How the eBay Phishing Scam Works

The eBay phishing scam is a common cyberattack where scammers impersonate eBay to steal user credentials, financial details, or personal information. These scams often take the form of fake emails, text messages, or websites designed to trick users into providing sensitive information.
In eBay phishing scams, attackers send counterfeit emails or messages that appear to originate from eBay. These communications often contain urgent prompts, such as warnings about account issues or unauthorized transactions, compelling recipients to click on malicious links. These links lead to fake websites resembling eBay’s login page, where users are tricked into entering their credentials. Once obtained, cybercriminals can exploit this information for fraudulent activities, including unauthorized purchases or identity theft.

Red Flags to Watch Out For:
🚨 Generic Greetings – Legitimate eBay emails usually address you by name. Look for fake logos!
🚨 Suspicious Links – Hover over links before clicking—real eBay links should start with “ebay.com.”
🚨 Poor Grammar & Spelling – Many phishing emails have obvious errors. Look for fake phone numbers!
🚨 Requests for Personal Info – eBay never asks for passwords, payment info, or security details via email.
How to Protect Yourself:
✅ Enable Two-Factor Authentication (2FA) for extra security.
✅ Go Directly to eBay – Instead of clicking links, log in at eBay.com.
✅ Report Suspicious Emails to eBay at spoof@ebay.com.
✅ Use Strong, Unique Passwords – Avoid reusing your eBay password on other sites.
Mitigating Phishing Risks with ExchangeDefender PRO
To safeguard against such evolving threats, businesses require robust cybersecurity solutions. ExchangeDefender PRO offers comprehensive email security designed to protect organizations from advanced email-borne attacks. Key features include:
Anti-Phishing Protection: Identifies and blocks phishing attempts, preventing unauthorized access to sensitive information.
Anti-Spam and Malware Defense: Filters out spam and detects malicious attachments, reducing the risk of malware infections.
Ransomware Protection: Guards against ransomware attacks that can encrypt critical business data.
Domain Fraud Prevention: Prevents spoofing and unauthorized use of your domain, protecting your brand’s integrity.
On-Demand Encryption: Ensures sensitive communications are securely encrypted, maintaining confidentiality.
Adding ExchangeDefender PRO to your cybersecurity setup can help protect your organization from phishing scams and other email threats. It’s a smart way to stay safe online and keep your business and relationships secure.
How to Spot & Avoid the Latest DocuSign Scam

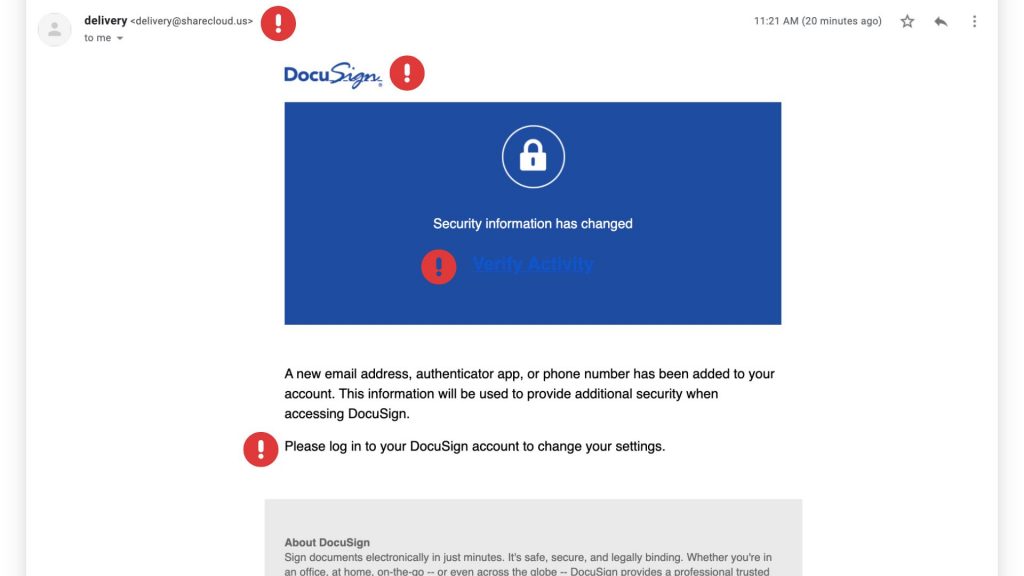
Cybercriminals are getting craftier, and one of their favorite new tricks is impersonating trusted services like DocuSign. If you’ve recently received an email urging you to sign a document or verify your account, think twice before clicking! The latest wave of DocuSign email scams is designed to steal your personal information and compromise your security.
How the DocuSign Email Scam Works
Scammers send fake emails that appear to be from DocuSign, using official-looking branding and urgent messaging. Here’s how the scam typically unfolds:
- Fake Email Notification – You receive an email that looks like it’s from DocuSign, requesting you to review or sign a document.
- Urgency & Pressure – The email often claims the document requires your immediate attention, creating a sense of urgency.
- Malicious Links – Clicking the link redirects you to a fraudulent website that mimics DocuSign’s login page.
- Credential Theft – If you enter your login details, scammers steal them to access your DocuSign or other linked accounts.
- Malware Installation – Some scams include attachments or links that, when clicked, install malware on your device.
Red Flags to Watch For
These scams can be convincing, but there are a few telltale signs that can help you identify them:
✔ Suspicious Sender Address – Official DocuSign emails come from @docusign.com or @docusign.net, not random or misspelled domains.
✔ Unusual Language or Errors – Many phishing emails contain typos, grammatical mistakes, or odd phrasing. Look for fake logos as well!
✔ Unexpected Requests – If you weren’t expecting a document, verify with the sender before opening anything.
✔ Fake Links – Hover over any links in the email (without clicking) to see the actual URL. If it’s not docusign.com, don’t trust it.
✔ Generic Greetings – Scammers often use “Dear Customer” instead of your actual name.
How to Stay Safe
Protect yourself and your business from falling victim to these scams by following these best practices:
🔹 Verify Directly – Instead of clicking email links, go to www.docusign.com and log in to check if a document is waiting.
🔹 Enable Multi-Factor Authentication (MFA) – Adding an extra layer of security can prevent unauthorized access to your account.
🔹 Report Suspicious Emails – If you receive a fraudulent DocuSign email, forward it to spam@docusign.com and then delete it.
🔹 Keep Security Software Updated – Use up-to-date antivirus and security software to detect and block phishing attempts.
🔹 Educate Your Team – Ensure employees know how to recognize and avoid phishing emails.
Is That PayPal Email Real? How to Spot a Phishing Scam

PayPal is a convenient way to send and receive money online, but it’s also a popular target for scammers. PayPal phishing scams aim to trick you into handing over your login details or other sensitive information, potentially leading to financial loss and identity theft. At ExchangeDefender, we’re committed to helping you stay safe online, so let’s break down how these scams work and, more importantly, how to avoid them.
How PayPal Phishing Works
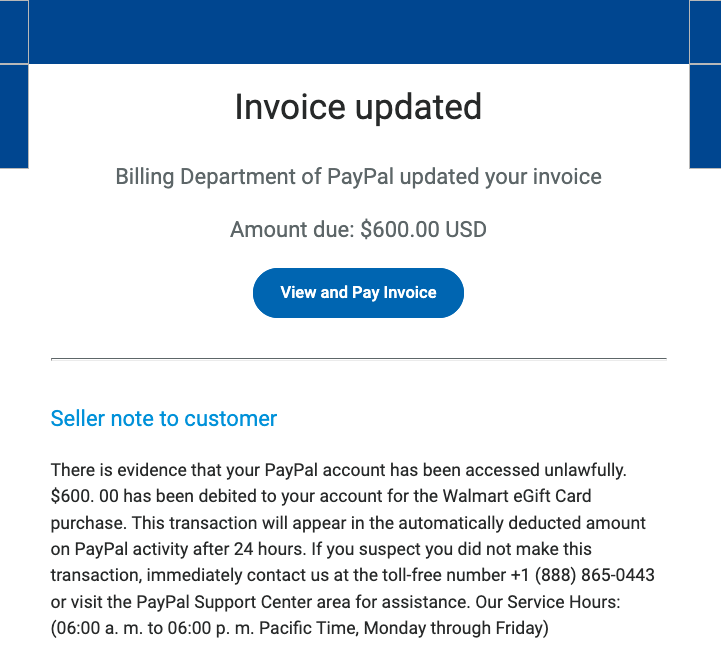
Imagine receiving an email that looks exactly like it’s from PayPal. It uses the familiar logo, branding, and even sounds official. The message might say there’s been unauthorized activity on your account, that your account has been limited, or that you need to update your information. It creates a sense of urgency, urging you to act quickly.
This is the core of a phishing scam. The email contains a link that leads to a fake website designed to mimic the real PayPal login page. If you enter your username and password on this fake site, the scammers instantly capture your information and can use it to access your real PayPal account.

Common Red Flags to Watch Out For:
- Unexpected Emails or Messages: Be suspicious of any unsolicited communication claiming to be from PayPal. Legitimate companies rarely ask for sensitive information via email or text.
- Urgent or Threatening Language: Scammers often use language that creates a sense of panic, such as “Your account will be suspended” or “Immediate action required.”
- Suspicious Links: Hover your mouse over any link without clicking to see the actual URL. Look for misspellings, unusual characters, or domains that don’t match PayPal’s official website (www.paypal.com).
- Generic Greetings: Phishing emails often use generic greetings like “Dear Customer” instead of your name.
- Requests for Personal Information: PayPal will never ask for your password, bank account details, or credit card numbers directly in an email.
Protecting Yourself: Practical Tips
Here are some simple but effective steps you can take to protect yourself from PayPal phishing scams:
- Never Click Links in Suspicious Emails: Always go directly to the PayPal website by typing www.paypal.com into your browser’s address bar. This ensures you’re on the legitimate site.
- Check the Sender’s Email Address: Carefully examine the sender’s email address. Look for any misspellings or unusual characters. Legitimate PayPal emails usually come from addresses ending in @paypal.com.
- Enable Two-Factor Authentication (2FA): 2FA adds an extra layer of security to your account by requiring a second form of verification, such as a code sent to your phone.
- Be Wary of Attachments: Avoid opening attachments from suspicious emails, as they may contain malware.
- Report Suspicious Activity: If you receive a suspicious email or message, forward it to phishing@paypal.com.
ExchangeDefender: Your Partner in Cybersecurity
At ExchangeDefender, we’re dedicated to providing comprehensive cybersecurity solutions to protect you from online threats. While we can’t prevent every phishing email from reaching your inbox, we can empower you with the knowledge and tools to identify and avoid them. By staying vigilant and following these tips, you can significantly reduce your risk of falling victim to a PayPal phishing scam.
The Latest Cyber Threats You Need to Know About (2025 Edition)

The cyber threat landscape is constantly evolving, with new and sophisticated attacks emerging every day. In 2025, we’re seeing a convergence of several concerning trends:
1. AI-Powered Attacks:
- Sophisticated Phishing: AI is now generating incredibly convincing phishing emails, making them harder to detect.
- Automated Exploits: AI can quickly identify and exploit vulnerabilities in systems, launching attacks at unprecedented speeds.
- Deepfakes: AI-generated deepfakes are becoming increasingly realistic, making it difficult to distinguish between real and fabricated content, leading to social engineering and disinformation campaigns.
2. The Rise of IoT Attacks:
- With the proliferation of Internet of Things (IoT) devices in homes and businesses, attack surfaces are expanding dramatically.
- Hackers can exploit vulnerabilities in connected devices to gain access to sensitive information or even control critical infrastructure.
3. Cloud Security Challenges:
- As more businesses migrate to the cloud, the security of cloud environments becomes increasingly critical.
- Cloud misconfigurations, vulnerabilities in cloud services, and insider threats pose significant challenges.
4. Ransomware 2.0:
- Ransomware attacks are becoming more sophisticated and targeted, with attackers demanding higher ransoms and threatening to release sensitive data publicly.
To stay safe online, practice strong password hygiene, be wary of suspicious emails and links, keep your devices and software updated, and be mindful of what you share online. The cyber threat landscape is constantly evolving, but by staying informed and taking proactive steps to protect yourself, you can minimize your risk of falling victim to cyberattacks.
Most Googled Cybersecurity Definitions in 2024

Cybersecurity is more important than ever. To protect ourselves online, it’s important to understand key cybersecurity terms. This guide will break down these concepts in simple terms, making them easy to grasp.
Encryption
The process of converting information or data into a code, preventing unauthorized access. It’s like locking a message in a safe, only accessible with the right key.
Firewall
A security system that monitors network traffic and blocks unauthorized access. It’s like a security guard, protecting your digital fortress.
Spyware
Malicious software that secretly tracks your online activity, stealing personal information and compromising your privacy.
Malware
Harmful software designed to damage or disrupt computer systems. It’s like a digital virus that can infect your device.
Smishing
A type of phishing attack that uses text messages to trick people into revealing sensitive information. It’s a sneaky tactic to steal your personal data.
SpearPhishing
A targeted phishing attack that uses personalized messages to deceive specific individuals or organizations. It’s a more sophisticated form of phishing that often mimics legitimate emails.
By understanding these core cybersecurity terms, you can take control of your online security. Remember, a little knowledge can go a long way in protecting yourself from cyber threats. Stay informed, stay safe, and enjoy the digital world with confidence.
Whaling: A Sophisticated Cyber Threat Targeting High-Profile Individuals

Whaling, a type of phishing attack, targets high-profile individuals within an organization, such as CEOs, CFOs, and other executives. These individuals are often referred to as “whales” due to their high-value status and the potential for significant financial gain or data breaches if compromised.
How does whaling differ from traditional phishing attacks?
While traditional phishing attacks cast a wide net, sending out generic emails to a large number of recipients, whaling attacks are highly targeted and meticulously crafted. Cybercriminals conduct extensive research on their victims, gathering information about their personal and professional lives to create highly convincing and personalized messages.
Key Characteristics of Whaling Attacks:
- Highly Personalized: Whaling emails are tailored to the specific recipient, often referencing their role, recent projects, or personal information.
- Urgent Tone: Whaling attacks often create a sense of urgency, urging the victim to take immediate action, such as transferring funds or sharing sensitive information.
- Spoofed Identities: Cybercriminals may spoof the email addresses of trusted individuals or organizations to increase credibility.
- Sophisticated Social Engineering Techniques: Whaling attacks employ sophisticated social engineering tactics to manipulate victims into compromising their security.
Example of a Whaling Attack
A cybercriminal might impersonate a company’s CEO and send an urgent email to the CFO, requesting an immediate wire transfer. The email could be crafted to appear legitimate, using the CEO’s email address and signature. If the CFO falls for the deception, they could unknowingly transfer a large sum of money to the attacker’s account.
Protecting Yourself and Your Organization
To protect against whaling attacks, organizations should implement robust security measures, including employee awareness training, strong password policies, multi-factor authentication, and email filtering solutions. Additionally, executives should be particularly cautious when receiving unexpected requests, especially those that involve financial transactions or sensitive information.
Protect your Microsoft 365 environment with ExchangeDefender security solutions. Try ExchangeDefender PRO for free today!
Hack the Future: RSVP for the ExchangeDefender Hack-a-ton

We will, we will hack you!
Please join us for a special ExchangeDefender virtual event.
Friday, September 13th, 2024 – 1 PM EST
https://attendee.gotowebinar.com/register/3500231937112410199
You will be among the first to hear about our new line of business that we are currently building in public. See how you can get involved and profit from the platform we’re putting in our partner’s back pocket.
Remember that more than 90% of corporate security exploits start with a phishing email. We’ve done everything possible to keep those messages out of your Inbox and now have something new to announce.
See you next Friday 🙂
Insider Threats: A Growing Cybersecurity Challenge

Insider threats pose a significant risk to organizations of all sizes. These threats come from individuals within an organization who have authorized access to systems and data. They can range from unintentional mistakes to deliberate acts of sabotage.

Types of Insider Threats
- Malicious Acts: Deliberately stealing data, sabotaging systems, or causing damage.
- Negligence: Accidentally compromising security due to carelessness or lack of awareness.
- Espionage: Sharing sensitive information with unauthorized parties.
- Fraud: Using their position to gain financial advantage.

Why Insider Threats Are Dangerous
- Access to Sensitive Data: Insiders have legitimate access to critical systems and data, making them a significant threat.
- Difficult to Detect: Insider threats can often go undetected for extended periods, as they may mimic normal user behavior.
- Damage Potential: Insider threats can cause significant damage, including financial loss, reputational harm, and operational disruption.

How to Mitigate Insider Threats
- Strong Access Controls: Implement robust access controls to limit user privileges and prevent unauthorized access.
- Regular Security Awareness Training: Educate employees about the risks of insider threats and provide them with the tools to identify and report suspicious activity.
- Behavioral Analytics: Monitor user behavior for anomalies that may indicate malicious activity.
- Data Loss Prevention (DLP): Implement DLP solutions to prevent unauthorized data exfiltration.
- Incident Response Plan: Develop a comprehensive incident response plan to address security breaches effectively.
By understanding the risks posed by insider threats and implementing appropriate measures, organizations can significantly reduce their vulnerability to these attacks.
ExchangeDefender Supernet

Last month we announced a major upgrade and expansion of our network to better serve our clients in a more challenging cybersecurity world. I’m sure you’ve seen many stories in the news about cyber attacks and how some groups and nations are expected to attack our critical infrastructure.
We can assure you that those threats are real and are ongoing in a very focused fashion. In order to prepare for a more massive attack, we’ve had to rely on some BGP routing magic to make ExchangeDefender far more resilient.
Make sure you allow inbound SMTP traffic from ExchangeDefender’s 65.99.255.0/24 (255.255.255.0) range.
This range has been in use by ExchangeDefender since 2003 so if you’ve followed our deployment guide correctly you should be all set. If you’ve chosen to deploy ExchangeDefender differently and have other scanning/security active on that range, you might see email delivery delays and failures. Easy fix, just add the whole class C.
What is happening under the hood is that all of our different data centers are routing traffic via the same 65.99.255.x range. Even if half of our data centers disappear due to a telecom or power event, we will be able to continue email delivery.
As you’ve seen over the past year, we’ve focused on Inbox, LiveArchive, and upcoming Replay features to improve security and reliability. Like you, we wake up every day to another Exchange/Gmail event/issue/policy/fubar and nobody likes losing email or the ability to communicate. This is why having ExchangeDefender around your email infrastructure is critical if email is critical to your organization. The new supernet has been routing messages for over a month with no issue and on Wednesday, May 15th we will make it available for everyone.
Enhanced Security: ExchangeDefender Now Supports Custom Authenticator Apps for MFA!

ExchangeDefender has recently enhanced our MFA features (multi-factor authentication) to help you enforce domain-level MFA compliance and to make it easier for users to be enrolled and protected by a layered authentication process automatically.
Simply put, we’re making it easier for you to keep everyone protected.
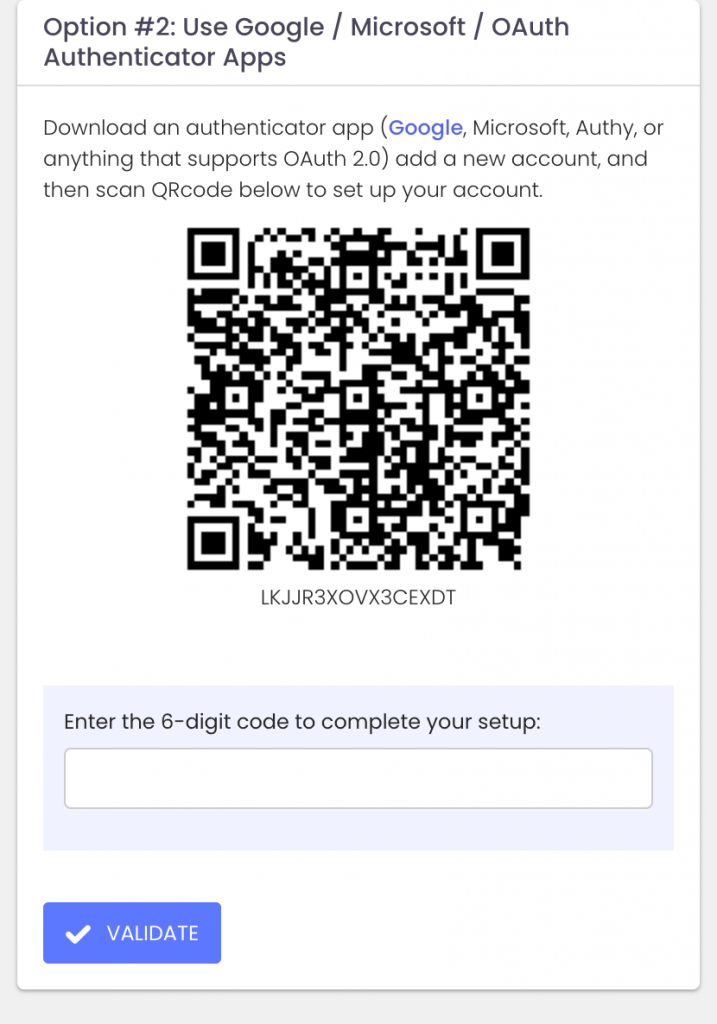
Today we are announcing ExchangeDefender MFA support for custom authenticator apps. By now everyone is familiar with our typical MFA functionality, available under your Settings at https://admin.exchangedefender.com. Just scan the QR code on your device and you’re set!
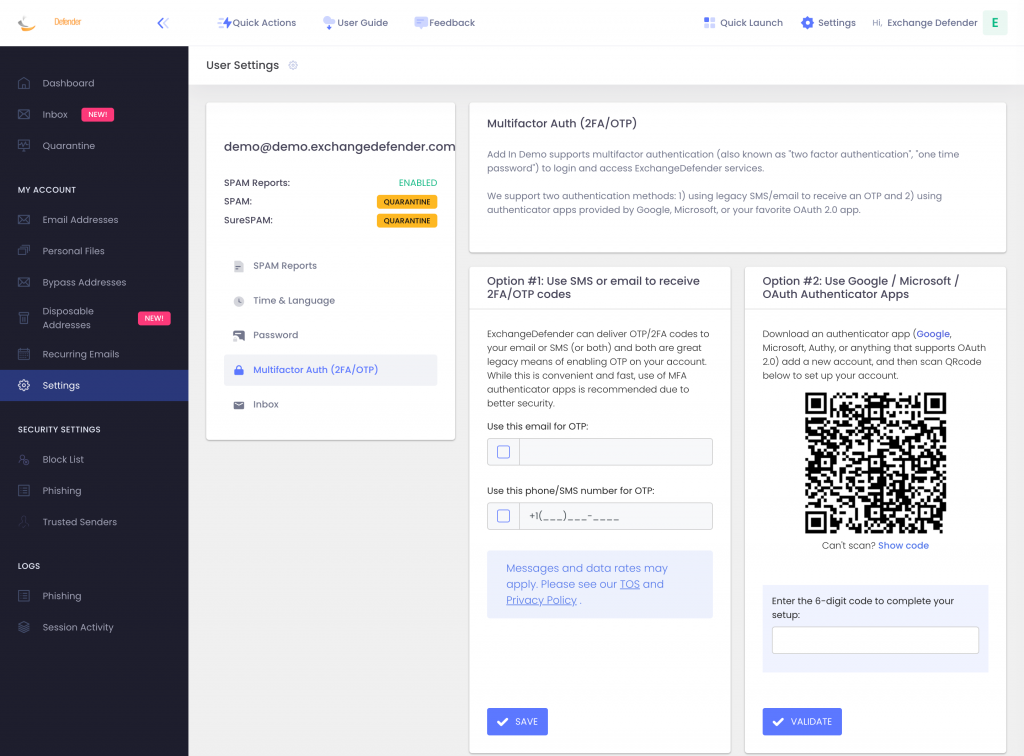
BUT WHAT IF YOUR DEVICE DOESN’T HAVE A CAMERA?
ExchangeDefender now supports MFA app enrollment using a QR code. This is great for scenarios in which:
– You don’t have a camera on your device
– The QR code doesn’t seem to scan (problems with the camera or monitor)
– You want to use a text-based MFA app
– You want to integrate PowerShell/no-code with MFA
– You want to share your MFA codes with others
If you’re in one of those scenarios, note the text under the QR code when you start the enrollment:
Click on the Can’t scan? Show code link and you’ll get the TOTP secret (aka secret code, MFA code). Paste it in your solution and paste back the 6 digit code it generates. That’s it, you’re done. MFA is now enforced and ExchangeDefender will rely on the codes generated by your app to validate MFA and grant access to your account.
All our features come from user feedback so if there is something we need to be doing to keep you more secure please let us know!