Don’t Take the Bait: Xfinity Phishing Emails on the Rise
Phishing emails targeting Xfinity (Comcast) customers are flooding inboxes again—and this wave is particularly deceptive. Disguised as legitimate communications from Xfinity, these emails are designed to create panic and trick users into compromising their security.
What’s Happening
Cybercriminals are sending emails that appear to be from Xfinity, warning users about urgent account issues. Common themes include service interruptions, billing errors, or suspicious activity. The emails often ask recipients to “secure their account” or update personal information, directing them to fake login pages that harvest credentials.
Many of these messages are styled with official-looking Xfinity branding, and even the sender email address can appear authentic at a glance. Some victims have reported receiving fake invoices or confirmations for charges they never made—creating just enough concern to drive a click.
📌 Source:
Why It’s a Problem
Once you click on these links or share information, the consequences can be serious. Scammers may gain access to your Xfinity account, personal data, or even your entire device. This type of phishing can lead to identity theft, financial loss, or malware infections—especially if users unknowingly download files or enable remote access.
Even savvy users can fall for these tricks, which is why prevention and education are key.
📌 Sources:
How ExchangeDefender Helps
ExchangeDefender’s advanced threat protection is already working behind the scenes to block phishing emails like these. By scanning for malicious links, suspicious attachments, and known spam patterns, our system keeps these messages out of your inbox.
If you’re using our LiveArchive solution, your email continues to run smoothly—even if an attack disrupts your main provider.
Want to level up even further? Our Spearphish training platform delivers realistic phishing simulations to help your team recognize red flags before they click.
What You Should Do
If you receive a suspicious message claiming to be from Xfinity:
- Do not click any links or download attachments
- Go directly to your account via xfinity.com
- Report it to Comcast at abuse@comcast.net
📌 Also check out:
Make sure your team knows the signs of phishing and doesn’t trust emails that feel rushed, pushy, or “off.” And if you manage email for clients, now’s a great time to reinforce best practices.
Watch Out: New Norton LifeLock Phishing Scam Targets Inboxes Nationwide

Email scams are getting bolder, and the latest one impersonating Norton LifeLock is making waves across inboxes everywhere. If you or your clients have received a suspicious email about a Norton subscription renewal or refund, here’s what you need to know—and why it matters.
🚨 What the Scam Looks Like
This phishing campaign is cleverly designed to mimic official Norton communications. The email usually warns of a pending charge or a renewal for Norton LifeLock services you never signed up for. Some versions say the charge is already complete, encouraging panic.
It may include:
- Official-looking logos and invoice PDFs
- Toll-free numbers to “cancel” the subscription
- Links that direct you to phishing pages
🤔 Why It Works
Scammers know how to create urgency. These emails often claim you’re being billed hundreds of dollars, prompting victims to call the provided number or click a cancellation link. Once on the phone, scammers may:
- Request remote access to your computer
- Ask for banking credentials to “process a refund”
- Install malware or steal sensitive data
🛡️ How to Protect Your Organization
ExchangeDefender recommends taking the following actions to stay safe:
- Never call phone numbers listed in suspicious emails
- Avoid clicking links or downloading attachments
- Report emails that look off – even if they seem to come from a known brand
- Enable 2FA wherever possible
If you’re using ExchangeDefender’s advanced phishing protection, our system is already working behind the scenes to stop these attacks before they hit your inbox.
MSPs, Take Note
This scam isn’t just a one-off – it’s part of a growing trend targeting businesses through brand impersonation. If you’re an MSP, we recommend sharing this post with clients and ensuring email continuity is part of your disaster recovery planning.
With ExchangeDefender’s LiveArchive, even if a phishing email triggers an outage or breach, business communication can continue seamlessly.
🔎 Learn More
Stay informed, stay secure. Read Norton’s official scam alert page here or contact ExchangeDefender support if you need help tightening your phishing defenses.
Have questions or want to beef up your email security stack? Try ExchangeDefender PRO! Contact us today.
Stay safe out there!
ExchangeDefender — Email Security, Backup & Continuity Built for Business.
The Anatomy of a Phishing Email (With Examples)

Phishing emails have come a long way from the hilariously obvious scams of the early 2000s. Today, they’re more convincing, better designed, and — worst of all — more effective. Knowing how to spot a phishing email can mean the difference between avoiding a breach… or becoming the next cautionary tale.
Let’s break down the anatomy of a phishing email — using real examples and highlighting the red flags you should never ignore.
What is Phishing?
Phishing is a type of social engineering attack where cybercriminals pose as trusted entities to trick people into giving up sensitive information — like passwords, credit card numbers, or access credentials. These emails may look like they’re from your boss, your bank, or even your favorite app.
Key Elements to Watch For
Let’s dissect a classic phishing email and highlight where the danger hides:
1. Weird or Slightly Off Email Address
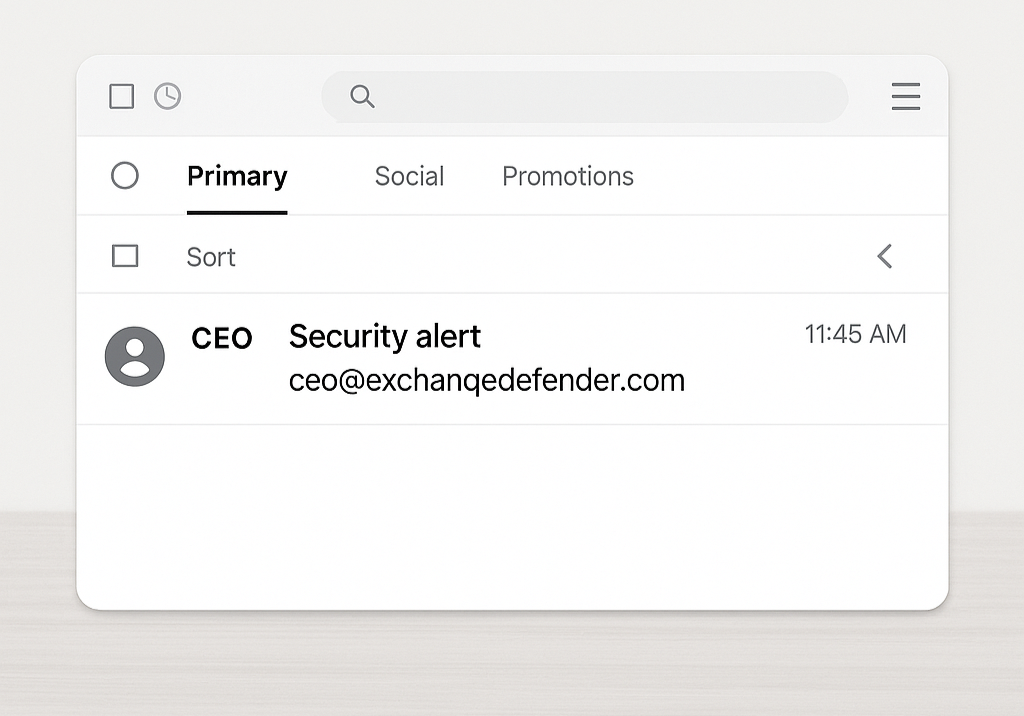
Example: ceo@exchanqedefender.com instead of ceo@exchangedefender.com
A single letter can be all it takes to trick someone. Always double-check the sender’s email. If it looks “off,” it probably is.
👉 Pro Tip: Hover over the sender’s email or tap to reveal full details.
2. Urgent or Threatening Language
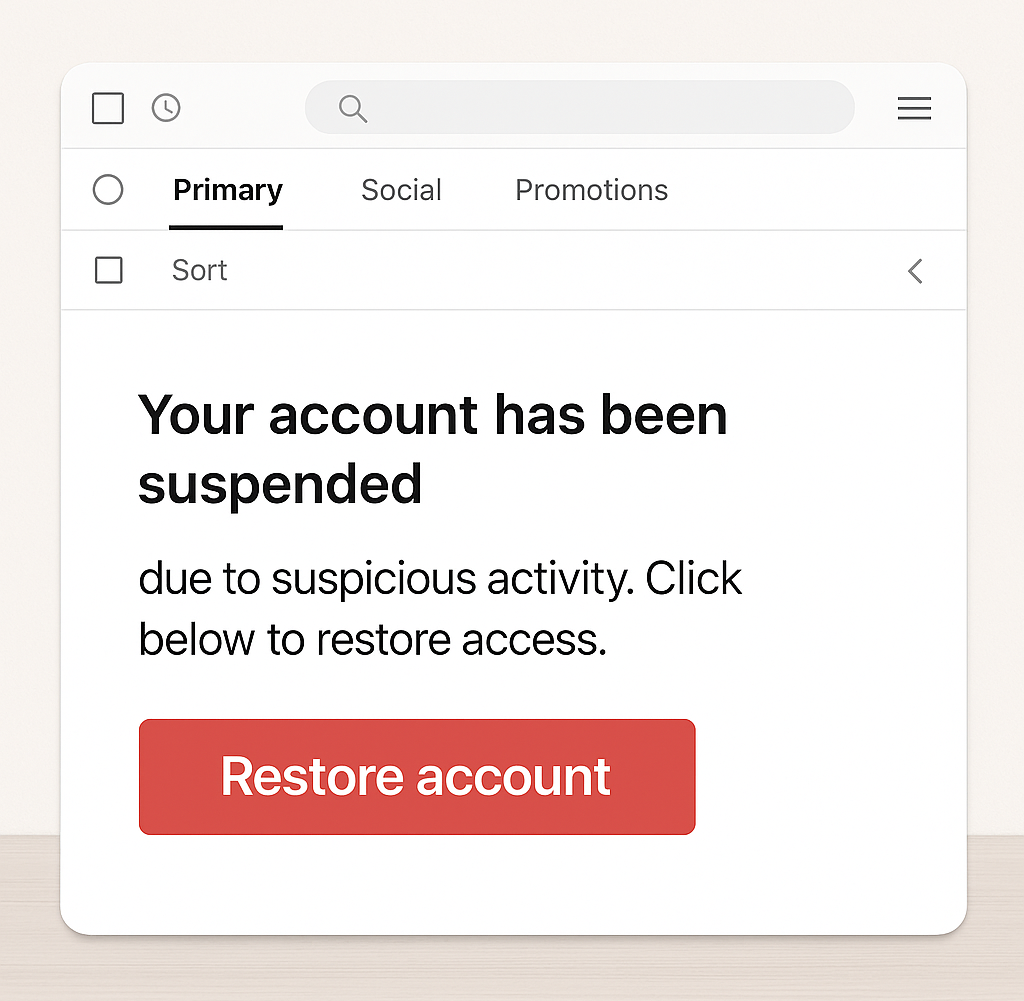
Example: “Your account has been suspended due to suspicious activity. Click below to restore access.”
Scammers want you to act fast without thinking. Anything that demands “immediate action” is likely designed to panic you into clicking.
3. Generic Greetings
Example: “Dear user” or “Hi customer”
If it’s a real company emailing you, they probably know your name. Phishing emails often use vague intros to cast a wide net.
4. Suspicious Links or Attachments
Example: A button that says “Restore Account” but links to a random URL like http://secure-login-info.com
Always hover before you click. If the URL doesn’t match the legitimate site, run far away (and don’t open attachments either).
5. Spelling + Grammar Errors
Even today, many phishing emails are riddled with typos and weird formatting.
Example: “You acount has been suspened. Click hear to restore”
You’d be surprised how many people overlook this — don’t be one of them.
✅ How to Protect Yourself
- Slow down. Urgency is a tactic.
- Verify. If in doubt, call or message the sender directly (don’t reply).
- Train your team. Run phishing simulations regularly.
- Use protection. Email filtering tools like ExchangeDefender can stop threats before they hit your inbox.
Phishing emails rely on one thing: human error. But with awareness, training, and the right tools, you can turn your team into a human firewall. Learn what to look for — and don’t let the phish hook you.
Want to test your team’s phishing detection skills?
👉 Try our free phishing simulation today
Stay safe. Stay alert. Stay unphished.
How the eBay Phishing Scam Works

The eBay phishing scam is a common cyberattack where scammers impersonate eBay to steal user credentials, financial details, or personal information. These scams often take the form of fake emails, text messages, or websites designed to trick users into providing sensitive information.
In eBay phishing scams, attackers send counterfeit emails or messages that appear to originate from eBay. These communications often contain urgent prompts, such as warnings about account issues or unauthorized transactions, compelling recipients to click on malicious links. These links lead to fake websites resembling eBay’s login page, where users are tricked into entering their credentials. Once obtained, cybercriminals can exploit this information for fraudulent activities, including unauthorized purchases or identity theft.

Red Flags to Watch Out For:
🚨 Generic Greetings – Legitimate eBay emails usually address you by name. Look for fake logos!
🚨 Suspicious Links – Hover over links before clicking—real eBay links should start with “ebay.com.”
🚨 Poor Grammar & Spelling – Many phishing emails have obvious errors. Look for fake phone numbers!
🚨 Requests for Personal Info – eBay never asks for passwords, payment info, or security details via email.
How to Protect Yourself:
✅ Enable Two-Factor Authentication (2FA) for extra security.
✅ Go Directly to eBay – Instead of clicking links, log in at eBay.com.
✅ Report Suspicious Emails to eBay at spoof@ebay.com.
✅ Use Strong, Unique Passwords – Avoid reusing your eBay password on other sites.
Mitigating Phishing Risks with ExchangeDefender PRO
To safeguard against such evolving threats, businesses require robust cybersecurity solutions. ExchangeDefender PRO offers comprehensive email security designed to protect organizations from advanced email-borne attacks. Key features include:
Anti-Phishing Protection: Identifies and blocks phishing attempts, preventing unauthorized access to sensitive information.
Anti-Spam and Malware Defense: Filters out spam and detects malicious attachments, reducing the risk of malware infections.
Ransomware Protection: Guards against ransomware attacks that can encrypt critical business data.
Domain Fraud Prevention: Prevents spoofing and unauthorized use of your domain, protecting your brand’s integrity.
On-Demand Encryption: Ensures sensitive communications are securely encrypted, maintaining confidentiality.
Adding ExchangeDefender PRO to your cybersecurity setup can help protect your organization from phishing scams and other email threats. It’s a smart way to stay safe online and keep your business and relationships secure.
How to Spot and Avoid Geek Squad Email Scams
In recent years, scammers have increasingly impersonated Geek Squad, Best Buy’s tech support service, to deceive individuals into divulging personal information or making unnecessary payments. Understanding how these scams operate and how to recognize them is crucial for safeguarding your personal data and finances.
Understanding the Geek Squad Email Scam
The Geek Squad email scam is a phishing attempt where fraudsters pose as Geek Squad representatives to steal personal information or trick victims into paying for fake services. These emails often appear legitimate, making it challenging to distinguish them from authentic communications.
Common Types of Geek Squad Email Scams
- Auto-Renewal Scam: Scammers send emails stating that your Geek Squad subscription is about to auto-renew at a substantial cost. The email urges you to call a provided number or click a link to cancel the subscription, aiming to extract personal and financial details.
- Fake Antivirus Software Offer: You might receive emails warning of malware infections among Geek Squad customers, offering free antivirus software downloads. However, these downloads are malicious and designed to infect your device, steal data, or gain remote access.
- Password Reset Scam: Emails claim suspicious activity on your Best Buy account, prompting you to reset your password via a provided link. The link leads to a fake website designed to capture your login credentials, allowing scammers unauthorized access to your account.
Recognizing Scam Emails
Be vigilant for the following signs:
- Sense of Urgency: Scammers often pressure you to act quickly, creating a false sense of urgency.
- Suspicious Sender Addresses: Examine the sender’s email address for inconsistencies or misspellings. Official communications will come from a legitimate Best Buy domain.
- Generic Greetings: Emails that don’t address you by name, such as “Dear Customer,” may be fraudulent.
- Poor Grammar and Spelling: Legitimate companies maintain professional communication standards.
- Unsolicited Attachments or Links: Avoid clicking on links or downloading attachments from unknown senders.
Protective Measures
- Verify Communications: If you receive a suspicious email, contact Geek Squad or Best Buy directly using official contact information from their website.
- Avoid Unsolicited Links and Downloads: Refrain from clicking on links or downloading attachments from unknown sources.
- Use Security Software: Ensure your devices are equipped with reputable antivirus and anti-malware programs.
- Stay Informed: Educate yourself about common phishing tactics to recognize and avoid potential scams.
Reporting Scams: If you encounter a Geek Squad scam, report it to Best Buy. Additionally, file a complaint with the Federal Trade Commission (FTC) through their Complaint Assistant.
How to Spot & Avoid the Latest DocuSign Scam

Cybercriminals are getting craftier, and one of their favorite new tricks is impersonating trusted services like DocuSign. If you’ve recently received an email urging you to sign a document or verify your account, think twice before clicking! The latest wave of DocuSign email scams is designed to steal your personal information and compromise your security.
How the DocuSign Email Scam Works
Scammers send fake emails that appear to be from DocuSign, using official-looking branding and urgent messaging. Here’s how the scam typically unfolds:
- Fake Email Notification – You receive an email that looks like it’s from DocuSign, requesting you to review or sign a document.
- Urgency & Pressure – The email often claims the document requires your immediate attention, creating a sense of urgency.
- Malicious Links – Clicking the link redirects you to a fraudulent website that mimics DocuSign’s login page.
- Credential Theft – If you enter your login details, scammers steal them to access your DocuSign or other linked accounts.
- Malware Installation – Some scams include attachments or links that, when clicked, install malware on your device.
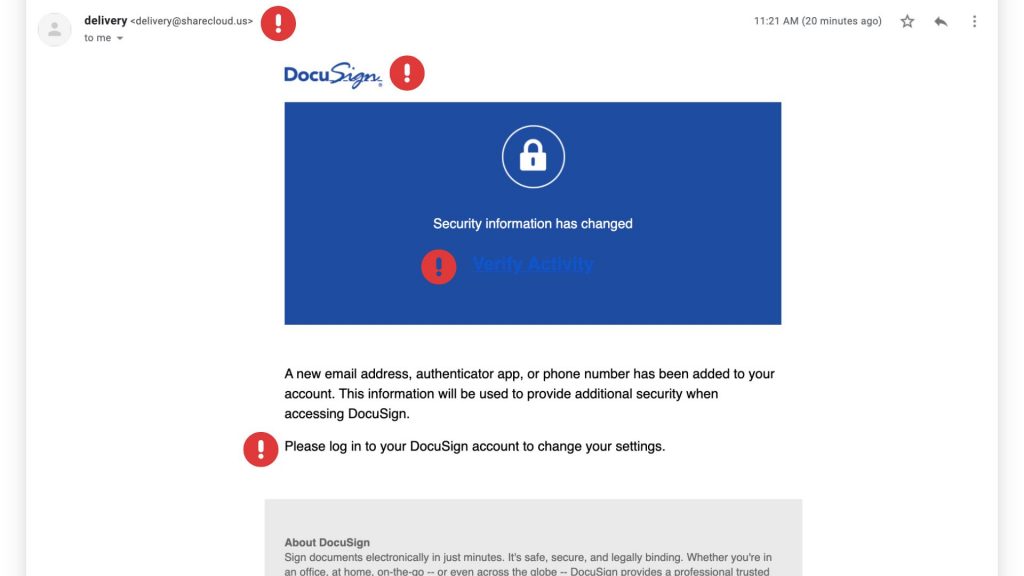
Red Flags to Watch For
These scams can be convincing, but there are a few telltale signs that can help you identify them:
✔ Suspicious Sender Address – Official DocuSign emails come from @docusign.com or @docusign.net, not random or misspelled domains.
✔ Unusual Language or Errors – Many phishing emails contain typos, grammatical mistakes, or odd phrasing. Look for fake logos as well!
✔ Unexpected Requests – If you weren’t expecting a document, verify with the sender before opening anything.
✔ Fake Links – Hover over any links in the email (without clicking) to see the actual URL. If it’s not docusign.com, don’t trust it.
✔ Generic Greetings – Scammers often use “Dear Customer” instead of your actual name.
How to Stay Safe
Protect yourself and your business from falling victim to these scams by following these best practices:
🔹 Verify Directly – Instead of clicking email links, go to www.docusign.com and log in to check if a document is waiting.
🔹 Enable Multi-Factor Authentication (MFA) – Adding an extra layer of security can prevent unauthorized access to your account.
🔹 Report Suspicious Emails – If you receive a fraudulent DocuSign email, forward it to spam@docusign.com and then delete it.
🔹 Keep Security Software Updated – Use up-to-date antivirus and security software to detect and block phishing attempts.
🔹 Educate Your Team – Ensure employees know how to recognize and avoid phishing emails.
Watch Out! The USPS Text Scam is Back (and Sneakier Than Ever)

We all rely on the USPS to deliver our mail and packages, but scammers are exploiting that trust with a devious new trick: the USPS text scam, also known as “smishing.” This isn’t just another annoying robocall; it’s a carefully crafted attempt to steal your personal information and leave you vulnerable to identity theft.

How the Scam Works:
Imagine this: You receive a text message that appears to be from the United States Postal Service. It might say something like:
- “Your package delivery has been delayed due to an unpaid shipping fee. Click here to resolve.”
- “We were unable to deliver your package. Please call this number to reschedule.”
- “Your package is being held at our facility. Verify your address to avoid return to sender.”
These messages often use urgent language to create a sense of panic. They want you to act quickly without thinking. The key element is a link or a phone number. Clicking the link takes you to a fake website that looks convincingly like the real USPS site, where you’re asked to enter sensitive information. Calling the number connects you to a scammer posing as a USPS representative.

The Danger Lurking Behind the Link:
The goal of these scams is simple: to trick you into handing over your personal and financial data. This could include:
- Account usernames and passwords
- Social Security numbers
- Dates of birth
- Credit and debit card numbers
With this information, scammers can wreak havoc on your finances and your identity.
How to Protect Yourself:
The good news is, you can easily protect yourself by remembering these crucial points:
- USPS Doesn’t Initiate Contact via Text or Email (Unless You Specifically Request It): The USPS will not send you unsolicited text messages or emails. The only exception is if you’ve signed up for tracking updates using a specific tracking number.
- USPS Messages Never Contain Links: Legitimate USPS communications will never include clickable links. This is a huge red flag.
- Be Wary of Urgent Language: Scammers use urgency to pressure you. Take a moment to think before you act.
What to Do If You Receive a Suspicious Text:
- DO NOT click on any links.
- DO NOT call any numbers provided in the text.
- Delete the message immediately.
- Report the scam: You can report the message to the USPS Inspection Service (www.uspis.gov) or the Federal Trade Commission (FTC) at ReportFraud.ftc.gov.
Stay Vigilant, Stay Safe:
By staying informed and following these simple tips, you can protect yourself from the latest USPS text scam and avoid becoming a victim of identity theft. Don’t let scammers ruin your day – be smart and stay safe!
Why Phishing Simulations Are Essential for Your Organization

Phishing attacks remain one of the most prevalent and effective cyber threats facing businesses today. These deceptive tactics target the human element, tricking employees into divulging sensitive information or installing malware. That’s why phishing simulations are no longer a “nice-to-have” but a critical component of any robust cybersecurity strategy. At ExchangeDefender, we understand the importance of proactive security measures, and we’re here to explain why phishing simulations are essential for protecting your organization.
1. Turning Employees into a Human Firewall
Your employees are your first line of defense against cyber threats. Phishing simulations empower them to recognize and avoid phishing attacks in the real world. Here’s how:
- Real-World Scenarios: We craft simulations that mimic real-world phishing attempts, using realistic emails, text messages, and even voice calls. This exposes your team to the latest tactics used by cybercriminals, preparing them for what they might encounter.
- Learning by Doing: Experiencing a simulated attack provides invaluable hands-on experience. Employees learn to identify red flags like suspicious sender addresses, urgent requests, unusual links, and grammatical errors.
- Driving Behavioral Change: This practical training is far more effective than simply reading about phishing in a manual. It helps employees develop the instincts to spot and avoid real threats, fostering a culture of security awareness.
2. Identifying Vulnerabilities Before Attackers Do
Phishing simulations not only train your employees but also provide valuable insights into your organization’s security posture:
- Measuring Employee Susceptibility: Simulations reveal how many employees are likely to fall for a phishing attack, highlighting areas where additional training is needed. This data-driven approach allows you to focus your resources effectively.
- Pinpointing Weaknesses: By analyzing simulation results, we can identify specific types of phishing attacks that are most effective against your workforce. This enables us to tailor training programs to address your organization’s unique vulnerabilities.
- Improving Training Programs: The data gathered from simulations allows for continuous improvement of your security awareness training, making it more relevant and effective over time.

3. Reducing the Risk of Successful Attacks (and the Costs They Incur)
The ultimate goal of phishing simulations is to reduce the risk of successful phishing attacks and the devastating consequences they can bring:
- Proactive Security: Phishing simulations take a proactive approach to security, addressing the human element before it becomes a vulnerability.
- Mitigating Incident Response Costs: By preventing successful phishing attacks, you can avoid the significant financial and reputational damage associated with data breaches, ransomware infections, and other security incidents.
- Building a Stronger Security Culture: Regular simulations foster a security-conscious culture where employees are actively engaged in protecting sensitive information, making security a shared responsibility.
ExchangeDefender: Your Partner in Cybersecurity
In today’s complex threat landscape, phishing simulations are an indispensable tool for protecting your organization. At ExchangeDefender, we offer comprehensive cybersecurity solutions, including phishing simulation services, to help you strengthen your defenses and empower your employees. Contact us today to learn more about how we can help you build a more secure future.
Whaling: A Sophisticated Cyber Threat Targeting High-Profile Individuals

Whaling, a type of phishing attack, targets high-profile individuals within an organization, such as CEOs, CFOs, and other executives. These individuals are often referred to as “whales” due to their high-value status and the potential for significant financial gain or data breaches if compromised.
How does whaling differ from traditional phishing attacks?
While traditional phishing attacks cast a wide net, sending out generic emails to a large number of recipients, whaling attacks are highly targeted and meticulously crafted. Cybercriminals conduct extensive research on their victims, gathering information about their personal and professional lives to create highly convincing and personalized messages.
Key Characteristics of Whaling Attacks:
- Highly Personalized: Whaling emails are tailored to the specific recipient, often referencing their role, recent projects, or personal information.
- Urgent Tone: Whaling attacks often create a sense of urgency, urging the victim to take immediate action, such as transferring funds or sharing sensitive information.
- Spoofed Identities: Cybercriminals may spoof the email addresses of trusted individuals or organizations to increase credibility.
- Sophisticated Social Engineering Techniques: Whaling attacks employ sophisticated social engineering tactics to manipulate victims into compromising their security.
Example of a Whaling Attack
A cybercriminal might impersonate a company’s CEO and send an urgent email to the CFO, requesting an immediate wire transfer. The email could be crafted to appear legitimate, using the CEO’s email address and signature. If the CFO falls for the deception, they could unknowingly transfer a large sum of money to the attacker’s account.
Protecting Yourself and Your Organization
To protect against whaling attacks, organizations should implement robust security measures, including employee awareness training, strong password policies, multi-factor authentication, and email filtering solutions. Additionally, executives should be particularly cautious when receiving unexpected requests, especially those that involve financial transactions or sensitive information.
Protect your Microsoft 365 environment with ExchangeDefender security solutions. Try ExchangeDefender PRO for free today!
Phishing 101: The Most Common Scams

Have you ever been hooked by a phishing email? It’s like those annoying telemarketers calling your landline, but way more dangerous. Instead of trying to sell you a vacation package, scammers are trying to steal your identity, your money, or both.
Let’s reel in some of the most common phishing scams
- Spear Phishing: Scammers use personal information to make their emails seem legit. They might know your name, job, or even your favorite vacation spot.
- Whaling: This is the big game of phishing. Think of it as hunting down CEOs and other high-profile targets. Scammers use sophisticated techniques to trick these folks into giving up sensitive information
- Smishing: This is like getting a text message from a friend asking for a favor. But instead of needing a ride, they want your bank account details.
- Vishing: This is the phone call version of phishing. Scammers will call you pretending to be from a bank or government agency, trying to trick you into giving up your personal information.
- Clone Phishing: This is like a scammer impersonating your friend or coworker. They’ll send you an email that looks almost identical to one you’ve received before, hoping you’ll fall for the trick.

But don’t worry, you’re not a helpless target. Here are some tips to avoid falling victim to phishing scams:
- Be cautious of unfamiliar emails. If you receive an email from someone you don’t know or a suspicious subject line, be extra careful.
- Verify the sender’s address. Look for typos or suspicious email addresses.
- Avoid clicking on suspicious links. If you’re unsure about a link, hover over it to see the actual URL
. - Never share personal information. Scammers will try to trick you into divulging your passwords, credit card numbers, or other sensitive data.
- Keep your software updated. Ensure your operating system and antivirus software are always up-to-date.
Remember, staying safe online requires vigilance, knowledge, and a bit of caution. So the next time you receive a suspicious email, don’t let scammers trick you!







