Getting Ready for LiveArchive UI – What You Need to Know!

ExchangeDefender will be launching the LiveArchive Web UI during our webinar next week and we are looking forward to showing you how to launch it with a single command! In the meantime, this blog post is intended to give you a heads-up about the requirements and functionality so you can make design decisions.
Docker & Design
In a recent post, we discussed why MariaDB/RDS is required for the LiveArchive Web UI: it’s where we store the message metadata such as sender/recipient/subject/etc. These elements drive the UI and enable users to locate messages, search, and complete eDiscovery and email recovery tasks.
ExchangeDefender has organized the entire LiveArchive Web UI into a single container that can run on your own docker on a workstation or NAS in your office, across a wide variety of virtualization products and services, as well as public cloud like Amazon Web Services and Microsoft Azure. This makes ExchangeDefender Web UI easy to update, easy to manage, and easy to tweak to your requirements.
There are two ways to configure and start the container: preconfigured with environment variables or on-demand browser configuration. If you start the container without the environment defined you will be presented with a web configuration wizard that will prompt for S3 and RDS credentials. If this is the first time you’re deploying LiveArchive Web UI or just want to test it, this is the best way. Once you close your browser all the configuration vanishes and nobody else has access to your mail.
After you’ve configured everything to your liking and are looking to put the service into production, place the appropriate information in the container environment variables, and the container will always launch in production mode and bypass the wizard configuration.
Authentication
ExchangeDefender Web UI was designed to facilitate your email backup and eDiscovery needs. Our experience in compliance archiving and long-term email archiving has allowed us to work with countless organizations and one thing they all have in common is that they all have their own unique access and control needs.
ExchangeDefender Web UI by default presents all the available mailboxes and each email address has its own path. Using this predictable data storage process your Web Application Firewall can easily be configured to include or exclude data by path alone.
We designed the solution so it can be launched quickly, accessed, and managed without a lot of technical skill, and so it can be quickly modified/optimized for production. LiveArchive offers a lot of solutions to modern email problems and the flexibility means you can run different LiveArchive Web UI for different personnel or different tasks.
Resources & Customization
ExchangeDefender Web UI is completely free and open source. This means you can download it, modify it, and use it freely.
It also means that the solution will live even after ExchangeDefender as an organization is gone. You will not find any references or callbacks to our network and all the protocols are fully documented. This enables you to truly craft a failover email solution that can be completely disconnected from the Internet and placed into cold storage / safe.
Resource-wise the container is a little more than a web server and you can run hundreds of users with even the minimal 1 cpu / 1gb ram. This is possible because the SQL workload and data storage are handled by other services.
We hope you’re as excited about the launch as we are. Please join us for the webinar to see how it’s done and we’ll even help you set yours up right after the event! Just think of a good subdomain to point to your new LiveArchive backup platform.
‘LiveArchive Web UI’ Launch Webinar – Join Now!

The new ExchangeDefender LiveArchive has been delighting our clients for months and we’ve got a surprise for you coming in February with a huge new feature pack we can’t wait to show you:

ExchangeDefender LiveArchive Web UI is the free, open-source, host-anywhere platform that will make it easy to access and perform eDiscovery tasks with your LiveArchive backups. Instead of just staring at a directory in S3, you can have a beautiful interface to quickly locate, view, and export messages. You can host it anywhere that offers container hosting or on your PC, you have the entire source code that’s free forever that you can customize and build on, and it’s free!
We’ve even rolled out similar user interface elements so that the experience will feel familiar to users of Microsoft M365 or Google Gmail:
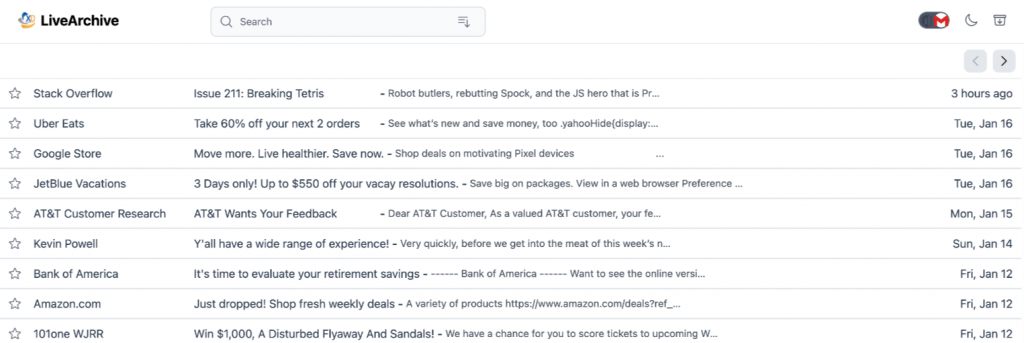
During the launch webinar, we will go over the features, execute a full deployment so you can see how easy and quick the process is, and go over the security best practices. In less than an hour, you will have all the expertise needed to position, price, deploy, and manage the entire LiveArchive backup system.
Unlocking the Power of LiveArchive: Exploring the Need for RDS/DB Integration

We’ve had a busy December rolling out LiveArchive with our partners and one of the most common questions that comes up is:
“Do I really need RDS/MariaDB/database service for LiveArchive? Can’t I get away with just S3 if we’re only using it for backup?”
The technical answers to this are “no” and “yes”, respectively. Unfortunately, in the real world both those answers are wrong. Allow us to explain:
ExchangeDefender LiveArchive relies on S3 object storage to store emails which is why it’s required for the service. ExchangeDefender does not require the RDS/MariaDB/database service for deployment – we will still perform the same backup of messages to object storage and place all emails into the appropriate user@domain.com folder. You can still download .eml files and open them with no issues in Outlook and other popular email clients.
Problem:
Unless you know the exact message I’d of the email you’re looking for you’ll have to download the entire user@domain.com directory and use a text search to locate it.
Solution:
Add RDS to LiveArchive so your archive looks more like this:
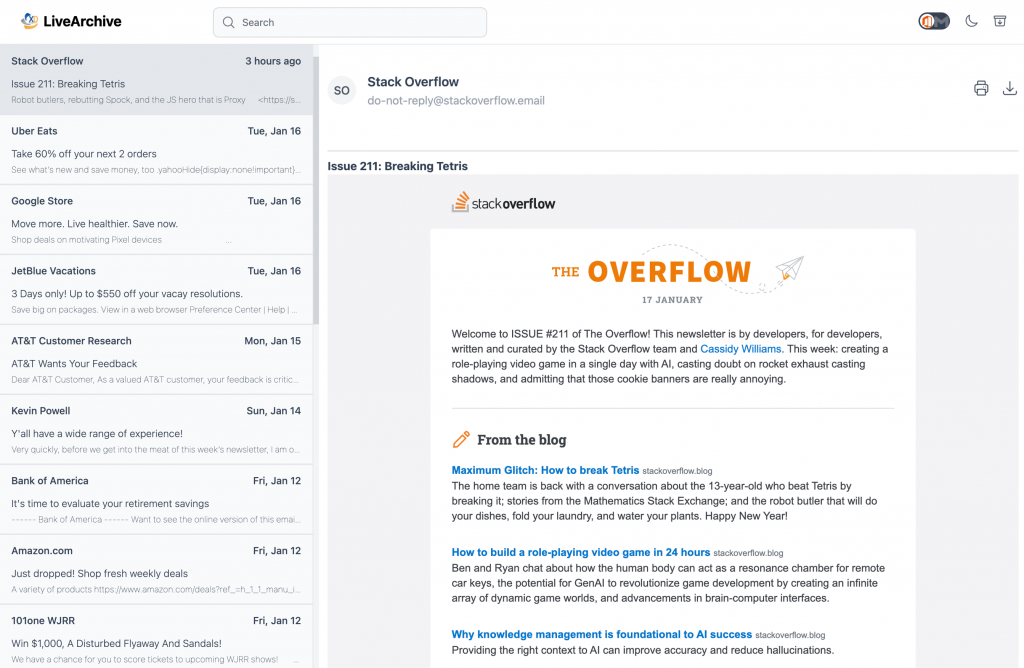
ExchangeDefender LiveArchive uses database services (choice of RDS, MariaDB, MySQL) to store message metadata which contains important message information such as message sender, recipient, subject, and attachments. That metadata is what our ExchangeDefender Web UI relies on to give you a friendly interface to access, search, export, and locate messages quickly in a friendly web interface. ExchangeDefender LiveArchive UI also enables you to filter your message view so you can do eDiscovery: enabling you to limit your search by sender, subject, and date.
We understand why some IT staff would want to do the bare minimum – the market, “nobody is buying stuff”, the complexity, nobody is ever going to look at it – and we hope that the explanation of how database services are used gives you the initiative to deploy RDS. It’s practically free (or totally free if you run it on your hardware) and it will greatly improve your performance, reduce time to recovery, and make it possible to quickly delegate eDiscovery or move data in a format that is open, documented, and will likely be around for decades. Not even tape can claim that! 
ExchangeDefender’s Top Solutions of 2023: Safeguarding Your Email Ecosystem

In the dynamic landscape of digital communication, having a robust and reliable email management system is crucial for businesses and individuals alike. ExchangeDefender, a leader in email security solutions, offers a suite of cutting-edge products designed to ensure seamless communication, data protection, and business continuity. Let’s delve into some of ExchangeDefender’s most popular solutions in 2023.
#1 – ExchangeDefender Inbox: Your Email’s Safety Net
ExchangeDefender Inbox is a modern and secure email platform that serves as a backup plan for your primary email systems, such as Outlook and Gmail. When faced with email outages, technical difficulties, or delivery issues, Inbox ensures uninterrupted communication by actively creating copies of your emails.
Inbox operates independently of your email hosting. If your primary email service experiences downtime, you can seamlessly switch to ExchangeDefender Inbox to send and receive emails in real-time. This innovative feature provides a safety net, ensuring you stay connected even during service outages.
#2 – ExchangeDefender Bypass: Overcoming Email Roadblocks
ExchangeDefender Bypass is a game-changer in overcoming email roadblocks. It offers a disposable email address service that delivers emails despite outages, blacklists, throttling, or other IT problems. With the ability to set up and delete addresses at any time, Bypass provides a free, simple, private, and secure solution for uninterrupted email flow.
Key Features:
- Masking your entire address and domain for enhanced privacy.
- Emails sent to Bypass addresses bypass typical security restrictions.
- Subject modification for easy identification of external messages.
#3 — ExchangeDefender Encryption: Simple and Secure Data Protection
Easy-to-Use Encryption
ExchangeDefender Encryption provides a simple yet powerful solution for encrypting emails and sharing documents securely. With auto-detection of sensitive data and real-time reporting, this on-demand encryption software is both user-friendly and affordable for small businesses.
Key Benefits:
- Regulatory compliance and enhanced business practices.
- Secure messaging via email, URL, or SMS.
- Detailed reporting on when an email is read.
#4 — ExchangeDefender PRO: Total Email Security for Business
Email Protection at Its Best
ExchangeDefender PRO is an advanced email security suite designed to safeguard your business against a wide range of threats, including SPAM, malware, phishing, spoofing, ransomware, and spyware. With 24/7 protection and new quarantine reports, ExchangeDefender PRO offers deeper insights into email management and security, empowering informed decision-making.
New Feature: Simplified Security Configuration
The introduction of the Default Domain Security Policy Wizard streamlines the configuration of essential security policies, making it user-friendly and efficient. Navigating the complexities of security policies becomes a breeze with this innovative tool, ensuring a safer digital environment for your business.
#5 — LiveArchive: Long-Term Email Archiving and Backup
Peace of Mind for Critical Data
LiveArchive.next is ExchangeDefender’s next-gen solution for long-term email archiving and backup. Designed to address the unique challenges faced by clients in 2023, LiveArchive.next ensures access to critical data even in worst-case scenarios, such as account wipes, crypto locks, or business closures.
Key Features:
- Live backup of all inbound and outbound messages.
- Email backups are stored on industry-standard S3 data object storage.
- Client-owned backups with customizable data retention.
ExchangeDefender’s suite of solutions goes beyond conventional email management, offering a comprehensive approach to security, continuity, and privacy. In an era where digital communication is paramount, these tools empower businesses and individuals to navigate the challenges of the modern email landscape with confidence and ease.
LiveArchive Onboarding

ExchangeDefender LiveArchive has gotten a massive refresh for 2024 to help our users get a better email backup & archiving solution that fits their needs. We are helping our partners and clients deploy the new LiveArchive solution stack and export data so here are some best practices and suggestions if you’re waiting for your deployment window or choose to DIY it.
Overview
If you already have a plan, roll it out right now! Documentation and step-by-step guide is available here: https://exchangedefender.com/docs/livearchive-cloud-backend
If you’re deploying this for someone else, here is a quick executive overview of the features you might want to bring up and explain to the decision-maker:
– Archiving solution in which you control and own the backend (no vendor lock-in)
– Archives corporate email from a journal mbox on M365
– No size limitation for archived messages
– No limit for attachments
– Integrates with cloud (Gmail/O365/etc) or on-prem
– Encrypted storage of archive emails and attachments
– One-time setup, no need to maintain a user list
– Filter archive emails on a per-domain basis
– Enable archive rules in S3 to enable pruning of archive messages
– Quickly download the entire mailbox for any user
– Downloaded mailboxes can be imported into Outlook/O365/imap/maildir etc
In a nutshell, it’s an archiving solution for email that integrates with all popular email and cloud services, is affordable to operate, and relies on open-source solutions with an excellent track record that can enable you to create a backup strategy that fits your needs. There are tons of providers and hardware/software platforms that you can use as the backend depending on the complexity of retention policies.
Choose your cloud service
ExchangeDefender LiveArchive backend is powered by open source stack of MariaDB (open source version of Oracle MySQL) and S3 (open source object storage). They are available from public cloud companies as hosted services (example: Amazon Web Services RDS) as well as containers that can be deployed on a wide variety of cloud solutions (Azure, AWS, Linode, Dreamcloud), virtualized locally, even on consumer-level NAS appliances (example: QNap).
In terms of functionality, LiveArchive has the same features regardless of where the backend is hosted.
The choice is mostly between convenience and flexibility. You will have the most convenience deploying LiveArchive with Amazon AWS but you can build a more flexible or more affordable solution as well. You will have the most control over your data if you store it on a local NAS or server but that comes at the expense of maintenance and management of the backend hardware/software stack. You should find a provider that can reliably host the open source stack, offer you support if you ever have an issue with the account, and most importantly provide a reliable high-speed connection for you to restore your data with someday.
Choose your access & recovery strategy
ExchangeDefender LiveArchive can function in minimal mode with just access to S3 bucket to store messages. This is the most affordable and most efficient way to archive messages, but without message metadata, all you’ll have is user@domain.com directories and any eDiscovery/search/recovery would require you to run a full-text search on the entire directory. If you are primarily concerned about the cost and are only backing up email for CYA purposes in the event of a disaster, this might be a viable option.
ExchangeDefender recommends deploying LiveArchive with MariaDB/AWS RDS service enabled. Doing so will enable LiveArchive to log your messages to a SQL database that is used by LiveArchive Web UI to access and recover messages. Deploying Web UI with MariaDB enables you to deliver the same LiveArchive service we have delivered for decades, but with you fully owning the entire archiving solution end to end on a proven and reliable open-source platform.
Your choice of access will dictate your recovery strategy. Minimalist/CYA approach to archiving will enable you to restore and search entire mailboxes. Adding LiveArchive Web UI and MariaDB makes the entire solution more user-friendly.
Confirm that you can access your cloud services remotely
ExchangeDefender LiveArchive onboarding calendar for 2023 is nearly full so to make sure your deployment goes smoothly make sure you can access your S3 and RDS resources remotely. Our documentation will help you set the whole thing up but please pay particular attention to confirming remote connectivity. If you can’t reach the S3 or SQL from Starbucks Wifi odds are great that LiveArchive won’t be able to either so please make sure you can access all the buckets, that you can create and drop tables in SQL, etc. We look forward to getting your next-gen archiving solution up and running!
Preparing for LiveArchive Retirement

As mentioned on our recent webinars and blog posts, LiveArchive has worked very hard for us for decades and it’s time for it to go to Florida and retire.
The new kid on the block – ExchangeDefender Inbox – has been running our client’s business continuity for over a year and it’s proven to be more efficient and popular than LiveArchive. Just log in to your account (https://admin.exchangedefender.com) or use passwordless login and click on Inbox. You’ll have the last two weeks of email waiting for you there and you can send/receive while your email server/mailbox/or whatever is down or under maintenance.
Longer Term Archiving
While Inbox will take care of our clients’ email needs when their email is having issues, many of you need long-term archiving. If LiveArchive was ever power-used it would be in the realm of data recovery after a disaster, cryptolocker, or other threat destroyed the client’s email infrastructure. For those of you who are aware of the risk, there will be a need for archiving to go way beyond two weeks – even years. This is what the new LiveArchive will start doing for you on January 1st, 2024!
First, let’s get ready for the retirement of the current LiveArchive – the service will shut off on December 31st, 2023 at which point all data including backups and configurations will be removed from our network. This means that if you wish to keep current LiveArchive contents the migration request must be put in as a ticket at our support site at https://support.exchangedefender.com. Simply open a ticket with the subject “LiveArchive Migration” and provide the domain names you wish to migrate and the S3/RDS login credentials by December 1st, 2023. As promised on the webinar, we are offering this migration free of charge to our clients and partners but you need to get in the line by December 1st and have your AWS S3/RDS or self-hosted setup completed.
Second, if you need any help with AWS S3/RDS or if you’d like assistance with deploying this solution in your home office or data center, we got you too. If you need help and get in touch with us by December 1st, we’ll take care of it for you. It’s super simple, takes about 5 minutes total, and is extensively documented – but we love our clients and if you want an extra pair of hands we can help you. After December 1st (and depending on availability) we will take care of the setup for a one-time fee of $499 for AWS or $999 for self-hosted.
Future of LiveArchive
We look forward to this middle tier that every organization that relies on email to run their business needs. For business continuity, Inbox will give you access to email anywhere, anytime. For backups and long-term retention across various clouds and storage options, LiveArchive will take care of archiving your data. For additional assurance and best-in-class storage that meets complex compliance and insurance requirements, ComplianceArchive is your eDiscovery and compliance archiving solution. Simply put no matter how critical email is to your organization we’ve got a solution that fits your problems and your budget.
The new LiveArchive will start doing for you on January 1st, 2024!
Announcing LiveArchive.Next

We’re excited to introduce you to our next version of LiveArchive: a long-term email archiving and backup solution that you can take with you. With the new LiveArchive we had to solve some unique challenges our clients face in 2023 and beyond:
1. We don’t have any room in our IT budget (and need to save $)
2. If we get compromised our backups will get crypto locked too
3. We have to protect and backup our email for years
We heard you loud and clear and the LiveArchive.next was designed from the ground up to give you the peace of mind that you’ll have access to your critical data even if Microsoft wipes your account, even if you get crypto locked out of your network, even if we go out of business, and yes it can also do it for you nearly free of charge.
Choice of Storage
LiveArchive.next uses object-based storage backend that is widely used and available for free with full source code. You don’t have to worry about the product getting discontinued or the company going out of business and most modern IT workers will have experience/certification for it. ExchangeDefender provides documentation on how to set a service up with Amazon Web Services using the S3 object storage if you want to keep your backups in the cloud. We also provide docker documentation for those who want to keep the backups on their own Synology NAS or as affordable as a Raspberry Pi.
There is no “one size fits all” when it comes to how you protect your backups and the point is to have flexibility that will fit your needs. LiveArchive.next will accommodate you no matter where you point it. Some organizations may rely on LiveArchive in the cloud to reduce complexity while others will point LiveArchive to their office NAS where they can save years of mailboxes and terabytes of data on an appliance/drives that can be taken offsite like old-timey tape backups you heard about in in IT history class.
Choice of Database Options
LiveArchive.next can optionally store your message metadata in an SQL database. While this is an optional part that isn’t required for backups to work, it does make LiveArchive very user-friendly. Without the database, all your messages will still be backed up and you will still be able to retrieve them directly from the S3 object storage bucket through a friendly web user interface or S3 client.
With Amazon RDS or MySQL configured, ExchangeDefender will also send message metadata to your database: sender email address, recipient email address, subject, date, etc. This information is used by our LiveArchive Web UI service to show users the friendly webmail interface you’ve become accustomed to.
This feature is optional but highly recommended by ExchangeDefender and you’ll appreciate it immensely the first time you’re sent on a quest to retrieve an email from 4 years ago.
Choose to be Live
Most backups are still performed as a scheduled task / job and only run periodically. When there is an issue the alert may or may not be sent to your IT staff and responsible IT providers have staff that frequently manually checks and verifies backups.
ExchangeDefender LiveArchive is live, meaning that a message that was received in your Outlook will be received in your LiveArchive archive in seconds instead of hours or days. There are no jobs or backup tasks to monitor or review – and we’ll notify you the second we identify a problem.
When you enable database services your users will be able to access their LiveArchive in realtime as well, so for those of you trying to save $ on IT this will help you to diversify some of the monitoring and risk away.
Additionally, everything being live means that our service will backup and archive email the moment it arrives so there is no job to set up, no new mailboxes or services to enroll. If the mail is hitting a mailbox in your organization you can expect it to automatically show up in LiveArchive in seconds.
To find out more about the next LiveArchive please join us for an informative webinar on November 8th, 2023. Take the moment to sign up for the ExchangeDefender LiveArchive Migration Service if you’d like us to port your existing LiveArchive data to your next LiveArchive. Check out all the documentation we’re putting out there and get in touch with us early because this service is in heavy demand and December quickly books up with EOY projects.
We look forward to helping you expand and improve your email protection in 2024 and beyond!
Sunsetting LiveArchive
On December 31st, our current version of LiveArchive will be decommissioned. Inbox, a business continuity solution we launched last year, has already taken the workload of LiveArchive and it does the job better, faster, with fewer clicks.
LiveArchive served our client base well for over a decade and we’re thankful for all the disasters it’s saved us and our clients from. Now that we’re looking at 2024 and beyond, LiveArchive must solve new problems. For starters, most email is no longer hosted on low-grade hardware in SMB offices managed by part-time hobbyist IT: It’s now professionally managed in high-end data centers. The primary concern is no longer “What if my T1 Internet connection goes down?”; “BACKUPS ARE OUR RESPONSIBILITY” and keeping all your eggs in one basket is never a good idea.
COVID and the work-from-home era have only exacerbated the problem of how quickly (if at all) you’ll get your email back when the disaster occurs. Cloud operators are vague in their data protection statements and there is no way to audit it. Backup tools and services similarly offer few guarantees and the supply chain attacks have only gotten more prominent.

New LiveArchive Migration Service
New LiveArchive is designed to help solve the 3 problems clients have with protecting cloud email:
1. We don’t have any room in our IT budget (and need to save $)
2. If we get compromised our backups will get cryptolocked too
3. We have to protect and backup our email
ExchangeDefender LiveArchive.next webinar on November 8th, 2023 covered exactly how the next version of LiveArchive is going to help you solve all of these problems.
Furthermore, we announced a LiveArchive Migration Service for our clients who wish to have the LiveArchive data ported to the new LiveArchive. Because LiveArchive is IMAP based we can pull existing LiveArchive data into the new version. We can use the same IMAP process to bring over mailboxes hosted on any other IMAP accessible (M365, Office365, Gmail, Exchange, and virtually every legacy email service).
In order to get your data migrated all you have to do is configure your new LiveArchive service and put your ticket request in by December 1st, 2023. We take care of everything else and to reward our loyal clients over the years the service will be provided free of charge (est $499 value).
LiveArchive MSP Launch
As you’ve read/heard we’re expanding our LiveArchive offering to include unlimited backups of email (external + inter-domain/office) powered by an affordable and flexible S3 object storage. We’re nearing completion of the deployment with our enterprise and managed clients and are starting to schedule rollouts for our MSP and SMB clients in November.
ExchangeDefender LiveArchive will enable you to provide long-term archiving and email backup. It may surprise you that none of the email hosting operations includes a backup – so if your mailbox gets accidentally deleted, if you suffer a crypto locker or similar compromise, if you have a malicious actor internally, or if you get hacked – all your data is at risk. The vendor will quickly point you to their terms of service that tell you data backups are your responsibility. LiveArchive has traditionally been the “backup of last resorts” to many of our clients who trusted their vendor for backups or used a local NTFS backup facility.
To thank our partners and clients for their business, we’re including this in our offering free of charge but you must deploy it in 2023. This type of service starts around $3-5/month/mailbox for MSP resellers with a big volume discount so if you’re currently backing up your Exchange or Office365 / M365 or Gmail you’ll be able to save your clients ~$30-60/mailbox every year!
We want to make our partners look good with this new service and invest in a free rollout service for LiveArchive. Every Office365 client we demoed this service to has signed up for it and we fully intend to charge for new domains after January 1st so if you want to grandfather this offering for free and make some $ during a tough economic cycle, we’re here for you:
LiveArchive Orientation Webinar
November 8th, 2023, 12PM EST
To sign up, https://attendee.gotowebinar.com/register/9154739856133683550
Webinar attendance is required in order to get LiveArchive deployment and support, if you cannot make it to the event don’t worry the recording will be available shortly after the event ends. Please keep in mind this offering has had enormous interest from our partners in particular (again, you’ll be able to save your clients $30-60/user/year). Please do not delay as we fully expect to book our 2023 deployment calendar by mid-November. To get ready, launch a Minio instance or set up a free Amazon S3 account and confirm they are accessible from the Internet. We look forward to seeing you on November 8th, sign up today!
LiveArchive is Dead, Long Live LiveArchive
ExchangeDefender recently announced changes to our LiveArchive service and its future as an email backup and archiving service that gives you control and ownership over your email. As you may know, no popular email solutions like Office365 and Gmail include a backup. If your account is accidentally deleted, hacked, or encrypted your data is lost – permanently.
Until now ExchangeDefender LiveArchive has served as a business continuity solution, enabling clients to send and receive email when their mail server or email cloud service experiences an outage or maintenance window.
When we first built LiveArchive in early 00’s the business Internet world was different. Clients overwhelmingly owned and managed their own email servers that ran on Internet connections and experienced frequent outages.
Our clients needed to send and receive email during these outages reliably but this was way before the era of smartphones, hotspots, reliable Wi-Fi, and secure Wi-Fi availability virtually everywhere. Naturally, clients needed a sophisticated web interface (first LiveArchive ran on an Exchange Server 2003 backend) and were usually working from LiveArchive for hours or days depending on the severity of the outage.
As many organizations moved their email hosting to the cloud the need changed from long-term powerful archiving to fast, secure, and mobile-friendly access to the latest messages and the ability to send and receive email during outages.
-Vlad Mazek, CEO ExchangeDefender
Last year we introduced you to ExchangeDefender Inbox, our next-generation live mailbox explicitly designed for reliable email access during outages. ExchangeDefender Inbox features a minimalist user interface that is fast, reliable, and intuitive – making it easy to work with from anywhere and on any device without having to set up or maintain anything – It’s just your Inbox live on ExchangeDefender.
If you can’t reach your email, Go to Inbox.
Need long-term backups and archiving? That’s LiveArchive’s new trick.
So what is LiveArchive up to?
Over the past few years of crypto locker and frequent Microsoft security exploits, many of our clients faced ransomware and lost email after getting hacked. Many found out the hard way that Microsoft and Google only offer the service but do not provide backup or mail snapshots – that’s your responsibility.
Enter new LiveArchive.
As many of our clients moved to the cloud we’ve become instrumental in providing them with a reliable backup solution for their Office365/M365 tenants as well as a wide variety of email servers and services.
For too many organizations LiveArchive became the last source of email data and the only emails they could recover after a security compromise that left their data cryptolocked and held for ransom. In working with them we were often asked to provide a more thorough email backup replication that could help organizations meet their new security objectives. At the same time, regulatory requirements and cyber-insurance got more demanding about keeping an offsite copy of all relevant company information.
We’ve built them all into the new LiveArchive.
Here are the main benefits:
- Live backup of all mail flowing through your organization (inbound and outbound messages are transparently archived through SMTP connectors)
- Email backups are stored on industry standard S3 data object storage service available in the cloud from Amazon AWS as well as free open source solutions, enabling you to store backups anywhere you want.
- The client owns all the email backups and storage accounts and can set data retention as they want. Because they are on a client-managed storage system messages can be connected to services for eDiscover, analytics, disaster recovery, record sharing, and more.
The key benefit is that you’re getting a free service that can archive your messages in real time to a data object storage service you own or control. Similar solutions cost between $30-50/year for each user/mailbox, enabling you to save on your backups while improving recovery.
TL;DR;
ExchangeDefender Inbox is your new always-available, always-realtime email business continuity solution, enabling your users to continue sending and receiving emails during an outage. Just go to https://admin.exchangedefender.com and click on Inbox.
Next steps:
Next month (early November) we will be making the new LiveArchive available enabling you to make live and continuous backups of your Microsoft M365, Office 365, Google Gmail, and other business email.




