How Secure File Sharing Enhances Remote Team Collaboration

In today’s increasingly remote work environment, teams often face challenges when sharing large files securely and efficiently. Traditional methods like email attachments or outdated file servers can be cumbersome and pose security risks. ExchangeDefender’s Web File Server (WFS) offers a solution tailored to these needs, facilitating seamless and secure collaboration across different locations.
Challenges in Remote File Sharing
Remote teams frequently encounter issues such as:
- File Size Limitations: Email systems often restrict attachment sizes, making it difficult to share large documents.
- Security Concerns: Transferring sensitive information without robust security measures can lead to data breaches.
- Lack of Real-Time Collaboration: Without centralized platforms, coordinating on document edits and updates becomes challenging.
How ExchangeDefender WFS Addresses These Challenges
ExchangeDefender WFS is designed to overcome these obstacles by providing:
- Unlimited File Sharing and Storage: Users can upload and share files of any size without worrying about storage limits, ensuring that large documents like contracts or design files are easily accessible.
- Enhanced Security Features: With 128-bit SSL encryption, password protection, and auto-destruction capabilities, WFS ensures that sensitive data remains secure during transit and storage.
- User-Friendly Interface: The platform’s intuitive dashboard allows users to create document libraries, manage recipients, and track activity without requiring extensive training or IT support.
- Real-Time Collaboration: Teams can work simultaneously on documents, with features like version control and activity logs keeping everyone informed of changes.
Real-World Application
A local real estate company, Orange Avenue Homes, utilizes ExchangeDefender WFS to share contracts between remote team members and clients. The platform’s ease of use and robust security features have streamlined their document management processes, enhancing overall productivity.
For remote teams seeking a reliable and secure method to share large files, ExchangeDefender Web File Server offers a comprehensive solution. Its combination of unlimited storage, advanced security, and collaborative tools makes it an invaluable asset in today’s digital workspace.
Explore more about ExchangeDefender Web File Server and how it can benefit your remote team at ExchangeDefender Web File Server.
How to Report Phishing Emails in Outlook: A Step-by-Step Guide

Phishing emails are deceptive messages designed to trick you into revealing personal information or installing malicious software. Reporting these emails helps protect your account and assists in improving Microsoft’s security measures. Here’s how you can report phishing emails in Outlook:

For Outlook on the Web (Outlook.com):
- Sign In: Log into your Outlook.com account.
- Select the Email: In your inbox, click the checkbox next to the phishing email you wish to report.
- Report as Phishing:
- At the top of the message list, click on the “Report” button.
- From the dropdown menu, select “Phishing”.
- Confirmation: The email will be moved to your Junk Email folder, and Microsoft will be notified to enhance their spam filters.
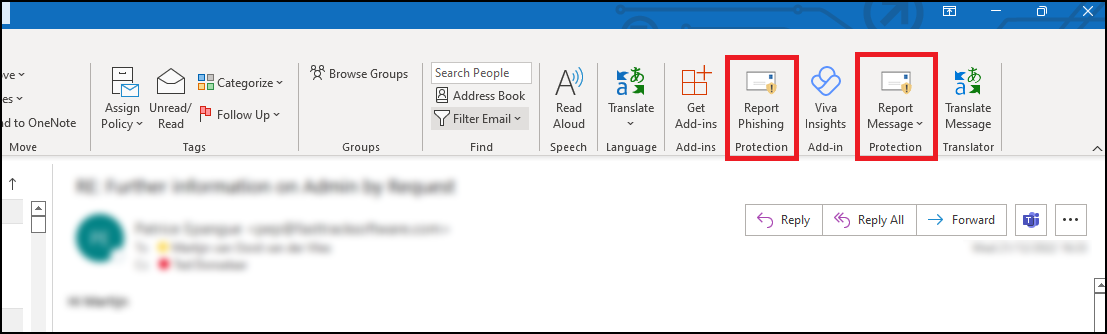
For Outlook Desktop Application (Windows):
- Open Outlook: Launch the Outlook application on your computer.
- Select the Email: In your inbox, click to highlight the phishing email.
- Access the Report Feature:
- Navigate to the “Home” tab in the ribbon at the top.
- Click on the “Report” button. If you don’t see this option, you may need to add the “Report Phishing” add-in:
- Click “Get Add-ins” in the ribbon.
- Search for “Report Phishing” and click “Add.”
- Report as Phishing:
- After adding the add-in, select the phishing email again.
- Click “Report” in the ribbon, then choose “Phishing.”
- Confirmation: The email will be moved to your Junk Email folder, and Microsoft will receive a report to improve their spam filters.
For Outlook Mobile App (iOS and Android):
- Open the App: Launch the Outlook app on your mobile device.
- Select the Email: Tap on the phishing email to open it.
- Access More Options:
- Tap the three-dot menu (⋮) at the top right corner of the email.Microsoft Support
- Report as Junk:
- Tap “Report Junk.”Microsoft Support
- Choose “Phishing” from the options provided.Microsoft Answers+1Gettysburg College+1
- Confirmation: The email will be moved to your Junk folder, and Microsoft will be notified to enhance their spam filters.
Source: Microsoft Support
ExchangeDefender WebUI: New Features & Enhancements! 🚀

As mentioned in the previous blog post, our new Web Services infrastructure is coming with a ton of new features, new UI, and new faster way of rolling things out that can help benefit & secure everyone.
In the previous post we discussed the scope of the update – rolling up over a decade and a half of legacy features, hacks, services, automations – all into a modern web services world where we can start rolling out features faster.
The biggest problem we are trying to solve now is how to quickly deploy efficient solutions. Most of the development time isn’t in actual coding or rollouts, most of the time is in design and confirming that users are able to quickly and effortlessly rely on them. Past service design was built over the years, as we helped our clients mitigate one security problem after another. Restructuring it will make things far smoother and easier to use.

Note the three single icons next to teach message checkbox. Tapping them on a touchscreen interface or with your mouse triggers the action to Release, Allow Sender, and Review. Icons aren’t very intuitive though – so we see people click on the checkbox and scroll all the way to the top to release a message.

Consider a new modern UI where icons become buttons. Would that change user behavior? Good news is that this will no longer be subject to opinion or guess but hard data as every element of our page will give us actual feedback about how the new feature is being used and how it’s performing:
By leveraging actual usage statistics and better insight on the backend, we can rely on AI to provide a far better level of service with a way faster delivery. In other words, we can respond to security problems faster.
ExchangeDefender Web Services Update

ExchangeDefender Web Services Update has concluded and the new infrastructure is handling 100% of the ExchangeDefender traffic. So far the new platform is performing exactly as expected and we have already closed several minor bugs. Overall, we are extremely happy at ExchangeDefender today!
We want to take a moment to high-five ourselves and highlight three main areas where our clients and partners are going to benefit from this investment:
1. Enhanced Security
With the changes in the development backend, our platform now utilizes the latest security patches and modern language features, significantly reducing vulnerabilities and providing a more robust threat defense.
Our old platform was also rock-solid in terms of performance and security, but that secure-by-design methodology forced us to reverse-engineer as well as design and manage everything from input validation to report routing. Modern web services take care of these routine things allowing us to spend more time on policy development.
2. Improved Performance
The new infrastructure supports faster processing and is optimized for global operations allowing us to deliver a more responsive and reliable service.
You’ve already seen a hint of this in the ExchangeDefender LiveArchive relaunch as a standalone data vault for cloud operations. By breaking up our infrastructure into microservices we’re able to deliver edge operations closer to where our clients are, we can keep data more securely in your local data geography, and we can delegate away control as required.
3. Features Shipped Faster
By moving away from legacy code and internal systems/plugins for policy and protocol enforcement, we can dedicate more of our development cycles to policies and training that will keep your organization more secure. You will be able to benefit from the latest improvements and security innovations while we deliver more.
Thank you for filling out our survey, if you haven’t done so please take a moment to tell us where we can help. We have intentionally dedicated a large window to bringing the new web service infrastructure online so we do have spare cycles to help alleviate some pain points our clients are experiencing. Please take a moment to fill out our survey
We are hard at work on the new User Interface, we’re nearly ready for the public launch of our Phishing platform, all sorts of goodies are heading your way so once again – thank you for your business and your faith in us to deliver safe and secure email to your organization.
Sincerely, Vlad Mazek CEO ExchangeDefender
ExchangeDefender 2025 Web Service Expansion

In less than a week, ExchangeDefender will be running on a new generation of web services. While improving security and performance, the new platform will enable us to launch a ton of new features in 2025 and we would like our clients and partners have a say.
If you have a moment, we would appreciate some feedback. Only (3) questions, should take less than ONE minute and will help us a TON!
https://www.surveymonkey.com/r/YXQ5TKZ
In 2025 we are looking forward to growing ExchangeDefender to do every aspect of email security. We want to extend our protection to phishing simulations, training, and analytics tools. We have also heard from you regarding having mobile apps to manage the user mailbox for users who are full-time mobile. We are redesigning our SPAM reports. We are improving our M365 security footprint with built-in monitoring and performance metrics.
But most of all, we are looking to help meet the problems you’re experiencing in your organization with better solutions, better documentation, and the AI integrations you’ve been demanding.
Please take a moment to fill out our survey and let us know if you’d like us to get in touch with you. We often work with partners on custom solutions and if we can make ExchangeDefender work better for you let us know in the survey or the support ticket and we’ll be happy to set a time.
Looking forward to working with you in 2025 and thank you for your business.
Facebook Security Email Scams You Need to Know

We all rely on Facebook to stay connected with friends and family, but are you aware of the sneaky scams targeting Facebook users through fake security emails? These phishing attempts can have serious consequences, so it’s crucial to know how to spot them and protect yourself.

The Scam: How It Works
Imagine receiving an email that looks like it’s from Facebook Security. It might say something alarming like:
- “Suspicious activity detected on your account!”
- “Your Facebook account will be suspended if you don’t act now!”
- “We’ve noticed unusual login attempts from an unknown location.”
These emails are designed to scare you into taking immediate action without thinking. They often include official-looking logos and urgent language to make them seem legitimate. The real danger lies in the links within these emails. Clicking them takes you to a fake Facebook login page, meticulously crafted to mimic the real thing. If you enter your username and password on this fake page, you’re handing your account directly to scammers.
What Happens Next?
Once scammers have your login credentials, they can:
- Take over your account: They can change your password, profile information, and even lock you out.
- Spread more scams: They can use your account to send spam messages and phishing emails to your friends, potentially tricking them as well.
- Steal personal information: They might access your personal messages, photos, and other sensitive data.

How to Protect Yourself: Stay Safe Online
Luckily, there are simple steps you can take to avoid falling victim to these scams:
- Be suspicious of unexpected emails: If you receive an unexpected email about your Facebook account security, be extra cautious. Facebook rarely contacts users directly via email regarding security issues unless you’ve specifically requested it.
- Check the sender’s address: Carefully examine the sender’s email address. Legitimate emails from Facebook usually come from an address ending in “@facebookmail.com”. Anything else should raise a red flag.
- Don’t click on links in emails: This is the golden rule! Instead of clicking on links in suspicious emails, go directly to the Facebook website by typing “facebook.com” into your browser. This ensures you’re on the real website.
- Enable two-factor authentication: This adds an extra layer of security. Even if a scammer gets your password, they’ll need a code from your phone or another device to access your account. You can find this option in your Facebook security settings.
- Report suspicious emails: If you receive a suspicious email, don’t just delete it. Report it to Facebook to help them combat these scams.
Stay Vigilant, Stay Safe
Facebook security email scams are a constant threat, but by staying informed and following these simple tips, you can significantly reduce your risk. Remember, vigilance is key to staying safe online. Don’t let fear or urgency cloud your judgment. Always double-check, and when in doubt, go directly to Facebook’s website. By taking these precautions, you can protect yourself and your online presence.
The Latest Cyber Threats You Need to Know About (2025 Edition)

The cyber threat landscape is constantly evolving, with new and sophisticated attacks emerging every day. In 2025, we’re seeing a convergence of several concerning trends:
1. AI-Powered Attacks:
- Sophisticated Phishing: AI is now generating incredibly convincing phishing emails, making them harder to detect.
- Automated Exploits: AI can quickly identify and exploit vulnerabilities in systems, launching attacks at unprecedented speeds.
- Deepfakes: AI-generated deepfakes are becoming increasingly realistic, making it difficult to distinguish between real and fabricated content, leading to social engineering and disinformation campaigns.
2. The Rise of IoT Attacks:
- With the proliferation of Internet of Things (IoT) devices in homes and businesses, attack surfaces are expanding dramatically.
- Hackers can exploit vulnerabilities in connected devices to gain access to sensitive information or even control critical infrastructure.
3. Cloud Security Challenges:
- As more businesses migrate to the cloud, the security of cloud environments becomes increasingly critical.
- Cloud misconfigurations, vulnerabilities in cloud services, and insider threats pose significant challenges.
4. Ransomware 2.0:
- Ransomware attacks are becoming more sophisticated and targeted, with attackers demanding higher ransoms and threatening to release sensitive data publicly.
To stay safe online, practice strong password hygiene, be wary of suspicious emails and links, keep your devices and software updated, and be mindful of what you share online. The cyber threat landscape is constantly evolving, but by staying informed and taking proactive steps to protect yourself, you can minimize your risk of falling victim to cyberattacks.
Why Phishing Simulations Are Essential for Your Organization

Phishing attacks remain one of the most prevalent and effective cyber threats facing businesses today. These deceptive tactics target the human element, tricking employees into divulging sensitive information or installing malware. That’s why phishing simulations are no longer a “nice-to-have” but a critical component of any robust cybersecurity strategy. At ExchangeDefender, we understand the importance of proactive security measures, and we’re here to explain why phishing simulations are essential for protecting your organization.
1. Turning Employees into a Human Firewall
Your employees are your first line of defense against cyber threats. Phishing simulations empower them to recognize and avoid phishing attacks in the real world. Here’s how:
- Real-World Scenarios: We craft simulations that mimic real-world phishing attempts, using realistic emails, text messages, and even voice calls. This exposes your team to the latest tactics used by cybercriminals, preparing them for what they might encounter.
- Learning by Doing: Experiencing a simulated attack provides invaluable hands-on experience. Employees learn to identify red flags like suspicious sender addresses, urgent requests, unusual links, and grammatical errors.
- Driving Behavioral Change: This practical training is far more effective than simply reading about phishing in a manual. It helps employees develop the instincts to spot and avoid real threats, fostering a culture of security awareness.
2. Identifying Vulnerabilities Before Attackers Do
Phishing simulations not only train your employees but also provide valuable insights into your organization’s security posture:
- Measuring Employee Susceptibility: Simulations reveal how many employees are likely to fall for a phishing attack, highlighting areas where additional training is needed. This data-driven approach allows you to focus your resources effectively.
- Pinpointing Weaknesses: By analyzing simulation results, we can identify specific types of phishing attacks that are most effective against your workforce. This enables us to tailor training programs to address your organization’s unique vulnerabilities.
- Improving Training Programs: The data gathered from simulations allows for continuous improvement of your security awareness training, making it more relevant and effective over time.

3. Reducing the Risk of Successful Attacks (and the Costs They Incur)
The ultimate goal of phishing simulations is to reduce the risk of successful phishing attacks and the devastating consequences they can bring:
- Proactive Security: Phishing simulations take a proactive approach to security, addressing the human element before it becomes a vulnerability.
- Mitigating Incident Response Costs: By preventing successful phishing attacks, you can avoid the significant financial and reputational damage associated with data breaches, ransomware infections, and other security incidents.
- Building a Stronger Security Culture: Regular simulations foster a security-conscious culture where employees are actively engaged in protecting sensitive information, making security a shared responsibility.
ExchangeDefender: Your Partner in Cybersecurity
In today’s complex threat landscape, phishing simulations are an indispensable tool for protecting your organization. At ExchangeDefender, we offer comprehensive cybersecurity solutions, including phishing simulation services, to help you strengthen your defenses and empower your employees. Contact us today to learn more about how we can help you build a more secure future.
Upgrade Notice: Login Service Enhancements and Monitoring Improvements

Over the weekend, we designed, tested, and implemented new architectural solutions to address recent issues with the central login service for ExchangeDefender products. Additionally, we identified and began resolving a critical alerting issue that had prevented our NOC from receiving timely notifications about service outages.
To expedite improvements, we deployed a web cluster originally planned for a later release. This new cluster introduces advanced high-availability features, including self-healing capabilities and integration with modern, distributed monitoring solutions to ensure consistent global accessibility.
Given the scope of this upgrade, we opted for a phased rollout using A/B testing to ensure service reliability. Over the past three days, we’ve gradually increased traffic to the new cluster, starting at 12%, while monitoring server and load balancer performance metrics. Currently, 20% of traffic is routed through the new cluster, with the remaining 80% handled by the legacy system. In the event of a failure in either cluster, the load balancer will dynamically shift all traffic to the active system, even if a customer was initially pinned to the affected cluster.
Performance Improvements
The initial results have been highly encouraging, with noticeable performance gains. We’ve observed a 5x improvement in P95 latency and a 3x improvement in P99 latency compared to the previous setup.
Next Steps
Next weekend, we plan to implement the final phase of this upgrade, introducing automated transitions between data centers to address any performance or reliability issues proactively.
Addressing Notification System Failures
During our investigation, we identified a failure point in our notification system. Alerts were being throttled or discarded by our SMS gateway, particularly during cascading outages triggered by login server downtime. We’ve since refreshed our monitoring solution with modern analytics tools and implemented multiple alerting pipelines to prevent future disruptions. While we continue to work with our SMS gateway provider to resolve filtering issues, these changes significantly improve our ability to detect and respond to service issues.
Thank You for Your Patience
We sincerely appreciate your understanding as we worked to diagnose and resolve these challenges. We recognize how frustrating the repeated service interruptions have been and want to assure you that we’ve been actively addressing these issues with a focus on long-term reliability and minimal disruption.
Thank you for your continued trust in ExchangeDefender.
What is Ransomware? The Price of Clickbait


What is Ransomware?
Ransomware is a type of Malware. It is a nasty computer virus that locks up your important files. Think of your files as your favorite photos, important documents, or work projects. When ransomware strikes, it scrambles these files, making them useless until you pay the hackers. It’s like a digital thief who kidnaps your data and demands a ransom to give it back.

The Allure of Malicious Links and Attachments
Let’s be real, we’re constantly bombarded with information. From social media to email, we’re exposed to a constant stream of links and attachments. While many of these are harmless, some can be incredibly dangerous.

Why do people click on malicious links and attachments?
- Curiosity: A well-crafted subject line or intriguing message can pique our interest, leading us to click without thinking.
- Sense of urgency: Cybercriminals often use tactics like “urgent action required” or “limited-time offer” to create a sense of urgency, prompting us to click impulsively.
- Trust in the sender: If the email appears to be from a trusted source, such as a friend, family member, or colleague, we may be more likely to let our guard down.

The Devastating Consequences
The consequences of clicking on a malicious link or attachment can be severe. Ransomware attacks can cripple businesses, government agencies, and individuals, leading to significant financial losses, data breaches, and reputational damage.
How to Protect Yourself
To protect yourself from ransomware attacks, it’s essential to practice good cyber hygiene. Here are some tips:
- Be cautious of unsolicited emails: Avoid opening emails from unknown senders or those with suspicious subject lines.
- Verify the sender: Double-check the sender’s email address and look for any typos or grammatical errors.
- Hover over links before clicking: This can help you identify malicious links that may redirect you to harmful websites.
- Use strong, unique passwords: A strong password can make it more difficult for cybercriminals to access your accounts.
- Keep your software up-to-date: Regularly update your operating system and software applications to patch vulnerabilities.
- Back up your data: Regularly back up your important files to an external hard drive or cloud storage service.
By following these simple tips, you can significantly reduce your risk of falling victim to a ransomware attack.
Remember, a single click can have devastating consequences.









