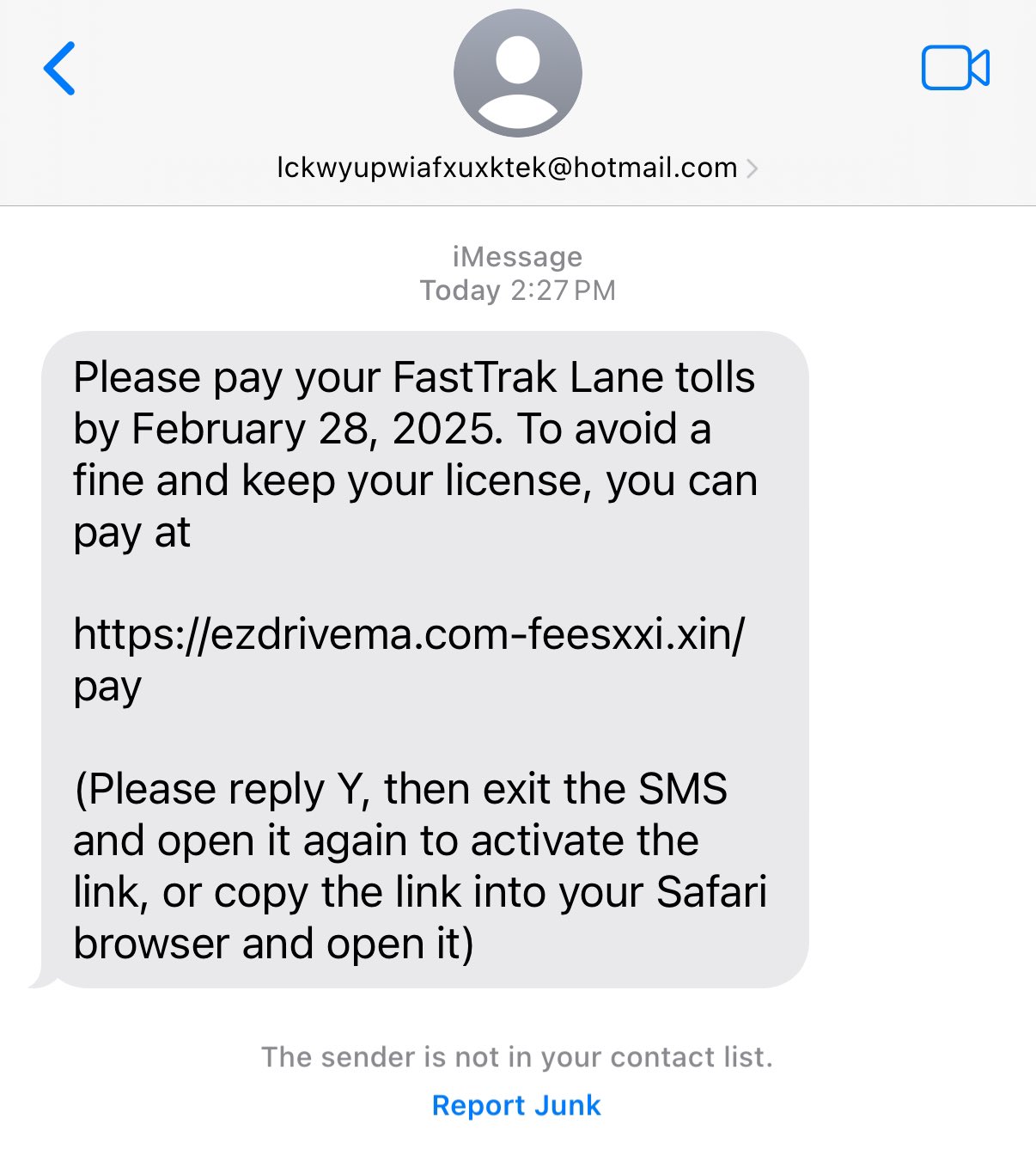
- Deceptive Messages: You receive an unsolicited text stating you have unpaid tolls, sometimes specifying an amount owed and threatening late fees.
- Phishing Links: The message includes a link directing you to a fake website resembling an official toll agency’s site, prompting you to enter sensitive information.
Recent Incidents:
Texas: The Texas Department of Transportation (TxDOT) warned about fraudulent texts targeting toll users, emphasizing that legitimate communications do not come via text messages.
Bay Area, California: A surge in FasTrak scams has been reported, with fake texts demanding toll payments and threatening penalties. Authorities advise against clicking on suspicious links, as FasTrak does not communicate via text message.
Protective Measures:
- Avoid Clicking Links: Do not click on links in unsolicited texts.
- Verify with Official Sources: Contact the tolling agency directly using known contact information to confirm any claims.
- Report Suspicious Messages: Use your phone’s “report junk” option or forward the message to 7726 (SPAM).
- Monitor Accounts: Regularly check your toll accounts for unauthorized charges.
How to Spot & Avoid the Latest DocuSign Scam

Cybercriminals are getting craftier, and one of their favorite new tricks is impersonating trusted services like DocuSign. If you’ve recently received an email urging you to sign a document or verify your account, think twice before clicking! The latest wave of DocuSign email scams is designed to steal your personal information and compromise your security.
How the DocuSign Email Scam Works
Scammers send fake emails that appear to be from DocuSign, using official-looking branding and urgent messaging. Here’s how the scam typically unfolds:
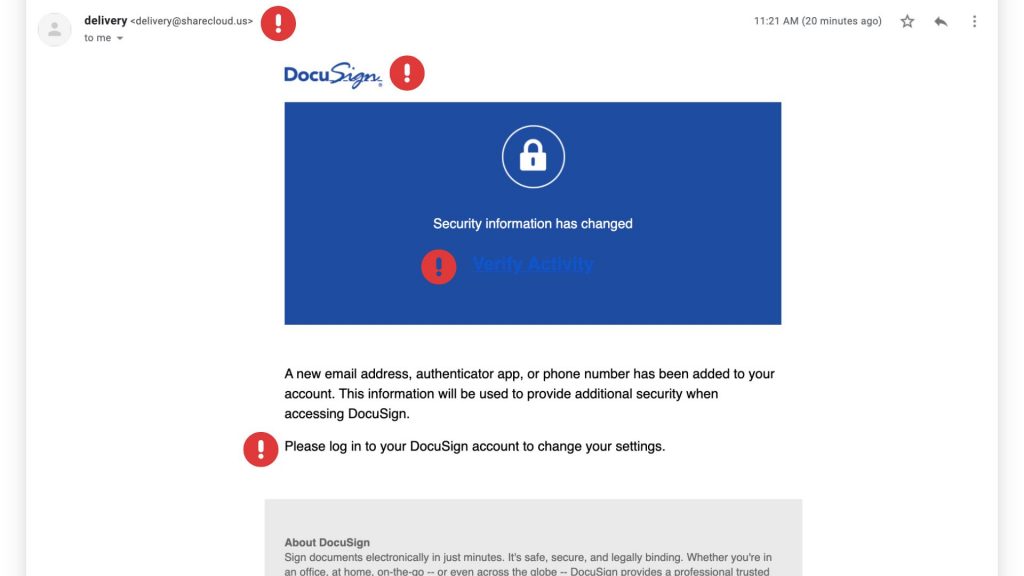
- Fake Email Notification – You receive an email that looks like it’s from DocuSign, requesting you to review or sign a document.
- Urgency & Pressure – The email often claims the document requires your immediate attention, creating a sense of urgency.
- Malicious Links – Clicking the link redirects you to a fraudulent website that mimics DocuSign’s login page.
- Credential Theft – If you enter your login details, scammers steal them to access your DocuSign or other linked accounts.
- Malware Installation – Some scams include attachments or links that, when clicked, install malware on your device.
Red Flags to Watch For
These scams can be convincing, but there are a few telltale signs that can help you identify them:
✔ Suspicious Sender Address – Official DocuSign emails come from @docusign.com or @docusign.net, not random or misspelled domains.
✔ Unusual Language or Errors – Many phishing emails contain typos, grammatical mistakes, or odd phrasing. Look for fake logos as well!
✔ Unexpected Requests – If you weren’t expecting a document, verify with the sender before opening anything.
✔ Fake Links – Hover over any links in the email (without clicking) to see the actual URL. If it’s not docusign.com, don’t trust it.
✔ Generic Greetings – Scammers often use “Dear Customer” instead of your actual name.
How to Stay Safe
Protect yourself and your business from falling victim to these scams by following these best practices:
🔹 Verify Directly – Instead of clicking email links, go to www.docusign.com and log in to check if a document is waiting.
🔹 Enable Multi-Factor Authentication (MFA) – Adding an extra layer of security can prevent unauthorized access to your account.
🔹 Report Suspicious Emails – If you receive a fraudulent DocuSign email, forward it to spam@docusign.com and then delete it.
🔹 Keep Security Software Updated – Use up-to-date antivirus and security software to detect and block phishing attempts.
🔹 Educate Your Team – Ensure employees know how to recognize and avoid phishing emails.
Texas Strengthens Cybersecurity with New State-Level Command Center

In February 2025, Texas Governor Greg Abbott announced the creation of the Texas Cyber Command, a state-level initiative headquartered in San Antonio.
This command center aims to enhance the state’s ability to anticipate, detect, and prevent cyberattacks, leveraging local expertise from institutions like The University of Texas at San Antonio. The Texas Cyber Command will collaborate with state universities, Regional Security Operation Centers, and various local and state agencies to create a unified defense against cyber threats.
Key objectives include promoting cybersecurity awareness, conducting simulation exercises, and providing forensic analysis for post-attack investigations. This development underscores the growing importance of state-level initiatives in safeguarding digital assets and infrastructure.
For a visual overview of the Texas Cyber Command, you can watch the following video:
ExchangeDefender WebUI: New Features & Enhancements! 🚀

As mentioned in the previous blog post, our new Web Services infrastructure is coming with a ton of new features, new UI, and new faster way of rolling things out that can help benefit & secure everyone.
In the previous post we discussed the scope of the update – rolling up over a decade and a half of legacy features, hacks, services, automations – all into a modern web services world where we can start rolling out features faster.
The biggest problem we are trying to solve now is how to quickly deploy efficient solutions. Most of the development time isn’t in actual coding or rollouts, most of the time is in design and confirming that users are able to quickly and effortlessly rely on them. Past service design was built over the years, as we helped our clients mitigate one security problem after another. Restructuring it will make things far smoother and easier to use.

Note the three single icons next to teach message checkbox. Tapping them on a touchscreen interface or with your mouse triggers the action to Release, Allow Sender, and Review. Icons aren’t very intuitive though – so we see people click on the checkbox and scroll all the way to the top to release a message.

Consider a new modern UI where icons become buttons. Would that change user behavior? Good news is that this will no longer be subject to opinion or guess but hard data as every element of our page will give us actual feedback about how the new feature is being used and how it’s performing:
By leveraging actual usage statistics and better insight on the backend, we can rely on AI to provide a far better level of service with a way faster delivery. In other words, we can respond to security problems faster.
Blue Cross Blue Shield Phishing Scam on the Rise

Blue Cross Blue Shield (BCBS) phishing emails are fraudulent messages designed to trick recipients into providing personal information, such as login credentials, Social Security numbers, or financial details. These emails often appear to come from BCBS but are actually sent by scammers aiming to steal sensitive data.
Common Tactics Used in BCBS Phishing Emails:
- Fake Account Alerts – The email may claim there’s an issue with your BCBS account, such as suspicious activity or a need to update your information.
- Urgent Payment Requests – Scammers may say you owe money for coverage or claim a payment failed, urging you to click a link.
- Fake Benefits or Refunds – Some phishing emails promise refunds, benefits, or changes to your health plan, requiring you to enter personal details.
- Malicious Links or Attachments – These emails often include links that lead to fake BCBS login pages or attachments containing malware.
- Spoofed Email Addresses – The sender’s email address may look official but often has subtle misspellings or extra characters (e.g.,
support@bcbs-secure.cominstead ofsupport@bcbs.com).

How to Spot and Avoid BCBS Phishing Emails:
✅ Check the Sender’s Email – Verify the email address carefully. Official BCBS emails come from legitimate domains.
✅ Look for Typos & Grammar Mistakes – Many phishing emails contain odd phrasing, spelling errors, or unprofessional formatting.
✅ Hover Over Links (But Don’t Click!) – Hover your mouse over links to see the actual destination URL. If it looks suspicious, don’t click.
✅ Never Enter Personal Info via Email – BCBS will never ask for sensitive data like passwords, Social Security numbers, or banking details via email.
✅ Contact BCBS Directly – If you’re unsure, call BCBS using the official number on their website, not the one in the email.
What to Do If You Receive a BCBS Phishing Email:
📌 Do NOT Click on Any Links or Attachments
📌 Report the Email – Forward phishing emails to BCBS’s fraud department or report them to the FTC at reportfraud.ftc.gov.
📌 Delete the Email Immediately
📌 Monitor Your Accounts – If you accidentally clicked a link, change your BCBS password immediately and watch for unauthorized activity.
Always stay cautious—cybercriminals keep improving their scams, but with awareness, you can protect yourself from falling victim! 🚨










