Enhanced Security: ExchangeDefender Now Supports Custom Authenticator Apps for MFA!

ExchangeDefender has recently enhanced our MFA features (multi-factor authentication) to help you enforce domain-level MFA compliance and to make it easier for users to be enrolled and protected by a layered authentication process automatically.
Simply put, we’re making it easier for you to keep everyone protected.
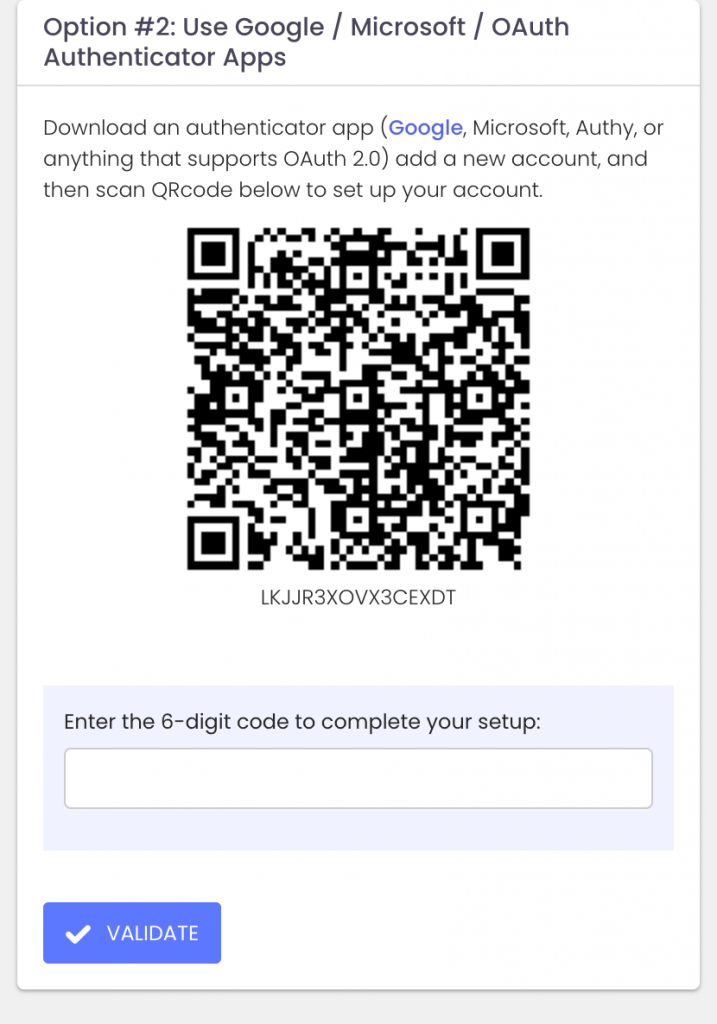
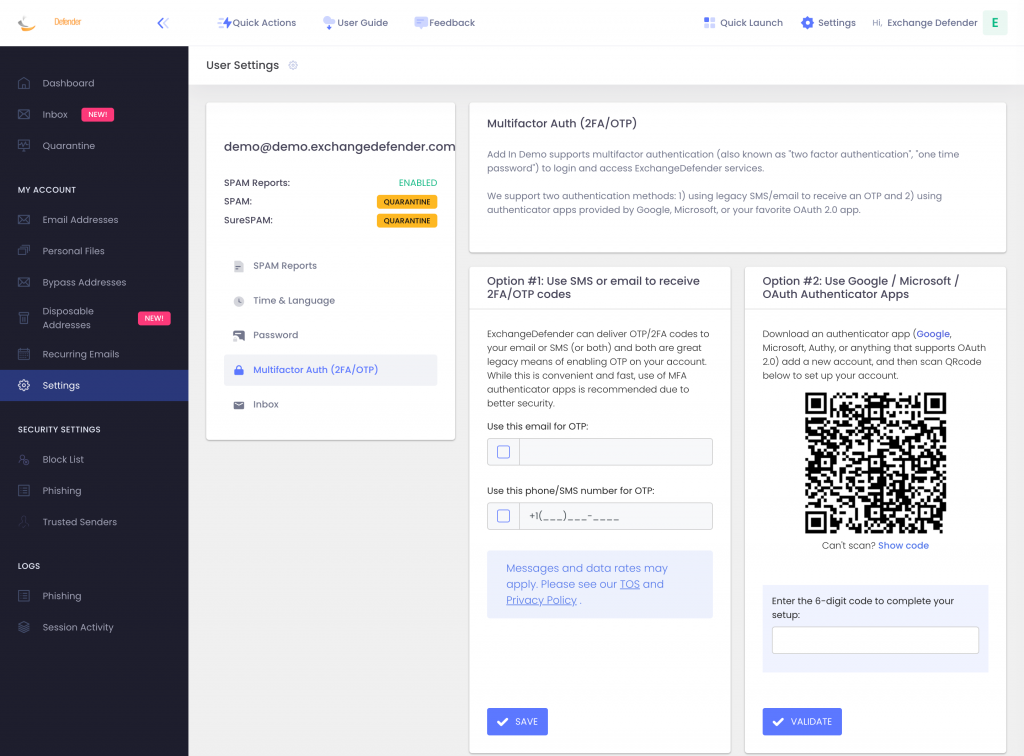
Today we are announcing ExchangeDefender MFA support for custom authenticator apps. By now everyone is familiar with our typical MFA functionality, available under your Settings at https://admin.exchangedefender.com. Just scan the QR code on your device and you’re set!
BUT WHAT IF YOUR DEVICE DOESN’T HAVE A CAMERA?
ExchangeDefender now supports MFA app enrollment using a QR code. This is great for scenarios in which:
– You don’t have a camera on your device
– The QR code doesn’t seem to scan (problems with the camera or monitor)
– You want to use a text-based MFA app
– You want to integrate PowerShell/no-code with MFA
– You want to share your MFA codes with others
If you’re in one of those scenarios, note the text under the QR code when you start the enrollment:
Click on the Can’t scan? Show code link and you’ll get the TOTP secret (aka secret code, MFA code). Paste it in your solution and paste back the 6 digit code it generates. That’s it, you’re done. MFA is now enforced and ExchangeDefender will rely on the codes generated by your app to validate MFA and grant access to your account.
All our features come from user feedback so if there is something we need to be doing to keep you more secure please let us know!
Enhanced MFA Enforcement Policy: Strengthening ExchangeDefender Security Measures

For years, ExchangeDefender users have enjoyed enhanced login security via multi-factor authentication security (aka MFA, 2FA, OTP). In our March feature update, we hope to improve your security and enhance MFA enrollment to keep you and your data safe. Allow us to introduce to you the new MFA Enforcement Policy!
Note from the boss: Before we get to any discussion of policies, our official recommendation is to enforce MFA on every service we provide and to rotate passwords at least once a quarter. I know, nobody likes the second validation prompt but this is a standard in the industry and I can’t think of a bank or a vendor that doesn’t require it. Maybe I’m jaded because we’re a cybersecurity company.. and with all the layers of MFA/VPN/auth we have in place I spend an insane amount of time trying to find my key or wait for the new pin to display in my authentication app. Because when I interact with a vendor that holds my information and they have no login security.. all I can wonder is what else they’re not doing to keep my data safe? Is this a real business or some WordPress plugin?
At the same time, I understand we have a ton of customers in SMB space where sometimes (obnoxious) tech can be slow and difficult to implement. But you pay us to keep you safe – and to keep your backups safe, and to keep your business continuity safe, and to do that we absolutely must require MFA. But we also can’t expect staff who have clicked on a Release/Trust link for over a decade to be cool with suddenly being forced into MFA enforcement workflow on Monday. So we designed a compromise. I hope it fits your organization and I hope you adopt it as fast as possible.
Sincerely,
–Vlad Mazek, CEO Own Web Now Corp.
In March 2024 you will have the ability to enforce or require MFA enrollment at the domain level. What this means is that you’ll be able to require MFA enrollment with an authenticator app for everyone with just one click at https://admin.exchangedefender.com:
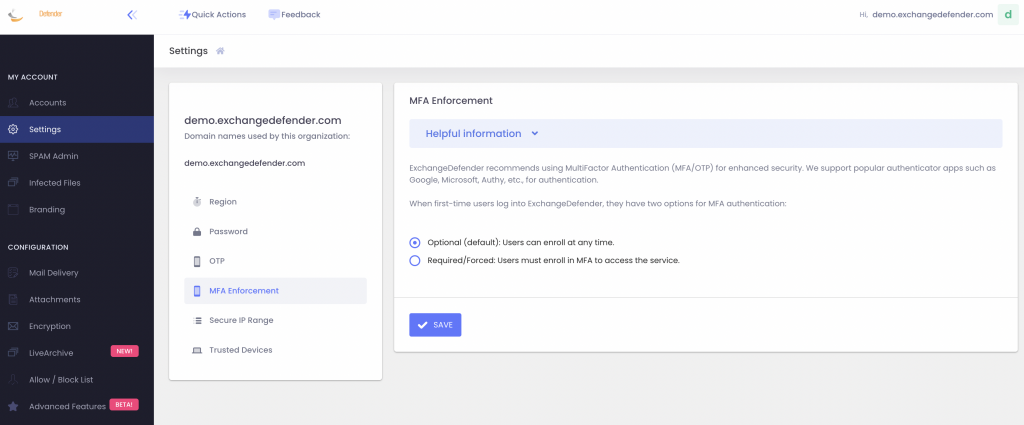
With this policy, you can secure your users’ login with multi-factor authentication without making them enroll a device.
How does it work?
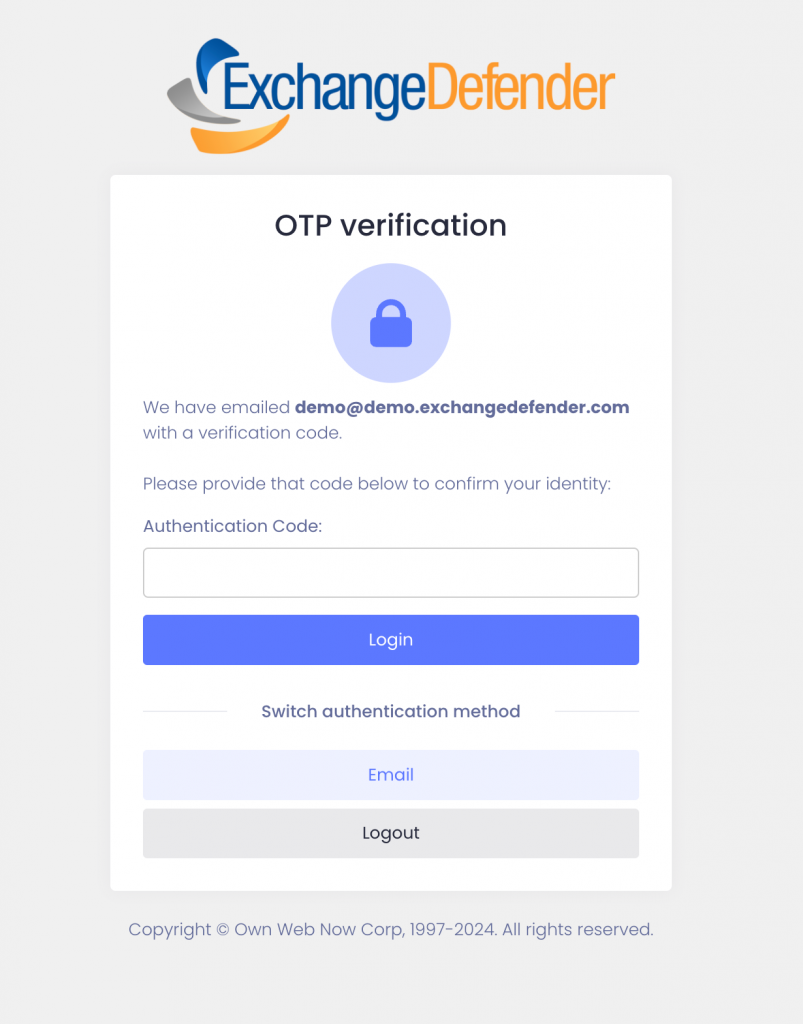
When your users go to admin.exchangedefender.com and attempt to access Inbox, WFS, or LiveArchive we will check their MFA enrollment and if none is found we’ll just tell them we have to verify their identity:
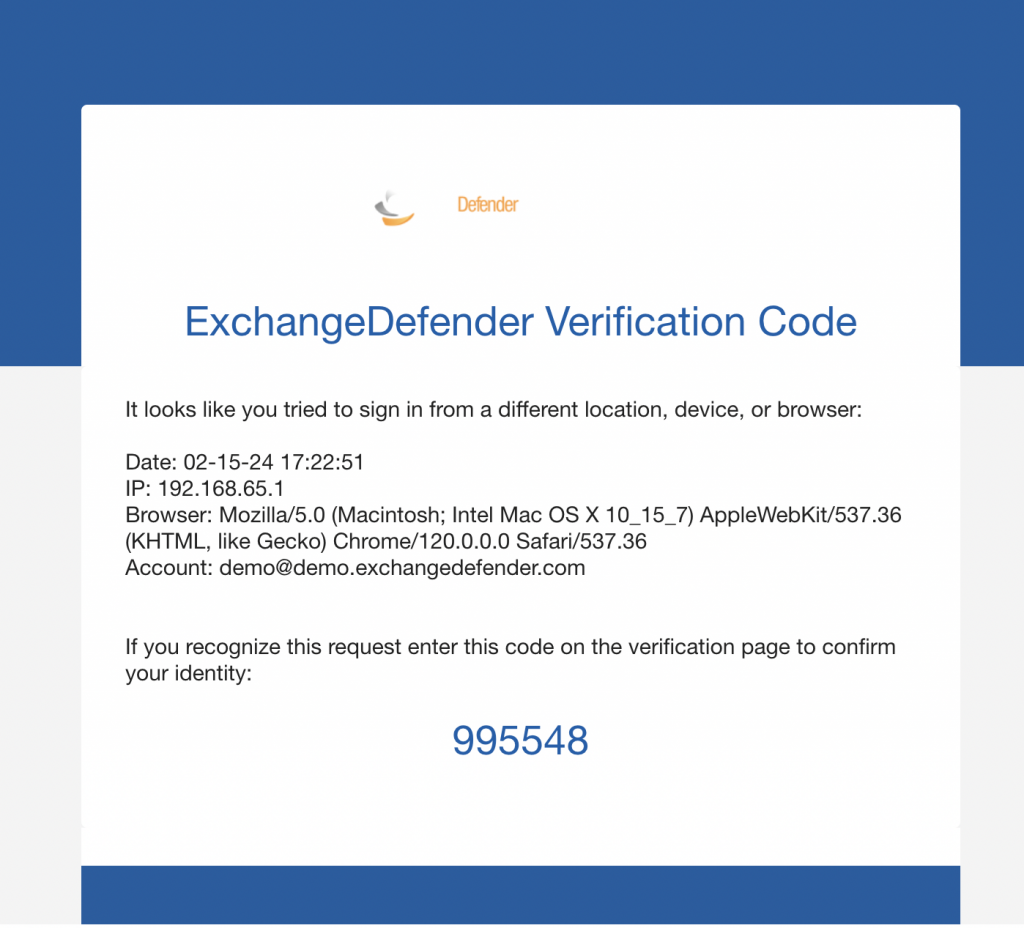
When they check their mailbox they’ll see an email from ExchangeDefender and just provide the code back.
This way your ExchangeDefender login is technically secured at ExchangeDefender with MFA even if you haven’t enrolled a device in MFA yet. There is no way to get into the secure areas of your account without enrolling into MFA. But what if someone guessed the password, they can just enroll a device and hijack the account, right? No.
When you set MFA Enforcement to Required/Forced, all your users are automatically set into an MFA mode that relies on their email address for secondary verification. When they visit admin.exchangedefender.com for the first time and provide their username and password the system will check their MFA enrollment and if email MFA is detected the system will send them an email with a verification code to proceed. This way we’re using the email MFA as a way to verify their identity and then we enroll their authenticator app as usual by scanning the QR code.
ExchangeDefender Quarantine Reports behavior will not change at all as a result of the change in the MFA Enforcement policy. ExchangeDefender Quarantine Reports do not rely on the login system at all as the user is never prompted to authenticate to trigger the release of the message. Instead, quarantine operations are tokenized and one “release” request does not automatically grant any other release or trust requests with the same token. It also doesn’t automatically log them into ExchangeDefender so there is no getting by the MFA!
Secure your logins now
It’s 2024 and the world has changed when it comes to authentication and identity when dealing with services online. Experiencing a cybersecurity threat or compromise is an incredibly expensive and frustrating experience that can easily be avoided by requiring an ID check before granting access to sensitive information. ExchangeDefender MFA Enforcement Policy is your way to protecting your organization from unauthorized and unverified access.
ExchangeDefender MFA Service Upgrades

ExchangeDefender has beefed up our MFA (multi-factor authentication aka 2FA / OTP) service with addition of new vendors and a wider reach.
Setting up MFA involves either installing an authenticator app or authorizing us to send you a text message. When you login to our service the system will expect you to provide the 6 digit code that will only* be known to your trusted device. Essentially, it keeps people who only know your username and password out of your account.
While we would prefer a more secure and reliable model in which our clients rely on MFA authenticator apps over the less secure SMS, we understand that is not a practical solution everywhere and absolutely every needs this second layer of authentication when accessing mission critical systems such as email and file sharing.
As you may remember, we had an issue with SMS MFA before Christmas and thanks to some heavy lifting by our team over the holidays the new SMS infrastructure is truly global, scalable – and will be delivered by multiple providers for better redundancy (eliminating the 10DLC compliance issues).
With the retirement of ExchangeDefender Essentials and all the compromises it required, you will be seeing a flurry of new security features in the ExchangeDefender Email Security service. First of many will be the access restrictions and the ability to restrict access to ExchangeDefender services based on location, time, etc. The attacks on email infrastructure are only getting more numerous and more sophisticated by the day and traditional (or cheap) security methods are no longer viable in 2023 and certainly not beyond. We look forward to continuing the best email security money can buy and we thank you all in advance for trusting us with your email.