Merry Christmas
From our family to yours, Merry Christmas.
And remember — Santa comes down the chimney, not through your inbox. That “urgent gift card” email isn’t from the North Pole.

ExchangeDefender Rolls Out Advanced ‘Reject Policies’ for Safer Inboxes
At ExchangeDefender we’ve always seen ourselves as the firewall that keeps unwanted email content entering or exiting our clients network. To keep compliance simple we never deleted emails – if the content was objectionable we would scan it, log it, and let org and user policies choose what happens to the message.
As the email world becomes more dangerous, with AI capable of conducting social engineering scams at scale, IT teams are looking for new policies that can handle it.
At ExchangeDefender we work closely with our partners around the world and this feature is courtesy of Tommy from Twisted Networx.
Tommy is hardly alone when it comes to this issue, some businesses pride themselves on the amount of money they spend on aggressive marketing via email. Ghost resubscribes, unsubscribe pages not working, confusing UI to trick you into buying or sharing info, and endless scams are just a part of business on the Internet these days. It’s something ExchangeDefender can help you fix.
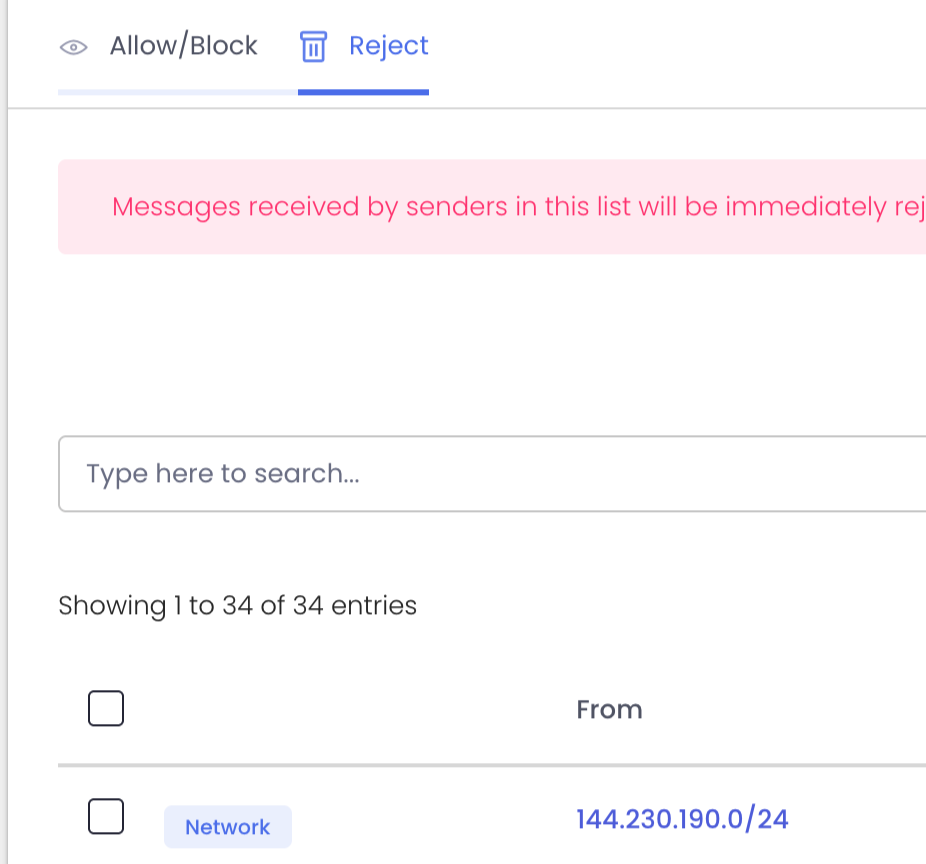
We’re introducing Reject Policies.
If you’ve identified an organization you do not want to communicate with for any reason, or if you have a network you want to keep out, or if you just want a quieter quarantine: ExchangeDefender will now reject the email on your behalf and you will never have to see it again.
For compliance purposes we will of course log the rejection in the Domain Admin logging facility at https://admin.exchangedefender.com but the message meta and any data will be rejected at the edge of the ExchangeDefender network. This way you will still be able to troubleshoot mail flow and make adjustments as needed.
We’re building a more flexible, powerful ExchangeDefender to meet real-world business challenges—and your feedback plays a big part in that. If you’ve got ideas that could make your email experience more secure or productive, we’d love to hear them.
New features and updated policies are rolling out later this fall. Stay in the loop by visiting https://support.exchangedefender.com, checking out our blog, or following us on social media.
5 Hidden Email Problems Encryption Solves Instantly
(and why ExchangeDefender is your easiest fix)
For most small businesses, email is the default way to communicate, send documents, close deals, and support clients. It’s fast, familiar, and convenient.
But under the surface? It’s also where some of your biggest risks live—risks that most SMBs and MSPs don’t see until it’s too late.
That’s where ExchangeDefender Encryption comes in. It’s not just about locking emails—it’s about solving the real problems you didn’t even know you had. Here are five issues it tackles the moment you turn it on:
1. You sent it to the wrong person
Mistakes happen. But when they involve sensitive info, they can turn into major incidents.
ExchangeDefender Encryption makes sure that even if your email ends up in the wrong hands, it can’t be read without proper authentication.
2. Your attachments are exposed
Contracts, client data, tax info—your attachments carry the good stuff. And without encryption, they’re easy targets.
With built-in attachment protection, ExchangeDefender keeps your files locked tight during transit and storage.
3. You have zero visibility
Standard email doesn’t tell you what happens after you hit “send.” Did they open it? Forward it? Screenshot it?
ExchangeDefender gives you detailed tracking and read receipts, so you stay in the loop.
4. Your team uses different email platforms
Some use Outlook. Some use Gmail. Others are mobile-only. Security gaps are everywhere.
ExchangeDefender works seamlessly across all platforms—no special downloads, no learning curve, just secure email everywhere.
5. You’re worried about compliance
HIPAA. GDPR. CMMC. It’s a lot. And falling short isn’t an option.
ExchangeDefender offers auto-detection, policy enforcement, reporting, and message expiration tools to make compliance a breeze.
Bottom line
You don’t have to overhaul your email system to get secure. With ExchangeDefender Encryption, you protect sensitive data, build client trust, and avoid costly mistakes—with one simple solution.
What Happens to Your Email During an Outage?
It’s Monday morning. Your inbox is unusually quiet. You open your browser—Outlook is down. Gmail? Frozen. Panic mode begins.
Enter Inbox by ExchangeDefender: your seamless, always-on backup email solution designed to just work when your primary provider doesn’t.
Never Miss an Email—Even During Outages
Email outages aren’t just annoying—they can be devastating for business. Whether it’s Microsoft 365, Google Workspace, or any other email provider, downtime happens. What matters is how quickly you bounce back.
Inbox automatically activates when your main email goes offline. No downloads. No IT tickets. No setup. Just log in and keep communicating with your clients, vendors, and team like nothing ever happened.
Real-Time Archiving + Instant Access
Inbox isn’t just a “break glass in case of emergency” tool—it’s your live email archive. Every incoming and outgoing message is captured before it hits your mailbox. That means:
- Access to every message, even if Outlook never delivered it
- Searchable archives by date, sender, subject, or keyword
- Full message read/reply/forward functionality built in
It’s not just backup. It’s better-than-backup.
Works Anywhere, on Everything
Need to check in from your phone during an outage? Done. Working on your iPad from the airport lounge? Easy. Inbox works on:
- Desktops
- Tablets
- Mobile devices
- Any browser
Whether you’re fully remote, hybrid, or in the office, you’re always connected.
No Learning Curve. No Stress.
Unlike most email continuity solutions that require complicated server setup or IT babysitting, Inbox is plug-and-play. It’s designed for regular users—just log in and go. It works invisibly in the background until you need it, then steps into the spotlight like a superhero with a clean interface and powerful tools.
Final Thought: Inbox Is Peace of Mind
You don’t need to wait for the next outage to start thinking about business continuity. Inbox gives you confidence that even when your primary provider fails, your communication won’t.
🔒 Your email is always available.
💬 Your conversations never stop.
📦 Your business keeps moving.
Ready to see how Inbox makes outages disappear? Download the brochure or try a live demo!
Don’t Take the Bait: Xfinity Phishing Emails on the Rise
Phishing emails targeting Xfinity (Comcast) customers are flooding inboxes again—and this wave is particularly deceptive. Disguised as legitimate communications from Xfinity, these emails are designed to create panic and trick users into compromising their security.
What’s Happening
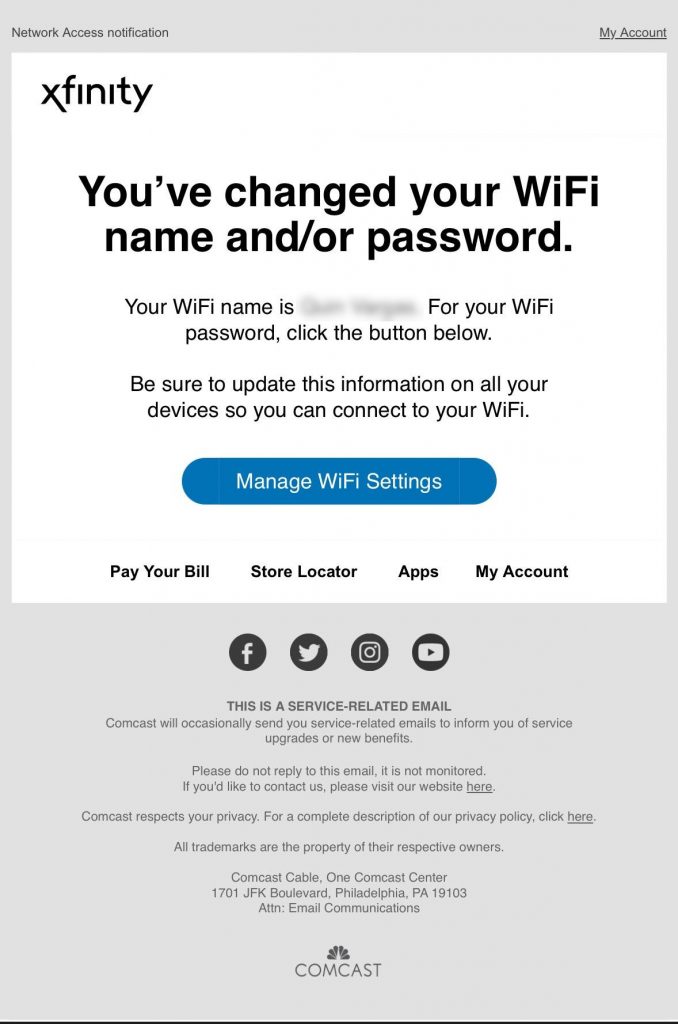
Cybercriminals are sending emails that appear to be from Xfinity, warning users about urgent account issues. Common themes include service interruptions, billing errors, or suspicious activity. The emails often ask recipients to “secure their account” or update personal information, directing them to fake login pages that harvest credentials.
Many of these messages are styled with official-looking Xfinity branding, and even the sender email address can appear authentic at a glance. Some victims have reported receiving fake invoices or confirmations for charges they never made—creating just enough concern to drive a click.
📌 Source:
Why It’s a Problem
Once you click on these links or share information, the consequences can be serious. Scammers may gain access to your Xfinity account, personal data, or even your entire device. This type of phishing can lead to identity theft, financial loss, or malware infections—especially if users unknowingly download files or enable remote access.
Even savvy users can fall for these tricks, which is why prevention and education are key.
📌 Sources:
How ExchangeDefender Helps
ExchangeDefender’s advanced threat protection is already working behind the scenes to block phishing emails like these. By scanning for malicious links, suspicious attachments, and known spam patterns, our system keeps these messages out of your inbox.
If you’re using our LiveArchive solution, your email continues to run smoothly—even if an attack disrupts your main provider.
Want to level up even further? Our Spearphish training platform delivers realistic phishing simulations to help your team recognize red flags before they click.
What You Should Do
If you receive a suspicious message claiming to be from Xfinity:
- Do not click any links or download attachments
- Go directly to your account via xfinity.com
- Report it to Comcast at abuse@comcast.net
📌 Also check out:
Make sure your team knows the signs of phishing and doesn’t trust emails that feel rushed, pushy, or “off.” And if you manage email for clients, now’s a great time to reinforce best practices.
Why Email Security Isn’t Optional Anymore (Even for Small Businesses)

Once upon a time, email security was something only big corporations worried about—firewalls, encryption, threat detection… it all sounded like enterprise stuff.
But those days? Long gone.
If your business has an email address (and let’s be honest, who doesn’t?), you’re already a target. And the bad guys? They’re counting on you thinking security is “someone else’s problem.”
Let’s break down why email security is no longer optional—especially for small businesses.
1. Small Businesses Are Easy Targets
Cybercriminals know that smaller companies don’t always have the time, money, or resources to invest in advanced security tools. That’s exactly why they get hit more often.
Think of it this way: would a burglar go after Fort Knox… or the house with the front door wide open?
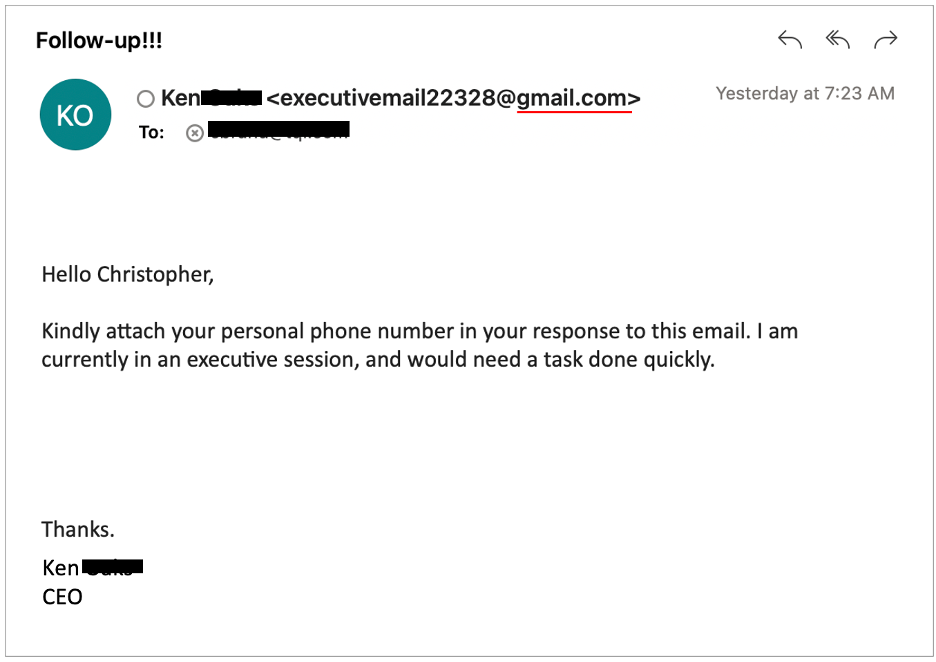
2. Phishing Scams Are Smarter (and Meaner)
Today’s phishing emails don’t look like Nigerian prince spam. They’re clean. Branded. Personalized.
They might come from what looks like your vendor, your CEO, or even your bank.
They want you to click the link, download the invoice, or reset your password.
And they’re sneaky good at it.
That’s why real-time threat detection and phishing filters are essential—not just “nice to have.”
3. Email Holds the Keys to Your Business
Think about it: your inbox is a treasure chest of…
- Client communications
- Invoices and payment links
- Internal documents
- Credentials and logins
- Contracts, quotes, and private notes
If someone gains access to your email, they don’t just read your messages—they own your business operations. And the recovery costs (both financially and reputation-wise) are brutal.

4. The Cost of NOT Securing Email Is Way Higher
Sure, tools like ExchangeDefender cost money. But do you know what costs more?
- Downtime
- Breach cleanup
- Legal fees
- Lost client trust
Email security is no longer a cost center—it’s a business continuity solution.
5. The Right Tools Make Security Simple
You don’t need to hire a team of security experts. ExchangeDefender helps small businesses stay protected with:
✅ Spam + phishing filters
✅ Email encryption
✅ Real-time malware scanning
✅ Quarantine reports + trusted sender controls
✅ Simulated phishing training
✅ 24/7 monitoring + support
It’s not just about defense—it’s about peace of mind.
Your email is your front door. Lock it.
Small business or not, today’s threats are real—and relentless. But with the right protection in place, you can focus on growing your business instead of chasing down security fires.
🔐 Want to see how ExchangeDefender can keep your email secure? Let’s talk.
Tired of Vendor Headaches? Why MSPs Choose ExchangeDefender for Streamlined Support

Let’s be honest: managing vendors can feel like babysitting a circus. You’re juggling tickets, waiting on “escalations,” and explaining the same problem five different times—while your client is breathing down your neck asking, “Is it fixed yet?”
Sound familiar?
That’s exactly why so many MSPs are switching to ExchangeDefender—not just for rock-solid email security, but for support that actually supports you.
We Know What MSPs Need—Because We’ve Been There
ExchangeDefender was built with MSPs in mind from day one. That means:
- Fast, no-nonsense support
- Clear escalation paths
- A team that understands how you work
No more battling a clueless Tier 1 rep reading from a script. When you call or chat with us, you’re talking to someone who gets it—and gets moving.
Less Waiting, More Solving
Other vendors? You submit a ticket… it disappears into the void.
With ExchangeDefender:
- You get status updates, not silence
- You can chat with a real person, not a bot
- And when there’s an issue, we’re proactive, not reactive
Because your reputation’s on the line, and we treat it like our own.
Partner-First, Not Product-First
Most vendors focus on their platform. We focus on your business.
That means:
- White-labeled portals to make you look good
- Multi-tenant dashboards that don’t require a PhD to use
- Sales and marketing support to help you grow—not just survive
When we help you win, we win. Simple as that.
What Our Partners Say
“We cut down support tickets by over 50% after switching to ExchangeDefender.”
— A Real-Life, Much-Happier MSP
“I don’t have to explain the same issue 3 times. They just get it—and fix it.”
— Another Grateful IT Pro

The Bottom Line
If you’re tired of chasing down support teams and patching together vendor chaos, it might be time to try something built for you.
💡 With ExchangeDefender, you get:
- Powerful email security & continuity
- End-user tools that make support easier
- Real humans who know their stuff
Ready to ditch the vendor headaches?
👉 Start your free trial today.
Top 5 Email Threats You Didn’t Know Were Hiding in Your Inbox

Let’s face it—email is the lifeblood of modern business. But behind every “urgent” subject line or familiar sender name, there could be something much more sinister lurking. At ExchangeDefender, we spend our days defending inboxes against threats most people don’t even know exist. So today, we’re spilling the secrets. Here are 5 sneaky email threats that could be hiding in plain sight:
1. Lookalike Domains (a.k.a. Evil Twins)

These emails come from addresses that look legit—maybe a single letter off from your CEO’s real email, or a domain that’s cleverly misspelled.
Why it’s dangerous: They’re made to trick you into clicking links or wiring money.
How we stop it: ExchangeDefender uses advanced domain and sender verification to block imposters fast.
2. Zero-Day Attachments
These are brand-new threats that haven’t even made it to antivirus databases yet. They come disguised as invoices, resumes, or project files.
Why it’s dangerous: Traditional filters might miss them.
How we stop it: Real-time scanning and sandboxing help catch unknown threats before you open them.
3. Credential Harvesting Links
Not all phishing scams are loud and obvious. Some hide in the form of password reset requests or shared documents.
Why it’s dangerous: One click can expose your login—and open the door to your entire system.
How we stop it: Link analysis and real-time URL scanning keep you protected, even from shortened or masked links.
4. Conversation Hijacking
Hackers insert themselves into real email threads and respond like they’re part of your team. Creepy, right?
Why it’s dangerous: You’re more likely to trust something that feels familiar.
How we stop it: Behavioral monitoring flags unusual responses—even when they happen mid-thread.
5. Impersonation of Internal Staff
Ever get a weird request from “Accounting” or “HR”? Sometimes, attackers mimic your internal teams to request sensitive info or payments.
Why it’s dangerous: These attacks rely on trust and internal knowledge.
How we stop it: ExchangeDefender uses AI and policy enforcement to detect when internal communication doesn’t add up.
So, What Can You Do?
Well, you already did the first step: you’re here. 🧠👏
The next step? Put a solution like ExchangeDefender Email Security between your team and the bad guys. We’re built to detect, block, and neutralize all of these threats—before they hit your inbox.
Because email should be for collaboration, not chaos.
👉 Learn more about how ExchangeDefender protects your business: https://exchangedefender.com/email-security
Email Outages Are Inevitable—Downtime Doesn’t Have to Be

We all know that email is the backbone of business communication. A disruption in email services can halt operations, delay responses, and impact customer trust. Recent events, such as the Microsoft Outlook outage in March 2025, left thousands without access to their emails, highlighting the vulnerability of relying solely on a single email provider.
The Business Impact of Email Downtime
When email services go down, the consequences can be severe:
- Operational Delays: Employees unable to access emails may miss critical deadlines and meetings.
- Customer Dissatisfaction: Delayed responses can frustrate clients and damage relationships.
- Financial Losses: Interruptions can lead to missed opportunities and revenue losses.
Introducing ExchangeDefender Inbox
To combat these challenges, ExchangeDefender offers Inbox — a robust email continuity solution designed to keep your business running smoothly during email outages. Inbox provides:
- Uninterrupted Access: Continue sending and receiving emails even when your primary service is down.
- Seamless Integration: Works alongside platforms like Outlook, Gmail, and Yahoo without the need for additional installations.
- Secure Storage: Automatically archives inbound and outbound emails for up to a year, ensuring data is always retrievable.
- User-Friendly Interface: Accessible on all modern devices, allowing your team to stay connected from anywhere.
Stay Prepared with ExchangeDefender Inbox
Email outages may be inevitable, but downtime doesn’t have to be. With ExchangeDefender Inbox, ensure your business remains responsive, reliable, and resilient.
Discover more about how Inbox can safeguard your communications: ExchangeDefender Inbox
Keep up with ExchangeDefender Changelog

When we launched our new user interface infrastructure, we did so that we could run ExchangeDefender at the cutting edge. By bringing all of our apps under one umbrella, we can now monitor and address bugs and performance issues in real-time.
The pace of development has really picked up, and when things are constantly improving, it’s important to keep everyone informed when issues get addressed and bugs get fixed. At https://admin.exchangedefender.com, when you log in as a Domain Administrator, you will now see a new Announcements button on the bottom right.
You can view our announcements on this screen (same content that is available on the login screen) and you can click on the Changelog to see our recent changes. This way you can see what is being added and fixed, and we can track it back to the original issue report.
We owe a huge thank you to our partners and clients for feature suggestions and bug-fix help last month, we are working hard to keep the web apps at the top security and industry standards because this is how people exchange sensitive information and we take great effort to make that easier and more secure.