Understanding Email Headers: How to Detect and Prevent Email Spoofing

Email Spoofing is a deceptive tactic where attackers forge email headers to make messages appear as if they originate from trusted sources. This technique is commonly used in phishing attacks to deceive recipients into revealing sensitive information or downloading malicious software. Understanding how to analyze email headers can help you identify and protect against such fraudulent activities.
What Are Email Headers?
Email headers are essential components of an email message that contain vital information about its origin, route, and authenticity. They include fields such as ‘From’, ‘To’, ‘Subject’, ‘Date’, and several others that provide a trail of the email’s journey from sender to recipient. While some of these fields are visible in your email client, many are hidden and can be viewed by accessing the email’s source or original message.
How to Access Email Headers:
- Outlook: Open the email, click on “File,” then “Properties,” and view the “Internet headers” box.
- Gmail: Open the email, click on the three vertical dots next to the reply arrow, and select “Show original.”
- Yahoo Mail: Open the email, click on the three horizontal dots, and select “View raw message.”
Delivered-To: user@example.com
Received: by 2002:a17:902:5307:0:0:0:0 with SMTP id v7csp1452976ejw;
Wed, 03 Apr 2024 12:34:56 -0700 (PDT)
X-Received: by 2002:a1c:4b09:: with SMTP id g9mr1234567wma.67.1712172896123;
Wed, 03 Apr 2024 12:34:56 -0700 (PDT)
Return-Path: sender@domain.com
Received: from mail.domain.com (mail.domain.com. [123.45.67.89])
by mx.google.com with ESMTPS id b7si1234567qke.287.2024.04.03.12.34.56
for user@example.com
(version=TLS1_3 cipher=TLS_AES_256_GCM_SHA384 bits=256/256);
Wed, 03 Apr 2024 12:34:56 -0700 (PDT)
Received-SPF: pass (google.com: domain of sender@domain.com designates 123.45.67.89 as permitted sender) client-ip=123.45.67.89;
Authentication-Results: mx.google.com;
dkim=pass header.i=@domain.com header.s=selector1 header.b=abcd1234;
spf=pass (google.com: domain of sender@domain.com designates 123.45.67.89 as permitted sender) smtp.mailfrom=sender@domain.com;
dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=domain.com
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=domain.com; s=selector1; t=1712172896;
bh=VYgWqzXb1q83L9efk9EtqvL7W0U=;
h=Date:From:To:Subject:Message-ID;
b=abcd1234efgh5678ijkl9012mnop3456qrstuvwx…
Date: Wed, 3 Apr 2024 12:34:56 -0700
From: Sender Name sender@domain.com
To: Recipient Name user@example.com
Message-ID: CAJ1234567890abcdefg@mail.domain.com
Subject: Important Update on Your Subscription
MIME-Version: 1.0
Content-Type: text/plain; charset=”UTF-8″
Content-Transfer-Encoding: 7bit
Key Email Header Fields to Examine:
- From: Indicates the sender’s email address. However, this field can be easily forged and should not be solely relied upon to verify the sender’s identity.
- Reply-To: Specifies the email address to which replies should be sent. Discrepancies between the ‘From’ and ‘Reply-To’ addresses can be a red flag for spoofing.
- Received: Shows the servers that handled the email during its transmission. By examining the sequence of ‘Received’ fields, you can trace the path the email took and identify anomalies.
- Return-Path: Indicates where non-delivery receipts (bounces) are sent. A mismatch between the ‘Return-Path’ and ‘From’ addresses may suggest spoofing.
- Received-SPF: Displays the result of the Sender Policy Framework (SPF) check, which verifies if the email comes from an authorized server. A ‘Fail’ or ‘Softfail’ status can indicate potential spoofing.
Detecting Spoofed Emails:
- Examine the ‘Received’ Fields: Trace the email’s path by reviewing the ‘Received’ fields. Inconsistencies or unfamiliar server names can be indicators of spoofing.
- Check SPF, DKIM, and DMARC Results: These authentication mechanisms help verify the legitimacy of the email. Failures or absence of these checks can be warning signs.
- Analyze the ‘Return-Path’ and ‘Reply-To’ Fields: Ensure these fields match the ‘From’ address and are consistent with the sender’s domain.
- Use Email Header Analysis Tools: Online tools like MxToolbox’s Email Header Analyzer can simplify the process by parsing headers and highlighting issues.
By understanding and analyzing email headers, you can better detect and prevent email spoofing attempts, thereby safeguarding your personal and organizational security. Need extra security? Try ExchangeDefender PRO for free!
Smishing: The Text Message Scam You Need to Know!

Cybercriminals are always looking for new ways to trick people, and one of the latest and most dangerous scams is smishing. But what exactly is smishing, and how can you protect yourself? Let’s break it down in simple terms.
What Is Smishing?
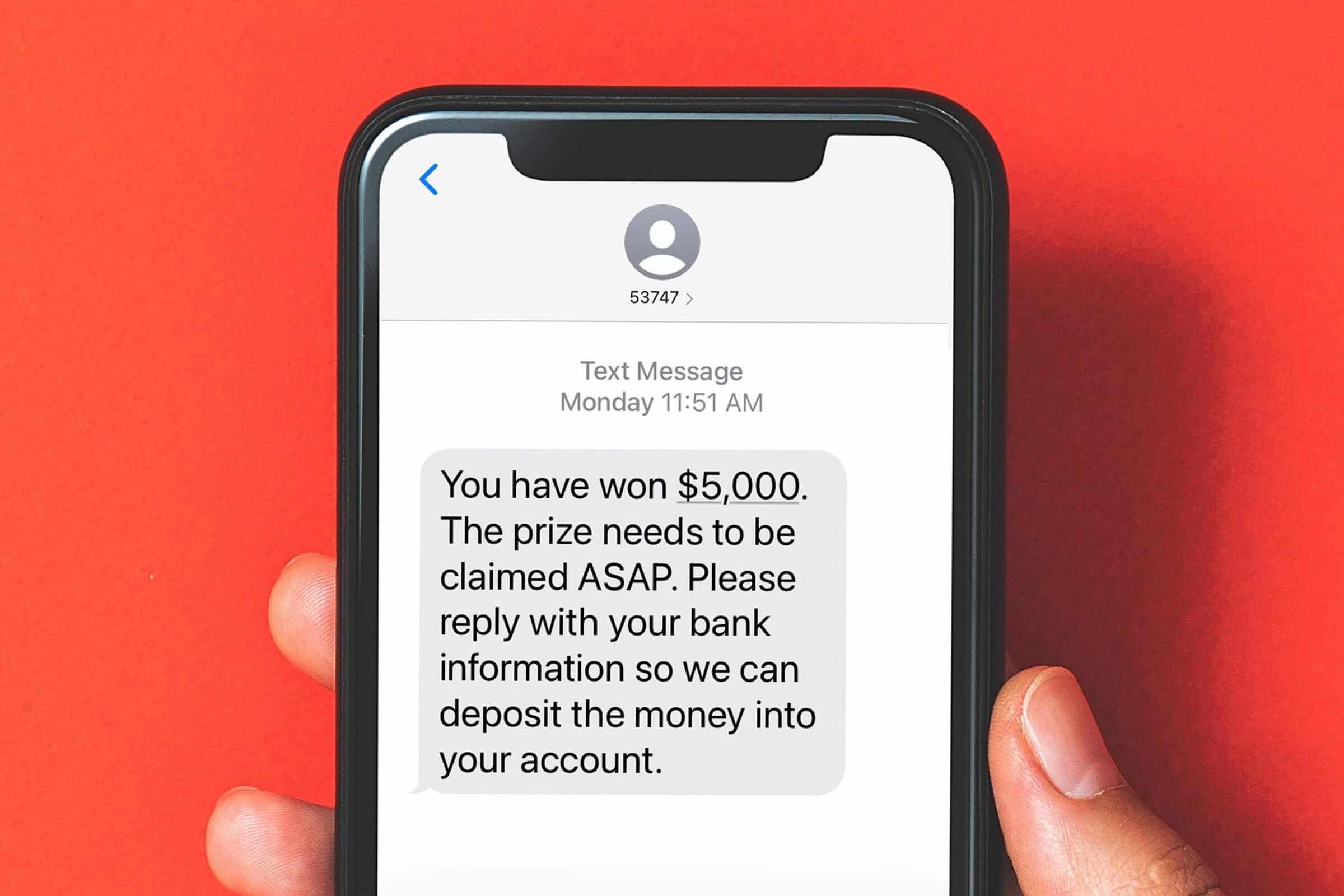
Smishing (a combination of “SMS” and “phishing”) is a type of cyberattack where scammers send fake text messages to trick people into giving up personal information. These messages often pretend to be from legitimate sources like banks, delivery services, or even government agencies.
The goal? To get you to click on a malicious link, call a fake customer service number, or reveal sensitive details such as passwords, credit card numbers, or Social Security numbers.
How Does Smishing Work?
Smishing messages typically create a sense of urgency, making you feel like you must act immediately. Here are a few common examples:
- Bank Alerts: “Urgent: Your account has been compromised. Click here to verify your identity.”
- Delivery Notifications: “Your package is delayed! Click this link to confirm your details.”
- Government Scams: “You are eligible for a tax refund. Claim it now by following this link.”
Once you click on the link, you might be taken to a fake website designed to look like a real one. If you enter your information, it goes straight into the hands of cybercriminals.
How to Protect Yourself from Smishing Attacks
- Don’t Click Links in Unsolicited Messages – If you receive a text from an unknown sender with a link, be cautious. Go directly to the company’s website instead.
- Verify the Sender – If a message appears to be from your bank or another trusted organization, contact them directly using a verified phone number.
- Look for Red Flags – Watch out for poor grammar, strange URLs, and urgent language designed to pressure you into acting quickly.
- Use Security Features – Many mobile carriers offer spam message filtering. Enable these features to reduce unwanted messages.
- Report Suspicious Messages – Most mobile carriers allow you to report spam texts by forwarding them to 7726 (SPAM).
Smishing is on the rise, but you don’t have to fall victim to it. By staying informed and practicing good cybersecurity habits, you can keep your personal information safe. If you’re ever unsure about a message, always take a moment to verify before responding.
For more cybersecurity tips and updates, stay tuned to the ExchangeDefender blog!
Spoofing vs. Phishing: Understanding the Differences

In today’s digital world, online security is more important than ever. Two common threats that can compromise your personal information and security are spoofing and phishing. While these terms may sound similar, they represent distinct types of cyberattacks. In this blog post, we’ll explore the differences between spoofing and phishing, how they work, and how you can protect yourself from falling victim to these scams.

Spoofing: It’s Not Who You Say You Are
Spoofing is like someone pretending to be someone else online. For example, a scammer might send you an email that looks like it’s from your bank, but it’s actually from them. They’re trying to trick you into thinking they’re someone you trust.

Phishing: A Fishing Expedition for Your Information
Phishing is a bit like a fishing expedition, but instead of catching fish, scammers are trying to catch your personal information. They might send you an email or text message that looks like it’s from a legitimate company, asking you to click on a link or download an attachment. If you do, you might end up giving away your personal information, like your passwords or credit card numbers.
The Key Differences
- While both spoofing and phishing involve deception, there are some key differences between them:
- Intent: Spoofing is often used to gain unauthorized access or launch other attacks, while phishing is primarily used to steal personal information.
- Techniques: Spoofing involves technical methods to disguise the sender’s identity, while phishing often relies on social engineering techniques to manipulate victims.
- Impact: Spoofing can have a variety of consequences, while phishing attacks are primarily used to steal personal information.

How to Protect Yourself
- Be skeptical. If you get an unexpected email, text, or phone call, be suspicious. Don’t click on links or open attachments unless you’re sure they’re from who they say they’re from.
- Check for typos and grammar mistakes. Scammers often make mistakes in their emails or texts.
- Never give out personal information. Don’t share your passwords, credit card numbers, or other sensitive information with anyone unless you’re absolutely sure they’re who they say they are.
By being aware of the difference between spoofing and phishing, and by following these tips, you can help protect yourself from becoming a victim of these scams.
Looking for Spoofing AND Phishing protection that’s affordable? Go for ExchangeDefender PRO!
How to Protect Yourself from Domain Spoofing and Phishing with ExchangeDefender

At ExchangeDefender we want you to be safe online. One of the biggest and best steps you can take towards that goal is to both protect your domain from being “spoofed” (forged by a spammer) and to block any such forgeries from arriving into your mailbox.
About Spoofing
Spammers and hackers routinely abuse domains that do not have a SPF or DKIM record. They configure their email software to use your domain name for a SPAM campaign or to launch sophisticated phishing attacks. If you’ve ever received an email from yourself, or from a forged government or corporate entity, you’ve been a victim of spoofing. If you’ve ever received thousands of rejections and delivery receipts for messages you never sent, you’ve been a victim of spoofing. Because so many domain owners do not take responsibility for their DNS configuration, this is the most widely abused mechanism.
Good news is, ExchangeDefender can help protect you from these attacks and brand misuse through implementation of SPF, DKIM, and our corporate policies.
SPF (Sender Policy Framework)
ExchangeDefender uses SPF to verify that the email is coming from a source that your organization trusts to send messages. This is typically your email server, our email server, and sometimes a business application (like a hosted CRM) that sends email using your domain name. All others get rejected as forgeries.
How do you setup your SPF record? Simply go to wherever your domain name is hosted (your name server) and add this TXT field to your zone. You may need assistance from your ISP, domain registrar, or whoever is actually running your name servers. If you don’t know who that is, or they are too difficult to use, ExchangeDefender will host your domain free of charge. The TXT record will not have a hostname and the value should be set to the following:
Hostname:
Record type: TXT
Value: v=spf1 include:proxy.exchangedefender.com -all
DKIM (Domain Keys)
ExchangeDefender uses DKIM to validate automated digital signatures. We also sign messages for all customers that rely on ExchangeDefender to send outbound mail (pretty much everyone). This is a 2 step process similar to SPF.
Step 1: Request public key
Go to https://support.ownwebnow.com and open a ticket requesting signatures of your outbound mail. Please specify which domains you wish to sign because each domain must have its own set of keys.
Step 2: Create a DKIM public record
Go to wherever your DNS is hosted and just like in SPF, create a DKIM record:
Hostname: default._domainkey
Record type: TXT
Value: v=DKIM1; k=rsa; s=email; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC0SXzBGHoJcBVKyNEntvTiMtoSIH4uiuY6i5hzF47
A2eYb4pB/gtsHpP1vpDgzZvwVLz65nQwnm4wvSFsarKwCyWYyvGwPvBd9+v2Jcrk5dsfHioUDZo5oSvbRY
+e8AD7eo42A/pYdgZxL9KRyZbMsCtHJrAqvYB6LZP0SFVvkYQIDAQAB
Important: This is just an example. You will need to use your own public key generated in Step 1 and provided by us. Also, the value of the TXT record has to be on the same line, if there are any line breaks (if you copy it from an email or web page) please remove them.
Step 3: Update the ticket with us to test deployment
After the DNS record has been created for your domain, we will validate it and if configuration is valid we will start signing your outbound messages going through ExchangeDefender.
After the DNS record has been created for your domain, we will validate it and if configuration is valid we will start signing your outbound messages going through ExchangeDefender.
ExchangeDefender Policy
While we encourage all of our clients to implement both SPF and DKIM, we understand that there are sometimes business scenario cases under which this is impossible. If you find yourself in this predicament you should immediately change where your name servers are hosted and take full control of your organizations identity online. But if that is still something you may not be able to do, ExchangeDefender can still protect you from phishing attacks and spoofing launched using your own domain name. If you’ve ever received email from yourself or from a colleague (but the email actually came from a server in Poland) then this setting will help you.
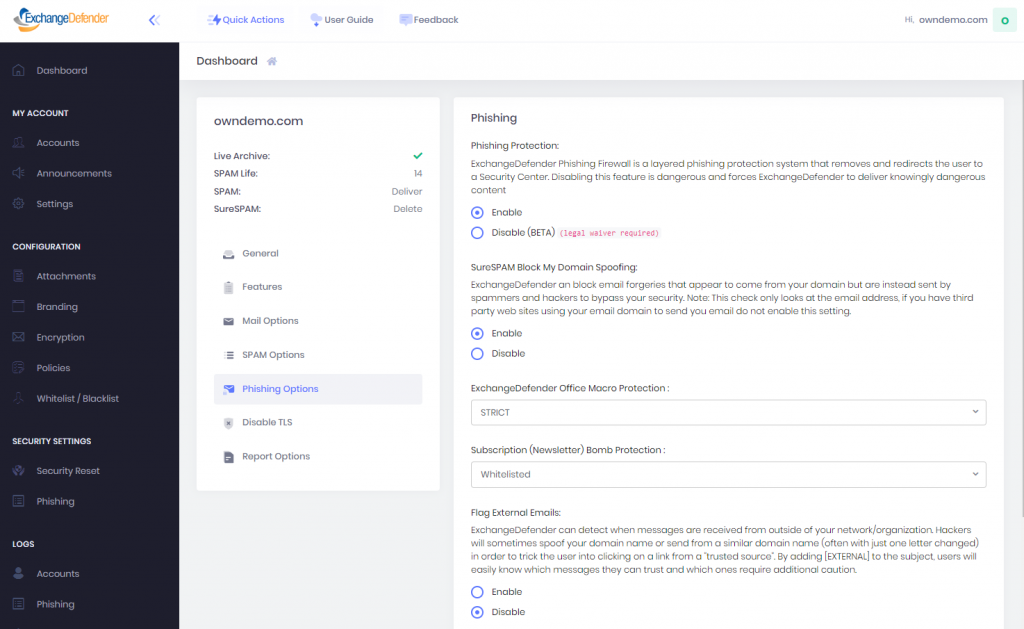
Go to https://admin.exchangedefender.com and login as the domain administrator (username is your domain name).
Click on Security Settings > Phishing
Under “Flag External Emails” click on Enable and then Save.
After this setting is applied, all messages from your domain that were sent from outside of the ExchangeDefender network will go into the SureSPAM quarantine. Just tell users not to trust, whitelist, or release messages that are coming from your own domain because they are certainly not legitimate.Note: This is the option of last resort and will not stop hackers or spammers from abusing your domain for phishing, spamming, or hacking. However, it will stop those messages from arriving directly into your users mailbox. If you already have a valid SPF record (with -all, not ~all) and DKIM in production, this setting is not necessary as ExchangeDefender will automatically reject messages that fail SPF/DKIM validation.
If you have any questions or concerns about ExchangeDefender and implementation of SPF, DKIM, or phishing policies please feel free to contact us.