Domain Admin Dude, where is my SPAM?

In our previous post we discussed how users can get to their own SPAM quarantines but did you know that you as the domain administrator have access to EVERYONE’s junk mail?
ExchangeDefender Admin Portal features a SPAM Admin section where you can release ANY message caught by ExchangeDefender to ANY user in your organization.
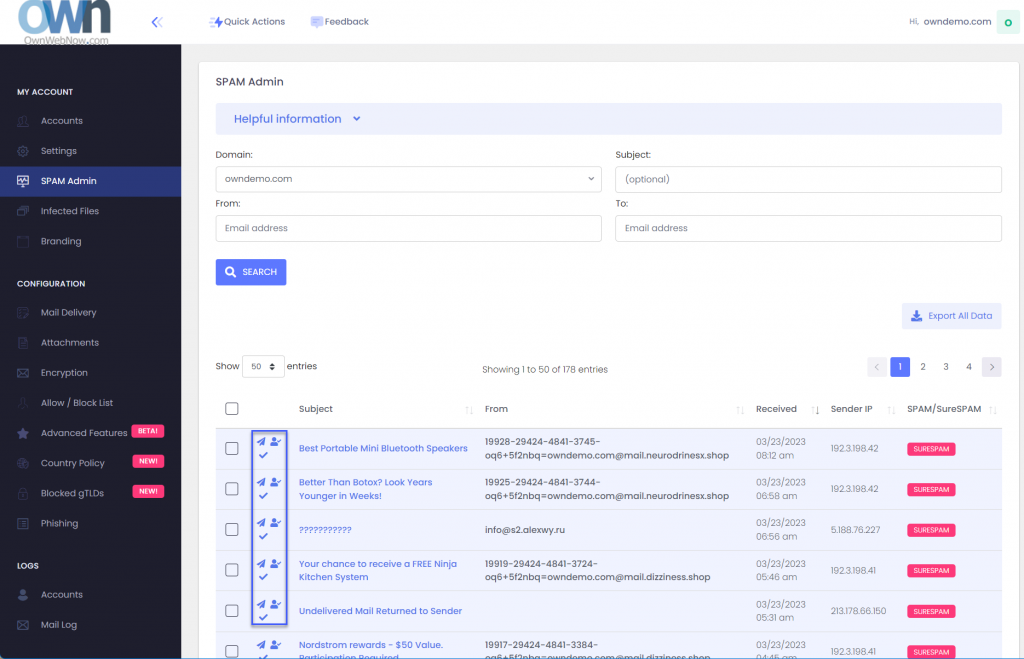
The three icons next to the message are Release Message, Allow Sender, and Mark as reviewed. Releasing a message will get it to the end users mailbox while allow sender will create an Allow policy for that email address so it skips SPAM checks in the future.
Many organizations designate a SPAM Admin that is in charge of fishing out important messages, attachments, and other content that was blocked by an IT or corporate policy. If you have a lot of users that are not tech-savvy this feature will save you a ton of time.
I already have an Allow Policy and my mail from this sender is always ending up in Junk Mail!
ExchangeDefender Advanced Features can help you here as this problem is so common we’ve built an entire feature to help solve it. The issue is, most of the messages coming are from automated systems (password reminders, newsletters, appointment confirmations, etc) that are sent by a computer instead of someone’s Outlook or phone. They all rely on mass/bulk mail systems like Amazon SES, Sendgrid, etc and those networks use a fake email address to send a message every time (so they can track bounces). You can’t create an allow policy (whitelist) for those addresses as they change every time, so take a look at the Bulk Mailer Policy section:
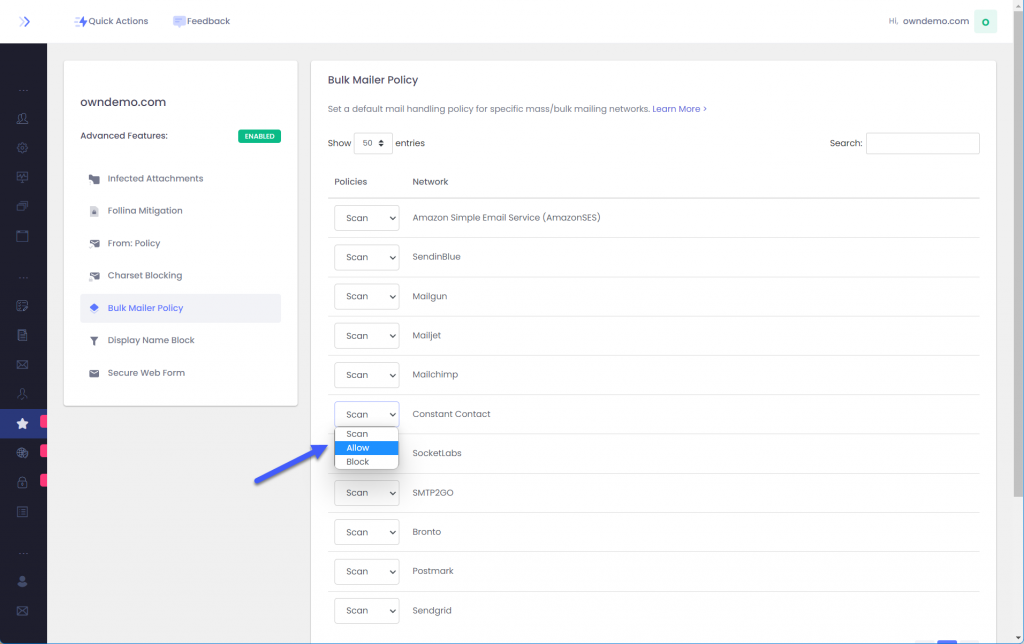
Here you can tweak the policy applied to each bulk mailer network to accommodate your users. By default we scan each message from these networks for SPAM contents but depending on the problem you are trying to solve with SPAM you can change it to Block or Allow messages from that network.
I already did all that, seriously, where is my email?
Most of policy enforcement problems stem from not knowing which message the user is looking. As mentioned earlier, automated systems forge the email address they send mail from so the address you see in Outlook is not the actual email address. It’s tough to make policies or find the message when you don’t know the senders email address: ExchangeDefender Mail Log to the rescue:
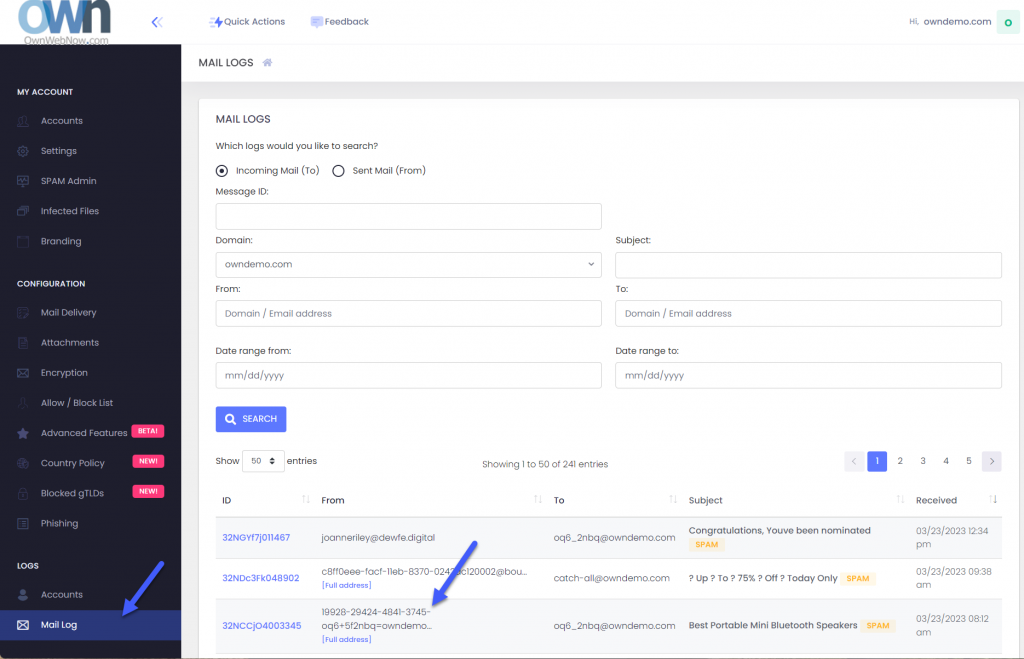
As the Domain Admin you have access to all the email logs for your domains. Click on Mail log and you’ll be able to search for the message based on time, date, subject, etc.
You can also scroll through the mail log. See the [Full address] below some senders? Those are the fake tracking email addresses we’re talking about. Generally you can create a domain-wide allow policy for the entire domain if you trust that the sender isn’t going to send malicious content (we’ll still check if any attachments are infected and apply your file/extension policy).
To sum it up
As an ExchangeDefender Domain admin you have powerful tools to locate SPAM, apply allow or block policies, and to scope them down to the bulk mailer network that is usually the #1 culprit. Go figure, nobody wants these messages and they sometimes get inadvertently reported as junk anyhow.
ExchangeDefender can save hours of going through transaction and message logs by presenting all of your messages in a user-friendly way where you can quickly release them to your user, create an allow policy so it doesn’t get intercepted again, and designate clients trusted partners/networks that should always go straight to their mailbox.
Introducing ExchangeDefender Inbox
Cybersecurity tops the list of IT concerns and spending, with email still being the most popular service with users and hackers alike: over 90% of compromises start with an email. If that sounds familiar you’ve undoubtedly had to deal with new email authorization standards, user training, troubleshooting mail flow, trying to figure out why email to or from certain people is bouncing, reconciling it all with new IT trends, cyber-insurance requirements, marketing. In a nutshell, email security is still a challenge and users just want something that works.
We’ve reimagined what the email security should look like in 2022 and we cannot wait to show it off:
ExchangeDefender Inbox Webinar
Wed, Sep 28, Noon EST
https://attendee.gotowebinar.com/register/1111619875721771023
We hope you can join us for the webinar and see just how we’ve integrated all the ExchangeDefender security and productivity services to give users a single panel of glass to make email work for them even when they have issues with email. Can’t wait till next Wednesday? Shoot us a ticket at support.exchangedefender.com and ask us to enable it for you today!
ExchangeDefender Inbox combines over two decades of email security experience with the modern, mobile-first world of countless email issues. It enables our clients to get things done with email security and work through all the issues without involving IT. Users want a quick and reliable email platform that just works – work around SPAM filters, around SPF/DKIM policies, around bounces – all while leveraging email encryption to protect sensitive data. The service has been enormously popular with our enterprise clients and now we’re bringing it to all ExchangeDefender users – see you next Wednesday!
Cybersecurity and Healthcare: what you need to know
Ransomware attacks on U.S healthcare organizations are predicted to quadruple by 2021, according to recent industry reports. Hackers are increasingly targeting healthcare due to the vast amounts of personal health information, which is considered 50 times more valuable on the black web than their financial information. The need for the ability to secure personal information is urgent, and requires immediate attention of the medical industry.
2022 CYBERSECURITY CHALLENGES
Malware, ransomware, and viruses
M365 application threats
Phishing attacks
Information protection
Misleading websites
Employee error
Account takeovers
Hackers deploy malware and ransomware to shut down and control devices, and even servers. Many healthcare organizations tend store health information without proper encryption leaving them vulnerable to external threats. Phishing attacks have been the newest and most successful method of cyber-attacks in which cyber criminals send mass emails from “reputable” sources to obtain sensitive information. Hackers link these emails to misleading websites to entice the user to enter their personal information, mainly their username and password to gain complete access, and commence in account takeover efforts.
OUR SOLUTIONS FOR HEALTHCARE
Thousands of Healthcare organizations trust ExchangeDefender to protect their data, and to keep their employees, and client information safe and secure. We protect your practice from malware, ransomware, and phishing attacks using Email Security, our advanced multilayered security suite. We secure patients’ information by enabling our Email Encryption which offers military grade security and prevents data leaks. Healthcare practices must be HIPAA compliant, and rely on ExchangeDefender for Email Archiving and Compliance. This service ensures compliance with long-term tamper-proof email archiving and unlimited storage. Our Web File Server protects your organization from cloud application threats, enables your team members to upload, manage, and share documents securely. The service is encrypted, and provides full reporting of all activity for accountability and transparency. Security tip: To increase your organization’s resistance against cyber-threats, start with powerful email security, add web security and data protection, and to ensure that you always have access to email even during service disruptions, our email outage protection.
Are you a medical office looking for IT solutions? We can help, visit www.365defender.com to see our services!
ExchangeDefender Office Macro (OLE) Dangerous Content Filtering
ExchangeDefender Office Macro (OLE) Dangerous Content Filtering
ExchangeDefender now includes advanced protection from dangerous Microsoft Office macro code (OLE). Since usage of Office macro code is very limited (and seldom moved via email) it’s almost universally used as an attack vector by hackers who send malicious macro code embedded in Microsoft Office documents that target vulnerabilities in Outlook, Word, Excel, Powerpoint, and more.
Specifically, our service scans the following attachments for the presence of dangerous, encrypted, malformed, malicious, or suspicious code: doc,dot,pot,ppa,pps,ppt,sldm,xl,xla,xls,xlt,xslb,docm,dotm,ppam,potm,ppst,ppsm,pptm,sldm,xlm,xlam,xlsb,xlsm, and xltm. If we detect something suspicious or dangerous the message will not be destroyed or quarantined (as is the case with virus or infected attachments) – rather we just filter it to SureSPAM.
Managing Your OLE Protection
We will start strictly enforcing macro protection on January 1, 2019. However, the feature is available now and can be enabled at any time by going to https://admin.exchangedefender.com and logging in as a domain administrator (if you don’t see the setting, you aren’t logging in with your domain account but your personal or service provider account).
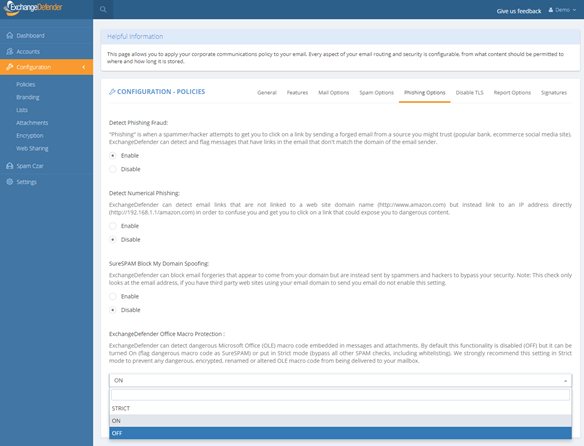
Click on Configuration > Policies > Phishing Options.
At the bottom of the form you will see “ExchangeDefender Office Macro Protection” section that is currently (October 2018) set to Off. The following options are available:
Off – Turns off ExchangeDefender Office Macro (OLE) protection
On – Turns on the protection but whitelisting the domain/email will bypass it
Strict – Turns on the protection and ignores whitelists
ExchangeDefender recommends this setting be configured as Strict in order to protect from spoofing where clients own domain or vendor (that doesn’t have SPF/DKIM implemented) address is used to deliver a dangerous attachment. Using “Strict” setting bypasses whitelist checks so if the message contains dangerous content it will automatically go into SureSPAM even if the domain is whitelisted.
What do I tell the users?
First, set the setting to Strict. Then, adjust the date in the message below and make sure SureSPAM settings are set to Quarantine.
“Starting with January 1, 2019, ExchangeDefender will protect you from dangerous attachments that contain rarely used Microsoft Office macro (OLE) code. If dangerous macro code is detected in an attachment, message will go into SureSPAM category and if configured to quarantine the message will be accessible at https://admin.exchangedefender.com in the SureSPAM quarantine. We have enabled the protection for you. If you ever see a familiar contact/domain but you were not expecting the message, it’s likely being spoofed/forged in order to trick you to click on a dangerous attachment. Take an extra step and contact the sender asking them if they sent you a document. If not, delete the message.”
We hope this helps keep your users more secure and in our production use so far it’s helping stop 100% of dangerous content
So You Think GDPR Doesn’t Apply to You?
That Four Letter Monster: GDPR
We know – you’re tired about hearing about GDPR – and you’ve probably received a billion emails about it from marketers all over the world urging you to “confirm” your subscription. As our CEO recently posted on Facebook:
“There were two kinds of IT people this week on Facebook – those that whined about
GDPR and those that got richer as a result of it.”
You can hear more of Vlad’s unfiltered thoughts on GDPR in the Game Changer webinar held earlier this month, but needless to say the GDPR is something that is here to stay and with every public privacy breach the notion of government regulation worldwide is going to start with GDPR as the foundation.
What this means for you – regardless of whether you’re the CIO or an MSP partner – is that client data privacy, disclosure, search, and reports will start consuming more of your time.
Do you currently have a solution in place that can quickly tell you what sort of data you have on your clients? Beyond your CRM.
What about the invoices that get emailed out with account numbers and addresses?
What about any contracts or agreements that got emailed back and forth?
I think you see where we are going with this: you need to prepare your IT for eDiscovery even if you don’t have urgent, current, and pressing reason to do so. Penalties for exposing financial data are extreme and the more the world gets used to privacy disclosure and where client data may be stored the more requests and inquiries you will start seeing. Businesses (aka “people with money”) are the low hanging fruit that will be sued first.
This is by no means a new trend: We have been selling Compliance Archive and Corporate Encryption for years but GDPR has really put the demand for these products into a new gear. For our partners, this has significantly increased both sales and service requests that are a giant opportunity for many to be ahead of the curve and regulatory changes worldwide.
Get ready for it today and call us – we have the products, the service, documentation, marketing collateral and back office legal support –
all you need to do is present it to the client and can help you do the rest.
Three Simple Ways To Begin Regulatory Compliance Archiving
Have you been putting off offering or relying on Compliance Archiving to meet regulatory compliance requirements? If so, you’re among friends as most businesses tend to view it as a form of a backup until they receive a letter from a law firm. Recently we published a quick and informal techie-free post about business continuity and we wanted to do the same for archiving because the #1 thing that will keep you out of trouble is making sure your entire organization is on the same page.
With that in mind, here are three steps that your organization needs to follow to get started with Compliance Archiving:
Step 1: Understand how your organization communicates
If you only knew what everyone did and what they had access to, things like security and compliance would be a non-issue. In the real world, organizations have a revolving door of staff, vendors, clients, laws, and projects that is constantly spinning. The notion that you can get something to manage it all, held together by IT staff and automation, is nothing short of a fantasy. Or rather, a nightmare, because you’ll get in trouble over one thing that was missed and went wrong not a million things that went right.
Our Compliance Archiving touches every message in your organization: doesn’t matter if it’s a message you sent to a client, a message you received from a vendor, or an interoffice email you sent to a coworker – we get them all. The important thing in step one is identifying the people and making sure that the way you communicate is set in stone: “We communicate with everyone through @ownwebnow.com email addresses, every ticket, every update, every inquiry, every quote, every bill pay – everything either comes from or is cc’d to an @ownwebnow.com address.”
Step 2: Get a grip on your devices, apps, and processes
Convenience is the enemy of order. And if you’re going to run a business, you cannot have everyone do exactly what they want to do. Yes, Subway will make your sandwich any way you want them to, but if you walk in and order a key lime cheesecake you’re going to be hungry. Same method applies to all the devices, apps, processes, etc. The simplest, most common sense, most effortless thing to do is to just give everyone that works on your behalf an email address on your infrastructure and have them use that email for all company communications.
If they use something else, and for some reason you wish to permit that rule change in your business, request that everything is cc’d to a local shared mailbox where you can keep ownership of it. Don’t make a big deal out of it – we get our office beer and red solo cups from Costco – and believe me we don’t have a massive asset inventory tracking system around it with people signing off on stuff left and right. We just take a picture of the receipt/order form and email to a receipts@ address – done.
Step 3: Get a regulatory compliance plan
The worst thing you can possibly do is start thinking about a plan when you’ve received a request for information or a legal hold. The good news is, step #3 is the simplest one because it’s just a matter of calling us at 877-546-0316 and talking to someone about implementing the Compliance Archiving solution. The complexity isn’t in the technology, it’s with the people and the constant sprawl of apps and devices that hold vital corporate information.
The great news about what we offer with our partners is that anything going in and out of your company can be screened, monitored, reported, and produced on demand or automatically for just a few bucks a month. The biggest challenge is knowing what to do – and you have to actually get started.
We look forward to serving you and making regulatory Compliance Archiving a breeze.
Pro Tip: How to Pitch Encryption and Compliance
Here is something that MSPs always get wrong when it comes to proposing Encryption and Archiving (HIPAA, compliance, eDiscovery): You can’t be something you’re not BUT you have to know the service you’re proposing. More on this topic tomorrow (if I can sneak it by the marketing)
Posted by ExchangeDefender on Thursday, April 5, 2018
Here is something that MSPs always get wrong when it comes to proposing Encryption and Archiving (HIPAA, compliance, eDiscovery): You can’t be something you’re not BUT you have to know the service you’re proposing.
Want to see part TWO of this video?
Disclaimer: There is tasteful profanity and light nudity to really drive the point of how to better interact with your clients. 🙂
How to kill SPAM without using ExchangeDefender
At ExchangeDefender we kill SPAM for a living. We spend a ton of time and energy identifying, filtering, and destroying junk mail. If you’ve ever wondered how you could make your email experience better, even without the massive layered security that ExchangeDefender provides, these are the steps you could take today:
1. Configure strict SPF/DKIM DNS records
SPF and DKIM (DMARC) can help you protect your domain name from being used in SPAM mailbombs. Spammers will often use real email addresses and domains to send forged “spoofed” email messages and SPF/DKIM provide a mechanism for identifying which email server/platform you use. By setting up an SPF/DKIM you can tell places that are receiving email from your domain what to do if the message wasn’t actually sent from you. If your inbox is full of email bounces and non-delivery receipts, someone is using your email address to send junk mail and an SPF/DKIM record will practically eliminate bouncebacks.
2. Get rid of generic email aliases
At ExchangeDefender we manually process SPAM complaints from our customers – that’s how we train our system to eliminate messages that otherwise make it through because they are legitimate in every way we can automatically process them. The number one way to get a ton of annoying email that may be on the borderine between legitimate commercial mail and an unsolicited one: generic email aliases. If you get info@, sales@, admin@ or so on, you are painting a giant bullseye on your Inbox and practically begging to be spammed.
3. Unsubscribe from newsletters
I know, I know, everyone that has your email address supports CAN-SPAM , would never send you unsolicited mail, would never sell their client list… and even if you believe all those lies most of the time, people still get hacked. All the time! As do their ISPs and infrastructure along the way. If you want to reduce the amount of junk mail you deal with, simply reduce the number of places that have your email address. Simple!
4. Don’t click on everything in your Inbox
Sometimes SPAM gets through. Sometimes dangerous stuff from your friends and colleagues gets forwarded around. Sometimes your antivirus isn’t up to date. Sometimes the firewall virus protection is misconfigured our expired. Things happen: none are a good excuse for the simplest thing you can do: avoid clicking on anything in messages that look or seem suspicious.
5. Do not blindly whitelist major ISPs
The second biggest source of SPAM complaints at ExchangeDefender is actually completely self-inflicted: people whitelist major email providers and wonder why blatant junk mail keeps on “slipping through” as whitelisted. Go through your whitelist entries in Outlook, etc and make sure you aren’t whitelisting Gmail, Outlook, Yahoo, Verizon, AT&T, Hotmail or any of the widely used and abused email domains. Spammers know your email admin doesn’t want to deal with complaints about messages you’re getting from these platforms so they treat them more leniently – so spammers simply abuse them.
It’s really that simple – following these steps will cut your junk mail pile in half within a day. If you want to reduce it to less than 1%, ExchangeDefender is here for you for less than a buck a month or you can layer it and add more protection if you need it because time is money: but no amount of technology and automation can replace just a little bit of common sense.
Federal Trade Commission
CAN-SPAM Act: A Compliance Guide for Business
The official website of the Federal Trade Commission, protecting America’s consumers for over 100 years.
VIDEO: Live Archive keeps emails up, and running!
So here is something that has always worked for me: everyone hates outages. Regardless of why I’m invited to speak to anyone about ExchangeDefender, and the billion problems we solve, I am here to help you with just one thing: uptime. If things are working, we can sort everything out, but the fear of the new unknown solution causing downtime is the #1 thing your client is thinking about. So address it first.
Posted by ExchangeDefender on Thursday, March 29, 2018
What’s this video about? Live Archive.
So here is something that has always worked for me: everyone hates outages. Regardless of why I’m invited to speak to anyone about ExchangeDefender, and the billion problems we solve, I am here to help you with just one thing: uptime. If things are working, we can sort everything out, but the fear of the new unknown solution causing downtime is the #1 thing your client is thinking about. So address it first.
What is Live Archive?
Access your email via the cloud when outages happen.
Organizations are constantly facing internet and email outages, maintenance cycles and service unavailability. The key to productivity is being able to access your email even when outages happen Exchange Defender LiveArchive Business Continuity is the solution.
As you send and receive email, we make a copy and store it on our network – when you experience an outage you can just pull up a webmail system on your computer, tablet, or phone and continue where you left off.
Visit Exchange Defender: Email Security, Archiving, and Business Continuity solutions
Why is there suddenly a heavy demand for Encryption?
What is behind the growth in the adoption of email encryption?
Over the past year we’ve seen an explosion in sales of ExchangeDefender Email Encryption – which is a surprise given that we’ve not only had it for years but that we’ve also given it away for free. HIPAA has been around for over 20 years, dozens of other regulations that almost all companies ignore have been gone for just as long – so why now?
In one word: penalties.
Companies have long known that they can’t operate efficiently without email – and that they cannot just move files around “just to get it to them” once they see the penalties. But selling a service to someone that has avoided using or paying for it is never an easy discussion so here are the 3 quick questions that should lead you to an effective pitch in under 1 minute:
1. Who sends you encrypted messages?
2. Who could get hurt if this information went public?
3. What is your exposure? How much negligence insurance do you have?
The more they mumble, the more of those questions they cannot answer, the more details or costs or scope they don’t understand, the more they need it. End your question with this line: How comfortable would you be having this conversation in a legal deposition?
Elevator pitch: How to position ExchangeDefender Encryption as an answer to all of the above problems
→It is included in your ExchangeDefender Pro subscription and it’s transparent – no software to install, nothing to manage or configure.
→ You’ll be using the same process and same security major banks, health care providers and lawyers use – so you’ll be protected from most critical security exploits.
→ Finally, it’s dead simple to use – all your employees need to do is put [ENCRYPT] in the subject when they are sending the message. Doesn’t matter if it’s on the phone our Outlook or Outlook Web Access, it just works.
Ding. You’re done. It’s virtually impossible not to sell this service – and it’s desperately needed by anyone using email to do business or conduct confidential discussions. One more thing: Because encryption is transparent and on demand in the cloud, it also protects you when the security issue is on the recipients end – because email is never stored on their PC or device, if someone hacks their network they won’t be able to get to the info stored in your encrypted message!
If email is a business necessity then email encryption is it’s insurance policy.
If you discuss business over email, then anything confidential that should be in that email should be a matter of employee communication protocol: If you attach something sensitive to this message, you better encrypt it and CYA. This is the way things go at banks, with lawyers, with accountants, with realtors and at nearly every white collar job: Nobody wants to assume the liability so they’ll all do what it takes to protect the data.
And with high profile hacks and compromises in the news daily, is not having it worth risking the whole company?