Keep up with ExchangeDefender Changelog

When we launched our new user interface infrastructure, we did so that we could run ExchangeDefender at the cutting edge. By bringing all of our apps under one umbrella, we can now monitor and address bugs and performance issues in real-time.
The pace of development has really picked up, and when things are constantly improving, it’s important to keep everyone informed when issues get addressed and bugs get fixed. At https://admin.exchangedefender.com, when you log in as a Domain Administrator, you will now see a new Announcements button on the bottom right.
You can view our announcements on this screen (same content that is available on the login screen) and you can click on the Changelog to see our recent changes. This way you can see what is being added and fixed, and we can track it back to the original issue report.
We owe a huge thank you to our partners and clients for feature suggestions and bug-fix help last month, we are working hard to keep the web apps at the top security and industry standards because this is how people exchange sensitive information and we take great effort to make that easier and more secure.
Enhanced Security: ExchangeDefender Now Supports Custom Authenticator Apps for MFA!

ExchangeDefender has recently enhanced our MFA features (multi-factor authentication) to help you enforce domain-level MFA compliance and to make it easier for users to be enrolled and protected by a layered authentication process automatically.
Simply put, we’re making it easier for you to keep everyone protected.
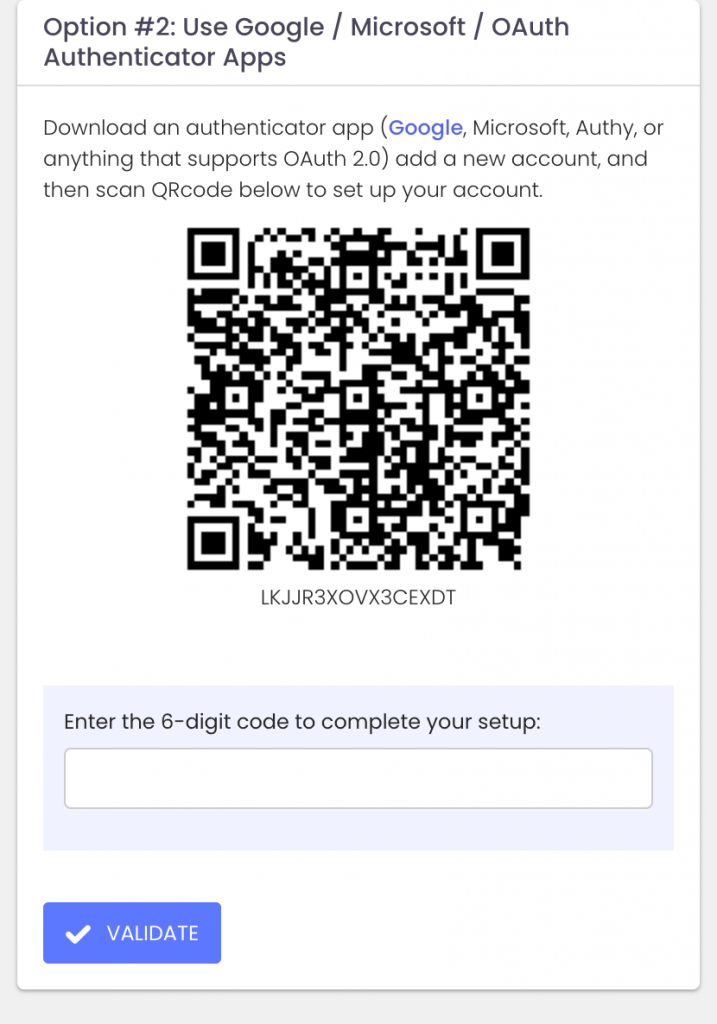
Today we are announcing ExchangeDefender MFA support for custom authenticator apps. By now everyone is familiar with our typical MFA functionality, available under your Settings at https://admin.exchangedefender.com. Just scan the QR code on your device and you’re set!
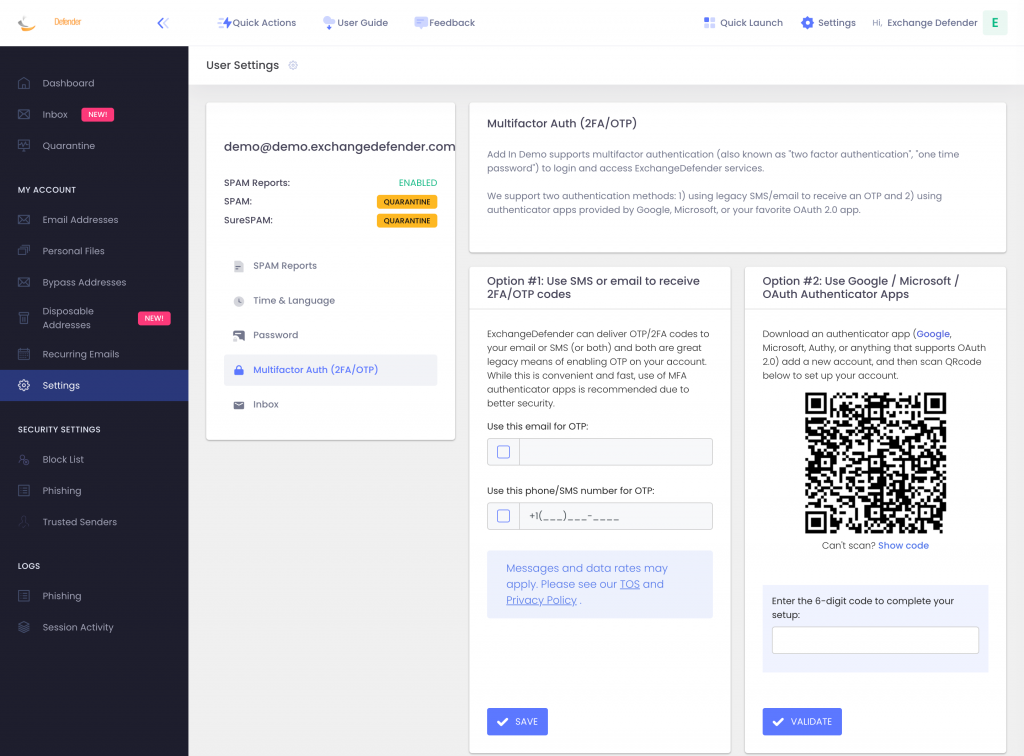
BUT WHAT IF YOUR DEVICE DOESN’T HAVE A CAMERA?
ExchangeDefender now supports MFA app enrollment using a QR code. This is great for scenarios in which:
– You don’t have a camera on your device
– The QR code doesn’t seem to scan (problems with the camera or monitor)
– You want to use a text-based MFA app
– You want to integrate PowerShell/no-code with MFA
– You want to share your MFA codes with others
If you’re in one of those scenarios, note the text under the QR code when you start the enrollment:
Click on the Can’t scan? Show code link and you’ll get the TOTP secret (aka secret code, MFA code). Paste it in your solution and paste back the 6 digit code it generates. That’s it, you’re done. MFA is now enforced and ExchangeDefender will rely on the codes generated by your app to validate MFA and grant access to your account.
All our features come from user feedback so if there is something we need to be doing to keep you more secure please let us know!
Something old, new, borrowed, and blue!
As the throwback to the Victorian era implies, ExchangeDefender looks forward to providing your protection and prosperity. From September to November of 2023 we will be launching a ton of new features and we want to invite you to a webinar that will explain all the details you need to know:

The pricing will not change but you’ll get many new features and security settings.
We are responding to the demands and problems our clients face every day exchanging information across the Internet securely.
What worked a decade or two ago, heck even a week or two ago in some cases, is no longer adequate. That’s what you pay us for and the primary value we provide – keeping new exploits and attacks on your technology away from your server/cloud/tenant.
To get the same level of protection and monitoring you’d need a dedicated cybersecurity team for even the smallest of organizations – and we’re taking big steps to simplify that process and give you the ability to control your security without having to deal with every little detail.
We’re excited and hope you get a chance to join us for this webinar – we promise it will save you a ton of time and get you ahead of what will be a very busy quarter.
How to access ExchangeDefender Raw Email Logs
ExchangeDefender has been holding Service Provider (MSP/VAR) Focus Group meetings this week and we’re beyond excited to hear what we can build to make your and your clients lives easier with ExchangeDefender.
One of the most common pieces of feedback from the *Service Provider crowd so far has to do with log access and particularly low-level log access that can give further insight into problems and message routing.
Allow us to introduce you to Raw SMTP Mail Logs which will give our partners direct access to the low-level SMTP transaction and error logs. It’s located in the same location where you currently have service provider logs at admin.exchangedefender.com
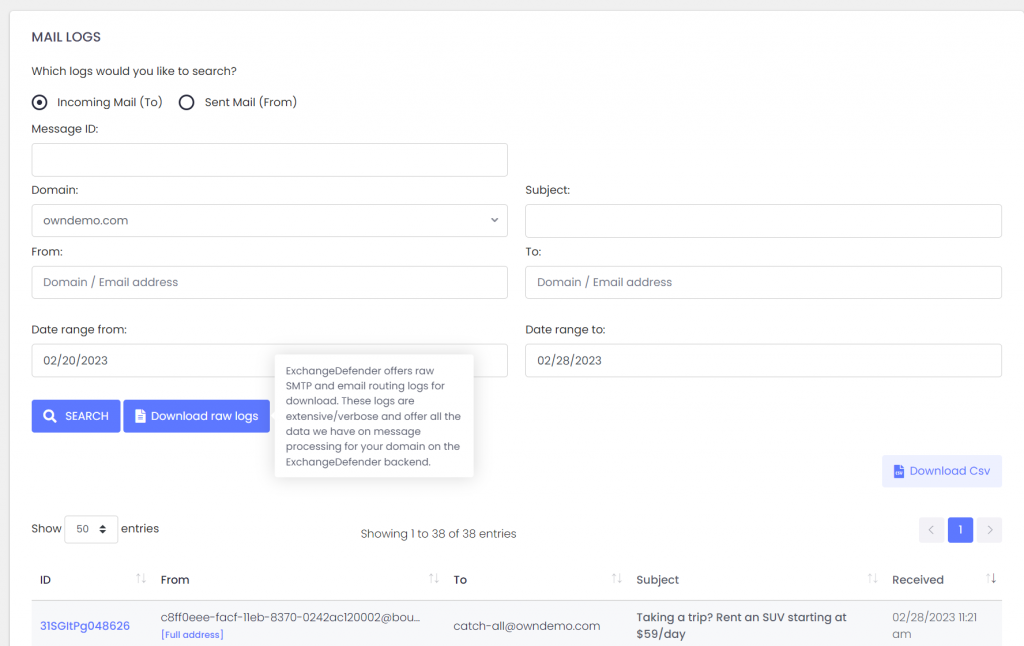
In addition to the live search which will give you an interactive access to our logs, you can see the button to Download raw logs.
Set your search criteria (at the very least a domain name and the direction of the search: inbound/outbound) and click on the button.
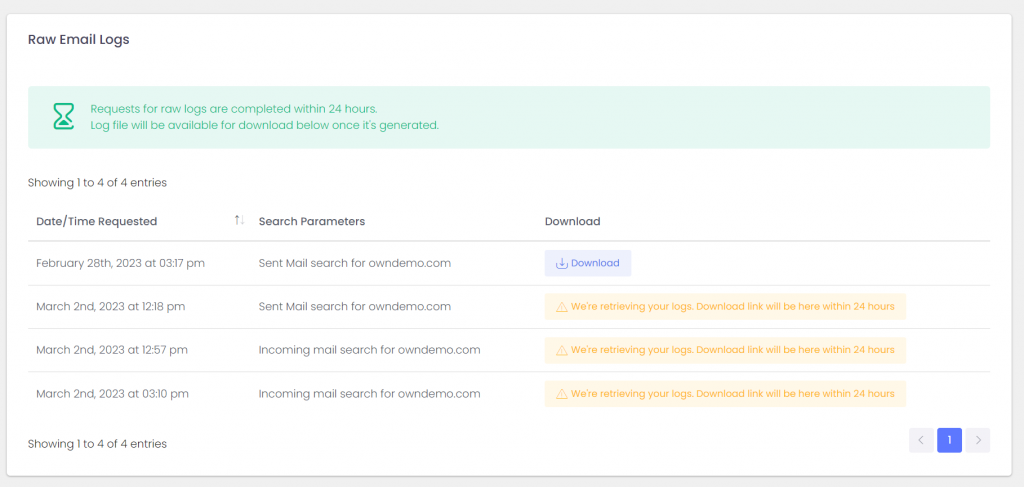
Logs will get pulled from all our services and will be available for download within 24 hours. Don’t let the boilerplate distract you, almost all of our clients will get their logs within the hour.
From there you can load the logs into your favorite analytics tool and dig for the errors and problems in the mail flow.
P.S. If you’re interested in contributing to our Service Provider Focus Groups please let us know!
Q: What is the difference between “Download raw logs” and “Download .csv”?
A: .csv export will save the current search results in a .csv file that can be used with Excel and other spreadsheet products. Search logs include to/from/subject/date/score/status only and are great for centralized analysis of messages that ExchangeDefender processed. By comparison, raw logs include SMTP protocol-level transactions/errors/notices that can help diagnose delivery and routing errors. So – .csv for Excel view for business analytics, raw log SMTP transactions for technical troubleshooting.
ExchangeDefender Invoices Got A Makeover!
We have listened to our partners and decided to redesign our invoicing system so it works better for our partners. One of the many benefits of having both Wrkoo and ExchangeDefender teams working together, (more details in our next webinar on September 10th, 2019) is that we can take great ideas from all sorts of businesses and adapt them to serve our IT partners better. Specifically, new ExchangeDefender invoices will be grouped by client:
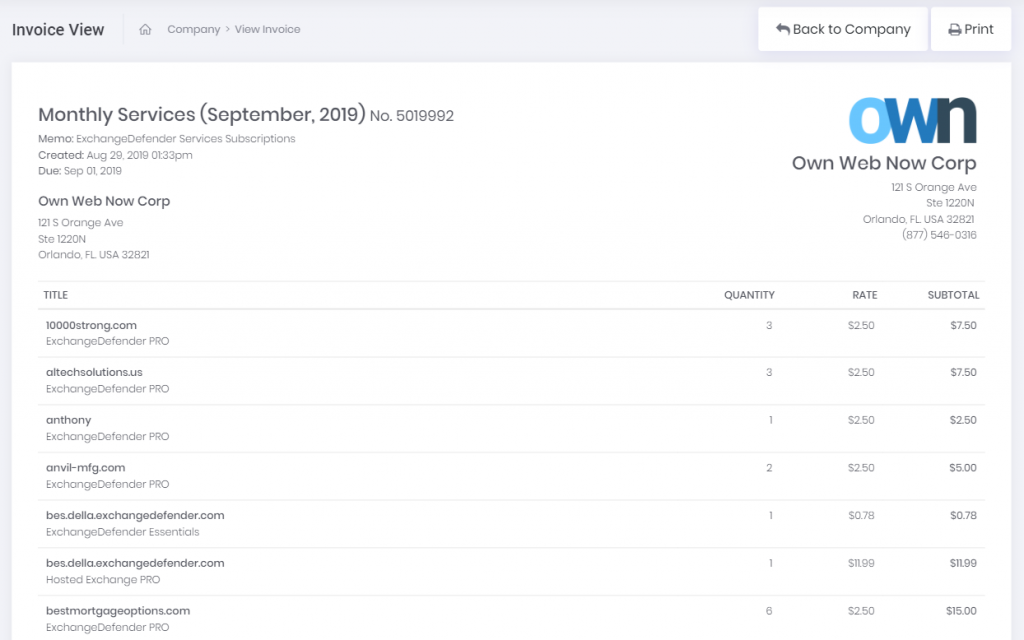
This will give you a clear indication of how many services each client is subscribed to, what type, amount, etc. For deeper dives by your CPA, you can filter and group by service and client so you can get exactly what you’re looking for (by default everything is sorted alphabetically, by the client):
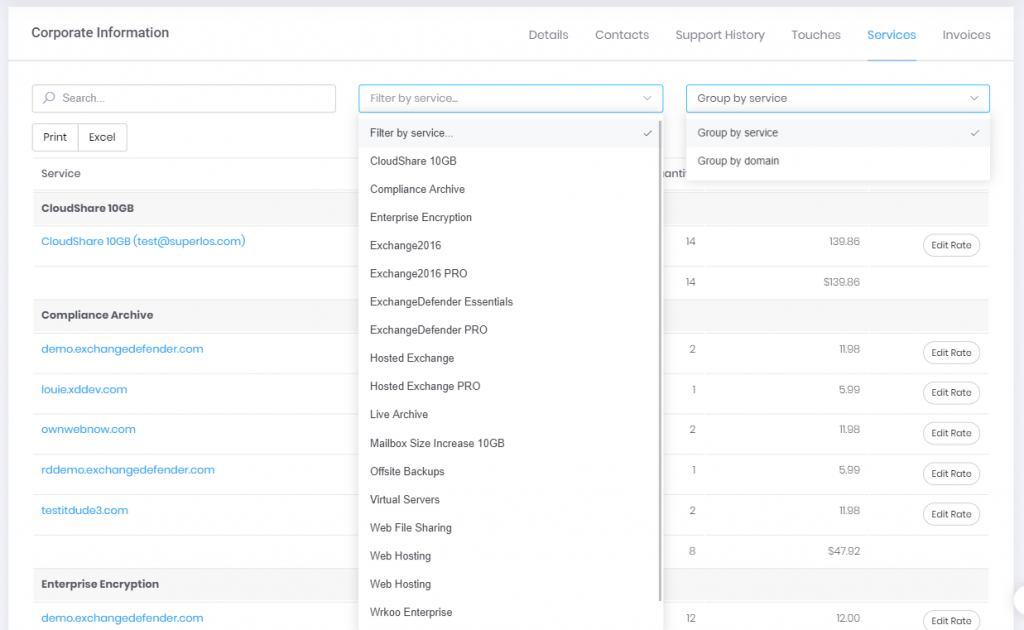
And for the full details, just tap the title:
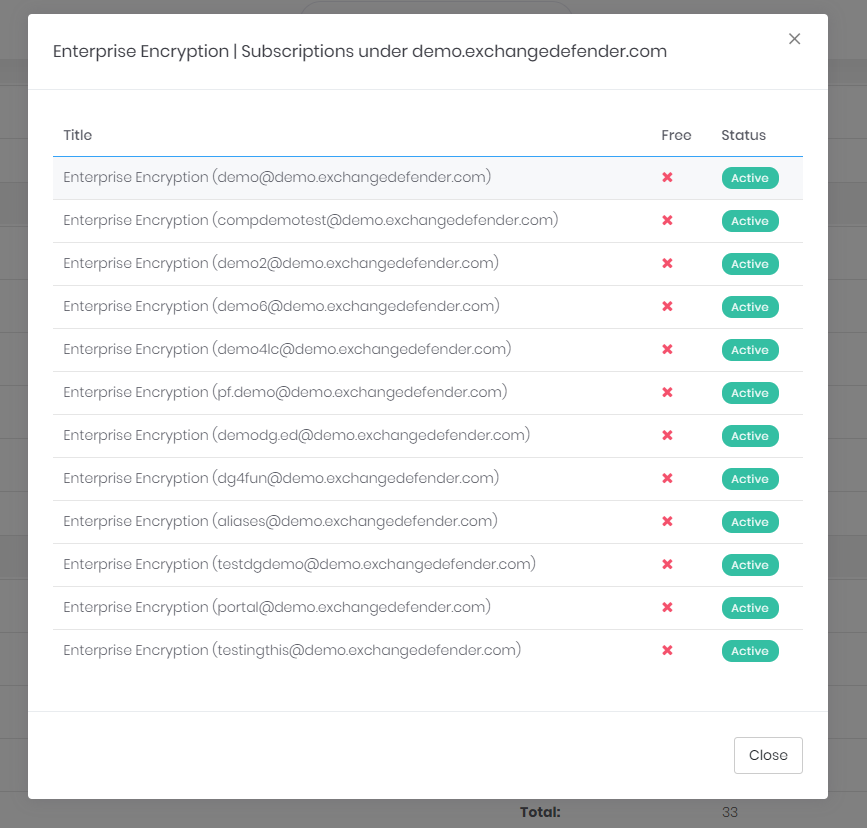
We’ll shortly be adding the ability to move services around, adjust titles, and for even more functionality as well as branding options you will have the ability to customize literally everything in your own Wrkoo portal.
Wrkoo and ExchangeDefender teams have been rolling out new features, listening to our partners needs, and you’re going to start seeing a lot of new features that result from that one-of-a-kind collaborative effort.
The best news though – as this is just a taste of what is coming – you’ll have to tune into our webinar on September 10th at NOON EDT. Trust us, you’re going to love what we’ve got coming!
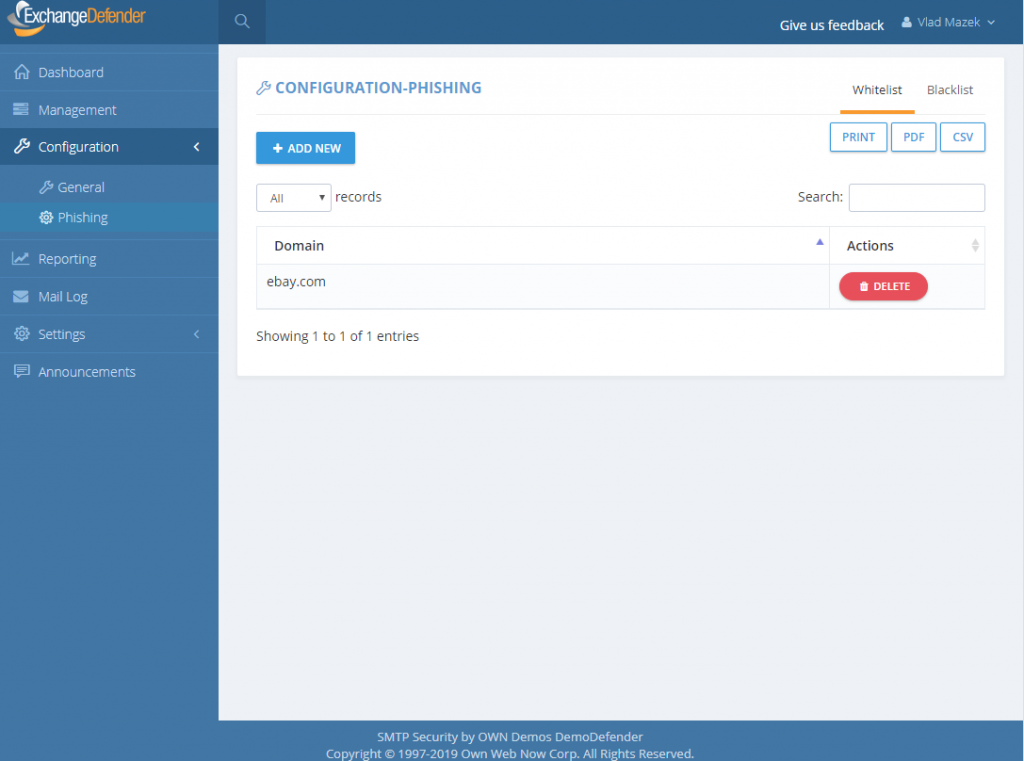
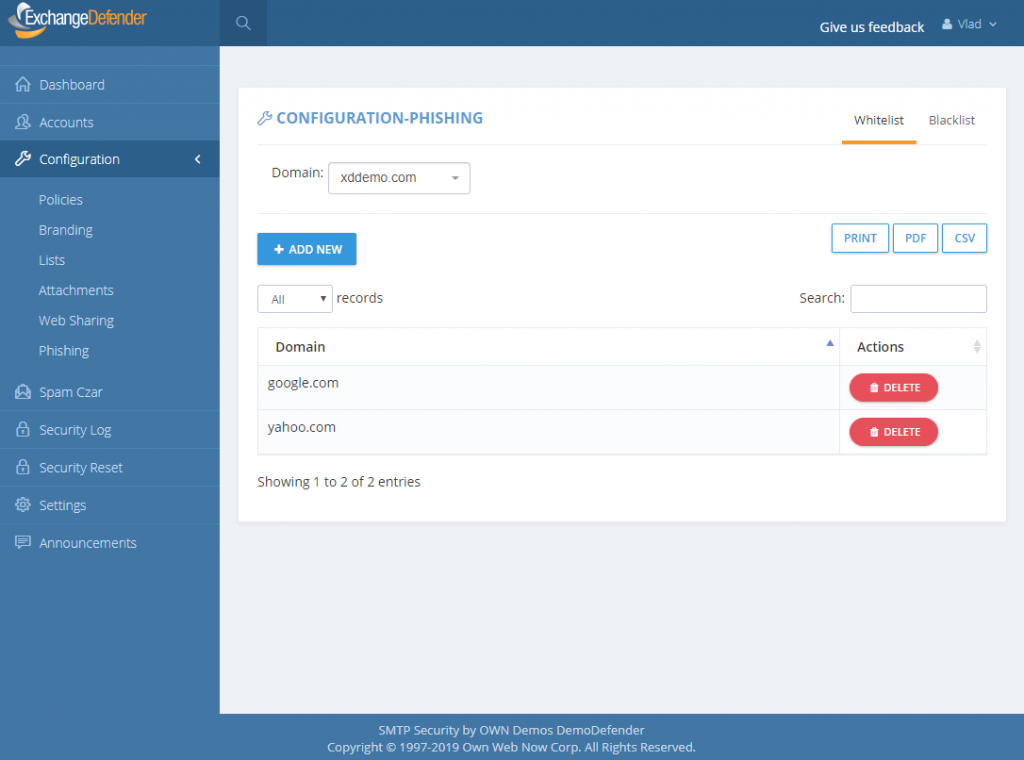
ExchangeDefender Phishing Firewall Whitelist and Blacklist explained
ExchangeDefender Phishing Firewall goes online tomorrow, and we wanted to explain our policy and our implementation of the URL rewriting/redirection because it is a departure from a traditional IT hierarchy where organizational policies override group and user requirements.
Our goal with ExchangeDefender PF is to provide a level of alert and notification to our clients that is designed to provide additional information about the link they clicked on. As we scale this service out, that will be it’s purpose: Be aware of what you clicked on, and prepare for what you’re about to see. Phishing, and spear phishing in particular, is designed to be a convincing fraudulent identity theft of an organization you know and trust (your bank, your coworker, your vendors) and our goal is to help you discern if something is valid or not.
Our whitelist/blacklist implementation is in line with “we inform, you decide” mantra, as we cannot outright block you from actually going to the dangerous site. That is the responsibility of your IT department, your network management, and your organization.
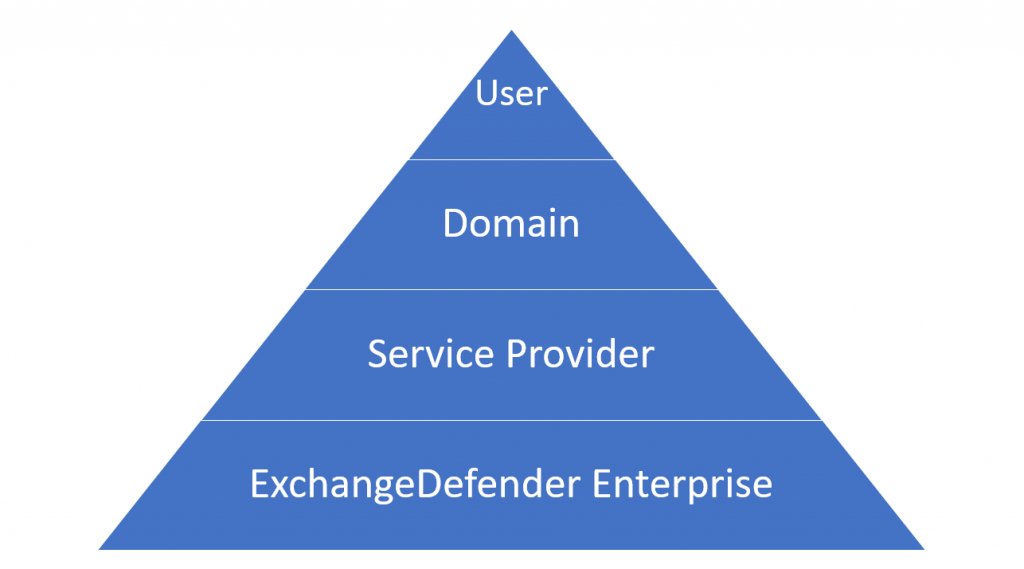
How do Whitelists and Blacklists work?
In ExchangeDefender we have 4 sets of whitelists and blacklists: user, domain/organization, service provider, and global. Our global lists are automatically populated for our service providers and when they protect a domain with ExchangeDefender, those entries are applied on the domain/organization level, and further down to the end user. As we continue to monitor, manage, and get additional intelligence about dangerous sites we will continue to curate these lists as a part of the service.
For example, we might find out that *.vlad8150.microsoft.net is a Microsoft Azure instance that is attempting to spread malware. We will promptly add it to our global blacklist and that site will now be blacklisted for every ExchangeDefender user. When they click on a link that leads them to that domain, they will see the ExchangeDefender PF notice with the URL in red. User will then have the option of ignoring it and proceeding to the site, or adding it to their whitelist. If they whitelist a domain/web site, any future requests will bypass ExchangeDefender PF web site and automatically redirect to the target URL.
The hierarchy of whitelists/blacklists is as follows, whichever rule is defined on the top is the one that is applied to the user when they click on a link.
But why, why not implement policies like NTFS, access list, or any other policy in which global deny rules override end user policies?
Simply put: Traffic blocking should be done on the network level. We are simply the alert service, we will advise you when we see something dangerous and it’s up to you to discern if the site is trustworthy or not. We believe that this implementation will cause the least amount of interruption to the day-to-day use.
That said, we have been working on additional controls and policies to help our service providers and CIO’s better enforce company security policies. As with everything, security policies must be implemented in layers – and dangerous content should be enforced in accordance to business requirements. This means that if your clients should not be downloading .exe files, the network firewall should be doing that. We don’t have the means to do that as an email service – users can right click on the email, put it in notepad, remove https://r.xdref.com/url= from the link and go straight to the web site.
How do we manage them?
ExchangeDefender PF whitelists are available at every level of ExchangeDefender. Simply add a site to either a whitelist and blacklist and ExchangeDefender will automatically propagate your rules down through the entire organization. Users will have the ability to add / block sites from the ExchangeDefender PF in real-time and their settings will be preserved in their account only.
P.S. Officially the service goes online tomorrow, unofficially it’s been in place for months we just haven’t rewritten a single URL except for the emails you received from us – we have worked very hard on the implementation and we don’t expect major problems but will have staff on hand around the clock to address any issues immediately. Spear phishing is an epidemic, over 90% of compromises start with a link in an email. We will handle any glitches, bugs, and issues as fast as possible and have full confidence that having an alerting service with potential problems is far more useful than having nothing and leaving clients exposed.
ExchangeDefender: Overhaul of Phishing Protection
ExchangeDefender is thrilled to announce the new Phishing Firewall in the cloud, going into full production – Wednesday, June 12th, 2019 for all ExchangeDefender Pro and Enterprise protected clients. The old way of highlighting, underlining, inserting warnings and so on will be removed from the service at the same time because it lacks the ability to protect clients in real-time.
The ExchangeDefender Phishing Firewall (EPF) is a real-time, active pishing protection. As ExchangeDefender processes inbound mail, it will rewrite every link to proxy it through EPF when user clicks on it. If the site is safe, the user will be automatically redirected to it and will not even know that EPF is in the way. If the site is not on the safe list, end users will see this warning:

They will have the option to just click on the link and proceed, add to whitelist (at which point they are automatically allowed through in the future) or add to blacklist.
Because of the way phishing works, and all identity theft or forgery in general, it is impossible to secure email messages in transit without making annoying modifications to the message that often distort the look and feel of it. Majority of those links are in the 95% of the mail that passes through ExchangeDefender as SPAM/SureSPAM, meaning that they would never even be seen by anyone. By moving the Phishing Firewall to the cloud, we can now secure every device and provide additional metrics and advisory on top of it to protect our clients from 0-day exploits.
This feature is provided to our clients free of charge and replaces expensive “security awareness training” solutions that users typically hate and do nothing to adequately secure the client. With Exchange Phishing Firewall we enable our clients to create custom policies, maintain whitelists, blacklists, get enterprise reporting and more. It further allows us to go one step beyond – in the upcoming releases we’ll offer the ability to display a screenshot of the site as well as link intelligence data (How long ago was the domain name registered? Where is the IP you’re about to go to located? Is the domain a close spelling error of a widely recognized site? Is the forged site just a cloud hosted Google, Microsoft or Amazon cloud service instance that is holding or redirecting you to another more dangerous location?)
If you’re currently on ExchangeDefender Essentials, we encourage you to schedule a demo with our team to check this feature out as it’s significantly cheaper than antivirus or “security training” solutions and will do a far better job. If you’re on ExchangeDefender Pro or ExchangeDefender Enterprise, you will get this feature free of charge. On Monday, June 10 we will send an email notification announcing this launch to our partners, MSPs, and Service Providers. On Tuesday, June 11 we will send an email notification to end users. Finally, on Wednesday, June 12th we will go live with the service and hope to minimize the annoyance of phishing once and for all. Email is the single most popular attack vector, with 91% of the compromises starting through a phishing attack, and we look forward to protecting all our users even better.
Phishing: Beware of Strangers
This Thursday, June 6th, we will be announcing a major overhaul in the way we deal with spear phishing SPAM. No, it’s not a mind-blowing patent-pending stroke-of-genius sort of stuff, it’s much closer to what your parents told you growing up: Don’t get into a car with strangers don’t click on links or open attachments from strangers.
In a way, ExchangeDefender has had protection from this issue for years. If you had a decent IT Solution Provider implementing ExchangeDefender for you, they would have setup your SPF record and eliminated this issue – but many don’t. Or they would have turned on ExchangeDefender protection where all messages spoofing/forging your domain would automatically get junked – almost none of them do. Which is why ExchangeDefender as a service has become less of an IT tool and more of an end user suite of services to get stuff done.
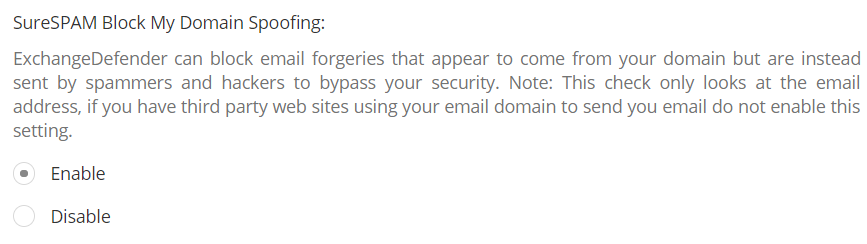
When features like this are left disabled “because they might become support issues” it becomes really difficult to secure users. But I get it, IT companies have a business to run too, which is why we’ve really stepped up our support efforts and are going to be there to help folks get things done without becoming an additional problem for the IT department. Doing so has really made us rethink how we implement features and how the service behavior needs to speak the same language as the end user. Which brings me to phishing beyond forgeries.
Can you spot a stranger?One of the new phishing protection features in ExchangeDefender will allow you to flag messages that are coming from outside of your organization. You will have two settings – to modify the subject and to modify the header of the message so when you look inside of your mailbox you’ll know what came from a stranger right away. Try it:
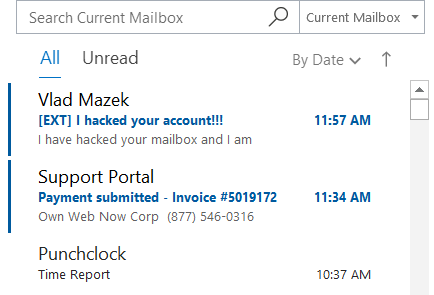
Even from the message listing you’ll know which messages shouldn’t even be opened. But suppose you ignored even that – you can set another warning, printed inside of the message, giving the user even more of an instruction of what to do.
Warning: Message was sent from outside of the organization. Do not click on links or open attachments if you don’t recognize the sender.
Far from subtle. And it has to be – because most people check email quickly, between tasks, or are simply interrupted by it. ExchangeDefender has your back, and we’ll make sure we alert you to possible issues before they become problems. Which we hope everyone will be aboard with.

Please join us, June 6th at Noon, for our NEW webinar featuring ExchangeDefender’s Phishing and Spoofing protection, plus see what’s new with Encryption, WFS, and Wrkoo!
Managing User Notifications
It’s no secret to anyone that’s been paying attention to this space that ExchangeDefender is getting a lot more user friendly – both in service and in design. We’ve been improving the way we communicate with our clients and our partners through efforts like embedded help, in-line training and support, real-time chat support, self service portals, NOC sites, etc
Next week we will launch a major feature in ExchangeDefender. It will address one of the biggest pain points in email security and it will give users a ton of control that will help close what is currently the biggest exploitable hole in email security: spear phishing. This will require us to give users a heads up about what they are about to see and training/documentation about how to use it to the fullest.
Which is where we have to make sure our partners are a part of the process too. During the webinar we’ll go over the details about how to insert branding and a message/note at https://admin.exchangedefender.com. This is generally not a big issue, since almost all of our partners would rather have us do more work for them than less, but if you’re really sensitive about this topic make sure you’re in the webinar to see what options you have and how to best leverage them for your own business purposes.
Looking forward to showing you all of this, and the redesigned ExchangeDefender Encryption product on June 6th at noon. https://register.gotowebinar.com/register/198414968804117507
New Feature: ExchangeDefender Announcements
ExchangeDefender Announcements
As you’ve probably noticed, our feature development has really picked up in 2018 and we have an even more aggressive product roadmap for 2019. To help make sure everyone is on top of all the new features and that our partners (MSP/VAR) have the best possible way to keep all of our clients informed of the new features, we’re happy to announce the Announcements feature!
Starting in late February 2019, our service providers and CIOs alike will have the ability to post announcements that will be featured prominently on the ExchangeDefender admin login page, inside the user control panel, and in the domain/org control panel. As you can imagine, this feature has a lot of flexibility to help you efficiently target the right organizations and users.
Announcement Feature Highlights:
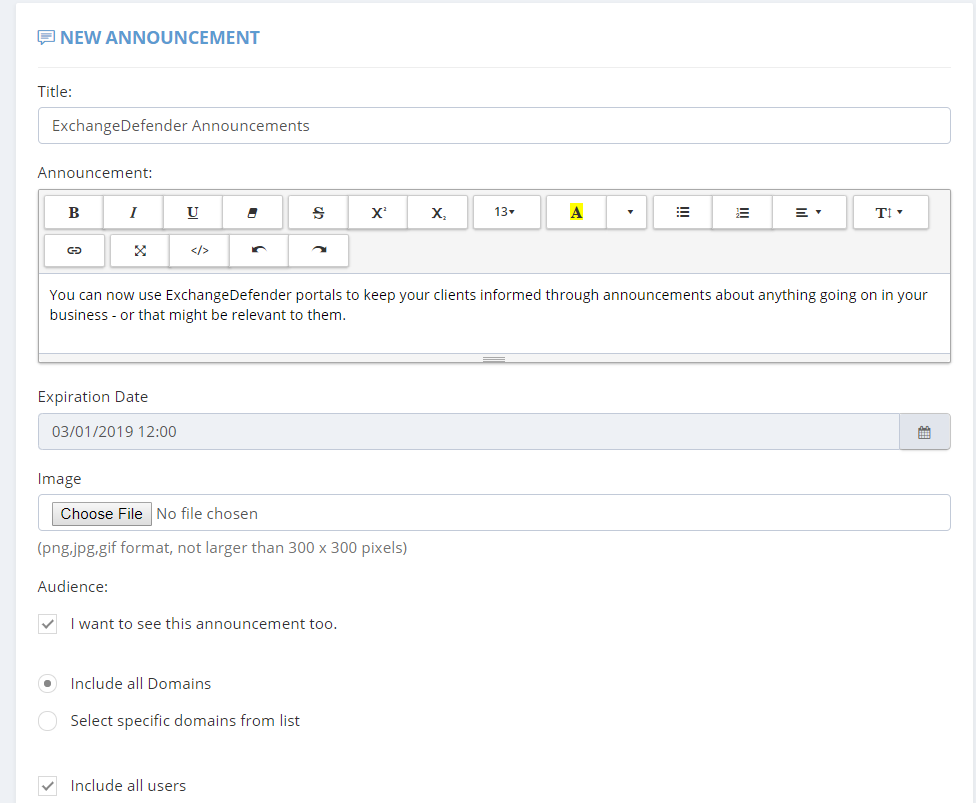
– Announcement title and announcement contents can include HTML and you can even insert a picture for each.
– You can set the announcement expiration date so that the announcement doesn’t show up after a certain date. This is great for sales promotions, webinar registrations, etc.
– You can scope the announcement: It can be global (for all of your domains) or it can be scoped down to a list of domains you choose. As most of our MSPs manage different kinds of organizations, one-size-fits-all announcements rarely work and this feature can help you solve that problem by targeting each organization specifically.
– I want to see this announcement too: If you’re in a larger organization you likely have personnel that is responsible for different departments or companies. Because announcements are visible on the login page of your portal as well as control panels for service provider, domain/org, and end users you have the ability to not show end user announcements to your IT and management staff.
– Include all users: You can even write specific announcements that are targeted at end users.
As ExchangeDefender gets bigger and as the complexity and service portfolio grows, we need to help our partners and CIOs communicate the new ExchangeDefender features more efficiently. Since you control your announcements it is up to you if you use it for ExchangeDefender related stuff or if you use it for your own promotion or if you delegate it to your companies to use it as another outlet to broadcast organization-specific but important news to everyone.
Most ExchangeDefender users interact with the service daily so you have a perfect (captive) spot to reach them about a product they are already interacting with – instead of having it burried in an email newsletter that they likely won’t read. This has been among the most demanded MSP features for years and we’re happy to deliver something with enough power and flexibility that will make both your tech/support people happy (so they can address possible support issues) as well as marketing/sales (so they can better target their message). You can only display up to two (2) announcements at a time though so the only bad news here is that you’ll have to prioritize.