How to Report Phishing Emails in Outlook: A Step-by-Step Guide

Phishing emails are deceptive messages designed to trick you into revealing personal information or installing malicious software. Reporting these emails helps protect your account and assists in improving Microsoft’s security measures. Here’s how you can report phishing emails in Outlook:

For Outlook on the Web (Outlook.com):
- Sign In: Log into your Outlook.com account.
- Select the Email: In your inbox, click the checkbox next to the phishing email you wish to report.
- Report as Phishing:
- At the top of the message list, click on the “Report” button.
- From the dropdown menu, select “Phishing”.
- Confirmation: The email will be moved to your Junk Email folder, and Microsoft will be notified to enhance their spam filters.
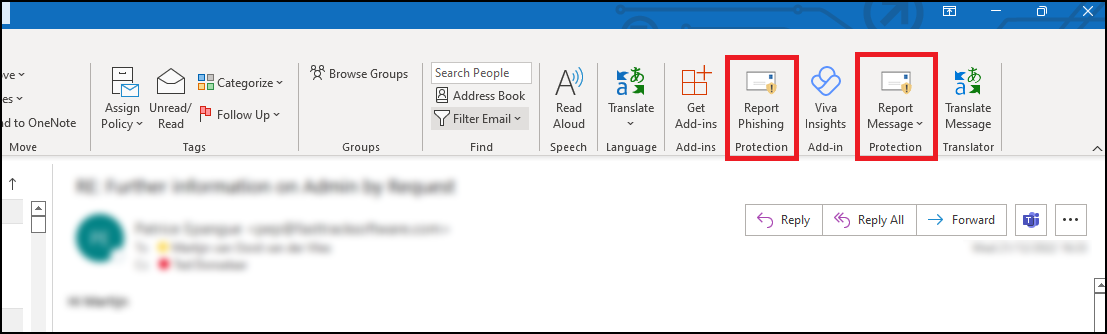
For Outlook Desktop Application (Windows):
- Open Outlook: Launch the Outlook application on your computer.
- Select the Email: In your inbox, click to highlight the phishing email.
- Access the Report Feature:
- Navigate to the “Home” tab in the ribbon at the top.
- Click on the “Report” button. If you don’t see this option, you may need to add the “Report Phishing” add-in:
- Click “Get Add-ins” in the ribbon.
- Search for “Report Phishing” and click “Add.”
- Report as Phishing:
- After adding the add-in, select the phishing email again.
- Click “Report” in the ribbon, then choose “Phishing.”
- Confirmation: The email will be moved to your Junk Email folder, and Microsoft will receive a report to improve their spam filters.
For Outlook Mobile App (iOS and Android):
- Open the App: Launch the Outlook app on your mobile device.
- Select the Email: Tap on the phishing email to open it.
- Access More Options:
- Tap the three-dot menu (⋮) at the top right corner of the email.Microsoft Support
- Report as Junk:
- Tap “Report Junk.”Microsoft Support
- Choose “Phishing” from the options provided.Microsoft Answers+1Gettysburg College+1
- Confirmation: The email will be moved to your Junk folder, and Microsoft will be notified to enhance their spam filters.
Source: Microsoft Support
Understanding Email Headers: How to Detect and Prevent Email Spoofing

Email Spoofing is a deceptive tactic where attackers forge email headers to make messages appear as if they originate from trusted sources. This technique is commonly used in phishing attacks to deceive recipients into revealing sensitive information or downloading malicious software. Understanding how to analyze email headers can help you identify and protect against such fraudulent activities.
What Are Email Headers?
Email headers are essential components of an email message that contain vital information about its origin, route, and authenticity. They include fields such as ‘From’, ‘To’, ‘Subject’, ‘Date’, and several others that provide a trail of the email’s journey from sender to recipient. While some of these fields are visible in your email client, many are hidden and can be viewed by accessing the email’s source or original message.
How to Access Email Headers:
- Outlook: Open the email, click on “File,” then “Properties,” and view the “Internet headers” box.
- Gmail: Open the email, click on the three vertical dots next to the reply arrow, and select “Show original.”
- Yahoo Mail: Open the email, click on the three horizontal dots, and select “View raw message.”
Delivered-To: user@example.com
Received: by 2002:a17:902:5307:0:0:0:0 with SMTP id v7csp1452976ejw;
Wed, 03 Apr 2024 12:34:56 -0700 (PDT)
X-Received: by 2002:a1c:4b09:: with SMTP id g9mr1234567wma.67.1712172896123;
Wed, 03 Apr 2024 12:34:56 -0700 (PDT)
Return-Path: sender@domain.com
Received: from mail.domain.com (mail.domain.com. [123.45.67.89])
by mx.google.com with ESMTPS id b7si1234567qke.287.2024.04.03.12.34.56
for user@example.com
(version=TLS1_3 cipher=TLS_AES_256_GCM_SHA384 bits=256/256);
Wed, 03 Apr 2024 12:34:56 -0700 (PDT)
Received-SPF: pass (google.com: domain of sender@domain.com designates 123.45.67.89 as permitted sender) client-ip=123.45.67.89;
Authentication-Results: mx.google.com;
dkim=pass header.i=@domain.com header.s=selector1 header.b=abcd1234;
spf=pass (google.com: domain of sender@domain.com designates 123.45.67.89 as permitted sender) smtp.mailfrom=sender@domain.com;
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=domain.com
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=domain.com; s=selector1; t=1712172896;
bh=VYgWqzXb1q83L9efk9EtqvL7W0U=;
h=Date:From:To:Subject:Message-ID;
b=abcd1234efgh5678ijkl9012mnop3456qrstuvwx…
Date: Wed, 3 Apr 2024 12:34:56 -0700
From: Sender Name sender@domain.com
To: Recipient Name user@example.com
Message-ID: CAJ1234567890abcdefg@mail.domain.com
Subject: Important Update on Your Subscription
MIME-Version: 1.0
Content-Type: text/plain; charset=”UTF-8″
Content-Transfer-Encoding: 7bit
Key Email Header Fields to Examine:
- From: Indicates the sender’s email address. However, this field can be easily forged and should not be solely relied upon to verify the sender’s identity.
- Reply-To: Specifies the email address to which replies should be sent. Discrepancies between the ‘From’ and ‘Reply-To’ addresses can be a red flag for spoofing.
- Received: Shows the servers that handled the email during its transmission. By examining the sequence of ‘Received’ fields, you can trace the path the email took and identify anomalies.
- Return-Path: Indicates where non-delivery receipts (bounces) are sent. A mismatch between the ‘Return-Path’ and ‘From’ addresses may suggest spoofing.
- Received-SPF: Displays the result of the Sender Policy Framework (SPF) check, which verifies if the email comes from an authorized server. A ‘Fail’ or ‘Softfail’ status can indicate potential spoofing.
Detecting Spoofed Emails:
- Examine the ‘Received’ Fields: Trace the email’s path by reviewing the ‘Received’ fields. Inconsistencies or unfamiliar server names can be indicators of spoofing.
- Check SPF, DKIM, and DMARC Results: These authentication mechanisms help verify the legitimacy of the email. Failures or absence of these checks can be warning signs.
- Analyze the ‘Return-Path’ and ‘Reply-To’ Fields: Ensure these fields match the ‘From’ address and are consistent with the sender’s domain.
- Use Email Header Analysis Tools: Online tools like MxToolbox’s Email Header Analyzer can simplify the process by parsing headers and highlighting issues.
By understanding and analyzing email headers, you can better detect and prevent email spoofing attempts, thereby safeguarding your personal and organizational security. Need extra security? Try ExchangeDefender PRO for free!
Are the BCBS settlement emails legit?

The recent Blue Cross Blue Shield (BCBS) settlement has led to a wave of emails notifying individuals about potential compensation. While many of these messages are legitimate, cybercriminals are using this as an opportunity to launch phishing scams. Here’s what you need to know to protect yourself.
What Is the BCBS Settlement?
BCBS agreed to a $2.67 billion settlement in an antitrust lawsuit alleging the company engaged in anti-competitive practices. Individuals or entities that had BCBS health insurance or administrative services between February 2008 and October 2020 may be eligible for compensation.
The official settlement administrator has been sending notifications via email and mail. Legitimate emails come from Notice@BCBSsettlement.com, and the official website is www.BCBSsettlement.com.
How Scammers Are Exploiting the Settlement
Cybercriminals are taking advantage of this widespread settlement by sending fraudulent emails that:
- Contain suspicious links, such as those prompting users to “request an electronic debit card”
- Use convincing BCBS logos and branding to appear legitimate
- Request personal or financial information
Users on forums like Reddit have reported phishing attempts disguised as official settlement notifications. Clicking on these fake links can lead to identity theft, malware infections, or financial fraud.
How to Protect Yourself
- Verify the Sender – Legitimate emails will come from Notice@BCBSsettlement.com.
- Avoid Clicking Links – Instead of clicking email links, visit the official website directly by typing www.BCBSsettlement.com in your browser.
- Contact the Official Source – If you’re unsure, reach out to the settlement administrator via info@BCBSsettlement.com or call (888) 681-1142.
- Use Email Security Solutions – A robust security tool like ExchangeDefender PRO can help filter out phishing emails before they reach your inbox.
Stay One Step Ahead with ExchangeDefender
With the rise of sophisticated phishing attacks, businesses need reliable email security solutions to prevent scams like these. ExchangeDefender PRO offers advanced phishing detection, real-time email filtering, and security awareness training to keep your organization safe from evolving cyber threats.
Protect your inbox today—ask us for a demo of ExchangeDefender PRO!
How to Spot and Avoid Geek Squad Email Scams
In recent years, scammers have increasingly impersonated Geek Squad, Best Buy’s tech support service, to deceive individuals into divulging personal information or making unnecessary payments. Understanding how these scams operate and how to recognize them is crucial for safeguarding your personal data and finances.
Understanding the Geek Squad Email Scam
The Geek Squad email scam is a phishing attempt where fraudsters pose as Geek Squad representatives to steal personal information or trick victims into paying for fake services. These emails often appear legitimate, making it challenging to distinguish them from authentic communications.
Common Types of Geek Squad Email Scams
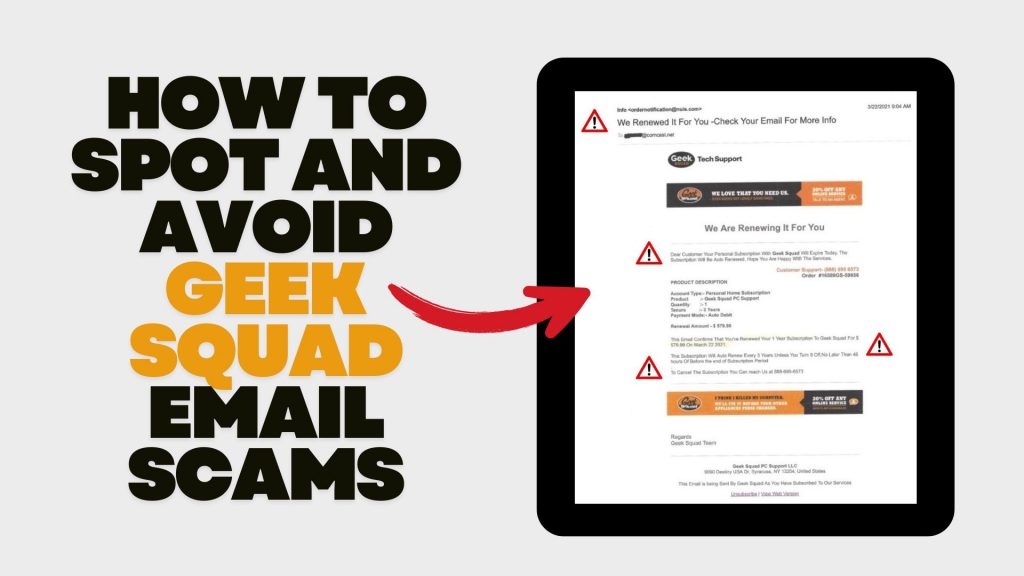
- Auto-Renewal Scam: Scammers send emails stating that your Geek Squad subscription is about to auto-renew at a substantial cost. The email urges you to call a provided number or click a link to cancel the subscription, aiming to extract personal and financial details.
- Fake Antivirus Software Offer: You might receive emails warning of malware infections among Geek Squad customers, offering free antivirus software downloads. However, these downloads are malicious and designed to infect your device, steal data, or gain remote access.
- Password Reset Scam: Emails claim suspicious activity on your Best Buy account, prompting you to reset your password via a provided link. The link leads to a fake website designed to capture your login credentials, allowing scammers unauthorized access to your account.
Recognizing Scam Emails
Be vigilant for the following signs:
- Sense of Urgency: Scammers often pressure you to act quickly, creating a false sense of urgency.
- Suspicious Sender Addresses: Examine the sender’s email address for inconsistencies or misspellings. Official communications will come from a legitimate Best Buy domain.
- Generic Greetings: Emails that don’t address you by name, such as “Dear Customer,” may be fraudulent.
- Poor Grammar and Spelling: Legitimate companies maintain professional communication standards.
- Unsolicited Attachments or Links: Avoid clicking on links or downloading attachments from unknown senders.
Protective Measures
- Verify Communications: If you receive a suspicious email, contact Geek Squad or Best Buy directly using official contact information from their website.
- Avoid Unsolicited Links and Downloads: Refrain from clicking on links or downloading attachments from unknown sources.
- Use Security Software: Ensure your devices are equipped with reputable antivirus and anti-malware programs.
- Stay Informed: Educate yourself about common phishing tactics to recognize and avoid potential scams.
Reporting Scams: If you encounter a Geek Squad scam, report it to Best Buy. Additionally, file a complaint with the Federal Trade Commission (FTC) through their Complaint Assistant.
Avoid Netflix Payment Scams: Recognize Phishing Emails
In recent months, a sophisticated email scam targeting Netflix users has emerged, aiming to steal personal and financial information. These phishing emails closely mimic legitimate Netflix communications, making them particularly deceptive. If you don’t have ExchangeDefender PRO Phishing protection, then here’s what you need to know:
How the Scam Operates
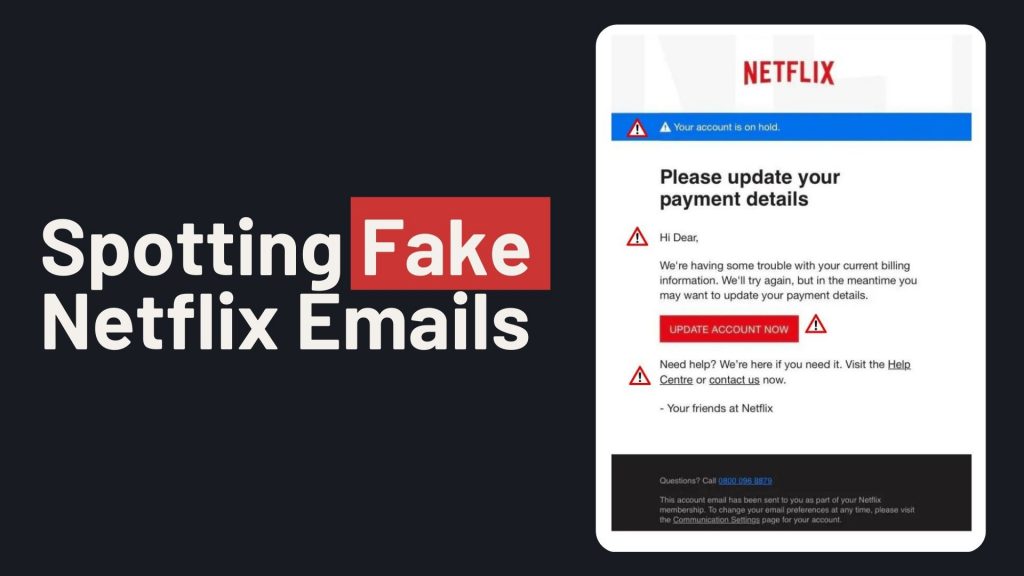
Victims receive emails claiming issues with their Netflix account, such as payment problems or account suspensions. The email urges recipients to update their payment details via a provided link, which leads to a fake Netflix login page. Entering information on this page allows scammers to harvest login credentials and credit card details.
Identifying the Scam
- Sender’s Email Address: Scam emails may originate from unofficial domains, such as an iCloud domain, rather than Netflix’s official domain.
- Urgent Language: The message may claim your account is on hold and prompt immediate action to update payment information.
- Suspicious Links: Hovering over links may reveal URLs that don’t direct to Netflix’s official website.
Protective Measures
- Avoid Clicking Links: Do not click on links or open attachments from unsolicited emails.
- Verify Authenticity: Log in directly through the official Netflix website to check your account status.
- Report Suspicious Emails: Forward any dubious emails to phishing@netflix.com.
- Monitor Financial Statements: Regularly check your bank and credit card statements for unauthorized transactions.
Netflix’s Official Stance
Netflix states it will never ask for personal information, such as credit card numbers or passwords, via email or text messages. By staying vigilant and recognizing the signs of phishing attempts, you can protect your personal and financial information from these scams.
Stay Safe from Zelle Scams: Simple Tips to Protect Your Money

Sending money through apps like Zelle is super convenient. But with that convenience comes the risk of scams. Let’s break down what these scams look like and how you can keep your hard-earned cash safe.
What’s a Zelle Scam?
Scammers have gotten crafty. They might send you a message or give you a call pretending to be from your bank or even Zelle itself. They’ll claim there’s an issue with your account or a suspicious transaction and urge you to act quickly. Their goal? To trick you into giving up personal information or sending them money.
Common Tricks Scammers Use:
- Fake Problems: They’ll say there’s unauthorized activity or that your account will be locked.
- Phony Links: They’ll send links that look official but lead to fake websites designed to steal your info.
- Too-Good-To-Be-True Offers: They might offer amazing deals or opportunities that require immediate payment.
How to Protect Yourself:
- Pause and Think: Don’t rush. Scammers rely on panic.
- Verify Before Acting: If you get a suspicious message, contact your bank
or Zelle directly using official channels. - Avoid Unsolicited Links: Don’t click on unexpected links or download attachments
from unknown senders.
ExchangeDefender PRO: Your Email Safety Net
One of the ways scammers reach out is through phishing emails. To shield yourself from these threats, consider using email security services like ExchangeDefender PRO. It offers top-notch protection against phishing attempts, spam, and other email-based threats. With features like advanced threat detection and real-time monitoring, it acts as a robust defense for your digital communications.
How to Spot & Avoid the Latest DocuSign Scam

Cybercriminals are getting craftier, and one of their favorite new tricks is impersonating trusted services like DocuSign. If you’ve recently received an email urging you to sign a document or verify your account, think twice before clicking! The latest wave of DocuSign email scams is designed to steal your personal information and compromise your security.
How the DocuSign Email Scam Works
Scammers send fake emails that appear to be from DocuSign, using official-looking branding and urgent messaging. Here’s how the scam typically unfolds:
- Fake Email Notification – You receive an email that looks like it’s from DocuSign, requesting you to review or sign a document.
- Urgency & Pressure – The email often claims the document requires your immediate attention, creating a sense of urgency.
- Malicious Links – Clicking the link redirects you to a fraudulent website that mimics DocuSign’s login page.
- Credential Theft – If you enter your login details, scammers steal them to access your DocuSign or other linked accounts.
- Malware Installation – Some scams include attachments or links that, when clicked, install malware on your device.
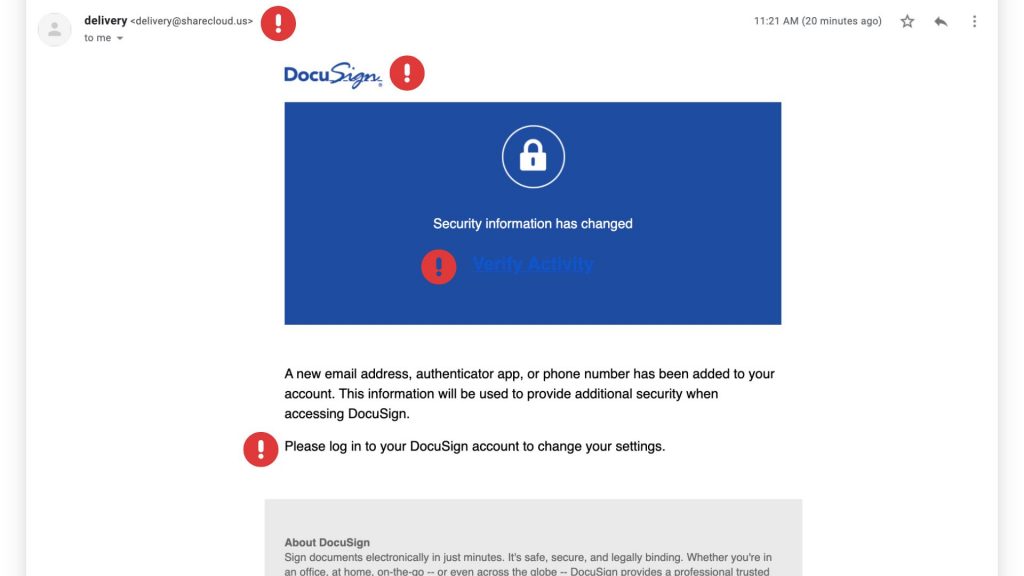
Red Flags to Watch For
These scams can be convincing, but there are a few telltale signs that can help you identify them:
✔ Suspicious Sender Address – Official DocuSign emails come from @docusign.com or @docusign.net, not random or misspelled domains.
✔ Unusual Language or Errors – Many phishing emails contain typos, grammatical mistakes, or odd phrasing. Look for fake logos as well!
✔ Unexpected Requests – If you weren’t expecting a document, verify with the sender before opening anything.
✔ Fake Links – Hover over any links in the email (without clicking) to see the actual URL. If it’s not docusign.com, don’t trust it.
✔ Generic Greetings – Scammers often use “Dear Customer” instead of your actual name.
How to Stay Safe
Protect yourself and your business from falling victim to these scams by following these best practices:
🔹 Verify Directly – Instead of clicking email links, go to www.docusign.com and log in to check if a document is waiting.
🔹 Enable Multi-Factor Authentication (MFA) – Adding an extra layer of security can prevent unauthorized access to your account.
🔹 Report Suspicious Emails – If you receive a fraudulent DocuSign email, forward it to spam@docusign.com and then delete it.
🔹 Keep Security Software Updated – Use up-to-date antivirus and security software to detect and block phishing attempts.
🔹 Educate Your Team – Ensure employees know how to recognize and avoid phishing emails.
Blue Cross Blue Shield Phishing Scam on the Rise

Blue Cross Blue Shield (BCBS) phishing emails are fraudulent messages designed to trick recipients into providing personal information, such as login credentials, Social Security numbers, or financial details. These emails often appear to come from BCBS but are actually sent by scammers aiming to steal sensitive data.
Common Tactics Used in BCBS Phishing Emails:
- Fake Account Alerts – The email may claim there’s an issue with your BCBS account, such as suspicious activity or a need to update your information.
- Urgent Payment Requests – Scammers may say you owe money for coverage or claim a payment failed, urging you to click a link.
- Fake Benefits or Refunds – Some phishing emails promise refunds, benefits, or changes to your health plan, requiring you to enter personal details.
- Malicious Links or Attachments – These emails often include links that lead to fake BCBS login pages or attachments containing malware.
- Spoofed Email Addresses – The sender’s email address may look official but often has subtle misspellings or extra characters (e.g.,
support@bcbs-secure.cominstead ofsupport@bcbs.com).

How to Spot and Avoid BCBS Phishing Emails:
✅ Check the Sender’s Email – Verify the email address carefully. Official BCBS emails come from legitimate domains.
✅ Look for Typos & Grammar Mistakes – Many phishing emails contain odd phrasing, spelling errors, or unprofessional formatting.
✅ Hover Over Links (But Don’t Click!) – Hover your mouse over links to see the actual destination URL. If it looks suspicious, don’t click.
✅ Never Enter Personal Info via Email – BCBS will never ask for sensitive data like passwords, Social Security numbers, or banking details via email.
✅ Contact BCBS Directly – If you’re unsure, call BCBS using the official number on their website, not the one in the email.
What to Do If You Receive a BCBS Phishing Email:
📌 Do NOT Click on Any Links or Attachments
📌 Report the Email – Forward phishing emails to BCBS’s fraud department or report them to the FTC at reportfraud.ftc.gov.
📌 Delete the Email Immediately
📌 Monitor Your Accounts – If you accidentally clicked a link, change your BCBS password immediately and watch for unauthorized activity.
Always stay cautious—cybercriminals keep improving their scams, but with awareness, you can protect yourself from falling victim! 🚨
Smishing: The Text Message Scam You Need to Know!

Cybercriminals are always looking for new ways to trick people, and one of the latest and most dangerous scams is smishing. But what exactly is smishing, and how can you protect yourself? Let’s break it down in simple terms.
What Is Smishing?
Smishing (a combination of “SMS” and “phishing”) is a type of cyberattack where scammers send fake text messages to trick people into giving up personal information. These messages often pretend to be from legitimate sources like banks, delivery services, or even government agencies.
The goal? To get you to click on a malicious link, call a fake customer service number, or reveal sensitive details such as passwords, credit card numbers, or Social Security numbers.
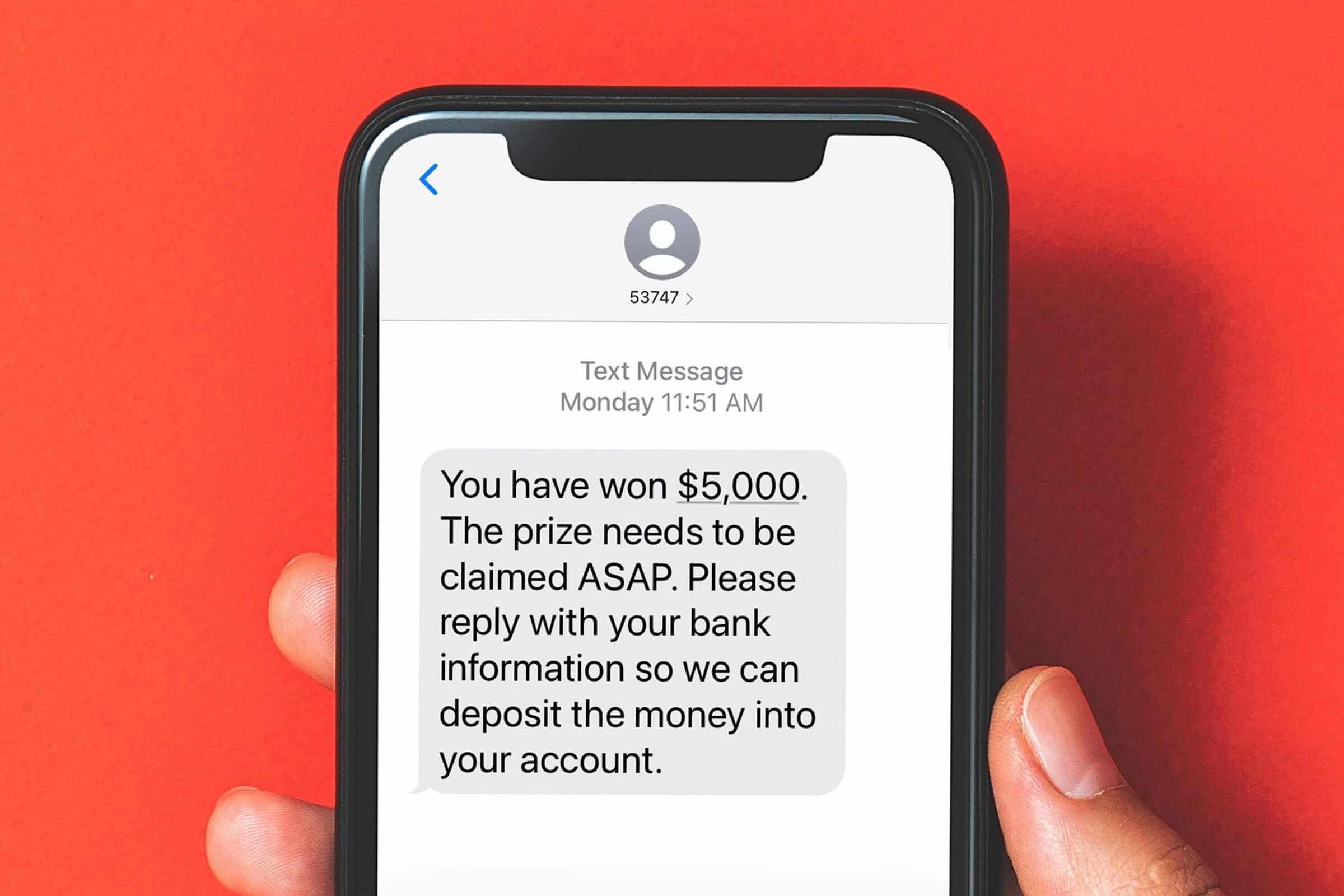
How Does Smishing Work?
Smishing messages typically create a sense of urgency, making you feel like you must act immediately. Here are a few common examples:
- Bank Alerts: “Urgent: Your account has been compromised. Click here to verify your identity.”
- Delivery Notifications: “Your package is delayed! Click this link to confirm your details.”
- Government Scams: “You are eligible for a tax refund. Claim it now by following this link.”
Once you click on the link, you might be taken to a fake website designed to look like a real one. If you enter your information, it goes straight into the hands of cybercriminals.
How to Protect Yourself from Smishing Attacks
- Don’t Click Links in Unsolicited Messages – If you receive a text from an unknown sender with a link, be cautious. Go directly to the company’s website instead.
- Verify the Sender – If a message appears to be from your bank or another trusted organization, contact them directly using a verified phone number.
- Look for Red Flags – Watch out for poor grammar, strange URLs, and urgent language designed to pressure you into acting quickly.
- Use Security Features – Many mobile carriers offer spam message filtering. Enable these features to reduce unwanted messages.
- Report Suspicious Messages – Most mobile carriers allow you to report spam texts by forwarding them to 7726 (SPAM).
Smishing is on the rise, but you don’t have to fall victim to it. By staying informed and practicing good cybersecurity habits, you can keep your personal information safe. If you’re ever unsure about a message, always take a moment to verify before responding.
For more cybersecurity tips and updates, stay tuned to the ExchangeDefender blog!
What All Phishing Scams Have in Common

Phishing. We hear about it constantly, but with new variations popping up all the time, it can be hard to keep track. While the delivery methods and specific lures might change, there’s a common thread that runs through every single phishing scam. Understanding these core elements is key to protecting yourself and your information.
At ExchangeDefender, we’re dedicated to helping you stay safe online. So, let’s break down the common characteristics that define all phishing attempts.
1. The Art of Deception: Impersonating Trust
The foundation of any phishing scam is deception. Scammers meticulously craft their messages to appear as if they’re coming from a trusted source. This could be:
- Big-name companies: Think PayPal, Amazon, Microsoft, or major banks. Scammers often use logos, branding, and even copy website layouts to create a convincing facade.
- Government agencies: The IRS, Social Security Administration, and other government bodies are frequently impersonated to instill a sense of authority and urgency.
- People you know: Scammers might spoof email addresses or social media profiles to impersonate colleagues, friends, family members, or even your boss.
The goal is to trick you into believing the message is legitimate, lowering your guard and making you more susceptible to their tactics.

2. The Pressure: Creating Urgency and Alarm
Once they’ve established a false sense of trust, scammers introduce a sense of urgency or alarm. This is designed to pressure you into acting quickly without thinking critically. Common tactics include:
- Account alerts: Claiming your account has been compromised, suspended, or limited.
- Security breaches: Warning of a data breach or security incident that requires immediate action.
- Missed payments or deadlines: Threatening late fees, service interruption, or legal action.
- Limited-time offers or prizes: Luring you with the promise of a reward if you act fast.
Scammers hope to bypass your rational thinking and trigger an emotional response by creating a sense of urgency, leading you to make a hasty decision.
3. The Hook: Requesting Information or Action
The final piece of the phishing puzzle is the hook – the specific action the scammer wants you to take. This usually involves:
- Clicking a malicious link: These links lead to fake websites designed to steal your login credentials, financial information, or install malware on your device.
- Opening an infected attachment: Attachments can contain viruses, ransomware, or other malicious software.
- Providing personal information directly: Scammers might ask you to reply to the email with your username, password, Social Security number, or other sensitive data.
The hook is the culmination of the scam, the point where the scammer attempts to extract valuable information or gain unauthorized access to your systems.
Staying Safe: The ExchangeDefender Approach
At ExchangeDefender, we believe that education is the first line of defense against phishing attacks. By understanding these three core elements – deception, urgency, and the hook – you can significantly reduce your risk of falling victim.
Here are a few key takeaways:
- Be skeptical of any unexpected communication, especially those requesting personal information or urging immediate action.
- Always verify the sender’s identity through a separate communication channel.
- Never click links in suspicious emails. Instead, type the website address directly into your browser.
- Enable multi-factor authentication whenever possible for an extra layer of security.
By staying vigilant and informed, you can avoid getting hooked by phishing scams and protect your valuable information. #cybersecurity #phishing #scams #onlinesafety #exchangedefender





